remove the ipv6 and accept local lines from below:
Do you need any ethernet ports for the NVR + cameras?
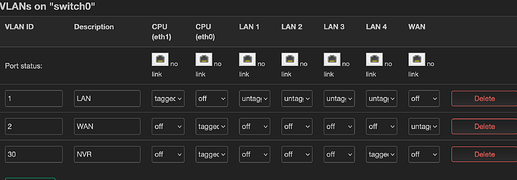
Currently, you've got VLAN 30 tagged on logical port 5 of the switch (not sure which physical port that maps to). Because it's tagged, unless your NVR (and/or whatever else is connected there) is VLAN aware, it will not be able to use that VLAN.
Instead, let's adjust like this... first remove logical port 5 from VLAN1, then use set that port as untagged in VLAN3. Also, we'll change the CPU connction to eth1 (logical port 0 - tagged so it'll be eth1.3):
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0t 2 3 4'
option vid '1'
option description 'LAN'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '0t 5'
option vid '30'
option description 'NVR'
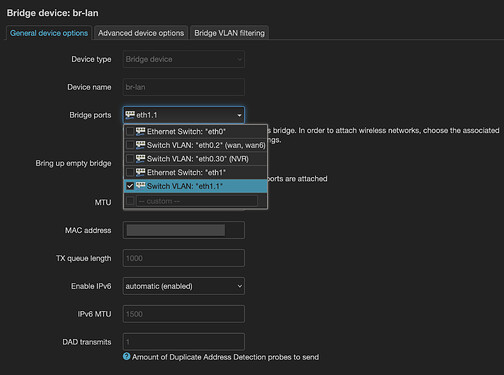
Your nvr bridge is referencing the wrong VLAN... we'll fix that like this:
config device
option type 'bridge'
option name 'br-NVR'
list ports 'eth1.30'
Finally, we'll fix the NVR network interface to use br-NVR and we'll fix some other issues there (the bridge type doesn't belong, and since this is the main router, it is the gateway -- you have another gateway listed which doesn't make sense):
config interface 'NVR'
option proto 'static'
option device 'br-NVR'
option ipaddr '192.168.30.1'
option netmask '255.255.255.0'
Your wifi for the NVR network does not have an SSID associated. Also, sae-mixed can cause problems with many devices. Use either WPA2 or WPA3, but avoid mixed mode.
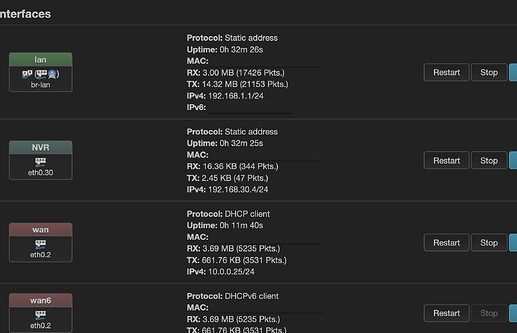
You don't have a DHCP server for your NVR network... add this to the DHCP file:
config dhcp 'NVR'
option interface 'NVR'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
Restart your router and then test again.
Connect a device via ethernet to logical port 5 (maybe physical port lan 4?? -- you might have to try all of the ports one at a time) -- it should get an address in the NVR network. And once you've fixed your wifi SSID issue for the NVR wireless, you should be able to connect by wifi as well.