I had recently been able to create a vlan for my tor network (only that vlan has tor), after that, I setup tinyproxy, which is working perfectly outside that lan. Every device is able to connect to it. (Note, the wiki doesn't say this, but you need to add the line "list ControlPort 80" in order to allow apps like proxifier to connect to the proxy).
I am not able to connect to the proxy when I am connected to this vlan though. This is probably because it's setup as a guest vlan and it's also a bit hardened for tor. I have no idea what I should be looking for to allow tinyproxy to be accessible in this vlan. Can anyone help?
I might not reply today but I'll keep looking and thinking of why I can't connect to tinyproxy while using this vlan.
Firewall configuration:
root@xRocS:~# uci show firewall
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[0].network='lan'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@zone[1].network='wan' 'wan6' 'wwan'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@rule[9]=rule
firewall.@rule[9].name='Support-UDP-Traceroute'
firewall.@rule[9].src='wan'
firewall.@rule[9].dest_port='33434:33689'
firewall.@rule[9].proto='udp'
firewall.@rule[9].family='ipv4'
firewall.@rule[9].target='REJECT'
firewall.@rule[9].enabled='false'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.@redirect[0]=redirect
firewall.@redirect[0].target='DNAT'
firewall.@redirect[0].name='Transparent Proxy Redirect'
firewall.@redirect[0].src='lan'
firewall.@redirect[0].proto='tcp'
firewall.@redirect[0].dest_port='8888'
firewall.@redirect[0].src_dport='80'
firewall.@redirect[0].src_dip='!192.168.1.1'
firewall.@redirect[0].dest_ip='192.168.1.1'
firewall.nat6=include
firewall.nat6.path='/etc/firewall.nat6'
firewall.nat6.reload='1'
firewall.doh=ipset
firewall.doh.name='doh'
firewall.doh.family='ipv4'
firewall.doh.storage='hash'
firewall.doh.match='ip'
firewall.doh.entry='redacted'
firewall.doh6=ipset
firewall.doh6.name='doh6'
firewall.doh6.family='ipv6'
firewall.doh6.storage='hash'
firewall.doh6.match='ip'
firewall.doh6.entry='redacted'
firewall.doh_fwd=rule
firewall.doh_fwd.name='Deny-DoH'
firewall.doh_fwd.src='lan'
firewall.doh_fwd.dest='wan'
firewall.doh_fwd.dest_port='443'
firewall.doh_fwd.proto='tcp udp'
firewall.doh_fwd.family='ipv4'
firewall.doh_fwd.ipset='doh dest'
firewall.doh_fwd.target='REJECT'
firewall.doh6_fwd=rule
firewall.doh6_fwd.name='Deny-DoH'
firewall.doh6_fwd.src='lan'
firewall.doh6_fwd.dest='wan'
firewall.doh6_fwd.dest_port='443'
firewall.doh6_fwd.proto='tcp udp'
firewall.doh6_fwd.family='ipv6'
firewall.doh6_fwd.ipset='doh6 dest'
firewall.doh6_fwd.target='REJECT'
firewall.dot_fwd=rule
firewall.dot_fwd.name='Deny-DoT'
firewall.dot_fwd.src='lan'
firewall.dot_fwd.dest='wan'
firewall.dot_fwd.dest_port='853'
firewall.dot_fwd.proto='tcp udp'
firewall.dot_fwd.target='REJECT'
firewall.dns_masq=nat
firewall.dns_masq.name='Masquerade-DNS'
firewall.dns_masq.src='lan'
firewall.dns_masq.dest_ip='192.168.1.96'
firewall.dns_masq.dest_port='53'
firewall.dns_masq.proto='tcp udp'
firewall.dns_masq.target='MASQUERADE'
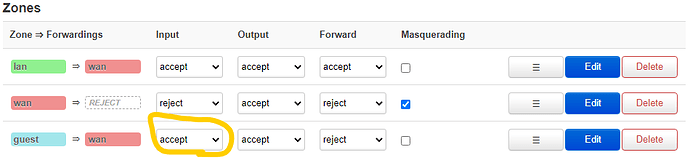
firewall.guest=zone
firewall.guest.name='guest'
firewall.guest.network='guest'
firewall.guest.input='REJECT'
firewall.guest.output='ACCEPT'
firewall.guest.forward='REJECT'
firewall.guest_wan=forwarding
firewall.guest_wan.src='guest'
firewall.guest_wan.dest='wan'
firewall.guest_wan.enabled='1'
firewall.guest_dns=rule
firewall.guest_dns.name='Allow-DNS-Guest'
firewall.guest_dns.src='guest'
firewall.guest_dns.dest_port='53'
firewall.guest_dns.proto='tcp udp'
firewall.guest_dns.target='ACCEPT'
firewall.guest_dhcp=rule
firewall.guest_dhcp.name='Allow-DHCP-Guest'
firewall.guest_dhcp.src='guest'
firewall.guest_dhcp.dest_port='67'
firewall.guest_dhcp.proto='udp'
firewall.guest_dhcp.family='ipv4'
firewall.guest_dhcp.target='ACCEPT'
firewall.tor=ipset
firewall.tor.name='tor'
firewall.tor.family='ipv4'
firewall.tor.storage='hash'
firewall.tor.match='net'
firewall.tor.entry='127.0.0.0/8 nomatch' '192.168.2.1/24 nomatch' '0.0.0.0/1' '128.0.0.0/1'
firewall.tor6=ipset
firewall.tor6.name='tor6'
firewall.tor6.family='ipv6'
firewall.tor6.storage='hash'
firewall.tor6.match='net'
firewall.tor6.entry='::1/128 nomatch' 'fe80::/10 nomatch' ' nomatch' '::/1' '8000::/1'
firewall.tcp_int=redirect
firewall.tcp_int.name='Intercept-TCP'
firewall.tcp_int.src='guest'
firewall.tcp_int.dest_port='9040'
firewall.tcp_int.proto='tcp'
firewall.tcp_int.extra='--syn'
firewall.tcp_int.ipset='tor dest'
firewall.tcp_int.target='DNAT'
firewall.@redirect[2]=redirect