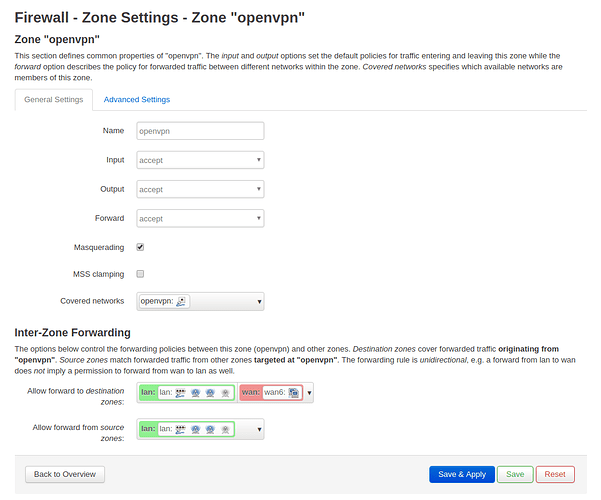
Hello!
I have 2 routers. My office is connecting to my home network via as an OpenVpn.
All works, awesome.
Now the problem that happens is, that on my home network I can ping and access the OpenVpn client from my office client, in my router via ssh, I can ping it:
root@home:~# ping 192.168.17.2
PING 192.168.17.2 (192.168.17.2): 56 data bytes
64 bytes from 192.168.17.2: seq=0 ttl=64 time=20.901 ms
64 bytes from 192.168.17.2: seq=1 ttl=64 time=24.463 ms
64 bytes from 192.168.17.2: seq=2 ttl=64 time=18.000 ms
64 bytes from 192.168.17.2: seq=3 ttl=64 time=16.572 ms
Now what I want to do is to access these OpenVPN clients via my LAN, eg:
patrikx3@bitang:~$ ping 192.168.17.2
PING 192.168.17.2 (192.168.17.2) 56(84) bytes of data.
From 192.168.78.1 icmp_seq=1 Destination Port Unreachable
From 192.168.78.1 icmp_seq=2 Destination Port Unreachable
From 192.168.78.1 icmp_seq=3 Destination Port Unreachable
From 192.168.78.1 icmp_seq=4 Destination Port Unreachable
From 192.168.78.1 icmp_seq=5 Destination Port Unreachable
But I cannot access that OpenVPN client from my LAN, but it would be nice! As I could access my remote office router.
My OpenVPN client subnet is 192.168.17.0/24, and my lan on my home router subnet is 192.168.78.0/24
I tried all kind of routes:
route add -net 192.168.17.0/24 gw 192.168.17.1
route add -net 192.168.17.0/24 gw 192.168.78.1
But not working. Is it although is possible?