hey, I found a solution, it was quite simple actually. I tried a lot of things from trying to see if a port was being blocked to trying to forward port 8888 to the subnet (which, probably doesn't make sense. Luckily I am also not naive to port forward the port to the internet accidentally). At first I had a theory that forwarding was being blocked for the subnet, so I went to the firewall and allowed subnetting for all my networks in network->firewall. When that didn't work, I enabled everything, and then it worked. After that I just disabled them one by one to find out which one was needed for this to work, process of elimination, I'll figure out why this happens later
Let's say that main subnet is the vlan that is hosting tinyproxy (192.168.1.1:8888). While the tor subnet, is the vlan that has clients that want to connect to tinyproxy (by using 192.168.2.1:8888)
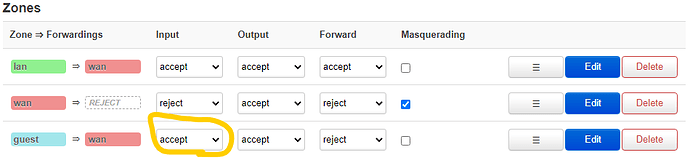
To allow clients from the tor subnet to connect to the proxy from the main subnet, you need to allow input from the tor subnet, to the main subnet.
It should look similar to this image. Guest is my tor subnet that needs to allow connections to tinyproxy
Additionally, to connect to tinyproxy, use tor's subnet address (192.168.2.1), not the main subnet's address.
the wiki says
INPUT rules for a zone describe what happens to traffic trying to reach the router itself through an interface in that zone.
Could allowing this lead to security risks? Probably, I am not sure. Based on what I can find, it's probably safe. If it could give any issues, I need to think of a way to reject all input, except if it's coming from one of my devices. In regards to security, below is all I can find, and because it doesn't seem urgent I won't fix it right now.
The links lead me to believe that the biggest threat would be devices in my network, not the internet, but I can trust my devices. My tor network already uses mac filters anyways