Hi,
First sorry for my English, it is not my native language.
And, just to be clear, I like a lot OpenWRT despite things I don't like on this distro (nothing can be perfect), I use it directly on my FTTH 300/300mbps line on a x86_64 mini-pc with VLANs, vlan priorisation (necessary because of my ISP), Wireguard, adblock etc .... so it was not easy to make all working
About this subject I can understand the 2 positions.
I'm an IT guy but not (not at all !!) a network's guy (working mostly on servers rooms+vmware+system to make things simple) and not even a security guy. I can't imagine how a "not IT guy" can understand anything about that stuff.
And, for my day to day needs, I almost never understand anything to the OpenWRT documentation when I need it (and when this doc exists and when it is not completly obsolete).
This existing doc it perhaps very well done .... but in my opinion only for those who already know what we are talking about. So it looks like a doc written by ... and for ... those who already know is not very usefull for all the others.
I don't want to blame anybody, writing good docs is almost more difficult that doing the code itself .. and less interesting.
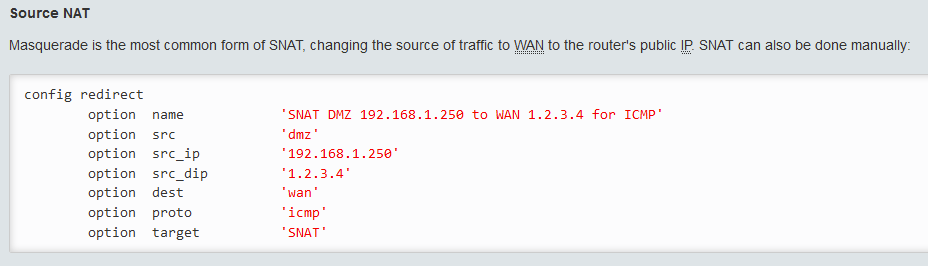
As an exemple (I took the first that came too me, I don't want anyone trying to explain SNAT today to me ... it's just an exemple):
Ok, those who know what is SNAT don't need to read this at all.
But in my case I (really) don't know what is SNAT ... and I simply didn't understand this chapter and what should be the difference(s) between DNAT/SNAT/Masquerading.
I also didn't understand how this can be done differently than manually (SNAT can also be done manually: .... also !
That's the same thing in many many many computer bioses:
Function Foo: yes/no with the comment: Used to enable the Foo fonction clap clap clap, thank you, very usefull
Same thing here (just another exemple, I really don't care about that today):
![]()
I have many (really, many) exemples of bad/incomplete/incomprehensible/non-existent doc for OpenWRT and I unfortunatly have no enough time to investigate for each new need.
So, for those who know how things work inside OpenWRT: stop telling us: that's not the good way to do, or, you dindn't understand the way it works, or, you have done a bad choice, or, do your homework before asking .... please just explain and/or redirect the guy wich is asking something to a good piece of documentation, we will be happy to learn how to do that well
because that's simply not so easy, neither it is accessible for everybody.
Many guys (like me, like @stringer ) do a lot of efforts/search to understand these things, to do what they can to have a better router/firewall to protect their home network (many ISP or commercial routers are bad with many backdoors and no security updates, so it is smart to try to replace them with a great piece of software like OpenWRT)
I read really too often replies like I read here from guys who knows to guys who ask ... it is not very kind.
Because many things are not explained about how things work inside OpenWRT. Many things are hidden inside OpenWRT, and these choices were not explained to us.
And for you, those who know, you can't even figure out that it's impossible to find the correct information for those who don't yet know how these things work
Almost all the documentation is done the same way (with short tutorials/exemples about the most common needs/use cases, and .... that's all, no explanation, nothing more) where it should perhaps be better to list/explain all the available functions instead. We (I) have no enough time to go on each package's Github to read all the code to discover wich option/variable do what.
And, as I told early, English is not my native language, I try to make a lot of efforts in this aspects but sometime the documention uses very complexe sentences/words/concepts for many guys (at least for me) and things can be very confusing
Last aspect, the beginning of the firewall doc tells:
... but nowhere .. NOWHERE ... on this doc it is explained how to do that with LUCI ... you can only find how to do that with the configuration files.
Even the most beginning of the firewall configuration doesn't visually match the configuration files organisation if you don't carrefully understand how it works on the files vs how it works on Luci, it is at least very confusing .. and if you don't understand why I'm saying that it is because you already know how it works for too long and so you are not able anymore to understand why it should be hard for some non-already-linux-firewall-aware guys (it is not my config, I took that on Google images):
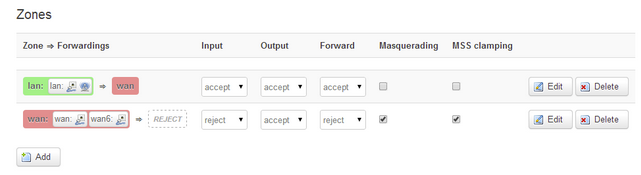
Just to help to understand what I mean:
- the left and right parts are independant on the firewall file (forwarding between defined zones on the left -- ONE zone configuration on the right) ... not on Luci because on the same line
- the right part (zone configuration) doesn't care about the forwarding destination, it only cares about the source zone defined on the left
.... but, because it is on the same line it is confusing.
A newcomer (like me a short time ago) will naturaly think that the right part is used to configure the left part, but it is not the case
There should be a better solution to display that no ? (just an example, remember)
Regards
Herve