Hello,
I am struggling for a while now to get a guest wifi running without success. I have tried following the UI-based approach, have tried the scripts from the Wiki, both with the same result of traffic not going through.
In the forum I have seen other people's similar problems, but reading through the threads, I haven't found what's wrong.
I am using an Archer C7, which is configured as AP for a long time, with the main router being another device. The C7 is connected to my LAN with its WAN port. The main device is 192.168.234.254, for the guest wifi I chose network 192.168.3.x, the C7 being 192.168.3.1.
My config is below. Any help greatly appreciated.
dhcp:
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option localservice '1'
list server '192.168.234.254'
config dhcp 'lan'
option interface 'lan'
option ignore '1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'guest'
option interface 'guest'
option start '100'
option limit '150'
option leasetime '1h'
network:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd0b:f729:6268::/48'
config interface 'lan'
option type 'bridge'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option _orig_ifname 'eth0.1 radio0.network1 radio1.network1'
option _orig_bridge 'true'
option ifname 'eth0.1 eth0.2'
option ipaddr '192.168.234.250'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
option type 'bridge'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0t 2 3 4 5'
option vid '1'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 1'
option vid '2'
config interface 'guest'
option type 'bridge'
option proto 'static'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
wireless:
config wifi-device 'radio0'
option type 'mac80211'
option hwmode '11a'
option path 'pci0000:00/0000:00:00.0'
option htmode 'VHT80'
option country 'DE'
option channel '44'
config wifi-iface 'default_radio0'
option device 'radio0'
option mode 'ap'
option ssid 'main'
option encryption 'psk2'
option wpa_disable_eapol_key_retries '1'
option key '***'
option network 'lan'
config wifi-device 'radio1'
option type 'mac80211'
option hwmode '11g'
option htmode 'HT20'
option country 'DE'
option channel '3'
option path 'platform/ahb/18100000.wmac'
config wifi-iface 'default_radio1'
option device 'radio1'
option mode 'ap'
option ssid 'main'
option encryption 'psk2'
option wpa_disable_eapol_key_retries '1'
option key '***'
option network 'lan'
config wifi-iface 'guest'
option device 'radio0'
option mode 'ap'
option network 'guest'
option ssid 'guest'
option encryption 'wpa2-psk2'
option key '***'
firewall:
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'REJECT'
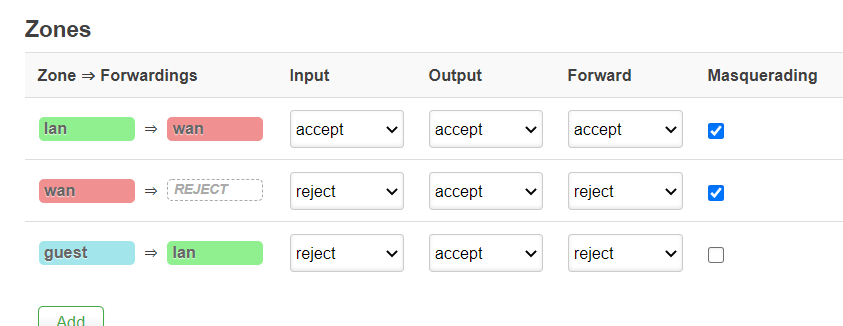
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
option masq '1'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone 'guest'
option name 'guest'
option network 'guest'
option output 'ACCEPT'
option input 'REJECT'
option forward 'REJECT'
config forwarding 'guest_wan'
option src 'guest'
option dest 'wan'
config rule 'guest_dns'
option name 'Allow-DNS-Guest'
option src 'guest'
option dest_port '53'
option proto 'tcp udp'
option target 'ACCEPT'
config rule 'guest_dhcp'
option name 'Allow-DHCP-Guest'
option src 'guest'
option dest_port '67'
option family 'ipv4'
option proto 'udp'
option target 'ACCEPT'
2 Likes
welcome...
Please use the "Preformatted text </>" button for logs, scripts, configs and general console output.
2 Likes
mk24
April 4, 2021, 4:50pm
3
It started out as a dumb AP, so no wan network is used. The path to the Internet is via lan. So the forwarding should be guest to lan, not guest to wan.
In one of the iterations of my trying, I did use one of the LAN switch ports and had the forward to LAN. Did not work. Of course can be some other misconfig.
But all other devices on the C7's LAN ports and also all wireless devices connected to the "regular" wifi can reach the internet. My assumption is that I should be able to keep the C7 connected via the WAN port, right? Should only by a port on the switch? Why would all else work otherwise?
mk24
April 4, 2021, 5:00pm
5
This has placed the lan and wan ports in the same bridge, the br-lan. You should delete the leftover wan and wan6 and use it as a LAN device with locally routed guests.
Also rather than software bridging eth0.1 and eth0.2, change the switch config to hardware switch all five external Ethernet ports in VLAN1, which is eth0.1 which is the lan.
OK, will try that.
mk24
April 4, 2021, 5:37pm
7
This starts as a dumb AP, which has only one network-- lan. Then a guest network was added which locally forwards to lan. So remove everything related to wan. This ends up with the lan zone, which forwards nowhere (it's bridged to your main network, not routed), and guest zone, which forwards to lan.
Masquerading must stay enabled on lan.
most people don't want guest forwarding to LAN, but might want lan forwarding to guest (and the return traffic will be allowed by default). However, guest traffic should usually forward to WAN otherwise there's no internet access.
mk24
April 4, 2021, 6:07pm
9
Guest forwards to lan to obtain Internet access. A firewall rule should be placed to block guests from the lan IP range. (This does not prevent using the LAN main router as the gateway to the Internet since the firewall looks at the final destination of the packet.)
Simplified version (without WAN zone etc.) still does not work either yet. Will continue tomorrow and post the new config then.
what does "work" mean for you here. What is this guest network supposed to be able to do and what is it not supposed to be able to do?
1 Like
Does not work in terms of being able to reach the internet.
Because you haven't allowed forwarding from the guest network to the WAN.
Following Mike's advice, there is no WAN anymore. I am having guest forwarding to LAN, which should be enough.
Will have another look tomorrow with a fresh mind and probably post the stripped-up config if it still does not work.
Thanks
The best way to handle this is to trunk tagged packets back to the actual router, and set the router up with guest -> WAN forwarding.
Why isn't it sufficient to control traffic based on IP networks? That sounds simpler to me.
I have never done the above and also the main router is provided by my network provider and I don't think I am supposed to fiddle with that in that way.
OK, the simplified config is shown below. As I said still does not allow guest devices to access the internet (and does not have a rule to prevent the home network, but I am going step-by-step
wireless:
config wifi-device 'radio0'
option type 'mac80211'
option hwmode '11a'
option path 'pci0000:00/0000:00:00.0'
option htmode 'VHT80'
option country 'DE'
option channel '44'
config wifi-iface 'default_radio0'
option device 'radio0'
option mode 'ap'
option ssid 'main'
option encryption 'psk2'
option wpa_disable_eapol_key_retries '1'
option key '***'
option network 'lan'
config wifi-device 'radio1'
option type 'mac80211'
option hwmode '11g'
option htmode 'HT20'
option country 'DE'
option channel '3'
option path 'platform/ahb/18100000.wmac'
config wifi-iface 'default_radio1'
option device 'radio1'
option mode 'ap'
option ssid 'main'
option encryption 'psk2'
option wpa_disable_eapol_key_retries '1'
option key 'main'
option network 'lan'
config wifi-iface 'guest'
option device 'radio0'
option mode 'ap'
option ssid 'guest'
option key '***'
option network 'guest'
option encryption 'psk2'
network:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd0b:f729:6268::/48'
config interface 'lan'
option type 'bridge'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option _orig_ifname 'eth0.1 radio0.network1 radio1.network1'
option _orig_bridge 'true'
option ipaddr '192.168.234.250'
option ifname 'eth0.1'
config switch
option name 'switch0'
option reset '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 2 3 4 5 1'
config interface 'guest'
option type 'bridge'
option proto 'static'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
option gateway '192.168.234.254'
list dns '192.168.234.254'
firewall:
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'REJECT'
config include
option path '/etc/firewall.user'
config zone
option name 'guest'
option input 'ACCEPT'
option network 'guest'
option output 'ACCEPT'
option forward 'ACCEPT'
list device 'wlan0-1'
option family 'ipv4'
option masq '1'
config zone
option name 'lan'
option input 'ACCEPT'
option network 'lan'
option output 'ACCEPT'
option forward 'ACCEPT'
config forwarding
option dest 'lan'
option src 'guest'
config rule 'guest_dns'
option name 'Allow-DNS-Guest'
option src 'guest'
option dest_port '53'
option proto 'tcp udp'
option target 'ACCEPT'
config rule 'guest_dhcp'
option name 'Allow-DHCP-Guest'
option src 'guest'
option dest_port '67'
option family 'ipv4'
option proto 'udp'
option target 'ACCEPT'
dhcp:
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option localservice '1'
list server '192.168.234.254'
config dhcp 'lan'
option interface 'lan'
option ignore '1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'guest'
option interface 'guest'
option start '100'
option limit '150'
option leasetime '1h'
1 Like
uci -q delete dhcp.@dnsmasq[0].server
uci commit dhcp
/etc/init.d/dnsmasq enable
/etc/init.d/dnsmasq restart
uci -q delete firewall.@zone[0].device
uci -q delete firewall.@zone[0].family
uci -q delete firewall.@zone[0].masq
uci set firewall.@zone[1].masq="1"
uci set firewall.@zone[1].masq_src="!192.168.234.0/24"
uci commit firewall
/etc/init.d/firewall enable
/etc/init.d/firewall restart
uci -q delete network.guest.gateway
uci -q delete network.guest.dns
uci set network.lan.gateway="192.168.234.254"
uci set network.lan.dns="192.168.234.254"
uci commit network
/etc/init.d/network restart
mk24
April 5, 2021, 3:41pm
19
In a dumb AP, the lan gateway must be set to the main router on the LAN (I assume 192.168.234.1). An upstream DNS also needs to be set, usually also the next router.
The routing table (run route with no parameters) should show the default route to the upstream router. Internet access from the OpenWrt OS (i.e. ping openwrt.org) needs to work.
Do not set gateway and DNS in the guest network, they will be effectively inherited.
The option _orig_xxxx are a vestige of a very old version of LuCI and can be removed. Are you running the latest version of OpenWrt?
Thanks, @vgaetera and @mk24 , I am one step further now!
Vladislav's script almost did the trick, but I needed the below line (gateway for lan to next router, as Mike said):
uci set network.lan.gateway="192.168.234.254"
Some additional questions:
Guest devices cannot see my lan zone, which is desired. But what is causing this? The masquerading?
Guests can see each other right now. What do I need to change to isolate them?
Thanks a lot!
1 Like