Thanks for the quick response and solution. Waiting for enabled, setting trigger to wan, and rebooting (and refreshing DNS Report) seems to have done the trick! 
Hi, Just wanted to hare some info on google safe search as enabled on adblock.
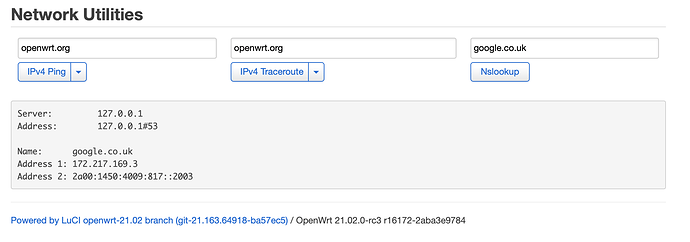
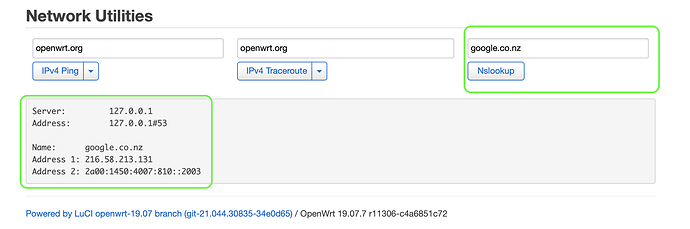
It appears that google.co.uk is not resolved as 216.239.38.120 as expected to the safe search VIP.
I have tried this on both 19.07.7 and 21.02rc3 with the same result. All other regional domains seem to work (at least the ones I have tried).
I may be wrong but it appears that google.co.uk is missing from the adblock SafeSearch list.
Has anyone else come across this ?
Nice finding. Clearly a bug in the dynamic domain preparation/regex for google. I'll fix this and come back to you.
Edit: Will be fixed in 4.1.3-3 with this PR https://github.com/openwrt/packages/pull/16226
As said before, the regex prepare is the culprit ... all 2-dotted domains are broken ... ![]()
Hello, little help needed please 
just to understand if i'm taking the correct way..
I've been using adblock for a while on my "normal" lan, with full success.
I've then created a specific interface for iot clients, with very limited access, but now i'm facing the problem that in any case some cients need internet access to specific domains.
So i think i should act this way:
- create a new dnsmasq instance for the iot network
- create a .jail file with the whitelist of allowed domains
- link the whitelist to the dnsmasq instance
and this should work: i should keep the blacklist approach on the first instance and the whitelist on the second.
It is not clear to me if i can manage this second whitelist with the luci adblock gui, and if so HOW?
is this correct? can this work?
Thanks
Adblock cant do that it will only operate on a single instance or have the same settings on instances that use the same confdir.
On my router I have seperate conf dir for each instance and setup adblock on one of them.
I have set up a cronjob in the second instance to copy adblock files into there along with white and black lists. from a non volitile location.
So I have a kids instance with adblock with aditional blocking of snapchat instragram etc...
The other adults instance only has adblocking without blocking of social media.
Is there a way to only have the manually entered white and blacklists operate on a time scedule ?
I wish to use adblock all the time but I only want to block the aditional white and blacklists at night time to block social media for my children when they should be doing homework could this be implemented?.
it looks like i can suspend or resume but not suspend or resume specific lists
I think I'm missing something. I want to allow a site to show ads... Can I do this with adblock easily ? Whitelisting the site doesn't do anything because the ads are coming from different domains. Do I need to find out what those domains are and whitelist them? Is do-able but more work and would allow those ads to appear on other sites too...
The later, it's not reasonably possible with a DNS (router-) based adblocking solution.
Hi all,
Is there some way (with adblock or even default routing rules?) to block an entire TLD? For example, I'd like to block *.XXX and *.ADULT since none of the lists keep a comprehensive set of these, it seems (and if it's either of those TLDs I know for sure I don't want to resolve it). I know wildcards aren't supported in the blacklist, but it seems like this should be doable somehow.
Thanks!
Adblock seems to be ignoring the blacklist for me
I have an address in the blacklist then i do a query and it shows up on the blacklist but for some reason the domain is not blocked it says OK in the latest statistics for that domain
/etc/init.d/adblock status
::: adblock runtime information
+ adblock_status : enabled
+ adblock_version : 4.1.3
+ blocked_domains : 43022
+ active_sources : adaway, adguard, disconnect, yoyo
+ dns_backend : dnsmasq (-), /tmp/Kids_Lan/
+ run_utils : download: /bin/uclient-fetch, sort: /usr/libexec/sort-coreutils, awk: /bin/busybox
+ run_ifaces : trigger: Wan, report: br-Kids_Lan
+ run_directories : base: /tmp, backup: /tmp/adblock-Backup, report: /tmp/adblock-Report, jail: /tmp
+ run_flags : backup: ✔, flush: ✔, force: ✘, search: ✔, report: ✔, mail: ✘, jail: ✘
+ last_run : reload, 0m 16s, 508/361/356, 30.08.2021 12:31:36
+ system : Wallystech DR40X9, OpenWrt SNAPSHOT r17471-709d7356ba
do i need to add the blacklist in as a source like so?
config source 'blacklist'
option adb_src '/etc/adblock/adblock.blacklist'
option adb_src_rset '/^([[:alnum:]_-]+\.)+[[:alpha:]]+([[:space:]]|$)/{print tolower(\$1)}'
option adb_src_desc 'static local domain blacklist, always deny these domains'
option enabled '1'
To my knowledge, unbound and bind are already capable to block entire TLDs within their zone files - but that is currently not supported by adblock. If you're using bind you could add a "*.xxx" to your rpz file, in unbound just add a local-zone "xxx" - be warned, I haven't tested this up to now. 
I doubt that, black- and whitelist are always enabled in adblock. Doublecheck you DNS config, seems that you're running a quite complex setup with different dnsmasq instances etc.
Just a short & pleasant news on unbound: with this commit https://github.com/NLnetLabs/unbound/commit/924ff7b3730e7af4dc8b8dc08f3373279671acc0 unbound will support the full set of RPZ triggers as well (like bind today). From adblock perspective the RPZ-CLIENT-IP is the interesting part, you can block/allow clients based on their IP address. Currently that's only supported by bind (under Advanced DNS Settings in adblock).
I'll update adblock once this unbound feature has arrived in a forthcoming release. 
Since it sounds like you have some expertise with both, which do you prefer (especially in conjunction with adblock) - bind or unbound?
Adblock supports both and currently the rpz feature is only supported by bind/named. Personally I use unbound on my main router and dnsmasq on my travel router ... almost forgotten the turris device is running with kresd ... 
Im getting blocked domains from the downloaded sources just it is ignoring the blacklist file as far as I can tell.
I'm using dnsmasq with dns http proxy a leak test reveals it is working corectly and requests are forwarded to the localhost 127.0.0.1:5053 to google and cloufare DOH servers
I'm lost as to why it is not working it worked corectly with a single instance and basically all i changed was seperate the conf dir and point adblock to the second instance.
config dnsmasq 'Adults_Dns'
option localise_queries '1'
option rebind_protection '0'
option local '/Adults_Lan/'
option domain 'Adults_Lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/Adults_Lan/dhcp.leases'
option confdir '/tmp/Adults_Lan/dnsmasq.d'
list interface 'Adults_Lan'
option localservice '0'
list server '127.0.0.1#5054'
list server '127.0.0.1#5053'
option noresolv '1'
option doh_backup_noresolv '-1'
list doh_backup_server '8.8.8.8'
config dnsmasq 'Kids_Dns'
option localise_queries '1'
option rebind_protection '0'
option local '/Kids_Lan/'
option domain 'Kids_Lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/Kids_Lan/dhcp.leases'
option confdir '/tmp/Kids_Lan/dnsmasq.d'
list interface 'Kids_Lan'
list notinterface 'loopback'
option localservice '0'
list server '127.0.0.1#5054'
list server '127.0.0.1#5053'
option noresolv '1'
option doh_backup_noresolv '-1'
list doh_backup_server '8.8.8.8'
config dhcp 'Adults_Lan'
option instance 'Adults_Dns'
option interface 'Adults_Lan'
option start '100'
option limit '150'
option leasetime '12h'
option force '1'
config dhcp 'Kids_Lan'
option instance 'Kids_Dns'
option interface 'Kids_Lan'
option start '100'
option leasetime '12h'
option limit '150'
option force '1'
config main 'config'
option update_dnsmasq_config '*'
list force_dns_port '53'
list force_dns_port '853'
option force_dns '0'
config https-dns-proxy
option bootstrap_dns '1.1.1.1,1.0.0.1'
option resolver_url 'https://cloudflare-dns.com/dns-query'
option listen_addr '127.0.0.1'
option listen_port '5054'
option user 'nobody'
option group 'nogroup'
config https-dns-proxy
option bootstrap_dns '8.8.8.8,8.8.4.4'
option resolver_url 'https://dns.google/dns-query'
option listen_addr '127.0.0.1'
option listen_port '5053'
option user 'nobody'
option group 'nogroup'
Sorry, I can't say anything to your config. Just check debug logs and search in the final blocklist for blacklist domains.
can you please tell me, how would you test that?