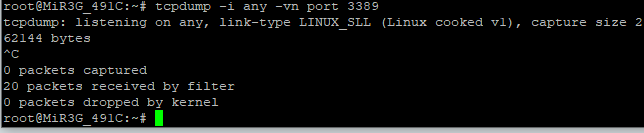
log OpenVPN
Tue Mar 24 23:05:09 2020 us=711755 OpenVPN 2.4.7 mipsel-openwrt-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD]
Tue Mar 24 23:05:09 2020 us=712218 library versions: OpenSSL 1.1.1d 10 Sep 2019, LZO 2.10
Tue Mar 24 23:05:09 2020 us=718927 Diffie-Hellman initialized with 2048 bit key
Tue Mar 24 23:05:09 2020 us=726991 Outgoing Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
Tue Mar 24 23:05:09 2020 us=727566 Outgoing Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
Tue Mar 24 23:05:09 2020 us=727874 Incoming Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
Tue Mar 24 23:05:09 2020 us=728186 Incoming Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
Tue Mar 24 23:05:09 2020 us=728440 TLS-Auth MTU parms [ L:1622 D:1156 EF:94 EB:0 ET:0 EL:3 ]
Tue Mar 24 23:05:09 2020 us=733031 TUN/TAP device tun0 opened
Tue Mar 24 23:05:09 2020 us=734743 TUN/TAP TX queue length set to 100
Tue Mar 24 23:05:09 2020 us=735295 do_ifconfig, tt->did_ifconfig_ipv6_setup=0
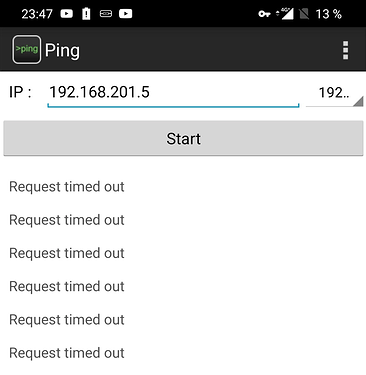
Tue Mar 24 23:05:09 2020 us=735769 /sbin/ifconfig tun0 192.168.201.1 pointopoint 192.168.201.2 mtu 1500
Tue Mar 24 23:05:09 2020 us=753702 /sbin/route add -net 192.168.201.0 netmask 255.255.255.0 gw 192.168.201.2
Tue Mar 24 23:05:09 2020 us=760761 Data Channel MTU parms [ L:1622 D:1450 EF:122 EB:406 ET:0 EL:3 ]
Tue Mar 24 23:05:09 2020 us=761264 Could not determine IPv4/IPv6 protocol. Using AF_INET
Tue Mar 24 23:05:09 2020 us=761641 Socket Buffers: R=[163840->163840] S=[163840->163840]
Tue Mar 24 23:05:09 2020 us=761979 UDPv4 link local (bound): [AF_INET][undef]:1194
Tue Mar 24 23:05:09 2020 us=762300 UDPv4 link remote: [AF_UNSPEC]
Tue Mar 24 23:05:09 2020 us=762723 MULTI: multi_init called, r=256 v=256
Tue Mar 24 23:05:09 2020 us=763659 IFCONFIG POOL: base=192.168.201.4 size=62, ipv6=0
Tue Mar 24 23:05:09 2020 us=764492 Initialization Sequence Completed
Tue Mar 24 23:05:12 2020 us=432914 MULTI: multi_create_instance called
Tue Mar 24 23:05:12 2020 us=433636 xxx.xxx.xxx.xxx:xxxx Re-using SSL/TLS context
Tue Mar 24 23:05:12 2020 us=433899 xxx.xxx.xxx.xxx:xxxx LZO compression initializing
Tue Mar 24 23:05:12 2020 us=434845 xxx.xxx.xxx.xxx:xxxx Control Channel MTU parms [ L:1622 D:1156 EF:94 EB:0 ET:0 EL:3 ]
Tue Mar 24 23:05:12 2020 us=435102 xxx.xxx.xxx.xxx:xxxx Data Channel MTU parms [ L:1622 D:1450 EF:122 EB:406 ET:0 EL:3 ]
Tue Mar 24 23:05:12 2020 us=435546 xxx.xxx.xxx.xxx:xxxx Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1542,tun-mtu 1500,proto UDPv4,comp-lzo,cipher BF-CBC,auth SHA1,keysize 128,key-method 2,tls-server'
Tue Mar 24 23:05:12 2020 us=435730 xxx.xxx.xxx.xxx:xxxx Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1542,tun-mtu 1500,proto UDPv4,comp-lzo,cipher BF-CBC,auth SHA1,keysize 128,key-method 2,tls-client'
Tue Mar 24 23:05:12 2020 us=436090 xxx.xxx.xxx.xxx:xxxx TLS: Initial packet from [AF_INET]xxx.xxx.xxx.xxx:xxxx, sid=061c62d1 2271c9c9
Tue Mar 24 23:05:13 2020 us=644046 xxx.xxx.xxx.xxx:xxxx VERIFY OK: depth=1, C=UK, ST=Yorkshire, O=OG.Infraverse
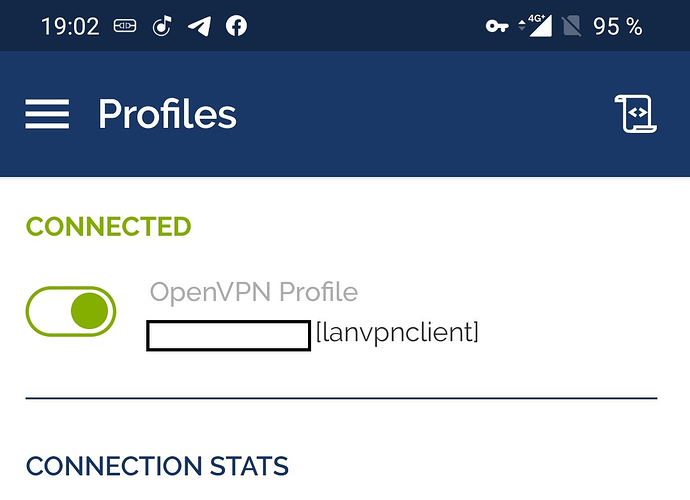
Tue Mar 24 23:05:13 2020 us=659486 xxx.xxx.xxx.xxx:xxxx VERIFY OK: depth=0, CN=lanvpnclient
Tue Mar 24 23:05:13 2020 us=771556 xxx.xxx.xxx.xxx:xxxx peer info: IV_GUI_VER=OC30Android
Tue Mar 24 23:05:13 2020 us=772009 xxx.xxx.xxx.xxx:xxxx peer info: IV_VER=3.git::728733ae:Release
Tue Mar 24 23:05:13 2020 us=772196 xxx.xxx.xxx.xxx:xxxx peer info: IV_PLAT=android
Tue Mar 24 23:05:13 2020 us=772379 xxx.xxx.xxx.xxx:xxxx peer info: IV_NCP=2
Tue Mar 24 23:05:13 2020 us=772564 xxx.xxx.xxx.xxx:xxxx peer info: IV_TCPNL=1
Tue Mar 24 23:05:13 2020 us=772749 xxx.xxx.xxx.xxx:xxxx peer info: IV_PROTO=2
Tue Mar 24 23:05:13 2020 us=772936 xxx.xxx.xxx.xxx:xxxx peer info: IV_LZO_STUB=1
Tue Mar 24 23:05:13 2020 us=773123 xxx.xxx.xxx.xxx:xxxx peer info: IV_COMP_STUB=1
Tue Mar 24 23:05:13 2020 us=773311 xxx.xxx.xxx.xxx:xxxx peer info: IV_COMP_STUBv2=1
Tue Mar 24 23:05:13 2020 us=773584 xxx.xxx.xxx.xxx:xxxx peer info: IV_AUTO_SESS=1
Tue Mar 24 23:05:13 2020 us=773943 xxx.xxx.xxx.xxx:xxxx peer info: IV_BS64DL=1
Tue Mar 24 23:05:13 2020 us=852767 xxx.xxx.xxx.xxx:xxxx Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
Tue Mar 24 23:05:13 2020 us=853311 xxx.xxx.xxx.xxx:xxxx [lanvpnclient] Peer Connection Initiated with [AF_INET]xxx.xxx.xxx.xxx:xxxx
Tue Mar 24 23:05:13 2020 us=853640 xxx.xxx.xxx.xxx:xxxx PUSH: Received control message: 'PUSH_REQUEST'
Tue Mar 24 23:05:13 2020 us=853920 lanvpnclient/xxx.xxx.xxx.xxx:xxxx MULTI_sva: pool returned IPv4=192.168.201.6, IPv6=(Not enabled)
Tue Mar 24 23:05:13 2020 us=854757 lanvpnclient/xxx.xxx.xxx.xxx:xxxx MULTI: Learn: 192.168.201.6 -> lanvpnclient/xxx.xxx.xxx.xxx:xxxx
Tue Mar 24 23:05:13 2020 us=855033 lanvpnclient/xxx.xxx.xxx.xxx:xxxx MULTI: primary virtual IP for lanvpnclient/xxx.xxx.xxx.xxx:xxxx: 192.168.201.6
Tue Mar 24 23:05:14 2020 us=896320 lanvpnclient/xxx.xxx.xxx.xxx:xxxx PUSH: Received control message: 'PUSH_REQUEST'
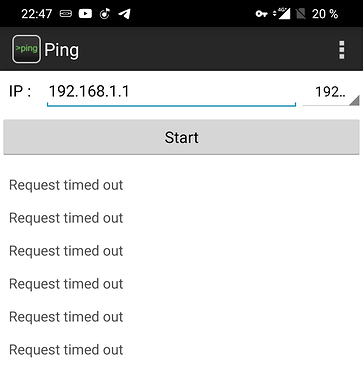
Tue Mar 24 23:05:14 2020 us=897188 lanvpnclient/xxx.xxx.xxx.xxx:xxxx SENT CONTROL [lanvpnclient]: 'PUSH_REPLY,route 192.168.1.0 255.255.255.0,dhcp-option DNS 192.168.1.1,route 192.168.201.0 255.255.255.0,topology net30,ping 10,ping-restart 120,ifconfig 192.168.201.6 192.168.201.5,peer-id 0,cipher AES-256-GCM' (status=1)
Tue Mar 24 23:05:14 2020 us=897425 lanvpnclient/xxx.xxx.xxx.xxx:xxxx Data Channel: using negotiated cipher 'AES-256-GCM'
Tue Mar 24 23:05:14 2020 us=897683 lanvpnclient/xxx.xxx.xxx.xxx:xxxx Data Channel MTU parms [ L:1550 D:1450 EF:50 EB:406 ET:0 EL:3 ]
Tue Mar 24 23:05:14 2020 us=898661 lanvpnclient/xxx.xxx.xxx.xxx:xxxx Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Tue Mar 24 23:05:14 2020 us=898968 lanvpnclient/xxx.xxx.xxx.xxx:xxxx Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Tue Mar 24 23:09:15 2020 us=454174 lanvpnclient/xxx.xxx.xxx.xxx:xxxx [lanvpnclient] Inactivity timeout (--ping-restart), restarting
Tue Mar 24 23:09:15 2020 us=454876 lanvpnclient/xxx.xxx.xxx.xxx:xxxx SIGUSR1[soft,ping-restart] received, client-instance restarting
Tue Mar 24 23:44:42 2020 us=296028 MULTI: multi_create_instance called
Tue Mar 24 23:44:42 2020 us=296707 xxx.xxx.xxx.xxx:xxxx Re-using SSL/TLS context
Tue Mar 24 23:44:42 2020 us=296901 xxx.xxx.xxx.xxx:xxxx LZO compression initializing
Tue Mar 24 23:44:42 2020 us=297536 xxx.xxx.xxx.xxx:xxxx Control Channel MTU parms [ L:1622 D:1156 EF:94 EB:0 ET:0 EL:3 ]
Tue Mar 24 23:44:42 2020 us=297820 xxx.xxx.xxx.xxx:xxxx Data Channel MTU parms [ L:1622 D:1450 EF:122 EB:406 ET:0 EL:3 ]
Tue Mar 24 23:44:42 2020 us=298272 xxx.xxx.xxx.xxx:xxxx Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1542,tun-mtu 1500,proto UDPv4,comp-lzo,cipher BF-CBC,auth SHA1,keysize 128,key-method 2,tls-server'
Tue Mar 24 23:44:42 2020 us=298455 xxx.xxx.xxx.xxx:xxxx Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1542,tun-mtu 1500,proto UDPv4,comp-lzo,cipher BF-CBC,auth SHA1,keysize 128,key-method 2,tls-client'
Tue Mar 24 23:44:42 2020 us=298789 xxx.xxx.xxx.xxx:xxxx TLS: Initial packet from [AF_INET]xxx.xxx.xxx.xxx:xxxx, sid=55ddd73b d424534d
Tue Mar 24 23:44:43 2020 us=438031 xxx.xxx.xxx.xxx:xxxx VERIFY OK: depth=1, C=UK, ST=Yorkshire, O=OG.Infraverse
Tue Mar 24 23:44:43 2020 us=449972 xxx.xxx.xxx.xxx:xxxx VERIFY OK: depth=0, CN=lanvpnclient
Tue Mar 24 23:44:44 2020 us=294280 xxx.xxx.xxx.xxx:xxxx tls-crypt unwrap error: bad packet ID (may be a replay): [ #7 / time = (1585082682) Tue Mar 24 23:44:42 2020 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
Tue Mar 24 23:44:44 2020 us=294514 xxx.xxx.xxx.xxx:xxxx tls-crypt unwrap error: packet replay
Tue Mar 24 23:44:44 2020 us=294735 xxx.xxx.xxx.xxx:xxxx TLS Error: tls-crypt unwrapping failed from [AF_INET]xxx.xxx.xxx.xxx:xxxx
Tue Mar 24 23:44:45 2020 us=295141 xxx.xxx.xxx.xxx:xxxx tls-crypt unwrap error: bad packet ID (may be a replay): [ #7 / time = (1585082682) Tue Mar 24 23:44:42 2020 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
Tue Mar 24 23:44:45 2020 us=295379 xxx.xxx.xxx.xxx:xxxx tls-crypt unwrap error: packet replay
Tue Mar 24 23:44:45 2020 us=295647 xxx.xxx.xxx.xxx:xxxx TLS Error: tls-crypt unwrapping failed from [AF_INET]xxx.xxx.xxx.xxx:xxxx
Tue Mar 24 23:44:45 2020 us=369884 xxx.xxx.xxx.xxx:xxxx peer info: IV_GUI_VER=OC30Android
Tue Mar 24 23:44:45 2020 us=370309 xxx.xxx.xxx.xxx:xxxx peer info: IV_VER=3.git::728733ae:Release
Tue Mar 24 23:44:45 2020 us=370494 xxx.xxx.xxx.xxx:xxxx peer info: IV_PLAT=android
Tue Mar 24 23:44:45 2020 us=370677 xxx.xxx.xxx.xxx:xxxx peer info: IV_NCP=2
Tue Mar 24 23:44:45 2020 us=370861 xxx.xxx.xxx.xxx:xxxx peer info: IV_TCPNL=1
Tue Mar 24 23:44:45 2020 us=371044 xxx.xxx.xxx.xxx:xxxx peer info: IV_PROTO=2
Tue Mar 24 23:44:45 2020 us=371230 xxx.xxx.xxx.xxx:xxxx peer info: IV_LZO_STUB=1
Tue Mar 24 23:44:45 2020 us=371416 xxx.xxx.xxx.xxx:xxxx peer info: IV_COMP_STUB=1
Tue Mar 24 23:44:45 2020 us=371770 xxx.xxx.xxx.xxx:xxxx peer info: IV_COMP_STUBv2=1
Tue Mar 24 23:44:45 2020 us=371968 xxx.xxx.xxx.xxx:xxxx peer info: IV_AUTO_SESS=1
Tue Mar 24 23:44:45 2020 us=372154 xxx.xxx.xxx.xxx:xxxx peer info: IV_BS64DL=1
Tue Mar 24 23:44:45 2020 us=445459 xxx.xxx.xxx.xxx:xxxx Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
Tue Mar 24 23:44:45 2020 us=445988 xxx.xxx.xxx.xxx:xxxx [lanvpnclient] Peer Connection Initiated with [AF_INET]xxx.xxx.xxx.xxx:xxxx
Tue Mar 24 23:44:45 2020 us=446328 lanvpnclient/xxx.xxx.xxx.xxx:xxxx MULTI_sva: pool returned IPv4=192.168.201.6, IPv6=(Not enabled)
Tue Mar 24 23:44:45 2020 us=446969 lanvpnclient/xxx.xxx.xxx.xxx:xxxx MULTI: Learn: 192.168.201.6 -> lanvpnclient/xxx.xxx.xxx.xxx:xxxx
Tue Mar 24 23:44:45 2020 us=447180 lanvpnclient/xxx.xxx.xxx.xxx:xxxx MULTI: primary virtual IP for lanvpnclient/xxx.xxx.xxx.xxx:xxxx: 192.168.201.6
Tue Mar 24 23:45:27 2020 us=522770 MULTI: multi_create_instance called
Tue Mar 24 23:45:27 2020 us=523411 xxx.xxx.xxx.xxx:xxxx Re-using SSL/TLS context
Tue Mar 24 23:45:27 2020 us=523702 xxx.xxx.xxx.xxx:xxxx LZO compression initializing
Tue Mar 24 23:45:27 2020 us=524330 xxx.xxx.xxx.xxx:xxxx Control Channel MTU parms [ L:1622 D:1156 EF:94 EB:0 ET:0 EL:3 ]
Tue Mar 24 23:45:27 2020 us=524622 xxx.xxx.xxx.xxx:xxxx Data Channel MTU parms [ L:1622 D:1450 EF:122 EB:406 ET:0 EL:3 ]
Tue Mar 24 23:45:27 2020 us=525078 xxx.xxx.xxx.xxx:xxxx Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1542,tun-mtu 1500,proto UDPv4,comp-lzo,cipher BF-CBC,auth SHA1,keysize 128,key-method 2,tls-server'
Tue Mar 24 23:45:27 2020 us=525260 xxx.xxx.xxx.xxx:xxxx Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1542,tun-mtu 1500,proto UDPv4,comp-lzo,cipher BF-CBC,auth SHA1,keysize 128,key-method 2,tls-client'
Tue Mar 24 23:45:27 2020 us=525593 xxx.xxx.xxx.xxx:xxxx TLS: Initial packet from [AF_INET]xxx.xxx.xxx.xxx:xxxx, sid=15215704 da37c3e2
Tue Mar 24 23:45:28 2020 us=732794 xxx.xxx.xxx.xxx:xxxx VERIFY OK: depth=1, C=UK, ST=Yorkshire, O=OG.Infraverse
Tue Mar 24 23:45:28 2020 us=744873 xxx.xxx.xxx.xxx:xxxx VERIFY OK: depth=0, CN=lanvpnclient
Tue Mar 24 23:45:28 2020 us=863897 xxx.xxx.xxx.xxx:xxxx peer info: IV_GUI_VER=OC30Android
Tue Mar 24 23:45:28 2020 us=864393 xxx.xxx.xxx.xxx:xxxx peer info: IV_VER=3.git::728733ae:Release
Tue Mar 24 23:45:28 2020 us=864603 xxx.xxx.xxx.xxx:xxxx peer info: IV_PLAT=android
Tue Mar 24 23:45:28 2020 us=864794 xxx.xxx.xxx.xxx:xxxx peer info: IV_NCP=2
Tue Mar 24 23:45:28 2020 us=864995 xxx.xxx.xxx.xxx:xxxx peer info: IV_TCPNL=1
Tue Mar 24 23:45:28 2020 us=865185 xxx.xxx.xxx.xxx:xxxx peer info: IV_PROTO=2
Tue Mar 24 23:45:28 2020 us=865371 xxx.xxx.xxx.xxx:xxxx peer info: IV_LZO_STUB=1
Tue Mar 24 23:45:28 2020 us=865557 xxx.xxx.xxx.xxx:xxxx peer info: IV_COMP_STUB=1
Tue Mar 24 23:45:28 2020 us=865745 xxx.xxx.xxx.xxx:xxxx peer info: IV_COMP_STUBv2=1
Tue Mar 24 23:45:28 2020 us=865932 xxx.xxx.xxx.xxx:xxxx peer info: IV_AUTO_SESS=1
Tue Mar 24 23:45:28 2020 us=866117 xxx.xxx.xxx.xxx:xxxx peer info: IV_BS64DL=1
Tue Mar 24 23:45:28 2020 us=942909 xxx.xxx.xxx.xxx:xxxx Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
Tue Mar 24 23:45:28 2020 us=943433 xxx.xxx.xxx.xxx:xxxx [lanvpnclient] Peer Connection Initiated with [AF_INET]xxx.xxx.xxx.xxx:xxxx
Tue Mar 24 23:45:28 2020 us=943862 xxx.xxx.xxx.xxx:xxxx PUSH: Received control message: 'PUSH_REQUEST'
Tue Mar 24 23:45:28 2020 us=944863 MULTI: new connection by client 'lanvpnclient' will cause previous active sessions by this client to be dropped. Remember to use the --duplicate-cn option if you want multiple clients using the same certificate or username to concurrently connect.
Tue Mar 24 23:45:28 2020 us=945123 MULTI_sva: pool returned IPv4=192.168.201.6, IPv6=(Not enabled)
Tue Mar 24 23:45:28 2020 us=945764 MULTI: Learn: 192.168.201.6 -> lanvpnclient/xxx.xxx.xxx.xxx:xxxx
Tue Mar 24 23:45:28 2020 us=945978 MULTI: primary virtual IP for lanvpnclient/xxx.xxx.xxx.xxx:xxxx: 192.168.201.6
Tue Mar 24 23:45:29 2020 us=941800 lanvpnclient/xxx.xxx.xxx.xxx:xxxx PUSH: Received control message: 'PUSH_REQUEST'
Tue Mar 24 23:45:29 2020 us=942579 lanvpnclient/xxx.xxx.xxx.xxx:xxxx SENT CONTROL [lanvpnclient]: 'PUSH_REPLY,route 192.168.1.0 255.255.255.0,dhcp-option DNS 192.168.1.1,route 192.168.201.0 255.255.255.0,topology net30,ping 10,ping-restart 120,ifconfig 192.168.201.6 192.168.201.5,peer-id 1,cipher AES-256-GCM' (status=1)
Tue Mar 24 23:45:29 2020 us=942780 lanvpnclient/xxx.xxx.xxx.xxx:xxxx Data Channel: using negotiated cipher 'AES-256-GCM'
Tue Mar 24 23:45:29 2020 us=943036 lanvpnclient/xxx.xxx.xxx.xxx:xxxx Data Channel MTU parms [ L:1550 D:1450 EF:50 EB:406 ET:0 EL:3 ]
Tue Mar 24 23:45:29 2020 us=944189 lanvpnclient/xxx.xxx.xxx.xxx:xxxx Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Tue Mar 24 23:45:29 2020 us=944514 lanvpnclient/xxx.xxx.xxx.xxx:xxxx Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Tue Mar 24 23:45:31 2020 us=541951 MULTI: multi_create_instance called
Tue Mar 24 23:45:31 2020 us=542611 xxx.xxx.xxx.xxx:xxxx Re-using SSL/TLS context
Tue Mar 24 23:45:31 2020 us=542803 xxx.xxx.xxx.xxx:xxxx LZO compression initializing
Tue Mar 24 23:45:31 2020 us=543440 xxx.xxx.xxx.xxx:xxxx Control Channel MTU parms [ L:1622 D:1156 EF:94 EB:0 ET:0 EL:3 ]
Tue Mar 24 23:45:31 2020 us=543948 xxx.xxx.xxx.xxx:xxxx Data Channel MTU parms [ L:1622 D:1450 EF:122 EB:406 ET:0 EL:3 ]
Tue Mar 24 23:45:31 2020 us=544456 xxx.xxx.xxx.xxx:xxxx Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1542,tun-mtu 1500,proto UDPv4,comp-lzo,cipher BF-CBC,auth SHA1,keysize 128,key-method 2,tls-server'
Tue Mar 24 23:45:31 2020 us=544672 xxx.xxx.xxx.xxx:xxxx Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1542,tun-mtu 1500,proto UDPv4,comp-lzo,cipher BF-CBC,auth SHA1,keysize 128,key-method 2,tls-client'
Tue Mar 24 23:45:31 2020 us=545026 xxx.xxx.xxx.xxx:xxxx TLS: Initial packet from [AF_INET]xxx.xxx.xxx.xxx:xxxx, sid=66690c5f 979f3abd
Tue Mar 24 23:45:32 2020 us=653079 xxx.xxx.xxx.xxx:xxxx VERIFY OK: depth=1, C=UK, ST=Yorkshire, O=OG.Infraverse
Tue Mar 24 23:45:32 2020 us=665993 xxx.xxx.xxx.xxx:xxxx VERIFY OK: depth=0, CN=lanvpnclient
Tue Mar 24 23:45:32 2020 us=763292 xxx.xxx.xxx.xxx:xxxx peer info: IV_GUI_VER=OC30Android
Tue Mar 24 23:45:32 2020 us=764186 xxx.xxx.xxx.xxx:xxxx peer info: IV_VER=3.git::728733ae:Release
Tue Mar 24 23:45:32 2020 us=764987 xxx.xxx.xxx.xxx:xxxx peer info: IV_PLAT=android
Tue Mar 24 23:45:32 2020 us=765204 xxx.xxx.xxx.xxx:xxxx peer info: IV_NCP=2
Tue Mar 24 23:45:32 2020 us=765388 xxx.xxx.xxx.xxx:xxxx peer info: IV_TCPNL=1
Tue Mar 24 23:45:32 2020 us=765573 xxx.xxx.xxx.xxx:xxxx peer info: IV_PROTO=2
Tue Mar 24 23:45:32 2020 us=765764 xxx.xxx.xxx.xxx:xxxx peer info: IV_LZO_STUB=1
Tue Mar 24 23:45:32 2020 us=765999 xxx.xxx.xxx.xxx:xxxx peer info: IV_COMP_STUB=1
Tue Mar 24 23:45:32 2020 us=766233 xxx.xxx.xxx.xxx:xxxx peer info: IV_COMP_STUBv2=1
Tue Mar 24 23:45:32 2020 us=766475 xxx.xxx.xxx.xxx:xxxx peer info: IV_AUTO_SESS=1
Tue Mar 24 23:45:32 2020 us=766682 xxx.xxx.xxx.xxx:xxxx peer info: IV_BS64DL=1
Tue Mar 24 23:45:32 2020 us=842072 xxx.xxx.xxx.xxx:xxxx Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
Tue Mar 24 23:45:32 2020 us=842607 xxx.xxx.xxx.xxx:xxxx [lanvpnclient] Peer Connection Initiated with [AF_INET]xxx.xxx.xxx.xxx:xxxx
Tue Mar 24 23:45:32 2020 us=843913 MULTI: new connection by client 'lanvpnclient' will cause previous active sessions by this client to be dropped. Remember to use the --duplicate-cn option if you want multiple clients using the same certificate or username to concurrently connect.
Tue Mar 24 23:45:32 2020 us=844305 MULTI_sva: pool returned IPv4=192.168.201.6, IPv6=(Not enabled)
Tue Mar 24 23:45:32 2020 us=845024 MULTI: Learn: 192.168.201.6 -> lanvpnclient/xxx.xxx.xxx.xxx:xxxx
Tue Mar 24 23:45:32 2020 us=845302 MULTI: primary virtual IP for lanvpnclient/xxx.xxx.xxx.xxx:xxxx: 192.168.201.6
Tue Mar 24 23:45:32 2020 us=861155 lanvpnclient/xxx.xxx.xxx.xxx:xxxx PUSH: Received control message: 'PUSH_REQUEST'
Tue Mar 24 23:45:32 2020 us=861871 lanvpnclient/xxx.xxx.xxx.xxx:xxxx SENT CONTROL [lanvpnclient]: 'PUSH_REPLY,route 192.168.1.0 255.255.255.0,dhcp-option DNS 192.168.1.1,route 192.168.201.0 255.255.255.0,topology net30,ping 10,ping-restart 120,ifconfig 192.168.201.6 192.168.201.5,peer-id 0,cipher AES-256-GCM' (status=1)
Tue Mar 24 23:45:32 2020 us=862068 lanvpnclient/xxx.xxx.xxx.xxx:xxxx Data Channel: using negotiated cipher 'AES-256-GCM'
Tue Mar 24 23:45:32 2020 us=862380 lanvpnclient/xxx.xxx.xxx.xxx:xxxx Data Channel MTU parms [ L:1550 D:1450 EF:50 EB:406 ET:0 EL:3 ]
Tue Mar 24 23:45:32 2020 us=863358 lanvpnclient/xxx.xxx.xxx.xxx:xxxx Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Tue Mar 24 23:45:32 2020 us=863729 lanvpnclient/xxx.xxx.xxx.xxx:xxxx Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Tue Mar 24 23:49:33 2020 us=853590 lanvpnclient/xxx.xxx.xxx.xxx:xxxx [lanvpnclient] Inactivity timeout (--ping-restart), restarting
Tue Mar 24 23:49:33 2020 us=854071 lanvpnclient/xxx.xxx.xxx.xxx:xxxx SIGUSR1[soft,ping-restart] received, client-instance restarting
Tue Mar 24 23:51:39 2020 us=740511 MULTI: multi_create_instance called
Tue Mar 24 23:51:39 2020 us=741193 xxx.xxx.xxx.xxx:xxxx Re-using SSL/TLS context
Tue Mar 24 23:51:39 2020 us=741387 xxx.xxx.xxx.xxx:xxxx LZO compression initializing
Tue Mar 24 23:51:39 2020 us=742015 xxx.xxx.xxx.xxx:xxxx Control Channel MTU parms [ L:1622 D:1156 EF:94 EB:0 ET:0 EL:3 ]
Tue Mar 24 23:51:39 2020 us=742306 xxx.xxx.xxx.xxx:xxxx Data Channel MTU parms [ L:1622 D:1450 EF:122 EB:406 ET:0 EL:3 ]
Tue Mar 24 23:51:39 2020 us=743101 xxx.xxx.xxx.xxx:xxxx Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1542,tun-mtu 1500,proto UDPv4,comp-lzo,cipher BF-CBC,auth SHA1,keysize 128,key-method 2,tls-server'
Tue Mar 24 23:51:39 2020 us=743638 xxx.xxx.xxx.xxx:xxxx Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1542,tun-mtu 1500,proto UDPv4,comp-lzo,cipher BF-CBC,auth SHA1,keysize 128,key-method 2,tls-client'
Tue Mar 24 23:51:39 2020 us=744034 xxx.xxx.xxx.xxx:xxxx TLS: Initial packet from [AF_INET]xxx.xxx.xxx.xxx:xxxx, sid=179421d1 3f6e029e
Tue Mar 24 23:51:40 2020 us=699941 xxx.xxx.xxx.xxx:xxxx tls-crypt unwrap error: bad packet ID (may be a replay): [ #1 / time = (1585083100) Tue Mar 24 23:51:40 2020 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
Tue Mar 24 23:52:24 2020 us=922099 xxx.xxx.xxx.xxx:xxxx TLS Error: tls-crypt unwrapping failed from [AF_INET]xxx.xxx.xxx.xxx:xxxx
Tue Mar 24 23:52:27 2020 us=834619 MULTI: multi_create_instance called
Tue Mar 24 23:52:27 2020 us=835364 xxx.xxx.xxx.xxx:xxxx Re-using SSL/TLS context
Tue Mar 24 23:52:27 2020 us=835666 xxx.xxx.xxx.xxx:xxxx LZO compression initializing
Tue Mar 24 23:52:27 2020 us=836312 xxx.xxx.xxx.xxx:xxxx Control Channel MTU parms [ L:1622 D:1156 EF:94 EB:0 ET:0 EL:3 ]
Tue Mar 24 23:52:27 2020 us=836624 xxx.xxx.xxx.xxx:xxxx Data Channel MTU parms [ L:1622 D:1450 EF:122 EB:406 ET:0 EL:3 ]
Tue Mar 24 23:52:27 2020 us=837082 xxx.xxx.xxx.xxx:xxxx Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1542,tun-mtu 1500,proto UDPv4,comp-lzo,cipher BF-CBC,auth SHA1,keysize 128,key-method 2,tls-server'
Tue Mar 24 23:52:27 2020 us=837265 xxx.xxx.xxx.xxx:xxxx Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1542,tun-mtu 1500,proto UDPv4,comp-lzo,cipher BF-CBC,auth SHA1,keysize 128,key-method 2,tls-client'
Tue Mar 24 23:52:27 2020 us=837599 xxx.xxx.xxx.xxx:xxxx TLS: Initial packet from [AF_INET]xxx.xxx.xxx.xxx:xxxx, sid=d6f7e88c b62e8d8f
Tue Mar 24 23:52:28 2020 us=952692 xxx.xxx.xxx.xxx:xxxx tls-crypt unwrap error: bad packet ID (may be a replay): [ #2 / time = (1585083148) Tue Mar 24 23:52:28 2020 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
Tue Mar 24 23:52:28 2020 us=952987 xxx.xxx.xxx.xxx:xxxx tls-crypt unwrap error: packet replay
Tue Mar 24 23:52:28 2020 us=953302 xxx.xxx.xxx.xxx:xxxx TLS Error: tls-crypt unwrapping failed from [AF_INET]xxx.xxx.xxx.xxx:xxxx
Tue Mar 24 23:52:29 2020 us=184205 xxx.xxx.xxx.xxx:xxxx VERIFY OK: depth=1, C=UK, ST=Yorkshire, O=OG.Infraverse
Tue Mar 24 23:52:29 2020 us=196316 xxx.xxx.xxx.xxx:xxxx VERIFY OK: depth=0, CN=lanvpnclient
Tue Mar 24 23:52:29 2020 us=312763 xxx.xxx.xxx.xxx:xxxx peer info: IV_GUI_VER=OC30Android
Tue Mar 24 23:52:29 2020 us=313211 xxx.xxx.xxx.xxx:xxxx peer info: IV_VER=3.git::728733ae:Release
Tue Mar 24 23:52:29 2020 us=313398 xxx.xxx.xxx.xxx:xxxx peer info: IV_PLAT=android
Tue Mar 24 23:52:29 2020 us=313821 xxx.xxx.xxx.xxx:xxxx peer info: IV_NCP=2
Tue Mar 24 23:52:29 2020 us=314027 xxx.xxx.xxx.xxx:xxxx peer info: IV_TCPNL=1
Tue Mar 24 23:52:29 2020 us=314212 xxx.xxx.xxx.xxx:xxxx peer info: IV_PROTO=2
Tue Mar 24 23:52:29 2020 us=314397 xxx.xxx.xxx.xxx:xxxx peer info: IV_LZO_STUB=1
Tue Mar 24 23:52:29 2020 us=314584 xxx.xxx.xxx.xxx:xxxx peer info: IV_COMP_STUB=1
Tue Mar 24 23:52:29 2020 us=314807 xxx.xxx.xxx.xxx:xxxx peer info: IV_COMP_STUBv2=1
Tue Mar 24 23:52:29 2020 us=315017 xxx.xxx.xxx.xxx:xxxx peer info: IV_AUTO_SESS=1
Tue Mar 24 23:52:29 2020 us=315263 xxx.xxx.xxx.xxx:xxxx peer info: IV_BS64DL=1
Tue Mar 24 23:52:29 2020 us=394839 xxx.xxx.xxx.xxx:xxxx Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
Tue Mar 24 23:52:29 2020 us=395406 xxx.xxx.xxx.xxx:xxxx [lanvpnclient] Peer Connection Initiated with [AF_INET]xxx.xxx.xxx.xxx:xxxx
Tue Mar 24 23:52:29 2020 us=395757 lanvpnclient/xxx.xxx.xxx.xxx:xxxx MULTI_sva: pool returned IPv4=192.168.201.6, IPv6=(Not enabled)
Tue Mar 24 23:52:29 2020 us=396398 lanvpnclient/xxx.xxx.xxx.xxx:xxxx MULTI: Learn: 192.168.201.6 -> lanvpnclient/xxx.xxx.xxx.xxx:xxxx
Tue Mar 24 23:52:29 2020 us=396613 lanvpnclient/xxx.xxx.xxx.xxx:xxxx MULTI: primary virtual IP for lanvpnclient/xxx.xxx.xxx.xxx:xxxx: 192.168.201.6
Tue Mar 24 23:52:29 2020 us=397126 lanvpnclient/xxx.xxx.xxx.xxx:xxxx PUSH: Received control message: 'PUSH_REQUEST'
Tue Mar 24 23:52:29 2020 us=397726 lanvpnclient/xxx.xxx.xxx.xxx:xxxx SENT CONTROL [lanvpnclient]: 'PUSH_REPLY,route 192.168.1.0 255.255.255.0,dhcp-option DNS 192.168.1.1,route 192.168.201.0 255.255.255.0,topology net30,ping 10,ping-restart 120,ifconfig 192.168.201.6 192.168.201.5,peer-id 1,cipher AES-256-GCM' (status=1)
Tue Mar 24 23:52:29 2020 us=397954 lanvpnclient/xxx.xxx.xxx.xxx:xxxx Data Channel: using negotiated cipher 'AES-256-GCM'
Tue Mar 24 23:52:29 2020 us=398211 lanvpnclient/xxx.xxx.xxx.xxx:xxxx Data Channel MTU parms [ L:1550 D:1450 EF:50 EB:406 ET:0 EL:3 ]
Tue Mar 24 23:52:29 2020 us=399214 lanvpnclient/xxx.xxx.xxx.xxx:xxxx Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Tue Mar 24 23:52:29 2020 us=399466 lanvpnclient/xxx.xxx.xxx.xxx:xxxx Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Tue Mar 24 23:52:39 2020 us=763561 xxx.xxx.xxx.xxx:xxxx TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Tue Mar 24 23:52:39 2020 us=764029 xxx.xxx.xxx.xxx:xxxx TLS Error: TLS handshake failed
Tue Mar 24 23:52:39 2020 us=764620 xxx.xxx.xxx.xxx:xxxx SIGUSR1[soft,tls-error] received, client-instance restarting