got a Chinese one to Germany
all I can do is to set it as a WiFi-AP - but no admin (no browser page, Mi-WiFi-App doesnt find/identify it)
another brick in my yard? hopefully not!any idea you can share how to even get Mi-WiFi-App connected?
function xxx()
local XQFunction = require("xiaoqiang.common.XQFunction")
local LuciUtil = require("luci.util")
local result = {
["code"] = 0
}
local ssid = LuciHttp.formvalue("ssid")
local bssid = LuciHttp.formvalue("bssid")
local uid = LuciHttp.formvalue("user_id")
XQLog.log(debug_level, "ssid = "..ssid)
XQLog.log(debug_level, "bssid = "..bssid)
XQLog.log(debug_level, "uid = "..uid)
if XQFunction.isStrNil(ssid)
or XQFunction.isStrNil(bssid)
or XQFunction.isStrNil(uid) then
result.code = 1523
end
if result.code ~= 0 then
result["msg"] = XQErrorUtil.getErrorMessage(result.code)
else
XQFunction.forkExec("connect -s "..ssid.." -b "..bssid.. " -u "..uid)
end
LuciHttp.write_json(result)
end
I think I've found the code to inject
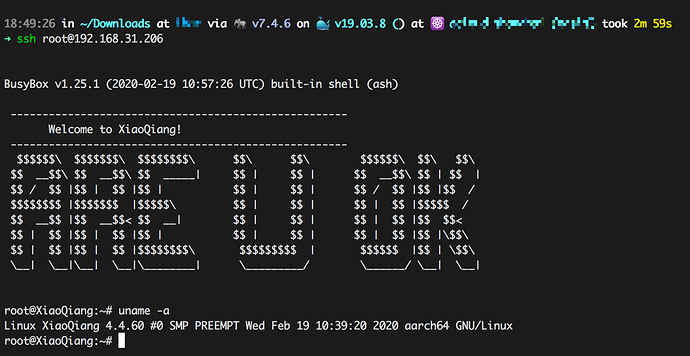
How to get SSH
1.Downgrade to 1.0.17 rom
http://cdn.cnbj1.fds.api.mi-img.com/xiaoqiang/rom/r3600/miwifi_r3600_firmware_5da25_1.0.17.bin
2.Web inject like below
http://192.168.31.1/cgi-bin/luci/;stok=<STOK>/api/misystem/set_config_iotdev?bssid=Xiaomi&user_id=longdike&ssid=-h%3Bnvram%20set%20ssh%5Fen%3D1%3B%20nvram%20commit%3B
3.The following code in /etc/init.d/dropbear needs to be commented out and reboot to get ssh
if [ "$flg_ssh" != "1" -o "$channel" = "release" ]; then return 0 fi
4.The default root password is calculated by SN, and the algorithm is the same as before
That's all, enjoy it
Step 2-3 can use url below to inject:
http://192.168.31.1/cgi-bin/luci/;stok=<STOK>/api/misystem/set_config_iotdev?bssid=Xiaomi&user_id=longdike&ssid=-h; cp /etc/init.d/dropbear /etc/init.d/dropbear_startup_backup; sed -i '/\"\$flg_ssh\"\ \!\=\ \"1\"\ \-o\ \"\$channel\"\ \=\ \"release\"/, 2d' /etc/init.d/dropbear; /etc/init.d/dropbear enable; /etc/init.d/dropbear start;
It backs up /etc/init.d/dropbear to /etc/init.d/dropbear_backup and create a new /etc/init.d/dropbear
Great job @LonGDikE
Hehe, I really should have taken a closer look at the AX3600 ubifs image when someone mentioned that all the lua wasn't obfuscated anymore.
Would have reaaaaally simplified things.
Although I think ath11k is in pretty early stages and openwrt does not pull in the ath11k firmware right now either. I don't even think there's a target for the cpu yet.
Good work. 
Should be a fun platform to work on (assuming the boot chain isn't too locked down).
I wish I had more knowledge what is going on here, to help you guys  But i am only .Net Developer in Microsoft world... In my free time i keep reading of forum and all openwrt stuff, soo maybe someday i can help
But i am only .Net Developer in Microsoft world... In my free time i keep reading of forum and all openwrt stuff, soo maybe someday i can help 
Yes, good. I'm just giving an example. It's OK to delete 3 rows with sed, but it feels dangerous if someone accidentally operate it several times
Yes, at present, only lua script in ROM of 1.0.17 is not obfuscated
I just updated the injection URL, it will deleted 3 lines after the matched line, which is much safer.

Can you modify the previous cmds to fit it? It's a little simple. I don't study linux commands and regularities very much. Hmmm.....
sed -i ":x:N:s/if \[.*\; then\n.*return 0\n.*fi/#tb/;b x" /etc/init.d/dropbear;
That's nice.
Can you check if it has any kind of boot verification?
There is a problem with the cmds I gave. An error will be reported during execution. I want you to help me modify it to be available...
Haha...
could you tell me how to verify if there is any boot verification?
and here is what I got from nvram show(I removed some private information)
root@XiaoQiang:~# nvram show
CountryCode=CN
Router_unconfigured=0
boot_wait=off
bootargs=ubi.mtd=rootfs_1 root=mtd:ubi_rootfs rootfstype=squashfs rootwait
bootcmd=tftp
bootdelay=5
color=101
fdt_high=0x4A400000
flag_boot_rootfs=1
flag_boot_success=1
flag_boot_type=2
flag_flash_permission=1
flag_last_success=1
flag_ota_reboot=0
flag_show_upgrade_info=1
flag_try_sys1_failed=0
flag_try_sys2_failed=0
flash_type=2
fsbootargs=ubi.mtd=rootfs_1 root=mtd:ubi_rootfs rootfstype=squashfs
ipaddr=192.168.31.1
mode=Router
model=R3600
mtddevname=fs
mtddevnum=0
mtdids=nand0=nand0
mtdparts=mtdparts=nand0:0x23c0000@0x2dc0000(fs),
partition=nand0,0
restore_defaults=0
serverip=192.168.31.100
soc_version_major=2
soc_version_minor=0
ssh_en=1
stderr=serial
stdin=serial
stdout=serial
telnet_en=0
uart_en=0
wl0_radio=1
wl0_ssid=Xiaomi_5G
wl1_radio=1
wl1_ssid=Xiaomi
wl2_ssid=Xiaomi_E81A
nv_wan_type=
Does the power supply have a German plug or just an adapter?
Not sure how QC's secure boot works, but try dumping uboot and kernel, see if they have anything like cert or signature attached.
If you order from china it has the chinese plug and the seller usually includes an adapter. If Xiaomi sells it in Europe they will include a european power adapter. It is the same for other devices like the xiaomi desktop lamp.
I think you could post a independent topic about how to open AX3600’s ssh. I know this from Chinese Enshan forum, but it seems hard to find in openwrt forum because it hide so deeply.
It's easy to get the ssh access. But it speed me much time to change the root password. Finally, i managed to change by using ld excute https://askubuntu.com/questions/354342/how-can-i-execute-a-file-without-execute-permissions
Ok, with ssh access now possible, and more and more folks seemingly interested, I am getting in on this early. I've been hunting around on Aliexpress, I can get 2x shipped via UPS Express Saver (7-10 days) for ~US$256. This will give me one for work and one for play. If anybody can point me to where it is cheaper, happy to know. BTW, there is clearly a serial header on board and the pinout is even silk-screened on:
https://www.acwifi.net/wp-content/uploads/2020/03/SAM_6424.jpg