cla
May 25, 2022, 2:11pm
1
Hello, I have OpenWRT working as a router and connected as a client to my ISP router.
I can access devices in 192.168.1.x from 192.168.2.x but not the other way around.
I have added a static route on my ISP router so to forward traffic for 192.168.2.x to 192.168.1.4 but no luck. Any help? Thanks!
faser
May 25, 2022, 2:20pm
2
cla:
Any help? Thanks!
You would need to do port forwarding on the Openwrt router as the connection to your ISP router is considered as WAN and no ports are open on the WAN port.
cla
May 25, 2022, 2:29pm
3
Thanks for the quick reply!
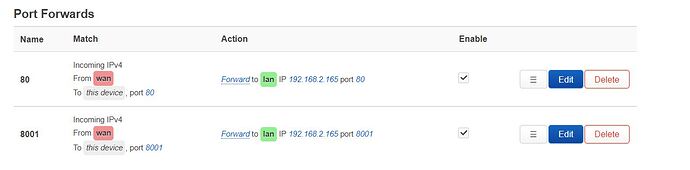
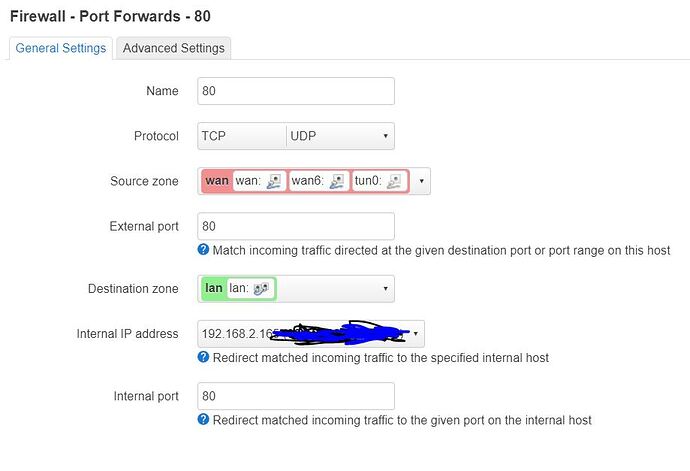
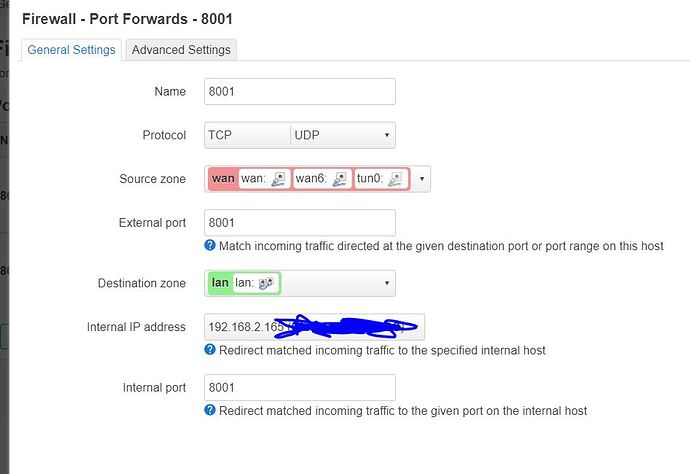
I have added port forwarding as shown below. The ip of the device i want to access is 192.168.2.165 and it listens on port 80 and 8001. Still no luck.
faser
May 25, 2022, 2:36pm
4
cla:
Still no luck.
Show the detail of the rule when you click Edit.
Static route is not needed. Hosts in 192.168.1.0/24 need to contact directly .1.4:80 or :8001iptables-save -c -t nat | grep 80
Do yu have a need for multiple hosts on 192.168.2.0/24 to be reachable in part or in whole from hosts on the upstream 192.168.1.0/24 network?
If no -- if this is the only system that needs to be accessed from the upstream network -- the port forwards are fine, but you would access the host via the WAN IP of the OpenWrt router (192.168.1.4)
If yes, you need to disable masquerading on your OpenWrt's wan firewall zone and then create traffic rules accordingly (not port forwards). Further...
Just make sure your static route is defined properly... depending on the interface, the details might be different, but the broad strokes should look like 192.168.2.0/24 via 192.168.1.4
cla
May 25, 2022, 3:29pm
7
Thank you all for your help!
I cannot access .1.4:80 from an ip .1.x.
You have a VPN running on that OpenWrt router? That likely explains the issue. Try turning off the VPN and see what happens.
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
cla
May 26, 2022, 7:22am
11
Here are the config files. Thanks a lot!
DHCP
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
option logqueries '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option mac 'XX:XX:XX:XX:XX:XX'
option ip '192.168.2.165'
FIREWALL
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
option output 'ACCEPT'
option forward 'REJECT'
option mtu_fix '1'
list device 'tun0'
list network 'wan'
list network 'wan6'
list network 'tun0'
option input 'REJECT'
option masq '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
config redirect
option dest 'lan'
option target 'DNAT'
option src 'wan'
option src_dport '80'
option dest_ip '192.168.2.165'
option dest_port '80'
option name '80'
config redirect
option dest 'lan'
option target 'DNAT'
option src 'wan'
option src_dport '8001'
option dest_ip '192.168.2.165'
option dest_port '8001'
option name '8001'
config forwarding
option src 'wan'
option dest 'lan'
NETWORK
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'XXXX:XXXX:XXXX::/48'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config device
option name 'eth0'
option macaddr 'XX:XX:XX:XX:XX:XX'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.2.1'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
option blinkrate '2'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 1 2 3 5'
config switch_port
option device 'switch0'
option port '1'
option led '6'
config switch_port
option device 'switch0'
option port '2'
option led '9'
config switch_port
option device 'switch0'
option port '5'
option led '2'
config interface 'tun0'
option proto 'none'
option auto '0'
option device 'tun0'
WIRELESS
config wifi-device 'radio0'
option type 'mac80211'
option path 'pci0000:00/0000:00:11.0'
option band '2g'
option htmode 'HT20'
option channel 'auto'
option cell_density '0'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option encryption 'sae-mixed'
option key 'XXXXXXXXXXXXXXXXXXXXXX'
option ssid 'XXXXXXXXXXX'
config wifi-device 'radio1'
option type 'mac80211'
option path 'pci0000:00/0000:00:12.0'
option channel '36'
option band '5g'
option htmode 'HT20'
option disabled '1'
option cell_density '0'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option encryption 'none'
option disabled '1'
option ssid 'XXXXXXXXXX'
Lucky1
May 26, 2022, 7:56am
12
what is the outcome you want ?
cla
May 26, 2022, 8:36am
13
Hi Lucky,
I would like to keep two subnets. I just want one device in subnet .2.x to be reachable from subnet .1.x.
Thanks for your help!
trendy
May 26, 2022, 9:03am
14
Verify the rules with iptables-save -c -t nat | grep 80
cla
May 26, 2022, 9:11am
15
Here it is:
root@OpenWrt:~# iptables-save -c -t nat | grep 80
[0:0] -A zone_lan_postrouting -s 192.168.2.0/24 -d 192.168.2.165/32 -p tcp -m tcp --dport 80 -m comment --comment "!fw3: 80 (reflection)" -j SNAT --to-source 192.168.2.1
[0:0] -A zone_lan_postrouting -s 192.168.2.0/24 -d 192.168.2.165/32 -p udp -m udp --dport 80 -m comment --comment "!fw3: 80 (reflection)" -j SNAT --to-source 192.168.2.1
[0:0] -A zone_lan_postrouting -s 192.168.2.0/24 -d 192.168.2.165/32 -p tcp -m tcp --dport 8001 -m comment --comment "!fw3: 8001 (reflection)" -j SNAT --to-source 192.168.2.1
[0:0] -A zone_lan_postrouting -s 192.168.2.0/24 -d 192.168.2.165/32 -p udp -m udp --dport 8001 -m comment --comment "!fw3: 8001 (reflection)" -j SNAT --to-source 192.168.2.1
[0:0] -A zone_lan_prerouting -s 192.168.2.0/24 -d 192.168.1.4/32 -p tcp -m tcp --dport 80 -m comment --comment "!fw3: 80 (reflection)" -j DNAT --to-destination 192.168.2.165:80
[0:0] -A zone_lan_prerouting -s 192.168.2.0/24 -d 192.168.1.4/32 -p udp -m udp --dport 80 -m comment --comment "!fw3: 80 (reflection)" -j DNAT --to-destination 192.168.2.165:80
[0:0] -A zone_lan_prerouting -s 192.168.2.0/24 -d 192.168.1.4/32 -p tcp -m tcp --dport 8001 -m comment --comment "!fw3: 8001 (reflection)" -j DNAT --to-destination 192.168.2.165:8001
[0:0] -A zone_lan_prerouting -s 192.168.2.0/24 -d 192.168.1.4/32 -p udp -m udp --dport 8001 -m comment --comment "!fw3: 8001 (reflection)" -j DNAT --to-destination 192.168.2.165:8001
[7:364] -A zone_wan_prerouting -p tcp -m tcp --dport 80 -m comment --comment "!fw3: 80" -j DNAT --to-destination 192.168.2.165:80
[0:0] -A zone_wan_prerouting -p udp -m udp --dport 80 -m comment --comment "!fw3: 80" -j DNAT --to-destination 192.168.2.165:80
[0:0] -A zone_wan_prerouting -p tcp -m tcp --dport 8001 -m comment --comment "!fw3: 8001" -j DNAT --to-destination 192.168.2.165:8001
[0:0] -A zone_wan_prerouting -p udp -m udp --dport 8001 -m comment --comment "!fw3: 8001" -j DNAT --to-destination 192.168.2.165:8001
root@OpenWrt:~#
any clue? thanks!
trendy
May 26, 2022, 9:40am
16
You can exclude the UDP from the http protocol, it works only with TCP.
The host .2.165 has proper gateway and is not using any vpn.
The server listening on port 80 (and 8001) is allowing requests from non-local networks.
The previous one also applies to the firewall of the host .2.165
cla
May 26, 2022, 12:31pm
17
i have checked 1,2, and 3 and still no luck
trendy
May 26, 2022, 2:06pm
18
If the .2.165 is a linux server we can run a tcpdump to verify it receives the packets. If it is a windows server, there is wireshark for that.
mk24
May 26, 2022, 2:10pm
19
When you do symmetric routing by installing a route to .2.0 in the ISP router, turn masquerade off on wan of the secondary router. Also you will need to permit forwarding from wan to lan, either with a global config forward or individual rules.
Lucky1
May 27, 2022, 11:57pm
20
that's easy