Working on the AP-303H, without DSA, was a bit of a nightmare. And you may have discovered this. Those issues are not solved by DSA, but the testing results and solutions on this post are 100% necessary for the AP-303H running DSA firmware. I have not rolled back to non DSA firmware to retest and solve all those nightmare issues I ran into.
I am happy to report that with r21632 DSA is now released for the Aruba AP-303H.
There are some interesting discoveries on how to deploy on the AP-303H. This is a dedicated thread to document that, based on testing I completed. In case you are wondering how is the sausage made, the original work on this concluded on this post linked below and summarized on the final two comments.
This post is not for learning about general DSA or dumb AP concepts. The steps are more about the things that are missing and additive to OpenWRT's default. These principals are broadly transferable to any device though.
-
You cannot migrate your existing non DSA config, so make sure you reset.
-
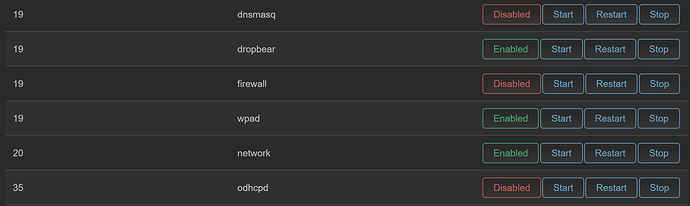
If this is future you reading this post and are coming back to upgrade your DSA to a newer version, be aware, after the upgrade, LUCI will not be installed, firewall, DHCP and DNSmasq will be enabled, which could cause problems for your accessing the management IP or your network. The packages you installed will be gone so likely will need to make a list of those things you installed.
-
Serial access is so important on this device, so buy or make a cable. Do not proceed until you have that.
-
Using the current snapshot build, follow the install procedure outlined here: https://openwrt.org/toh/aruba/ap-303h
-
Once you have IP connectivity, e.g. e0/WAN has a DHCP address from your network you should proceed.
-
manually install luci. You can do this by SSH on the LAN side (e1-e3) or by console.
opkg update
opkg install luci
-
Change your theme to Bootstrap as there is an invisible font (white on white) bug using theme OpenWrt2020 and documented here https://github.com/openwrt/luci/issues/6177
-
Put your management IP on a 802.11q sub-interface, with non-zero VID and assign a unique mac address. This solves errors when e0/WAN interface receives packets with same source MAC. This scenario will occur if you do any kind of upstream VLAN bridging. Basically, any scenario where a packet is leaving and then coming back in to the AP. This has been informally reported and in the future there may be improvements on the MAC address assignments on OpenWRT. I was even able to crash the AP until finding this solution.
[60035.624371] br-lan: received packet on wan with own address as source address (addr:20:4c:03:a8:10:f2, vlan:0)
[60035.669116] br-lan: received packet on wan with own address as source address (addr:20:4c:03:a8:10:f2, vlan:0)
[60035.787266] br-lan: received packet on wan with own address as source address (addr:20:4c:03:a8:10:f2, vlan:0)
[60035.907041] br-lan: received packet on wan with own address as source address (addr:20:4c:03:a8:10:f2, vlan:0)
[60036.026828] br-lan: received packet on wan with own address as source address (addr:20:4c:03:a8:10:f2, vlan:0)
[60036.146608] br-lan: received packet on wan with own address as source address (addr:20:4c:03:a8:10:f2, vlan:0)
[60036.266399] br-lan: received packet on wan with own address as source address (addr:20:4c:03:a8:10:f2, vlan:0)
[60036.386187] br-lan: received packet on wan with own address as source address (addr:20:4c:03:a8:10:f2, vlan:0)
[60036.506015] br-lan: received packet on wan with own address as source address (addr:20:4c:03:a8:10:f2, vlan:0)
[60036.625833] br-lan: received packet on wan with own address as source address (addr:20:4c:03:a8:10:f2, vlan:0)
This diagram demonstrates the issue:

In my case the physical MAC addresses (formerly eth0 and eth1) were as follows:
20:4C:03:A8:10:F2
20:4C:03:A8:10:F3
So to increment the last octet to a unique value for the management IP is how I selected the new MAC
20:4C:03:A8:10:F4 But you need this on a dedicated sub-interface (not the parent br-lan) with a non zero VID.
Here is a sample config.
config device
option type '8021q'
option ifname 'br-lan'
option vid '1'
option name 'br-lan.1'
option macaddr '20:4C:03:A8:10:F4'
option ipv6 '0'
config interface 'lan'
option proto 'static'
option ipaddr '192.168.1.3'
option netmask '255.255.255.0'
option ip6assign '60'
option device 'br-lan.1'
option gateway '192.168.1.254'
list dns '192.168.1.254'
list dns_search 'your.local.dns.zone.here'
- Disable routing as is not used on a dumb AP
vi /etc/sysctl.conf
# Defaults are configured in /etc/sysctl.d/* and can be customized in this file
net.ipv4.ip_forward=0
-
stop and disable firewall, DHCP and DNSMASQ permanently (after your next sysupgrade you will need to repeat this step)
-
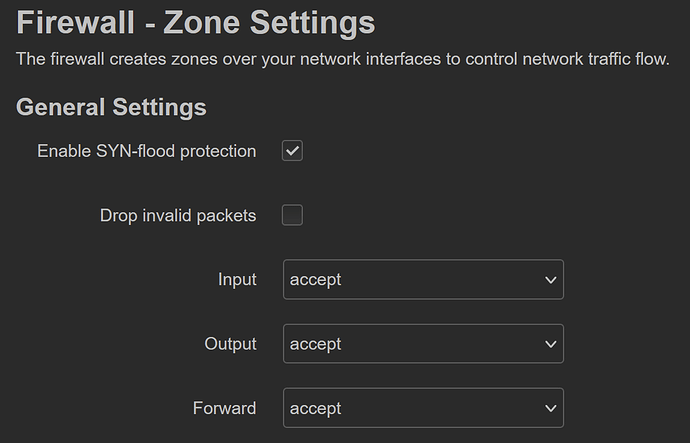
Delete firewall zones and set firewall to accept traffic as will be enabled after your 'next' sysupgrade. (You can test this by skipping this step. Enable your firewall and observe loss of access to the management IP from e0/WAN. Console access is always your friend in these situations.
/etc/init.d/firewall stop|start)
vi /etc/config/firewall
config defaults
option output 'ACCEPT'
option synflood_protect '1'
option input 'ACCEPT'
option forward 'ACCEPT'
Or like this...
- You may also benefit from deleting or renaming the
config dhcp 'lan'section of your DHCP config as is not needed, plus DHCP will be enable after a future sysupgrade.
vi /etc/config/dhcp
...
config dhcp 'lanx'
option interface 'lanx'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
option ignore '1'
option ra_slaac '0'
...
- Unless you plan to build out your IPv6 config, disable everywhere except loopback.
You can verify on the CLI and then go disable that interface.
ifconfig | egrep 'Link|inet'
br-lan Link encap:Ethernet HWaddr 20:4C:03:A8:10:F2
br-lan.1 Link encap:Ethernet HWaddr 20:4C:03:A8:10:F4 <----------------This MAC is unique and on non-zero VID
inet addr:192.168.1.3 Bcast:192.168.1.255 Mask:255.255.255.0
br-lan.11 Link encap:Ethernet HWaddr 20:4C:03:A8:10:F2
br-lan.31 Link encap:Ethernet HWaddr 20:4C:03:A8:10:F2
br-lan.4 Link encap:Ethernet HWaddr 20:4C:03:A8:10:F2
br-lan.5 Link encap:Ethernet HWaddr 20:4C:03:A8:10:F2
eth0 Link encap:Ethernet HWaddr 20:4C:03:A8:10:F2
lan1 Link encap:Ethernet HWaddr 20:4C:03:A8:10:F2
lan2 Link encap:Ethernet HWaddr 20:4C:03:A8:10:F2
lan3 Link encap:Ethernet HWaddr 20:4C:03:A8:10:F2
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
phy0-ap0 Link encap:Ethernet HWaddr 20:4C:03:A8:10:F2
phy1-ap0 Link encap:Ethernet HWaddr 20:4C:03:A8:10:F3
wan Link encap:Ethernet HWaddr 20:4C:03:A8:10:F2
You can pretty much role out your standard dumb AP config and VLANs.
Here is a final config:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd53:befa:5dae::/48'
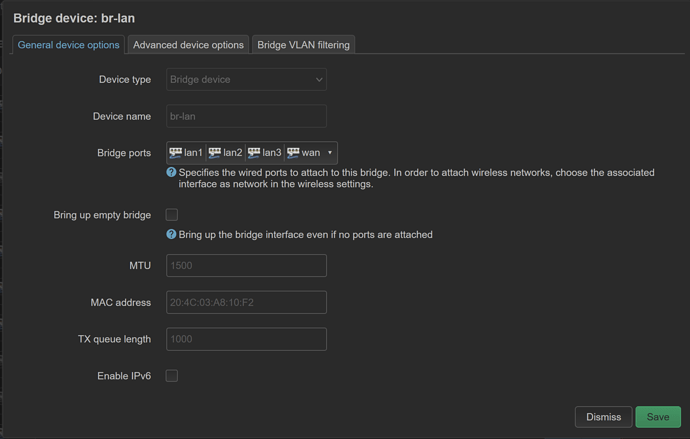
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'wan'
option ipv6 '0'
config interface 'lan'
option proto 'static'
option ipaddr '192.168.1.3'
option netmask '255.255.255.0'
option ip6assign '60'
option device 'br-lan.1'
option gateway '192.168.1.254'
list dns '192.168.1.254'
list dns_search 'your.local.dns.zone.here'
config device
option type '8021q'
option ifname 'br-lan'
option vid '1'
option name 'br-lan.1'
option macaddr '20:4C:03:A8:10:F4'
option ipv6 '0'
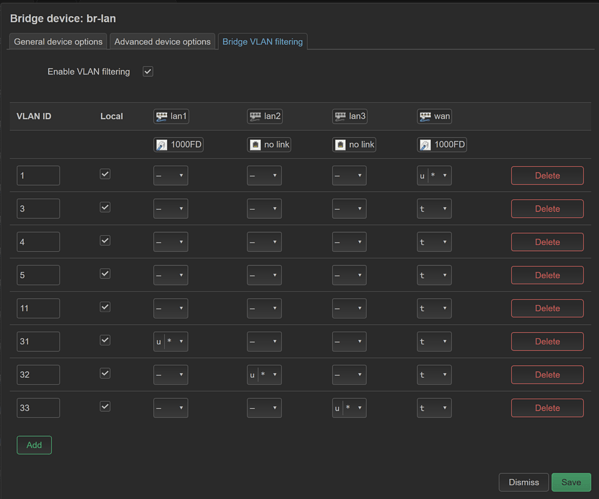
config bridge-vlan
option device 'br-lan'
option vlan '1'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'wan:u*'
config bridge-vlan
option device 'br-lan'
option vlan '3'
list ports 'wan:t'
config bridge-vlan
option device 'br-lan'
option vlan '4'
list ports 'wan:t'
config bridge-vlan
option device 'br-lan'
option vlan '5'
list ports 'wan:t'
config bridge-vlan
option device 'br-lan'
option vlan '11'
list ports 'wan:t'
config bridge-vlan
option device 'br-lan'
option vlan '31'
list ports 'lan1:u*'
list ports 'wan:t'
config bridge-vlan
option device 'br-lan'
option vlan '32'
list ports 'lan2:u*'
list ports 'wan:t'
config bridge-vlan
option device 'br-lan'
option vlan '33'
list ports 'lan3:u*'
list ports 'wan:t'
config device
option name 'eth0'
option ipv6 '0'
config device
option name 'br-lan.5'
option type '8021q'
option ifname 'br-lan'
option vid '5'
option ipv6 '0'
config device
option name 'br-lan.4'
option type '8021q'
option ifname 'br-lan'
option vid '4'
option ipv6 '0'
config device
option name 'br-lan.11'
option type '8021q'
option ifname 'br-lan'
option vid '11'
option ipv6 '0'
config device
option name 'br-lan.31'
option type '8021q'
option ifname 'br-lan'
option vid '31'
option ipv6 '0'
config device
option name 'br-lan.32'
option type '8021q'
option ifname 'br-lan'
option vid '32'
option ipv6 '0'
config device
option name 'br-lan.33'
option type '8021q'
option ifname 'br-lan'
option vid '33'
option ipv6 '0'
config device
option name 'phy0-ap0'
option ipv6 '0'
config device
option name 'phy1-ap0'
option ipv6 '0'
Issues:
2.4Ghz performance does not seem to match other Access Points. this can be seen in same room and edge of coverage area. More work to understand this needed.
5Ghz frequencies limited to those that don't require DFS radar detection. More work to understand this needed.
Possible issue with USB powered off and TBD