The above window is route lists. I've added the mentioned route in the last row.
Actually I had to add first source NAT because without that I couldn't connect to OpenWrt LUCI web page through MT devices.
Told you I wasn't a Mikrotik expert. However, what's the next hop for the 192.168.9.0/24 route?
It is ether2 port on MT routerboard which is connected to OpenWrt router
Again with the caveat that I'm not a Mikrotik expert, I suspect you need an IP address as the next hop, not an interface.
Yes, some static routes work with interfaces as their next hops, but I suspect that this one might not.
If you can get to it, it might be beneficial to examine the routing table on the Mikrotik device. That may also help confirm where traffic is likely to go.
That's down to the lack of working symmetric routing. SNAT isn't always necessary, but it can be a handy quick fix for situations like this.
The only NAT rule that should be in the Mikrotik is to NAT anything that goes out (i.e. all local Internet usage) to the LTE modem. Source NAT is not the answer here as it precludes any incoming connections, and the use case requires support of incoming connections from the road warrior to the Mikrotik's LAN.
Go to IP-->Routes click Add New and fill out only the two required fields, Dst. IP (192.168.9.0/24) and Gateway (192.168.1.1).
Thanks. Now everything from OpenWrt to MT router is working. However, on the opposite direction nothing works. (I have a wg server on MT router as well and I cannot connect to MT or OpenWrt when I am connected to MT wg server.)
Here is MT config:
# jun/28/2023 14:20:16 by RouterOS 7.9.2
/interface wireguard
add listen-port=6060 mtu=1420 name=wg1
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/ip hotspot profile
set [ find default=yes ] html-directory=hotspot
/ip pool
add name=dhcp_pool0 ranges=10.0.0.2-10.0.0.254
/ip dhcp-server
add address-pool=dhcp_pool0 interface=ether3 name=dhcp1
/interface wireguard peers
add allowed-address=192.168.5.2/32 interface=wg1 public-key=\
"XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX"
/ip address
add address=10.0.0.1/24 interface=ether3 network=10.0.0.0
add address=192.168.5.1/24 interface=wg1 network=192.168.5.0
/ip dhcp-client
add add-default-route=no interface=ether2 use-peer-dns=no use-peer-ntp=no
add interface=ether1 use-peer-dns=no use-peer-ntp=no
/ip dhcp-server network
add address=10.0.0.0/24 gateway=10.0.0.1
/ip dns
set allow-remote-requests=yes servers=1.1.1.1,8.8.8.8
/ip firewall nat
add action=masquerade chain=srcnat dst-address=192.168.1.0/24 out-interface=\
ether2
add action=masquerade chain=srcnat out-interface=ether1
/ip route
add disabled=no distance=1 dst-address=192.168.9.0/24 gateway=192.168.1.1 \
pref-src="" routing-table=main scope=30 suppress-hw-offload=no \
target-scope=10
add disabled=no distance=2 dst-address=0.0.0.0/0 gateway=192.168.2.1 \
pref-src="" routing-table=main scope=30 suppress-hw-offload=no \
target-scope=10
add disabled=no distance=1 dst-address=10.0.100.0/24 gateway=192.168.1.1 \
pref-src="" routing-table=main scope=30 suppress-hw-offload=no \
target-scope=10
I finally pulled my finger out and installed CHR as a guest on my ESXi box, and licensed it.
Now to learn how Mikrotik does stuff.
I'm going to bow out here as more and more stuff keeps appearing (what is the 10.0.0.0/24 network for?) and it's all Mikrotik which is outside the scope of this forum.
As mentioned before, this needs to be taken out. The general principle of symmetric routing still applies-- it's all destination based, and every route out of a network needs a return route back in.
10.0.0.0/24 is MT ether3 dhcp server which is connected to my laptop.
I can remove that. however, by removing that NAT entry, I will not be able to connect to OpenWrt or its connected devices from MT router.
So we need to work out what the proper alternative to that would be. I reckon it should be possible, so I'm going to have a stab at it this evening... subject to your being able to provide some details.
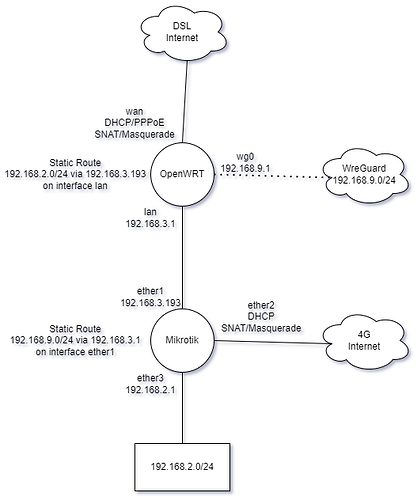
As you've been making changes to your devices, it would help greatly if you can provide a snapshot of what your network looks like right now. Ideally, this would be both a diagram and text configuration. The diagram would show what you believe your network looks like, or should look like. The text configuration would show what your network actually does look like.
As I advertise in my profile, diagrams.net is excellent for whipping up quick-and-dirty illustrations for situations just like this. And the visual result isn't dependent on playing around with text spacing for fixed-width and variable-width fonts.
Whatever tool you use, a picture you can post here would be helpful. Ideally it would show every device and every connection linking each device, complete with interface names, IP addresses, and subnet addresses.
As for the text configurations, from OpenWRT the contents of the usual culprits would be handy: /etc/config/network, /etc/config/firewall, /etc/config/dhcp. Redact any sensitive details such as passwords and keys.
And for the Mikrotik side, the responses to these commands would be handy: ip export, ip address print, interface export, interface print, routing table print, routing route print, ip route print. As above, redact any sensitive details such as passwords and keys.
I had a stab at this:
I used 192.168.3.0/24 instead of 192.168.1.0/24 because 192.168.1.0/24 is already in use here and working around the overlap was awkward.
I haven't yet got around to adding WireGuard to the test rig, but your configuration extract for WireGuard on OpenWRT looks good... but there's still something to check. Keep reading.
These are the configurations:
OpenWRT:
/etc/config/network:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
config interface 'lan'
option device 'eth0'
option proto 'static'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
config interface 'wg0'
<WireGuard configuration would go here, if I had configured it>
config wireguard_wg0
<WireGuard peer configuration would go here, if I had configured it>
config route
option interface 'lan'
option target '192.168.2.0/24'
option gateway '192.168.3.193'
Note: No additional route directive is necessary here for traffic originating from WireGuard peers. Extra routes are only necessary if there are remote destinations beyond the remote WireGuard peers.
/etc/config/firewall: no additional rules needed, as your configuration already puts wg0 in the lan zone.
Mikrotik:
[admin@MikroTik] > export
# 2023-06-29 01:21:38 by RouterOS 7.10.1
# software id =
#
/interface ethernet
set [ find default-name=ether1 ] disable-running-check=no
set [ find default-name=ether2 ] disable-running-check=no
set [ find default-name=ether3 ] disable-running-check=no
/interface list
add name=OpenWRT
add name=4G
add name=LAN
/interface list member
add interface=ether1 list=OpenWRT
add interface=ether2 list=4G
add interface=ether3 list=LAN
/ip address
add address=192.168.2.1/24 interface=ether3 network=192.168.2.0
/ip dhcp-client
add interface=ether1
add interface=ether2
/ip firewall nat
add action=masquerade chain=srcnat dst-address=0.0.0.0/0 out-interface=ether2
/ip route
add dst-address=192.168.9.0/24 gateway=192.168.3.1
[admin@MikroTik] >
I have removed some surplus commands unrelated to network flows; if you issue /export on your Mikrotik router you may see more than I quoted here.
As you can see, SNAT (masquerade) is configured only on the interface presented to the 4G connection.
And there is one single static route, for 192.168.9.0/24, with OpenWRT as the next hop for it.
However... this is where my lack of knowledge about all things Mikrotik trips me up.
Right now, both ether1 and ether2 have equally-weighted default routes:
[admin@MikroTik] > ip route print
Flags: D - DYNAMIC; A - ACTIVE; c, s, d, y - BGP-MPLS-VPN; + - ECMP
Columns: DST-ADDRESS, GATEWAY, DISTANCE
# DST-ADDRESS GATEWAY DISTANCE
DAd+ 0.0.0.0/0 172.16.0.1 1
DAd+ 0.0.0.0/0 192.168.3.1 1
DAc 172.16.0.0/24 ether2 0
DAc 192.168.2.0/24 ether3 0
DAc 192.168.3.0/24 ether1 0
0 As 192.168.9.0/24 192.168.3.1 1
[admin@MikroTik] >
The equal weighting means neither route takes precedence, which can lead to some amusing asymmetric routing fun. Fortunately, the static route and the connected routes take priority over the default routes, and they are unique.
You may have to spend time learning how to manipulate route weights (or "distances") on your Mikrotik router, to get the sort of traffic flow you want.
As for WireGuard, while your OpenWRT configuration for WireGuard looks good, how are the remote peers configured? If the peers don't have 192.168.2.0/24 (or, alternately, 0.0.0.0/0) in their AllowedIPs directive, then the traffic won't be routed properly through the VPN.