Despite doing the research, I'm struggling to get the setup done to do what I want to do. I'd like to be able to access the NVR and IP cams from the 192.168.1.0/24 subnet while blocking outgoing traffic from the NVR and IP cams (10.1.1.0/24 subnet).
Here's my network right now:
192.168.1.1 - Main router with two internet connections (wwan (LTE) and wan (Ubiquity Nano)).
10.1.1.1 - NVR with built-in POE switch
I connected 192.168.1.2 to the NVR (10.1.1.1) via ethernet. I created a VLAN for that port cwith the CPU tagged and the connected port untagged. Created an interface (CCTV) for the VLAN:
Static IP: 10.1.1.222
Proceeded to create what I thought were the proper routes and firewall to no success. I cannot ping the NVR nor any of the cameras from my laptop nor from the router itself.
I've read tonnes of threads and tried different things but I've gotten nowhere.
What am I missing?
trendy
September 23, 2023, 9:44pm
2
Please run the following commands (copy-paste the whole block) and paste the output here, using the "Preformatted text </> " button:
ubus call system board; \
uci export network; \
uci export dhcp; uci export firewall; \
ip -4 addr ; ip -4 ro li tab all ; ip -4 ru
1 Like
Here we have it all:
"kernel": "5.10.176",
"hostname": "CCTV",
"system": "MediaTek MT7628AN ver:1 eco:2",
"model": "TP-Link TL-MR3420 v5",
"board_name": "tplink,tl-mr3420-v5",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "22.03.5",
"revision": "r20134-5f15225c1e",
"target": "ramips/mt76x8",
"description": "OpenWrt 22.03.5 r20134-5f15225c1e"
}
}
package network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd6d:6df6:332f::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.1.2'
option gateway '192.168.1.1'
list dns '192.168.1.1'
config device
option name 'eth0.2'
option macaddr '*redacted*'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '6t 1 2 3'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '6t 0'
config interface 'wwan'
option proto 'static'
option ipaddr '192.168.1.2'
option netmask '255.255.255.0'
option gateway '192.168.1.1'
config switch_vlan
option device 'switch0'
option ports '6t 4'
option vlan '3'
option description 'CCTV'
config interface 'CCTV'
option proto 'static'
option device 'eth0.3'
option gateway '10.1.1.1'
option broadcast '10.1.1.225'
list ipaddr '10.1.1.222/24'
config route
option interface 'CCTV'
option target '10.1.1.0/24'
option gateway '10.1.1.1'
config rule
option src '192.168.1.0/24'
option dest '10.1.1.0/24'
option in 'lan'
option out 'CCTV'
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'wwan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option targ68.1.255 dev br-lan table local scope link src 192.168.1.2
0: from all lookup local
1: from 192.168.1.0/24 to 10.1.1.0/24 iif br-lan lookup unspec broadcast
32766: from all lookup main
32767: from all lookup defaultet 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'CCTV'
option output 'ACCEPT'
option forward 'REJECT'
list network 'CCTV'
option input 'REJECT'
config forwarding
option src 'lan'
option dest 'CCTV'
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
5: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.1.2/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
11: eth0.3@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 10.1.1.222/24 brd 10.1.1.225 scope global eth0.3
valid_lft forever preferred_lft forever
10.1.1.0/24 via 10.1.1.1 dev eth0.3
192.168.1.0/24 dev br-lan scope link src 192.168.1.2
broadcast 10.1.1.0 dev eth0.3 table local scope link src 10.1.1.222
local 10.1.1.222 dev eth0.3 table local scope host src 10.1.1.222
broadcast 10.1.1.225 dev eth0.3 table local scope link src 10.1.1.222
broadcast 10.1.1.255 dev eth0.3 table local scope link src 10.1.1.222
broadcast 127.0.0.0 dev lo table local scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
broadcast 192.168.1.0 dev br-lan table local scope link src 192.168.1.2
local 192.168.1.2 dev br-lan table local scope host src 192.168.1.2
broadcast 192.168.1.255 dev br-lan table local scope link src 192.168.1.2
0: from all lookup local
1: from 192.168.1.0/24 to 10.1.1.0/24 iif br-lan lookup unspec broadcast
32766: from all lookup main
32767: from all lookup default
trendy
September 23, 2023, 10:42pm
4
Remove this one.
Remove these from CCTV interface.
Remove the route.
Remove the rule.
2 Likes
All done. Still not able to ping nor access in any way the 10.1.1.0/24 subnet
I found this thread: Trying to bridge two subnets on the same interface (no separate LAN interfaces)
Unchecked 'use default route' on the CCTV interface settings. Also followed the same settings on the firewall as outline in the thread.
I can now ping the 10.1.1.0/24 subnet from the router!
However, I can't ping nor access the subnet from my laptop. When I do a traceroute, the first hop is to 192.168.1.1 (main router with internet connections) and then the default route of 192.168.5.1 (Nano connection).
trendy
September 24, 2023, 7:39am
7
I had already mentioned to remove the gateway from the CCTV interface.troubleshooting commands to see where we are.
ubus call system board; \
uci export network; \
uci export dhcp; uci export firewall; \
ip -4 addr ; ip -4 ro li tab all ; ip -4 ru
Ping results from 192.168.1.2:
PING 10.1.1.12 (10.1.1.12): 56 data bytes
64 bytes from 10.1.1.12: seq=0 ttl=64 time=12.976 ms
64 bytes from 10.1.1.12: seq=1 ttl=64 time=6.225 ms
64 bytes from 10.1.1.12: seq=2 ttl=64 time=5.891 ms
64 bytes from 10.1.1.12: seq=3 ttl=64 time=5.721 ms
64 bytes from 10.1.1.12: seq=4 ttl=64 time=5.969 ms
--- 10.1.1.12 ping statistics ---
5 packets transmitted, 5 packets received, 0% packet loss
round-trip min/avg/max = 5.721/7.356/12.976 ms
Ping results from my laptop (192.168.1.100):
PING 192.168.1.12 (192.168.1.12) 56(84) bytes of data.
From 192.168.1.50 icmp_seq=1 Destination Host Unreachable
From 192.168.1.50 icmp_seq=2 Destination Host Unreachable
From 192.168.1.50 icmp_seq=3 Destination Host Unreachable
^C
--- 192.168.1.12 ping statistics ---
4 packets transmitted, 0 received, +3 errors, 100% packet loss, time 3049ms
pipe 4
Ping results from 192.168.1.1:
PING 10.1.1.12 (10.1.1.12): 56 data bytes
--- 10.1.1.12 ping statistics ---
5 packets transmitted, 0 packets received, 100% packet loss
trendy
September 25, 2023, 5:38am
9
You didn't post the output of the commands.
My apologies:
"kernel": "5.10.176",
"hostname": "CCTV",
"system": "MediaTek MT7628AN ver:1 eco:2",
"model": "TP-Link TL-MR3420 v5",
"board_name": "tplink,tl-mr3420-v5",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "22.03.5",
"revision": "r20134-5f15225c1e",
"target": "ramips/mt76x8",
"description": "OpenWrt 22.03.5 r20134-5f15225c1e"
}
}
uci: Entry not found
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'CCTV'
option output 'ACCEPT'
list network 'CCTV'
option input 'ACCEPT'
option forward 'ACCEPT'
config forwarding
option src 'lan'
option dest 'CCTV'
config rule
list proto 'all'
option src 'lan'
option dest 'CCTV'
list dest_ip '10.1.1.0/24'
option target 'ACCEPT'
config forwarding
option src 'CCTV'
option dest 'lan'
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
5: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.1.2/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
13: eth0.3@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 10.1.1.222/24 brd 10.1.1.255 scope global eth0.3
valid_lft forever preferred_lft forever
10.1.1.0/24 dev eth0.3 scope link src 10.1.1.222
192.168.1.0/24 dev br-lan scope link src 192.168.1.2
broadcast 10.1.1.0 dev eth0.3 table local scope link src 10.1.1.222
local 10.1.1.222 dev eth0.3 table local scope host src 10.1.1.222
broadcast 10.1.1.255 dev eth0.3 table local scope link src 10.1.1.222
broadcast 127.0.0.0 dev lo table local scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
broadcast 192.168.1.0 dev br-lan table local scope link src 192.168.1.2
local 192.168.1.2 dev br-lan table local scope host src 192.168.1.2
broadcast 192.168.1.255 dev br-lan table local scope link src 192.168.1.2
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
trendy
September 25, 2023, 12:34pm
11
The uci export network is missing.
You don't need the rule since you have the forwarding.
Do you need this?
Also I notice the lack of gateway from the routing table. Given that both interfaces had some gateway in the previous post your problem is probably lack of routes in some gateway or firewall drop due to asymmetric routing.
uci export network:
package network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd6d:6df6:332f::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.1.2'
option gateway '192.168.1.1'
list dns '192.168.1.1'
option defaultroute '0'
config device
option name 'eth0.2'
option macaddr '70:4f:57:f2:eb:a3'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '6t 1 2 3'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '6t 0'
config switch_vlan
option device 'switch0'
option ports '6t 4'
option vlan '3'
option description 'CCTV'
config interface 'CCTV'
option proto 'static'
option device 'eth0.3'
list ipaddr '10.1.1.222/24'
option defaultroute '0'
option force_link '0'
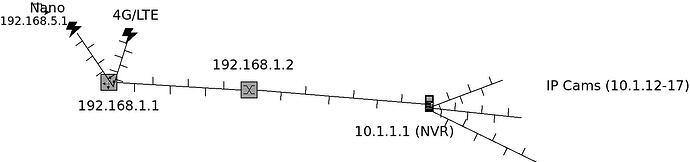
Here's the topology. Access to and from both the Nano and 4G connections are fine on the 192.168.1.0/24 subnet. It's simply trying to get access to the 10.1.1.0/24 sub from 192.168.1.0/24
trendy
September 25, 2023, 1:10pm
13
Do the devices in 10.1.1.0/24 have a static route towards 192.168.1.0/24 via 10.1.1.222? Or a default gateway via 10.1.1.222?
I set a static route on 10.1.1.1 (the NVR) to 10.1.1.222 and added a static route to 10.1.1.0/24 to 192.168.1.2 on my laptop.
The traceroute to 10.1.1.12 from my laptop:
traceroute to 10.1.1.12 (10.1.1.12), 30 hops max, 60 byte packets
1 192.168.1.2 (192.168.1.2) 4.148 ms 4.031 ms 3.963 ms
2 * * *
3 * * *
4 * * *
5 * * *
6 * * *
7 *^C
Here's my network configuration on 192.168.1.2 currently:
"kernel": "5.10.176",
"hostname": "CCTV",
"system": "MediaTek MT7628AN ver:1 eco:2",
"model": "TP-Link TL-MR3420 v5",
"board_name": "tplink,tl-mr3420-v5",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "22.03.5",
"revision": "r20134-5f15225c1e",
"target": "ramips/mt76x8",
"description": "OpenWrt 22.03.5 r20134-5f15225c1e"
}
}
package network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd6d:6df6:332f::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.1.2'
option gateway '192.168.1.1'
list dns '192.168.1.1'
config device
option name 'eth0.2'
option macaddr '70:4f:57:f2:eb:a3'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '6t 1 2 3'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '6t 0'
config switch_vlan
option device 'switch0'
option ports '6t 4'
option vlan '3'
option description 'CCTV'
config interface 'CCTV'
option proto 'static'
option device 'eth0.3'
list ipaddr '10.1.1.222/24'
option defaultroute '0'
option force_link '0'
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'CCTV'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'CCTV'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'CCTV'
config forwarding
option src 'lan'
option dest 'CCTV'
config forwarding
option src 'CCTV'
option dest 'lan'
config forwarding
option src 'lan'
option dest 'wan'
config forwarding
option src 'wan'
option dest 'lan'
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
5: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.1.2/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
15: eth0.3@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 10.1.1.222/24 brd 10.1.1.255 scope global eth0.3
valid_lft forever preferred_lft forever
default via 192.168.1.1 dev br-lan
10.1.1.0/24 dev eth0.3 scope link src 10.1.1.222
192.168.1.0/24 dev br-lan scope link src 192.168.1.2
broadcast 10.1.1.0 dev eth0.3 table local scope link src 10.1.1.222
local 10.1.1.222 dev eth0.3 table local scope host src 10.1.1.222
broadcast 10.1.1.255 dev eth0.3 table local scope link src 10.1.1.222
broadcast 127.0.0.0 dev lo table local scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
broadcast 192.168.1.0 dev br-lan table local scope link src 192.168.1.2
local 192.168.1.2 dev br-lan table local scope host src 192.168.1.2
broadcast 192.168.1.255 dev br-lan table local scope link src 192.168.1.2
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
Thanks again for all your help. I've never tried to manage different subnets before and this is definitely a skull breaker for me!
I was just able to log into 10.1.1.1! I can't access any of the cameras (10.1.1.2-17) yet.
I just changed the default gateway on one camera to 10.1.1.222 and was able to login from my laptop.
This was a much simpler solution than I thought. Just a matter of changing the default gateway on each device.
Thank you so much!
trendy
September 25, 2023, 5:09pm
17
That's right, the devices need to know how to reach networks which are outside of their local network, and that is where the gateway steps in.
1 Like
Of course. Makes sense now. I was banging my head against the wall with the router setup.
Thank you!
1 Like
system
October 5, 2023, 6:45pm
19
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.