Hardware:
- Rpi4 with USB eth dongle
- TP link 8 port managed switch
- TP link AP with VLANs
What I am hoping to accomplish:
WAN - eth1
VLAN10 - eth0.10 trusted 192.168.10.0/24
VLAN20 - eth0.20 untrusted 192.168.20.0/24
VLAN50 - eth0.50 personal 192.168.50.0/24
TP-link managed switch:
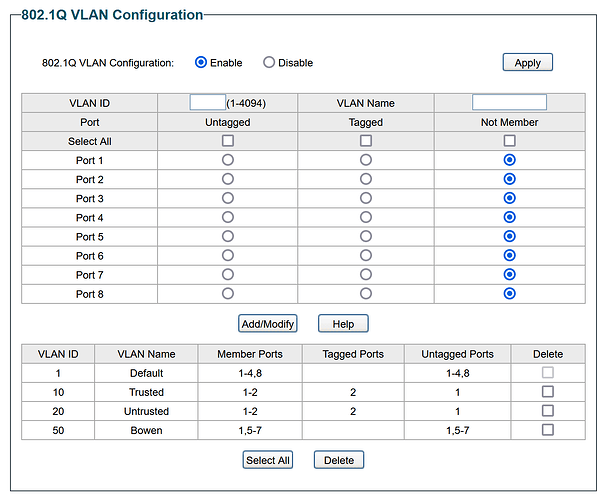
Port 1: trunk to openwrt (vlan 10, 20, 50)
Port 2: trunk to WAP (vlan 10, 20)
Port 5, 6, 7: personal access ports (vlan 50)
I would like for none of these VLANs to be completely segregated from each other.
Here is my current switch configuration:
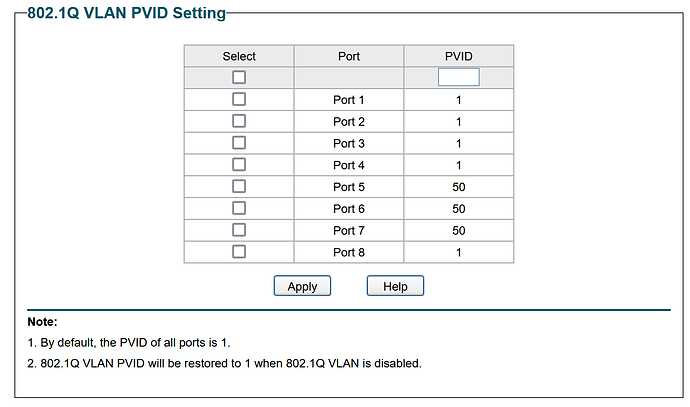
And here is my current network configuration:
/etc/config/network
config interface 'loopback'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
option device 'lo'
config globals 'globals'
option ula_prefix 'fde6:05ac:dbe0::/48'
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.0.1'
option device 'br-lan.1'
config interface 'wan'
option proto 'dhcp'
option hostname 'router'
option device 'br-wan'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config device
option name 'br-wan'
option type 'bridge'
list ports 'eth1'
config device
option name 'eth0'
config device
option type '8021q'
option ifname 'eth0'
option vid '10'
option name 'eth0.10'
config device
option type '8021q'
option ifname 'eth0'
option vid '20'
option name 'eth0.20'
config device
option type '8021q'
option ifname 'eth0'
option vid '50'
option name 'eth0.50'
config bridge-vlan
option device 'br-lan'
option vlan '1'
list ports 'eth0'
config bridge-vlan
option device 'br-lan'
option vlan '10'
list ports 'eth0:t'
config bridge-vlan
option device 'br-lan'
option vlan '20'
list ports 'eth0:t'
config bridge-vlan
option device 'br-lan'
option vlan '50'
/etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
option dnsforwardmax '2300'
option min_cache_ttl '270'
option cachesize '5000'
list address '/router/192.168.0.1'
list interface 'lan'
list interface 'vlan10'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra_management '1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option name 'BRN0080774FDE70'
option ip '192.168.0.178'
option mac
/etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'vlan50'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'vlan10'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'vlan20'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
option reload '1'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
config rule
option src '*'
option target 'ACCEPT'
option proto 'udp'
option name 'Allow-Tailscale'
option dest_port '41641'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'
config forwarding
option src 'vlan50'
option dest 'wan'
config forwarding
option src 'vlan10'
option dest 'wan'
config forwarding
option src 'vlan20'
option dest 'wan'
config rule
option name 'allow dhcp dns bowen'
option src 'vlan50'
option dest '*'
option dest_port '53 67 68'
option target 'ACCEPT'
config rule
option name 'allow dhcp dns trust'
option src 'vlan10'
option dest_port '53 67 68'
option target 'ACCEPT'
I'd appreciate any help with this setup if possible, not really sure where I'm going wrong in the configuration. Thanks!