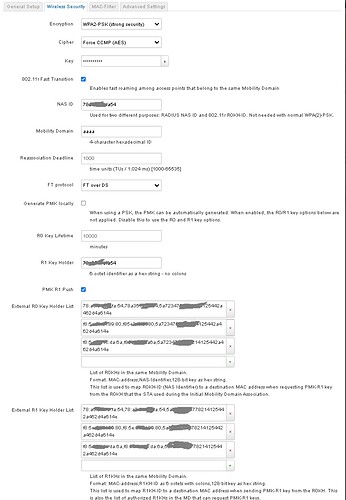
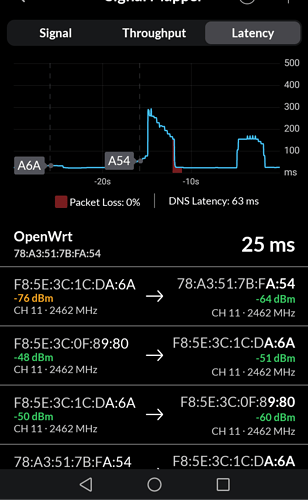
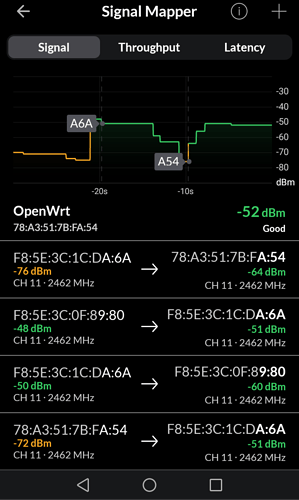
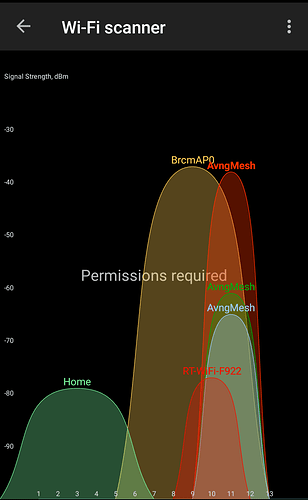
I have 3 routers (19.7.7) on every router 802.11r is enebled
is there any way to understand if FT works ?
and here is system.log
Wed Nov 3 21:45:48 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc MLME: MLME-REASSOCIATE.indication(70:8a:09:df:f1:bc)
Wed Nov 3 21:45:48 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc MLME: MLME-DELETEKEYS.request(70:8a:09:df:f1:bc)
Wed Nov 3 21:45:48 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc IEEE 802.11: binding station to interface 'wlan0'
Wed Nov 3 21:45:48 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: event 1 notification
Wed Nov 3 21:45:48 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: sending 1/4 msg of 4-Way Handshake
Wed Nov 3 21:45:48 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: received EAPOL-Key frame (2/4 Pairwise)
Wed Nov 3 21:45:48 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: sending 3/4 msg of 4-Way Handshake
Wed Nov 3 21:45:48 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: received EAPOL-Key frame (4/4 Pairwise)
Wed Nov 3 21:45:48 2021 daemon.notice hostapd: wlan0: AP-STA-CONNECTED 70:8a:09:df:f1:bc
Wed Nov 3 21:45:48 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc IEEE 802.1X: authorizing port
Wed Nov 3 21:45:48 2021 daemon.info hostapd: wlan0: STA 70:8a:09:df:f1:bc RADIUS: starting accounting session 429C07DC1FA17CC8
Wed Nov 3 21:45:48 2021 daemon.info hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: pairwise key handshake completed (RSN)
Wed Nov 3 21:47:59 2021 daemon.notice hostapd: wlan0: AP-STA-DISCONNECTED 70:8a:09:df:f1:bc
Wed Nov 3 21:47:59 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc IEEE 802.11: authentication OK (open system)
Wed Nov 3 21:47:59 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: event 0 notification
Wed Nov 3 21:47:59 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc MLME: MLME-AUTHENTICATE.indication(70:8a:09:df:f1:bc, OPEN_SYSTEM)
Wed Nov 3 21:47:59 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc MLME: MLME-DELETEKEYS.request(70:8a:09:df:f1:bc)
Wed Nov 3 21:47:59 2021 daemon.info hostapd: wlan0: STA 70:8a:09:df:f1:bc IEEE 802.11: authenticated
Wed Nov 3 21:47:59 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc IEEE 802.11: association OK (aid 1)
Wed Nov 3 21:47:59 2021 daemon.info hostapd: wlan0: STA 70:8a:09:df:f1:bc IEEE 802.11: associated (aid 1)
Wed Nov 3 21:47:59 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc MLME: MLME-REASSOCIATE.indication(70:8a:09:df:f1:bc)
Wed Nov 3 21:47:59 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc MLME: MLME-DELETEKEYS.request(70:8a:09:df:f1:bc)
Wed Nov 3 21:47:59 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc IEEE 802.11: binding station to interface 'wlan0'
Wed Nov 3 21:47:59 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: event 1 notification
Wed Nov 3 21:47:59 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: sending 1/4 msg of 4-Way Handshake
Wed Nov 3 21:47:59 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: received EAPOL-Key frame (2/4 Pairwise)
Wed Nov 3 21:47:59 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: sending 3/4 msg of 4-Way Handshake
Wed Nov 3 21:47:59 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: received EAPOL-Key frame (4/4 Pairwise)
Wed Nov 3 21:47:59 2021 daemon.notice hostapd: wlan0: AP-STA-CONNECTED 70:8a:09:df:f1:bc
Wed Nov 3 21:47:59 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc IEEE 802.1X: authorizing port
Wed Nov 3 21:47:59 2021 daemon.info hostapd: wlan0: STA 70:8a:09:df:f1:bc RADIUS: starting accounting session 429C07DC1FA17CC8
Wed Nov 3 21:47:59 2021 daemon.info hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: pairwise key handshake completed (RSN)
Wed Nov 3 21:48:46 2021 daemon.notice hostapd: wlan0: AP-STA-DISCONNECTED 70:8a:09:df:f1:bc
Wed Nov 3 21:48:46 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc IEEE 802.11: authentication OK (open system)
Wed Nov 3 21:48:46 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: event 0 notification
Wed Nov 3 21:48:46 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc MLME: MLME-AUTHENTICATE.indication(70:8a:09:df:f1:bc, OPEN_SYSTEM)
Wed Nov 3 21:48:46 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc MLME: MLME-DELETEKEYS.request(70:8a:09:df:f1:bc)
Wed Nov 3 21:48:46 2021 daemon.info hostapd: wlan0: STA 70:8a:09:df:f1:bc IEEE 802.11: authenticated
Wed Nov 3 21:48:46 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc IEEE 802.11: association OK (aid 1)
Wed Nov 3 21:48:46 2021 daemon.info hostapd: wlan0: STA 70:8a:09:df:f1:bc IEEE 802.11: associated (aid 1)
Wed Nov 3 21:48:46 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc MLME: MLME-REASSOCIATE.indication(70:8a:09:df:f1:bc)
Wed Nov 3 21:48:46 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc MLME: MLME-DELETEKEYS.request(70:8a:09:df:f1:bc)
Wed Nov 3 21:48:46 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc IEEE 802.11: binding station to interface 'wlan0'
Wed Nov 3 21:48:46 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: event 1 notification
Wed Nov 3 21:48:46 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: sending 1/4 msg of 4-Way Handshake
Wed Nov 3 21:48:46 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: received EAPOL-Key frame (2/4 Pairwise)
Wed Nov 3 21:48:46 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: sending 3/4 msg of 4-Way Handshake
Wed Nov 3 21:48:46 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: received EAPOL-Key frame (4/4 Pairwise)
Wed Nov 3 21:48:46 2021 daemon.notice hostapd: wlan0: AP-STA-CONNECTED 70:8a:09:df:f1:bc
Wed Nov 3 21:48:46 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc IEEE 802.1X: authorizing port
Wed Nov 3 21:48:46 2021 daemon.info hostapd: wlan0: STA 70:8a:09:df:f1:bc RADIUS: starting accounting session 429C07DC1FA17CC8
Wed Nov 3 21:48:46 2021 daemon.info hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: pairwise key handshake completed (RSN)
Wed Nov 3 21:50:32 2021 daemon.notice hostapd: wlan0: AP-STA-DISCONNECTED 70:8a:09:df:f1:bc
Wed Nov 3 21:50:32 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc IEEE 802.11: authentication OK (open system)
Wed Nov 3 21:50:32 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: event 0 notification
Wed Nov 3 21:50:32 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc MLME: MLME-AUTHENTICATE.indication(70:8a:09:df:f1:bc, OPEN_SYSTEM)
Wed Nov 3 21:50:32 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc MLME: MLME-DELETEKEYS.request(70:8a:09:df:f1:bc)
Wed Nov 3 21:50:32 2021 daemon.info hostapd: wlan0: STA 70:8a:09:df:f1:bc IEEE 802.11: authenticated
Wed Nov 3 21:50:32 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc IEEE 802.11: association OK (aid 1)
Wed Nov 3 21:50:32 2021 daemon.info hostapd: wlan0: STA 70:8a:09:df:f1:bc IEEE 802.11: associated (aid 1)
Wed Nov 3 21:50:32 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc MLME: MLME-REASSOCIATE.indication(70:8a:09:df:f1:bc)
Wed Nov 3 21:50:32 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc MLME: MLME-DELETEKEYS.request(70:8a:09:df:f1:bc)
Wed Nov 3 21:50:32 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc IEEE 802.11: binding station to interface 'wlan0'
Wed Nov 3 21:50:32 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: event 1 notification
Wed Nov 3 21:50:32 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: sending 1/4 msg of 4-Way Handshake
Wed Nov 3 21:50:32 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: received EAPOL-Key frame (2/4 Pairwise)
Wed Nov 3 21:50:32 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: sending 3/4 msg of 4-Way Handshake
Wed Nov 3 21:50:32 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: received EAPOL-Key frame (4/4 Pairwise)
Wed Nov 3 21:50:32 2021 daemon.notice hostapd: wlan0: AP-STA-CONNECTED 70:8a:09:df:f1:bc
Wed Nov 3 21:50:32 2021 daemon.debug hostapd: wlan0: STA 70:8a:09:df:f1:bc IEEE 802.1X: authorizing port
Wed Nov 3 21:50:32 2021 daemon.info hostapd: wlan0: STA 70:8a:09:df:f1:bc RADIUS: starting accounting session 429C07DC1FA17CC8
Wed Nov 3 21:50:32 2021 daemon.info hostapd: wlan0: STA 70:8a:09:df:f1:bc WPA: pairwise key handshake completed (RSN)
this log shows one AP and i was moving every1 -2 minutes among them