I have successfully flashed the QWRT image [OpenWrt 21.02-SNAPSHOT, r47273-b4df38cf18, R23.8.10 (QSDK 12.1)] as provided by xHikari post on Apr 10, please review my sysupgrade process as below:-
root@OpenWrt:/# sysupgrade -n /tmp/qrt-arcadyan-aw1000.bin
Thu Jan 1 00:23:44 UTC 1970 upgrade: Image metadata not present
Thu Jan 1 00:23:44 UTC 1970 upgrade: Use sysupgrade -F to override this check when downgrading or flashing to vendor firmware
Image check failed.
root@OpenWrt:/# sysupgrade -F /tmp/qrt-arcadyan-aw1000.bin
Thu Jan 1 00:24:18 UTC 1970 upgrade: Image metadata not present
Image check failed but --force given - will update anyway!
Cannot save config while running from ramdisk.
Thu Jan 1 00:24:19 UTC 1970 upgrade: Commencing upgrade. Closing all shell sessions.
Watchdog handover: fd=3
- watchdog -
Watchdog did not previously reset the system
Thu Jan 1 00:24:19 UTC 1970 upgrade: Sending TERM to remaining processes ...
Thu Jan 1 00:24:19 UTC 1970 upgrade: Sending signal TERM to netifd (1974)
Thu Jan 1 00:24:23 UTC 1970 upgrade: Sending KILL to remaining processes ...
Thu Jan 1 00:24:23 UTC 1970 upgrade: Sending signal KILL to netifd (1974)
[ 1472.109718] stage2 (3122): drop_caches: 3
Thu Jan 1 00:24:32 UTC 1970 upgrade: Switching to ramdisk...
Thu Jan 1 00:24:33 UTC 1970 upgrade: Performing system upgrade...
ubiformat: mtd18 (nand), size 104857600 bytes (100.0 MiB), 400 eraseblocks of 262144 bytes (256.0 KiB), min. I/O size 4096 bytes
libscan: scanning eraseblock 399 -- 100 % complete
ubiformat: 400 eraseblocks have valid erase counter, mean value is 74
ubiformat: flashing eraseblock 399 -- 100 % complete
[ 1487.941798] ubi0: attaching mtd18
[ 1488.344951] ubi0: scanning is finished
[ 1488.351382] ubi0: attached mtd18 (name "rootfs", size 100 MiB)
[ 1488.351422] ubi0: PEB size: 262144 bytes (256 KiB), LEB size: 253952 bytes
[ 1488.356128] ubi0: min./max. I/O unit sizes: 4096/4096, sub-page size 4096
[ 1488.362978] ubi0: VID header offset: 4096 (aligned 4096), data offset: 8192
[ 1488.369831] ubi0: good PEBs: 400, bad PEBs: 0, corrupted PEBs: 0
[ 1488.376610] ubi0: user volume: 3, internal volumes: 1, max. volumes count: 128
[ 1488.382857] ubi0: max/mean erase counter: 231/75, WL threshold: 4096, image sequence number: 2061238594
[ 1488.389888] ubi0: available PEBs: 0, total reserved PEBs: 400, PEBs reserved for bad PEB handling: 80
[ 1488.399190] ubi0: background thread "ubi_bgt0d" started, PID 3913
[ 1488.409071] block ubiblock0_1: created from ubi0:1(rootfs)
UBI device number 0, total 400 LEBs (101580800 bytes, 96.8 MiB), available 0 LEBs (0 bytes), LEB size 253952 bytes (248.0 KiB)
sysupgrade successful
umount: can't unmount /dev: Resource busy
umount: can't unmount /tmp: Resource busy
[ 1488.943010] reboot: Restarting system
...
...
...
root@QWRT:/# free
total used free shared buff/cache available
Mem: 889856 190816 647484 1036 51556 648168
Swap: 0 0 0
root@QWRT:/# df
Filesystem 1K-blocks Used Available Use% Mounted on
/dev/root 39680 39680 0 100% /rom
tmpfs 444928 1036 443892 0% /tmp
/dev/ubi0_2 27748 696 25588 3% /overlay
overlayfs:/overlay 27748 696 25588 3% /
tmpfs 512 0 512 0% /dev
root@QWRT:~# ubus call system board; \
> head -n -0 /etc/opkg/*.conf
{
"kernel": "5.4.164",
"hostname": "QWRT",
"system": "ARMv8 Processor rev 4",
"model": "Arcadyan AW1000",
"board_name": "arcadyan,aw1000",
"release": {
"distribution": "OpenWrt",
"version": "21.02-SNAPSHOT",
"target": "ipq807x/generic",
"revision": "R23.8.10 (QSDK 12.1)",
"description": "QWRT "
}
}
==> /etc/opkg/customfeeds.conf <==
# add your custom package feeds here
#
# src/gz example_feed_name http://www.example.com/path/to/files
==> /etc/opkg/distfeeds.conf <==
src/gz openwrt_base https://downloads.immortalwrt.org/releases/21.02.1/packages/aarch64_cortex-a53/base
src/gz openwrt_luci https://downloads.immortalwrt.org/releases/packages-18.06-k5.4/aarch64_cortex-a53/luci
src/gz openwrt_packages https://downloads.immortalwrt.org/releases/21.02.1/packages/aarch64_cortex-a53/packages
src/gz openwrt_routing https://downloads.immortalwrt.org/releases/21.02.1/packages/aarch64_cortex-a53/routing
src/gz openwrt_telephony https://downloads.immortalwrt.org/releases/21.02.1/packages/aarch64_cortex-a53/telephony
The device's mobile 4G/5G interface wan appears to be working as I can ping any ip address and any domain name on the internet through via System TTYD Terminal prompt.
QWRT login: root
Password:
BusyBox v1.33.2 (2023-08-05 16:42:02 UTC) built-in shell (ash)
MM NM MMMMMMM M M
$MMMMM MMMMM MMMMMMMMMMM MMM MMM
MMMMMMMM MM MMMMM. MMMMM:MMMMMM: MMMM MMMMM
MMMM= MMMMMM MMM MMMM MMMMM MMMM MMMMMM MMMM MMMMM'
MMMM= MMMMM MMMM MM MMMMM MMMM MMMM MMMMNMMMMM
MMMM= MMMM MMMMM MMMMM MMMM MMMM MMMMMMMM
MMMM= MMMM MMMMMM MMMMM MMMM MMMM MMMMMMMMM
MMMM= MMMM MMMMM, NMMMMMMMM MMMM MMMM MMMMMMMMMMM
MMMM= MMMM MMMMMM MMMMMMMM MMMM MMMM MMMM MMMMMM
MMMM= MMMM MM MMMM MMMM MMMM MMMM MMMM MMMM
MMMM$ ,MMMMM MMMMM MMMM MMM MMMM MMMMM MMMM MMMM
MMMMMMM: MMMMMMM M MMMMMMMMMMMM MMMMMMM MMMMMMM
MMMMMM MMMMN M MMMMMMMMM MMMM MMMM
MMMM M MMMMMMM M M
M
---------------------------------------------------------------
For those about to rock... OpenWrt 21.02-SNAPSHOT, r47273-b4df38cf18
---------------------------------------------------------------
root@QWRT:~# ping 8.8.8.8
PING 8.8.8.8 (8.8.8.8): 56 data bytes
64 bytes from 8.8.8.8: seq=0 ttl=116 time=260.560 ms
64 bytes from 8.8.8.8: seq=1 ttl=116 time=42.125 ms
64 bytes from 8.8.8.8: seq=2 ttl=116 time=161.885 ms
^C
--- 8.8.8.8 ping statistics ---
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max = 42.125/154.856/260.560 ms
root@QWRT:~# ping -4 cisco.com
PING cisco.com (72.163.4.185): 56 data bytes
64 bytes from 72.163.4.185: seq=0 ttl=229 time=276.897 ms
64 bytes from 72.163.4.185: seq=1 ttl=229 time=236.860 ms
64 bytes from 72.163.4.185: seq=2 ttl=229 time=356.435 ms
^C
--- cisco.com ping statistics ---
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max = 236.860/290.064/356.435 ms
root@QWRT:~# traceroute 8.8.8.8
traceroute to 8.8.8.8 (8.8.8.8), 30 hops max, 46 byte packets
1 10.111.13.188 (10.111.13.188) 151.329 ms 10.111.13.189 (10.111.13.189) 16.616 ms 14.414 ms
2 172.24.126.1 (172.24.126.1) 14.875 ms 14.381 ms 14.857 ms
3 10.194.122.209 (10.194.122.209) 15.897 ms 19.326 ms 23.782 ms
4 * * *
5 hu0-5-0-0.22rrpr01.optus.net.au (59.154.142.250) 47.193 ms hu0-3-0-0.22rrpr01.optus.net.au (124.19.61.167) 21.832 ms 25.545 ms
6 74.125.147.174 (74.125.147.174) 19.862 ms 28.842 ms 24.815 ms
7 192.178.97.155 (192.178.97.155) 24.409 ms 192.178.98.33 (192.178.98.33) 17.799 ms 192.178.97.225 (192.178.97.225) 20.384 ms
8 216.239.56.69 (216.239.56.69) 18.384 ms 142.250.224.225 (142.250.224.225) 19.756 ms 142.250.234.213 (142.250.234.213) 16.818 ms
9 dns.google (8.8.8.8) 23.612 ms 15.867 ms 18.749 ms
I can also obtain IP address via both wired Ethernet and wifi on my Windows PC from the device's DHCP server, however when pinging an internet address the packet can't be routed back to my PC, see below:-
C:\>ping 8.8.8.8
Pinging 8.8.8.8 with 32 bytes of data:
Reply from 192.168.1.1: Destination port unreachable.
Reply from 192.168.1.1: Destination port unreachable.
Reply from 192.168.1.1: Destination port unreachable.
Reply from 192.168.1.1: Destination port unreachable.
C:\>tracert -4 8.8.8.8
Tracing route to dns.google [8.8.8.8]
over a maximum of 30 hops:
1 <1 ms <1 ms <1 ms QWRT.lan [192.168.1.1]
2 QWRT.lan [192.168.1.1] reports: Destination protocol unreachable.
Trace complete.
C:\>ipconfig/all
Ethernet adapter Ethernet:
Connection-specific DNS Suffix . : lan
Description . . . . . . . . . . . : Alienware AW1022 2.5GbE Adapter
Physical Address. . . . . . . . . : 0C-37-96-94-CC-46
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
IPv4 Address. . . . . . . . . . . : 192.168.1.145(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Lease Obtained. . . . . . . . . . : Thursday, 4 July 2024 11:48:53 AM
Lease Expires . . . . . . . . . . : Thursday, 4 July 2024 11:59:26 PM
Default Gateway . . . . . . . . . : 192.168.1.1
DHCP Server . . . . . . . . . . . : 192.168.1.1
DNS Servers . . . . . . . . . . . : 192.168.1.1
NetBIOS over Tcpip. . . . . . . . : Enabled
C:\>ping -4 cisco.com
Pinging cisco.com [72.163.4.185] with 32 bytes of data:
Reply from 192.168.1.1: Destination port unreachable.
Reply from 192.168.1.1: Destination port unreachable.
Reply from 192.168.1.1: Destination port unreachable.
Reply from 192.168.1.1: Destination port unreachable.
C:\>ping 72.163.4.185
Pinging 72.163.4.185 with 32 bytes of data:
Reply from 192.168.1.1: Destination port unreachable.
Reply from 192.168.1.1: Destination port unreachable.
Reply from 192.168.1.1: Destination port unreachable.
Reply from 192.168.1.1: Destination port unreachable.
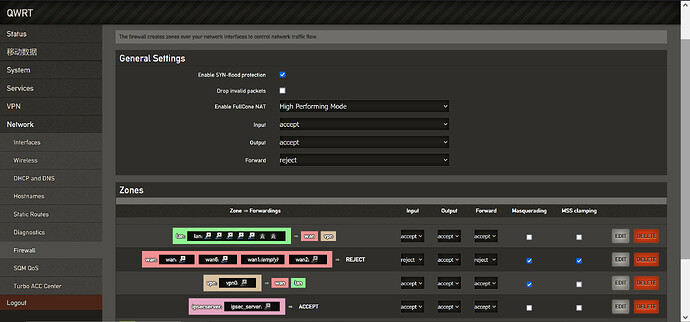
It may well be the firewall is blocking the traffic but I have a quick look at the both the /etc/config/network and /etc/config/firewall files, but I couldn't see anything apparent. As this is my very first time flashing the device and also looking at a Linux system, can someone share some thought and provide some insight?
root@QWRT:~# cat /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdff:1401:8ad2::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0 eth1 eth2 eth3 eth4'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option multicast_querier '0'
option igmp_snooping '0'
option force_link '1'
config interface 'wan'
option ifname 'wwan0'
option proto 'dhcp'
option metric '1'
config interface 'wan6'
option ifname 'wwan0'
option proto 'dhcpv6'
config interface 'vpn0'
option ifname 'tun0'
option proto 'none'
config interface 'ipsec_server'
option ifname 'ipsec0'
option device 'ipsec0'
option proto 'static'
option ipaddr '192.168.100.1'
option netmask '255.255.255.0'
config interface 'wan2'
option proto 'dhcp'
option metric '20'
option ifname 'wan2'
config interface 'wan1'
option proto 'dhcp'
option _orig_bridge 'false'
option metric '10'
option peerdns '0'
option dns '8.8.8.8 8.8.4.4 1.1.1.1 1.0.0.1'
root@QWRT:~# cat /etc/config/firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option flow_offloading '0'
option flow_offloading_hw '0'
option fullcone '2'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6 wan1 wan2'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
config include 'zerotier'
option type 'script'
option path '/etc/zerotier.start'
option reload '1'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
config include 'qcanssecm'
option type 'script'
option path '/etc/firewall.d/qca-nss-ecm'
option family 'any'
option reload '1'
config include 'luci_app_ipsec_server'
option type 'script'
option path '/var/etc/ipsecvpn.include'
option reload '1'
config include 'openclash'
option type 'script'
option path '/var/etc/openclash.include'
option reload '1'
config rule 'openvpn'
option name 'openvpn'
option target 'ACCEPT'
option src 'wan'
option proto 'tcp udp'
option dest_port '1194'
config zone 'vpn'
option name 'vpn'
option input 'ACCEPT'
option forward 'ACCEPT'
option output 'ACCEPT'
option masq '1'
option network 'vpn0'
config forwarding 'vpntowan'
option src 'vpn'
option dest 'wan'
config forwarding 'vpntolan'
option src 'vpn'
option dest 'lan'
config forwarding 'lantovpn'
option src 'lan'
option dest 'vpn'
config zone 'ipsecserver'
option name 'ipsecserver'
option input 'ACCEPT'
option forward 'ACCEPT'
option output 'ACCEPT'
option network 'ipsec_server'
root@QWRT:~# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- anywhere anywhere /* !fw3 */
input_rule all -- anywhere anywhere /* !fw3: Custom input rule chain */
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED /* !fw3 */
syn_flood tcp -- anywhere anywhere tcp flags:FIN,SYN,RST,ACK/SYN /* !fw3 */
zone_lan_input all -- anywhere anywhere /* !fw3 */
zone_wan_input all -- anywhere anywhere /* !fw3 */
zone_vpn_input all -- anywhere anywhere /* !fw3 */
zone_ipsecserver_input all -- anywhere anywhere /* !fw3 */
Chain FORWARD (policy DROP)
target prot opt source destination
forwarding_rule all -- anywhere anywhere /* !fw3: Custom forwarding rule chain */
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED /* !fw3 */
zone_lan_forward all -- anywhere anywhere /* !fw3 */
zone_wan_forward all -- anywhere anywhere /* !fw3 */
zone_vpn_forward all -- anywhere anywhere /* !fw3 */
zone_ipsecserver_forward all -- anywhere anywhere /* !fw3 */
reject all -- anywhere anywhere /* !fw3 */
ACCEPT all -- anywhere anywhere PHYSDEV match --physdev-is-bridged
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- anywhere anywhere /* !fw3 */
output_rule all -- anywhere anywhere /* !fw3: Custom output rule chain */
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED /* !fw3 */
zone_lan_output all -- anywhere anywhere /* !fw3 */
zone_wan_output all -- anywhere anywhere /* !fw3 */
zone_vpn_output all -- anywhere anywhere /* !fw3 */
zone_ipsecserver_output all -- anywhere anywhere /* !fw3 */
Chain MINIUPNPD (0 references)
target prot opt source destination
Chain RATE-LIMIT (1 references)
target prot opt source destination
RETURN all -- anywhere anywhere limit: avg 1000/sec burst 1000
DROP all -- anywhere anywhere
Chain forwarding_ipsecserver_rule (1 references)
target prot opt source destination
Chain forwarding_lan_rule (1 references)
target prot opt source destination
Chain forwarding_rule (1 references)
target prot opt source destination
Chain forwarding_vpn_rule (1 references)
target prot opt source destination
Chain forwarding_wan_rule (1 references)
target prot opt source destination
Chain input_ipsecserver_rule (1 references)
target prot opt source destination
Chain input_lan_rule (1 references)
target prot opt source destination
Chain input_rule (1 references)
target prot opt source destination
Chain input_vpn_rule (1 references)
target prot opt source destination
Chain input_wan_rule (1 references)
target prot opt source destination
Chain output_ipsecserver_rule (1 references)
target prot opt source destination
Chain output_lan_rule (1 references)
target prot opt source destination
Chain output_rule (1 references)
target prot opt source destination
Chain output_vpn_rule (1 references)
target prot opt source destination
Chain output_wan_rule (1 references)
target prot opt source destination
Chain reject (3 references)
target prot opt source destination
REJECT tcp -- anywhere anywhere /* !fw3 */ reject-with tcp-reset
REJECT all -- anywhere anywhere /* !fw3 */ reject-with icmp-port-unreachable
Chain syn_flood (1 references)
target prot opt source destination
RETURN tcp -- anywhere anywhere tcp flags:FIN,SYN,RST,ACK/SYN limit: avg 25/sec burst 50 /* !fw3 */
DROP all -- anywhere anywhere /* !fw3 */
Chain zone_ipsecserver_dest_ACCEPT (2 references)
target prot opt source destination
ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_ipsecserver_forward (1 references)
target prot opt source destination
forwarding_ipsecserver_rule all -- anywhere anywhere /* !fw3: Custom ipsecserver forwarding rule chain */
ACCEPT all -- anywhere anywhere ctstate DNAT /* !fw3: Accept port forwards */
zone_ipsecserver_dest_ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_ipsecserver_input (1 references)
target prot opt source destination
input_ipsecserver_rule all -- anywhere anywhere /* !fw3: Custom ipsecserver input rule chain */
ACCEPT all -- anywhere anywhere ctstate DNAT /* !fw3: Accept port redirections */
zone_ipsecserver_src_ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_ipsecserver_output (1 references)
target prot opt source destination
output_ipsecserver_rule all -- anywhere anywhere /* !fw3: Custom ipsecserver output rule chain */
zone_ipsecserver_dest_ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_ipsecserver_src_ACCEPT (1 references)
target prot opt source destination
ACCEPT all -- anywhere anywhere ctstate NEW,UNTRACKED /* !fw3 */
Chain zone_lan_dest_ACCEPT (5 references)
target prot opt source destination
ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_lan_forward (1 references)
target prot opt source destination
forwarding_lan_rule all -- anywhere anywhere /* !fw3: Custom lan forwarding rule chain */
zone_wan_dest_ACCEPT all -- anywhere anywhere /* !fw3: Zone lan to wan forwarding policy */
zone_vpn_dest_ACCEPT all -- anywhere anywhere /* !fw3: Zone lan to vpn forwarding policy */
ACCEPT all -- anywhere anywhere ctstate DNAT /* !fw3: Accept port forwards */
zone_lan_dest_ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_lan_input (1 references)
target prot opt source destination
input_lan_rule all -- anywhere anywhere /* !fw3: Custom lan input rule chain */
ACCEPT all -- anywhere anywhere ctstate DNAT /* !fw3: Accept port redirections */
zone_lan_src_ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_lan_output (1 references)
target prot opt source destination
output_lan_rule all -- anywhere anywhere /* !fw3: Custom lan output rule chain */
zone_lan_dest_ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_lan_src_ACCEPT (1 references)
target prot opt source destination
ACCEPT all -- anywhere anywhere ctstate NEW,UNTRACKED /* !fw3 */
Chain zone_vpn_dest_ACCEPT (3 references)
target prot opt source destination
DROP all -- anywhere anywhere ctstate INVALID /* !fw3: Prevent NAT leakage */
ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_vpn_forward (1 references)
target prot opt source destination
forwarding_vpn_rule all -- anywhere anywhere /* !fw3: Custom vpn forwarding rule chain */
zone_wan_dest_ACCEPT all -- anywhere anywhere /* !fw3: Zone vpn to wan forwarding policy */
zone_lan_dest_ACCEPT all -- anywhere anywhere /* !fw3: Zone vpn to lan forwarding policy */
ACCEPT all -- anywhere anywhere ctstate DNAT /* !fw3: Accept port forwards */
zone_vpn_dest_ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_vpn_input (1 references)
target prot opt source destination
input_vpn_rule all -- anywhere anywhere /* !fw3: Custom vpn input rule chain */
ACCEPT all -- anywhere anywhere ctstate DNAT /* !fw3: Accept port redirections */
zone_vpn_src_ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_vpn_output (1 references)
target prot opt source destination
output_vpn_rule all -- anywhere anywhere /* !fw3: Custom vpn output rule chain */
zone_vpn_dest_ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_vpn_src_ACCEPT (1 references)
target prot opt source destination
ACCEPT all -- anywhere anywhere ctstate NEW,UNTRACKED /* !fw3 */
Chain zone_wan_dest_ACCEPT (3 references)
target prot opt source destination
DROP all -- anywhere anywhere ctstate INVALID /* !fw3: Prevent NAT leakage */
ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_wan_dest_REJECT (1 references)
target prot opt source destination
reject all -- anywhere anywhere /* !fw3 */
Chain zone_wan_forward (1 references)
target prot opt source destination
forwarding_wan_rule all -- anywhere anywhere /* !fw3: Custom wan forwarding rule chain */
zone_lan_dest_ACCEPT esp -- anywhere anywhere /* !fw3: Allow-IPSec-ESP */
zone_lan_dest_ACCEPT udp -- anywhere anywhere udp dpt:isakmp /* !fw3: Allow-ISAKMP */
ACCEPT all -- anywhere anywhere ctstate DNAT /* !fw3: Accept port forwards */
RATE-LIMIT all -- anywhere anywhere ctstate NEW
zone_wan_dest_REJECT all -- anywhere anywhere /* !fw3 */
Chain zone_wan_input (1 references)
target prot opt source destination
input_wan_rule all -- anywhere anywhere /* !fw3: Custom wan input rule chain */
ACCEPT udp -- anywhere anywhere udp dpt:bootpc /* !fw3: Allow-DHCP-Renew */
ACCEPT icmp -- anywhere anywhere icmp echo-request /* !fw3: Allow-Ping */
ACCEPT igmp -- anywhere anywhere /* !fw3: Allow-IGMP */
ACCEPT tcp -- anywhere anywhere tcp dpt:openvpn /* !fw3: openvpn */
ACCEPT udp -- anywhere anywhere udp dpt:openvpn /* !fw3: openvpn */
ACCEPT all -- anywhere anywhere ctstate DNAT /* !fw3: Accept port redirections */
zone_wan_src_REJECT all -- anywhere anywhere /* !fw3 */
Chain zone_wan_output (1 references)
target prot opt source destination
output_wan_rule all -- anywhere anywhere /* !fw3: Custom wan output rule chain */
zone_wan_dest_ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_wan_src_REJECT (1 references)
target prot opt source destination
reject all -- anywhere anywhere /* !fw3 */