Hi @trendy
So I installed Termux on an Android phone.
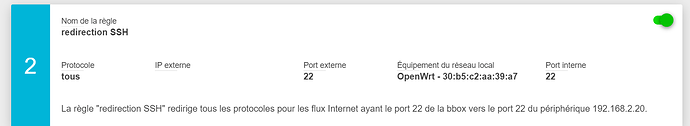
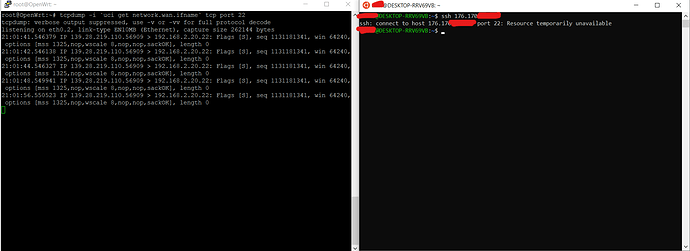
Here is what happens when I ssh the router :
root@OpenWrt:~# tcpdump -i `uci get network.wan.ifname` tcp port 22 -v
tcpdump: listening on eth0.2, link-type EN10MB (Ethernet), capture size 262144 bytes
13:03:40.557554 IP (tos 0x0, ttl 54, id 40122, offset 0, flags [DF], proto TCP (6), length 60)
unn-185.246.211-92.datapacket.com.43984 > 192.168.2.20.22: Flags [S], cksum 0xb6d2 (correct), seq 4174284961, win 65535, options [mss 1326,sackOK,TS val 3 216411 ecr 0,nop,wscale 8], length 0
13:03:41.568798 IP (tos 0x0, ttl 54, id 40123, offset 0, flags [DF], proto TCP (6), length 60)
unn-185.246.211-92.datapacket.com.43984 > 192.168.2.20.22: Flags [S], cksum 0xb5d5 (correct), seq 4174284961, win 65535, options [mss 1326,sackOK,TS val 3 216664 ecr 0,nop,wscale 8], length 0
13:03:43.565855 IP (tos 0x0, ttl 54, id 40124, offset 0, flags [DF], proto TCP (6), length 60)
unn-185.246.211-92.datapacket.com.43984 > 192.168.2.20.22: Flags [S], cksum 0xb3dd (correct), seq 4174284961, win 65535, options [mss 1326,sackOK,TS val 3 217168 ecr 0,nop,wscale 8], length 0
13:03:47.625627 IP (tos 0x0, ttl 54, id 40125, offset 0, flags [DF], proto TCP (6), length 60)
unn-185.246.211-92.datapacket.com.43984 > 192.168.2.20.22: Flags [S], cksum 0xafed (correct), seq 4174284961, win 65535, options [mss 1326,sackOK,TS val 3 218176 ecr 0,nop,wscale 8], length 0
13:03:55.807929 IP (tos 0x0, ttl 54, id 40126, offset 0, flags [DF], proto TCP (6), length 60)
unn-185.246.211-92.datapacket.com.43984 > 192.168.2.20.22: Flags [S], cksum 0xa7ed (correct), seq 4174284961, win 65535, options [mss 1326,sackOK,TS val 3 220224 ecr 0,nop,wscale 8], length 0
13:04:11.939271 IP (tos 0x0, ttl 54, id 40127, offset 0, flags [DF], proto TCP (6), length 60)
unn-185.246.211-92.datapacket.com.43984 > 192.168.2.20.22: Flags [S], cksum 0x982d (correct), seq 4174284961, win 65535, options [mss 1326,sackOK,TS val 3 224256 ecr 0,nop,wscale 8], length 0
13:04:47.297229 IP (tos 0x0, ttl 54, id 40128, offset 0, flags [DF], proto TCP (6), length 60)
unn-185.246.211-92.datapacket.com.43984 > 192.168.2.20.22: Flags [S], cksum 0x76ed (correct), seq 4174284961, win 65535, options [mss 1326,sackOK,TS val 3 232768 ecr 0,nop,wscale 8], length 0
I don't know how to interpret this...
Dropbear doesn't see anything :
root@OpenWrt:~# logread | grep -i dropbear
Sat Feb 29 11:51:24 2020 authpriv.info dropbear[5580]: Exit (root): Keepalive timeout
Sat Feb 29 11:53:43 2020 authpriv.info dropbear[4352]: Exit (root): Keepalive timeout
Sat Feb 29 11:54:03 2020 authpriv.info dropbear[6285]: Exit (root): Keepalive timeout
Sat Feb 29 12:44:50 2020 authpriv.info dropbear[7005]: Child connection from 192.168.1.209:62288
Sat Feb 29 12:44:54 2020 authpriv.notice dropbear[7005]: Password auth succeeded for 'root' from 192.168.1.209:62288
root@OpenWrt:~#