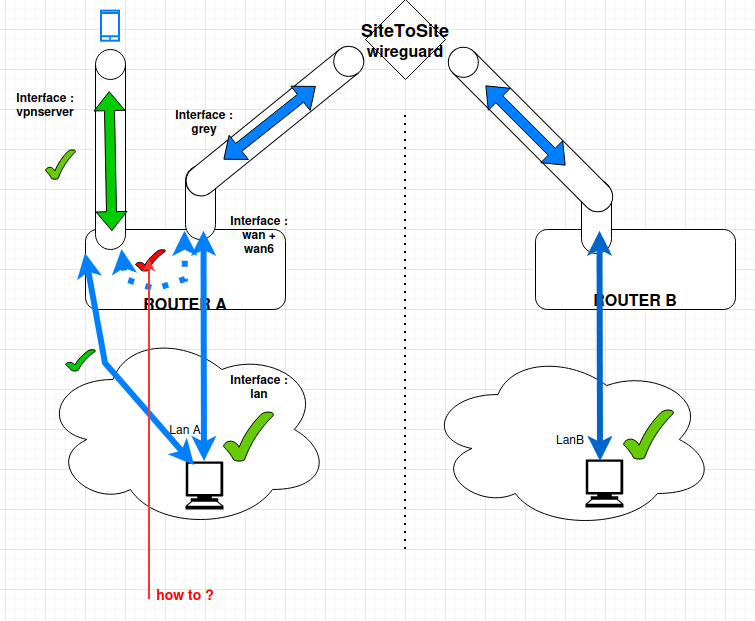
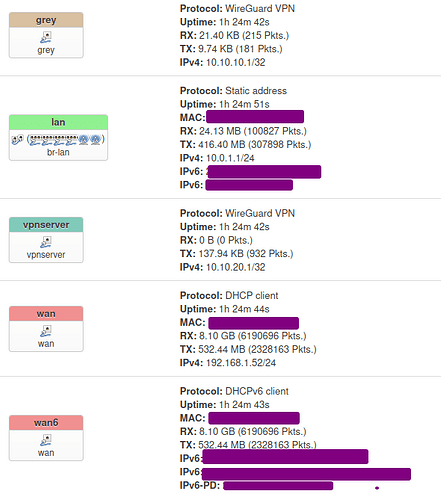
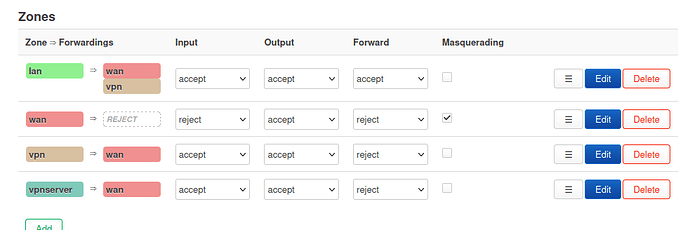
Just an one infortmation:
On site A: i've a box configured lie this:
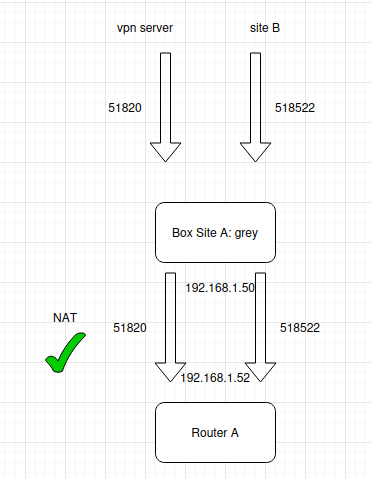
Thanks for your welcomed help! 
~>ubus call system board
{
"kernel": "5.15.134",
"hostname": "grey",
"system": "MediaTek MT7621 ver:1 eco:3",
"model": "Netgear R6220",
"board_name": "netgear,r6220",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.0",
"revision": "r23497-6637af95aa",
"target": "ramips/mt7621",
"description": "OpenWrt 23.05.0 r23497-6637af95aa"
}
}
~> cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdcb:089f:05aa::/48'
option packet_steering '1'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '10.0.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
config interface 'grey'
option proto 'wireguard'
option private_key 'xx...... :) ........xx'
option listen_port '51821'
list addresses '10.10.10.1/32'
config wireguard_grey
option description 'green'
option public_key 'xx...... :) ........xx'
option route_allowed_ips '1'
option endpoint_host 'mydomain.ovh'
option endpoint_port '51822'
option persistent_keepalive '25'
list allowed_ips '10.10.10.0/24'
list allowed_ips '10.0.2.0/24'
config interface 'vpnserver'
option proto 'wireguard'
option private_key 'xx...... :) ........xx'
option listen_port '51820'
list addresses '10.10.20.1/32'
config wireguard_vpnserver 'wgserver'
option public_key 'xx...... :) ........xx'
option preshared_key 'xx...... :) ........xx'
option endpoint_host 'mydomain.ovh'
option persistent_keepalive '25'
option route_allowed_ips '1'
option private_key 'xx...... :) ........xx'
option endpoint_port '51820'
list allowed_ips '10.10.20.2'
list allowed_ips '10.0.2.0/24'
cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone 'lan'
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone 'wan'
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Allow-WireGuard-Inbound'
option src 'wan'
option dest_port '51820'
option target 'ACCEPT'
option src_port '51820'
list src_ip '192.168.1.52'
option dest 'vpnserver'
list dest_ip '10.0.1.1'
list proto 'tcp'
list proto 'udp'
option enabled '0'
config zone
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'grey'
config forwarding
option src 'lan'
option dest 'vpn'
config forwarding
option src 'vpn'
option dest 'wan'
config zone
option name 'vpnserver'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'vpnserver'
config forwarding
option src 'vpnserver'
option dest 'wan'
config redirect
option dest 'vpn'
option target 'DNAT'
option name 'site2site'
option src 'wan'
option src_dport '51821'
option dest_ip '10.0.1.1'
option dest_port '51821'
config redirect
option dest 'vpnserver'
option target 'DNAT'
option name 'allow_vpnserver_inbound'
option src 'wan'
option src_dport '51820'
option dest_port '51820'
option dest_ip '10.0.1.1'
ip route show
10.0.1.0/24 dev br-lan scope link src 10.0.1.1
10.0.2.0/24 dev vpnserver scope link
10.10.10.0/24 dev grey scope link
10.10.20.2 dev vpnserver scope link
176.163.162.239 via 192.168.1.50 dev wan
192.168.1.0/24 dev wan scope link src 192.168.1.52
..... :)..... via 192.168.1.50 dev wan
ip route show table all
default via 192.168.1.50 dev wan src 192.168.1.52
10.0.1.0/24 dev br-lan scope link src 10.0.1.1
10.0.2.0/24 dev vpnserver scope link
10.10.10.0/24 dev grey scope link
10.10.20.2 dev vpnserver scope link
xxxxxxxxxxxxxxx via 192.168.1.50 dev wan
192.168.1.0/24 dev wan scope link src 192.168.1.52
xxxxxxxxxxxxxxx via 192.168.1.50 dev wan
local 10.0.1.1 dev br-lan table local scope host src 10.0.1.1
broadcast 10.0.1.255 dev br-lan table local scope link src 10.0.1.1
local 10.10.10.1 dev grey table local scope host src 10.10.10.1
local 10.10.20.1 dev vpnserver table local scope host src 10.10.20.1
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
local 192.168.1.52 dev wan table local scope host src 192.168.1.52
broadcast 192.168.1.255 dev wan table local scope link src 192.168.1.52
default from xxxxxxxxxxxxxxx via xxxxxxxxxxxxxxx dev wan metric 512
default from xxxxxxxxxxxxxxx via xxxxxxxxxxxxxxx dev wan metric 512
default from xxxxxxxxxxxxxxx via xxxxxxxxxxxxxxx dev wan metric 512
xxxxxxxxxxxxxxx dev wan metric 256
unreachable xxxxxxxxxxxxxxx dev lo metric 2147483647
xxxxxxxxxxxxxxx dev br-lan metric 1024
unreachable xxxxxxxxxxxxxxx dev lo metric 2147483647
xxxxxxxxxxxxxxx dev br-lan metric 1024
unreachable xxxxxxxxxxxxxxx dev lo metric 2147483647
fe80::/64 dev eth0 metric 256
fe80::/64 dev br-lan metric 256
fe80::/64 dev wan metric 256
fe80::/64 dev phy0-ap0 metric 256
fe80::/64 dev phy1-ap0 metric 256
local ::1 dev lo table local metric 0
anycast xxxxxxxxxxxxxxx dev wan table local metric 0
local xxxxxxxxxxxxxxx dev wan table local metric 0
local xxxxxxxxxxxxxxx dev wan table local metric 0
anycast xxxxxxxxxxxxxxx dev br-lan table local metric 0
local xxxxxxxxxxxxxxx dev br-lan table local metric 0
anycast xxxxxxxxxxxxxxx dev br-lan table local metric 0
local xxxxxxxxxxxxxxx dev br-lan table local metric 0
anycast fe80:: dev eth0 table local metric 0
anycast fe80:: dev br-lan table local metric 0
anycast fe80:: dev phy0-ap0 table local metric 0
anycast fe80:: dev wan table local metric 0
anycast fe80:: dev phy1-ap0 table local metric 0
local xxxxxxxxxxxxxxx dev eth0 table local metric 0
local xxxxxxxxxxxxxxx dev br-lan table local metric 0
local xxxxxxxxxxxxxxx dev phy0-ap0 table local metric 0
local xxxxxxxxxxxxxxx dev wan table local metric 0
local xxxxxxxxxxxxxxx dev phy1-ap0 table local metric 0
multicast ff00::/8 dev eth0 table local metric 256
multicast ff00::/8 dev br-lan table local metric 256
multicast ff00::/8 dev wan table local metric 256
multicast ff00::/8 dev phy0-ap0 table local metric 256
multicast ff00::/8 dev phy1-ap0 table local metric 256
multicast ff00::/8 dev grey table local metric 256
multicast ff00::/8 dev vpnserver table local metric 256
ip rule show
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
wg show
interface: grey
public key: xxxxxxxxxxxxxxxxxxxxx
private key: (hidden)
listening port: 51821
peer: xxxxxxxxxxxxxxxxxxxxxx # peer of site B
endpoint: @IP-siteB:51822
allowed ips: 10.10.10.0/24, 10.0.2.0/24
latest handshake: 1 minute, 52 seconds ago
transfer: 33.34 KiB received, 17.57 KiB sent
persistent keepalive: every 25 seconds
interface: vpnserver
public key: xxxxxxxxxxxxxxxxxxxxxxxxxxxx
private key: (hidden)
listening port: 51820
peer: xxxxxxxxxxxxxxxxxxxxxxxx # peer of vpnserver
preshared key: (hidden)
endpoint: @IP-smartphone:6252
allowed ips: 10.10.20.2/32, 10.0.2.0/24
latest handshake: 1 minute, 5 seconds ago
transfer: 198.65 KiB received, 447.09 KiB sent
persistent keepalive: every 25 seconds