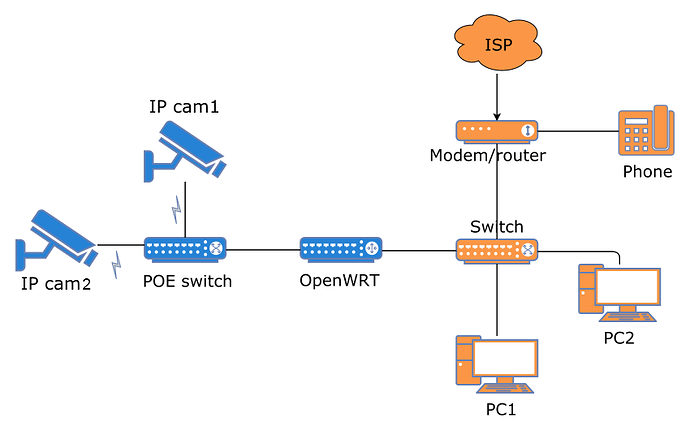
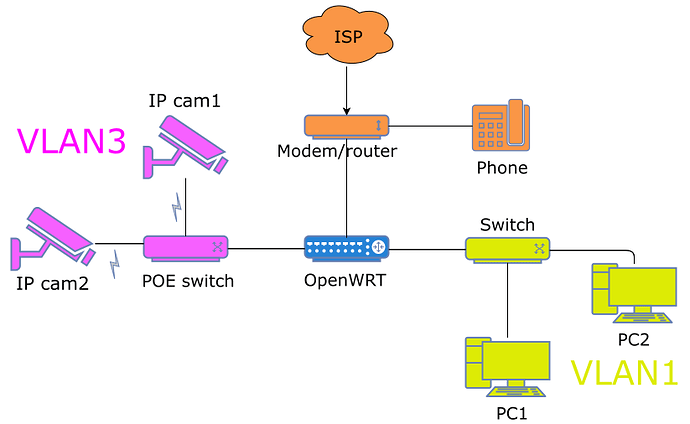
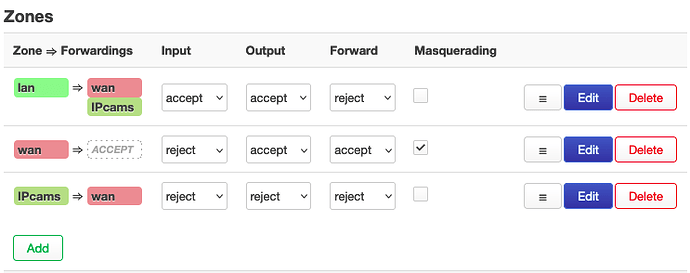
The ISP modem's IP is 192.168.1.1 and openWRT has 192.168.1.25 on wan. The dhcp server on vlan1 gives 192.168.0.x and on vlan3 it gives 10.0.30.x IP's.
{
"kernel": "5.10.146",
"hostname": "OpenWrt",
"system": "Broadcom BCM4712",
"model": "Linksys WRT54G/GS/GL",
"board_name": "0x0101:42",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "22.03.2",
"revision": "r19803-9a599fee93",
"target": "bcm47xx/legacy",
"description": "OpenWrt 22.03.2 r19803-9a599fee93"
}
}
package network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdeb:55fb:0078::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.0.100'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '1 2 5t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0 5t'
option vid '2'
config device
option name 'eth0'
config device
option name 'eth0.1'
option type '8021q'
option ifname 'eth0'
option vid '1'
config device
option name 'eth0.2'
option type '8021q'
option ifname 'eth0'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '3 4 5t'
option vid '3'
config device
option name 'eth0.3'
option type '8021q'
option ifname 'eth0'
option vid '3'
config device
option name 'br-lan-cam'
option type 'bridge'
list ports 'eth0.3'
config interface 'LANCAM'
option proto 'static'
option device 'br-lan-cam'
option ipaddr '10.0.30.1'
option netmask '255.255.255.0'
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'ACCEPT'
config zone
option name 'lan'
option output 'ACCEPT'
option forward 'REJECT'
option input 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option forward 'ACCEPT'
list network 'wan'
list network 'wan6'
option input 'REJECT'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'IPcams'
option forward 'REJECT'
list network 'LANCAM'
option input 'REJECT'
option output 'REJECT'
config forwarding
option src 'lan'
option dest 'IPcams'
config forwarding
option src 'IPcams'
option dest 'wan'
config rule
option name 'IPcams DHCP and DNS'
option src 'IPcams'
option dest_port '53 67 68'
option target 'ACCEPT'
config rule
list proto 'tcp'
option src 'lan'
option dest 'wan'
option dest_port '80 443'
option target 'ACCEPT'
option name 'allow modem web config'
head: /etc/firewall.user: No such file or directory
-ash: iptables-save: not found
-ash: ip6tables-save: not found
table inet fw4 {
chain input {
type filter hook input priority filter; policy accept;
iifname "lo" accept comment "!fw4: Accept traffic from loopback"
ct state established,related accept comment "!fw4: Allow inbound established and related flows"
tcp flags syn / fin,syn,rst,ack jump syn_flood comment "!fw4: Rate limit TCP syn packets"
iifname "br-lan" jump input_lan comment "!fw4: Handle lan IPv4/IPv6 input traffic"
iifname "eth0.2" jump input_wan comment "!fw4: Handle wan IPv4/IPv6 input traffic"
iifname "br-lan-cam" jump input_IPcams comment "!fw4: Handle IPcams IPv4/IPv6 input traffic"
}
chain forward {
type filter hook forward priority filter; policy accept;
ct state established,related accept comment "!fw4: Allow forwarded established and related flows"
iifname "br-lan" jump forward_lan comment "!fw4: Handle lan IPv4/IPv6 forward traffic"
iifname "eth0.2" jump forward_wan comment "!fw4: Handle wan IPv4/IPv6 forward traffic"
iifname "br-lan-cam" jump forward_IPcams comment "!fw4: Handle IPcams IPv4/IPv6 forward traffic"
}
chain output {
type filter hook output priority filter; policy accept;
oifname "lo" accept comment "!fw4: Accept traffic towards loopback"
ct state established,related accept comment "!fw4: Allow outbound established and related flows"
oifname "br-lan" jump output_lan comment "!fw4: Handle lan IPv4/IPv6 output traffic"
oifname "eth0.2" jump output_wan comment "!fw4: Handle wan IPv4/IPv6 output traffic"
oifname "br-lan-cam" jump output_IPcams comment "!fw4: Handle IPcams IPv4/IPv6 output traffic"
}
chain prerouting {
type filter hook prerouting priority filter; policy accept;
iifname "br-lan" jump helper_lan comment "!fw4: Handle lan IPv4/IPv6 helper assignment"
iifname "br-lan-cam" jump helper_IPcams comment "!fw4: Handle IPcams IPv4/IPv6 helper assignment"
}
chain handle_reject {
meta l4proto tcp reject with tcp reset comment "!fw4: Reject TCP traffic"
reject comment "!fw4: Reject any other traffic"
}
chain syn_flood {
limit rate 25/second burst 50 packets return comment "!fw4: Accept SYN packets below rate-limit"
drop comment "!fw4: Drop excess packets"
}
chain input_lan {
jump accept_from_lan
}
chain output_lan {
jump accept_to_lan
}
chain forward_lan {
tcp dport { 80, 443 } counter packets 0 bytes 0 jump accept_to_wan comment "!fw4: allow modem web config"
jump accept_to_wan comment "!fw4: Accept lan to wan forwarding"
jump accept_to_IPcams comment "!fw4: Accept lan to IPcams forwarding"
jump reject_to_lan
}
chain helper_lan {
}
chain accept_from_lan {
iifname "br-lan" counter packets 0 bytes 0 accept comment "!fw4: accept lan IPv4/IPv6 traffic"
}
chain accept_to_lan {
oifname "br-lan" counter packets 0 bytes 0 accept comment "!fw4: accept lan IPv4/IPv6 traffic"
}
chain reject_to_lan {
oifname "br-lan" counter packets 0 bytes 0 jump handle_reject comment "!fw4: reject lan IPv4/IPv6 traffic"
}
chain input_wan {
meta nfproto ipv4 udp dport 68 counter packets 0 bytes 0 accept comment "!fw4: Allow-DHCP-Renew"
icmp type echo-request counter packets 0 bytes 0 accept comment "!fw4: Allow-Ping"
meta nfproto ipv4 meta l4proto igmp counter packets 1 bytes 32 accept comment "!fw4: Allow-IGMP"
meta nfproto ipv6 udp dport 546 counter packets 0 bytes 0 accept comment "!fw4: Allow-DHCPv6"
ip6 saddr fe80::/10 icmpv6 type . icmpv6 code { mld-listener-query . no-route, mld-listener-report . no-route, mld-listener-done . no-route, mld2-listener-report . no-route } counter packets 0 bytes 0 accept comment "!fw4: Allow-MLD"
icmpv6 type { destination-unreachable, time-exceeded, echo-request, echo-reply, nd-router-solicit, nd-router-advert } limit rate 1000/second counter packets 1 bytes 144 accept comment "!fw4: Allow-ICMPv6-Input"
icmpv6 type . icmpv6 code { packet-too-big . no-route, parameter-problem . no-route, nd-neighbor-solicit . no-route, nd-neighbor-advert . no-route, parameter-problem . admin-prohibited } limit rate 1000/second counter packets 3 bytes 208 accept comment "!fw4: Allow-ICMPv6-Input"
jump reject_from_wan
}
chain output_wan {
jump accept_to_wan
}
chain forward_wan {
icmpv6 type { destination-unreachable, time-exceeded, echo-request, echo-reply } limit rate 1000/second counter packets 0 bytes 0 accept comment "!fw4: Allow-ICMPv6-Forward"
icmpv6 type . icmpv6 code { packet-too-big . no-route, parameter-problem . no-route, parameter-problem . admin-prohibited } limit rate 1000/second counter packets 0 bytes 0 accept comment "!fw4: Allow-ICMPv6-Forward"
meta l4proto esp counter packets 0 bytes 0 jump accept_to_lan comment "!fw4: Allow-IPSec-ESP"
udp dport 500 counter packets 0 bytes 0 jump accept_to_lan comment "!fw4: Allow-ISAKMP"
jump accept_to_wan
}
chain accept_to_wan {
oifname "eth0.2" counter packets 7 bytes 750 accept comment "!fw4: accept wan IPv4/IPv6 traffic"
}
chain reject_from_wan {
iifname "eth0.2" counter packets 0 bytes 0 jump handle_reject comment "!fw4: reject wan IPv4/IPv6 traffic"
}
chain input_IPcams {
tcp dport { 53, 67, 68 } counter packets 0 bytes 0 accept comment "!fw4: IPcams DHCP and DNS"
udp dport { 53, 67, 68 } counter packets 0 bytes 0 accept comment "!fw4: IPcams DHCP and DNS"
jump reject_from_IPcams
}
chain output_IPcams {
jump reject_to_IPcams
}
chain forward_IPcams {
jump accept_to_wan comment "!fw4: Accept IPcams to wan forwarding"
jump reject_to_IPcams
}
chain helper_IPcams {
}
chain accept_to_IPcams {
oifname "br-lan-cam" counter packets 0 bytes 0 accept comment "!fw4: accept IPcams IPv4/IPv6 traffic"
}
chain reject_from_IPcams {
iifname "br-lan-cam" counter packets 0 bytes 0 jump handle_reject comment "!fw4: reject IPcams IPv4/IPv6 traffic"
}
chain reject_to_IPcams {
oifname "br-lan-cam" counter packets 0 bytes 0 jump handle_reject comment "!fw4: reject IPcams IPv4/IPv6 traffic"
}
chain dstnat {
type nat hook prerouting priority dstnat; policy accept;
}
chain srcnat {
type nat hook postrouting priority srcnat; policy accept;
oifname "eth0.2" jump srcnat_wan comment "!fw4: Handle wan IPv4/IPv6 srcnat traffic"
}
chain srcnat_wan {
meta nfproto ipv4 masquerade comment "!fw4: Masquerade IPv4 wan traffic"
}
chain raw_prerouting {
type filter hook prerouting priority raw; policy accept;
}
chain raw_output {
type filter hook output priority raw; policy accept;
}
chain mangle_prerouting {
type filter hook prerouting priority mangle; policy accept;
}
chain mangle_postrouting {
type filter hook postrouting priority mangle; policy accept;
}
chain mangle_input {
type filter hook input priority mangle; policy accept;
}
chain mangle_output {
type route hook output priority mangle; policy accept;
}
chain mangle_forward {
type filter hook forward priority mangle; policy accept;
iifname "eth0.2" tcp flags syn tcp option maxseg size set rt mtu comment "!fw4: Zone wan IPv4/IPv6 ingress MTU fixing"
oifname "eth0.2" tcp flags syn tcp option maxseg size set rt mtu comment "!fw4: Zone wan IPv4/IPv6 egress MTU fixing"
}
}
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
5: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.0.100/24 brd 192.168.0.255 scope global br-lan
valid_lft forever preferred_lft forever
7: eth0.2@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.1.25/24 brd 192.168.1.255 scope global eth0.2
valid_lft forever preferred_lft forever
8: br-lan-cam: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 10.0.30.1/24 brd 10.0.30.255 scope global br-lan-cam
valid_lft forever preferred_lft forever
default via 192.168.1.1 dev eth0.2 src 192.168.1.25
10.0.30.0/24 dev br-lan-cam scope link src 10.0.30.1
192.168.0.0/24 dev br-lan scope link src 192.168.0.100
192.168.1.0/24 dev eth0.2 scope link src 192.168.1.25
broadcast 10.0.30.0 dev br-lan-cam table local scope link src 10.0.30.1
local 10.0.30.1 dev br-lan-cam table local scope host src 10.0.30.1
broadcast 10.0.30.255 dev br-lan-cam table local scope link src 10.0.30.1
broadcast 127.0.0.0 dev lo table local scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
broadcast 192.168.0.0 dev br-lan table local scope link src 192.168.0.100
local 192.168.0.100 dev br-lan table local scope host src 192.168.0.100
broadcast 192.168.0.255 dev br-lan table local scope link src 192.168.0.100
broadcast 192.168.1.0 dev eth0.2 table local scope link src 192.168.1.25
local 192.168.1.25 dev eth0.2 table local scope host src 192.168.1.25
broadcast 192.168.1.255 dev eth0.2 table local scope link src 192.168.1.25
0: from all lookup local
32766: from all lookup main
32767: from all lookup default