Hi folks,
Here is a project I've been developing for the past few months.
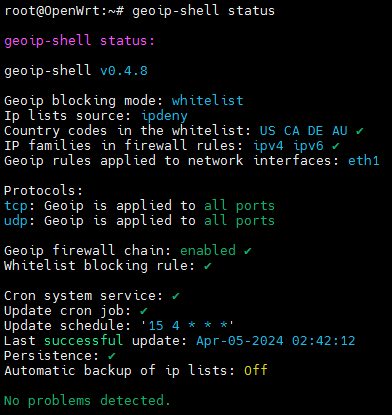
The idea is making geoip blocking easy on (almost) any Linux system (including OpenWrt), no matter which hardware, while also being reliable and providing flexible configuration options for the advanced users.
OpenWrt packages are available from my Github repo.
[ update April 22nd 2024 ] geoip-shell has been merged into OpenWrt packages repo. I'm currently still providing the .ipk packages from my Github repo since they include important changes which the downstream version still has not incorporated, and because the packages are currently only unavailable from the development OpenWrt branch, and because the ipk's intended for iptables-based systems are unlikely to get backported to earlier OpenWrt releases which support iptables and firewall3.
The project currently doesn't have a Luci interface. It does have a good and easy to use command-line interface. If there will be significant interest, I'll consider making a Luci interface for it.
Installation and uninstallation is either via an -install and an -uninstall scripts, or install via the ipk package and uninstall via opkg.
Actual blocking is done by the netfilter kernel component. geoip-shell creates a convenient interface with it, plus support for persistence and ip lists updates.
The ip lists can be fetched either from ipdeny (default for OpenWrt) or from RIPE (default for all other systems).
I regularly test on a VM with OpenWrt 23.05.2 and on my WNDR3700 v2 router with OpenWrt from around 2021 (with SFE patches), as well as on my Debian and Linux Mint machines.
Please let me know if you find any bugs or have a feature request, or if you have any questions, or simply if you find this project useful.
Here is the link:
OpenWrt-specific documentation for geoip-shell:
https://github.com/friendly-bits/geoip-shell/blob/main/OpenWrt/README.md
P.s. yes, there are some other projects capable of doing geoip blocking. I don't want to go into comparison here, I'll just say - this is a very different approach.
P.p.s. Post updated on April 22, 2024.