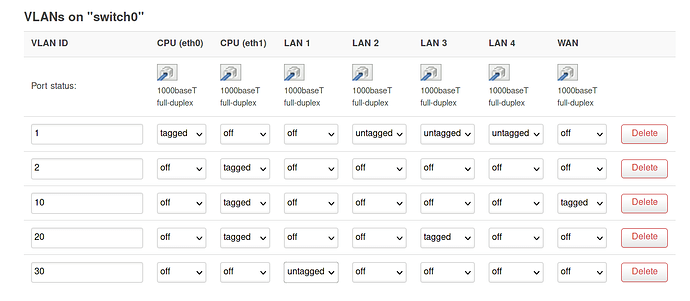
Don't think I can post the not working config Luci generates, since I can't connect to my router when that is configured.
I'm not sure what I did, but now it I can connect to my router when LAN4 is tagged to VLAN ID 20 or 30, but not when it's tagged to VLAN 1. I looked into the config and I don't see why that would be.
Also, I can add lan port 4 to the guest network and it works as expected:
/etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdbd:ac15:9a00::/48'
config interface 'lan'
option type 'bridge'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option ifname 'eth0.1'
config interface 'wan'
option proto 'dhcp'
option ifname 'eth1.2'
config interface 'wan6'
option ifname 'eth1.2'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix '56'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '1 2 3 5t'
config switch_vlan
option device 'switch0'
option vlan '2'
option vid '2'
option ports '6t'
config route
config wireguard_wireguard
option persistent_keepalive '25'
option public_key 'zFvqANLZMFwYrGAAUW+kv4JvI7sqCtDkBEBLLJIJayg='
list allowed_ips '192.168.20.0/24'
option route_allowed_ips '1'
config interface 'IoT'
option proto 'static'
option type 'bridge'
option netmask '255.255.255.0'
option ipaddr '192.168.2.1'
option ifname 'eth0.1'
config interface 'guest'
option type 'bridge'
option ifname 'eth1.20'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.20.1'
option ip6assign '64'
option ip6hint '20'
config interface 'wanb'
option proto 'static'
option type 'bridge'
option ifname 'eth0.1'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '10'
option ports '4t 6t'
config interface 'EDPNET'
option ifname 'eth1.10'
option proto 'pppoe'
option password 'PASSWORD'
option ipv6 'auto'
option username 'USERNAME'
config switch_vlan
option device 'switch0'
option vlan '4'
option vid '20'
option ports '0 1t 6t'
config switch_vlan
option device 'switch0'
option vlan '6'
option vid '30'
option ports '6t'
config interface 'kelder'
option ifname 'eth1.30'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.30.1'
option ip6assign '64'
option type 'bridge'
option ip6hint '30'
/etc/config/dhcp
config dnsmasq
option localise_queries '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option localservice '1'
option rebind_protection '1'
option rebind_localhost '1'
list server '127.0.0.1#5054'
list server '127.0.0.1#5053'
list server '127.0.0.1#5052'
option noresolv '1'
option doh_backup_noresolv '-1'
list doh_backup_server '1.1.1.1'
list doh_backup_server '1.0.0.1'
list doh_backup_server '2606:4700:4700::1111'
list doh_backup_server '2606:4700:4700::1001'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
option ra_management '1'
config dhcp 'wan'
option interface 'wan'
option start '100'
option limit '150'
option leasetime '12h'
option ra 'relay'
option dhcpv6 'relay'
option ndp 'relay'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'iot'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'iot'
config dhcp 'IoT'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'IoT'
option ra 'server'
option dhcpv6 'server'
option ra_management '1'
config dhcp 'guest'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'guest'
option ra 'server'
option dhcpv6 'server'
option ra_management '1'
config domain
config host
option name 'hass'
option dns '1'
option mac 'C0:3F:D5:65:54:00'
option ip '192.168.1.206'
config dhcp 'kelder'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'kelder'
option ra 'server'
option dhcpv6 'server'
option ra_management '1'
/etc/config/firewall
config defaults
option input 'DROP'
option forward 'DROP'
option output 'DROP'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option input 'DROP'
option forward 'DROP'
option network 'wan wan6 wwan EDPNET'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config redirect
option target 'DNAT'
option src 'wan'
option dest 'lan'
option proto 'tcp'
option src_dport '443'
option name 'hassio'
option dest_port '8123'
option dest_ip '192.168.1.206'
config rule
option target 'ACCEPT'
option src 'wan'
option proto 'tcp'
option dest_port '22'
option name 'Allow-SSH-WAN'
config zone
option input 'ACCEPT'
option output 'ACCEPT'
option name 'iot'
option forward 'ACCEPT'
option network 'IoT'
config forwarding
option dest 'lan'
option src 'iot'
config forwarding
option dest 'iot'
option src 'lan'
config zone
option name 'guest'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'guest'
config forwarding
option dest 'wan'
option src 'guest'
config forwarding
option dest 'guest'
option src 'lan'
config rule
option target 'ACCEPT'
option src 'wan'
option proto 'tcp udp'
option dest_port '8088'
option name 'Allow-Wireguard-Wan'
config redirect
option target 'DNAT'
option src 'wan'
option dest 'lan'
option proto 'tcp udp'
option src_dport '444'
option dest_ip '192.168.1.206'
option dest_port '444'
option name 'grafana'
config zone
option name 'kelder'
option network 'kelder'
option input 'ACCEPT'
option forward 'ACCEPT'
option output 'ACCEPT'
config forwarding
option dest 'wan'
option src 'kelder'
config forwarding
option dest 'kelder'
option src 'lan'
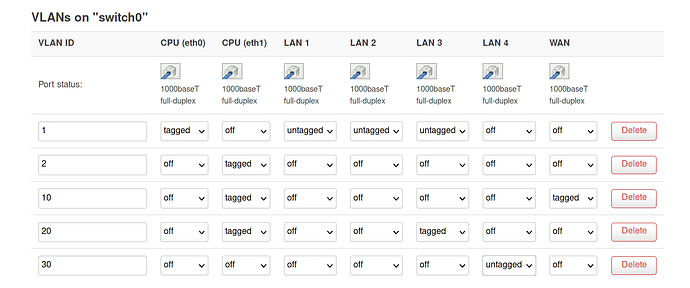
But if I create a separate VLAN and subnet for LAN 4, I can't connect to the devices on LAN 4. I looked through the config and I don't see any difference between the guest and kelder interfaces and their firewall setup, so I don't understand why this doesn't work.
/etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdbd:ac15:9a00::/48'
config interface 'lan'
option type 'bridge'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option ifname 'eth0.1'
config interface 'wan'
option proto 'dhcp'
option ifname 'eth1.2'
config interface 'wan6'
option ifname 'eth1.2'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix '56'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '1 2 3 5t'
config switch_vlan
option device 'switch0'
option vlan '2'
option vid '2'
option ports '6t'
config route
config wireguard_wireguard
option persistent_keepalive '25'
option public_key 'zFvqANLZMFwYrGAAUW+kv4JvI7sqCtDkBEBLLJIJayg='
list allowed_ips '192.168.20.0/24'
option route_allowed_ips '1'
config interface 'IoT'
option proto 'static'
option type 'bridge'
option netmask '255.255.255.0'
option ipaddr '192.168.2.1'
option ifname 'eth0.1'
config interface 'guest'
option type 'bridge'
option ifname 'eth1.20'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.20.1'
option ip6assign '64'
option ip6hint '20'
config interface 'wanb'
option proto 'static'
option type 'bridge'
option ifname 'eth0.1'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '10'
option ports '4t 6t'
config interface 'EDPNET'
option ifname 'eth1.10'
option proto 'pppoe'
option password 'PASSWORD'
option ipv6 'auto'
option username 'USERNAME'
config switch_vlan
option device 'switch0'
option vlan '4'
option vid '20'
option ports '1t 6t'
config switch_vlan
option device 'switch0'
option vlan '6'
option vid '30'
option ports '0 6t'
config interface 'kelder'
option ifname 'eth1.30'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.30.1'
option ip6assign '64'
option type 'bridge'
option ip6hint '30'
/etc/config/dhcp
config dnsmasq
option localise_queries '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option localservice '1'
option rebind_protection '1'
option rebind_localhost '1'
list server '127.0.0.1#5054'
list server '127.0.0.1#5053'
list server '127.0.0.1#5052'
option noresolv '1'
option doh_backup_noresolv '-1'
list doh_backup_server '1.1.1.1'
list doh_backup_server '1.0.0.1'
list doh_backup_server '2606:4700:4700::1111'
list doh_backup_server '2606:4700:4700::1001'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
option ra_management '1'
config dhcp 'wan'
option interface 'wan'
option start '100'
option limit '150'
option leasetime '12h'
option ra 'relay'
option dhcpv6 'relay'
option ndp 'relay'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'iot'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'iot'
config dhcp 'IoT'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'IoT'
option ra 'server'
option dhcpv6 'server'
option ra_management '1'
config dhcp 'guest'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'guest'
option ra 'server'
option dhcpv6 'server'
option ra_management '1'
config domain
config host
option name 'hass'
option dns '1'
option mac 'C0:3F:D5:65:54:00'
option ip '192.168.1.206'
config dhcp 'kelder'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'kelder'
option ra 'server'
option dhcpv6 'server'
option ra_management '1'
/etc/config/firewall
config defaults
option input 'DROP'
option forward 'DROP'
option output 'DROP'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option input 'DROP'
option forward 'DROP'
option network 'wan wan6 wwan EDPNET'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config redirect
option target 'DNAT'
option src 'wan'
option dest 'lan'
option proto 'tcp'
option src_dport '443'
option name 'hassio'
option dest_port '8123'
option dest_ip '192.168.1.206'
config rule
option target 'ACCEPT'
option src 'wan'
option proto 'tcp'
option dest_port '22'
option name 'Allow-SSH-WAN'
config zone
option input 'ACCEPT'
option output 'ACCEPT'
option name 'iot'
option forward 'ACCEPT'
option network 'IoT'
config forwarding
option dest 'lan'
option src 'iot'
config forwarding
option dest 'iot'
option src 'lan'
config zone
option name 'guest'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'guest'
config forwarding
option dest 'wan'
option src 'guest'
config forwarding
option dest 'guest'
option src 'lan'
config rule
option target 'ACCEPT'
option src 'wan'
option proto 'tcp udp'
option dest_port '8088'
option name 'Allow-Wireguard-Wan'
config redirect
option target 'DNAT'
option src 'wan'
option dest 'lan'
option proto 'tcp udp'
option src_dport '444'
option dest_ip '192.168.1.206'
option dest_port '444'
option name 'grafana'
config zone
option name 'kelder'
option network 'kelder'
option input 'ACCEPT'
option forward 'ACCEPT'
option output 'ACCEPT'
config forwarding
option dest 'wan'
option src 'kelder'
config forwarding
option dest 'kelder'
option src 'lan'
IPv6 subnets also don't seem to work as I expected, but I haven't looked to far into that yet...
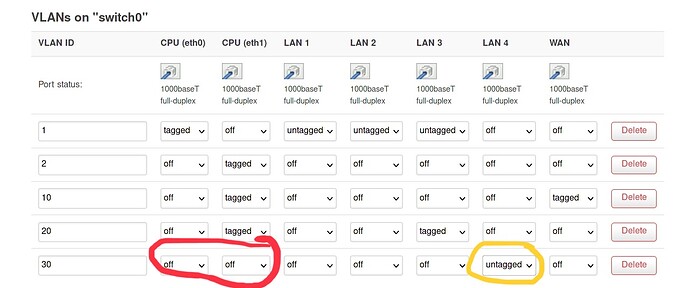
What is going on here with LAN 4? Any other files in/etc/config/ should look at?