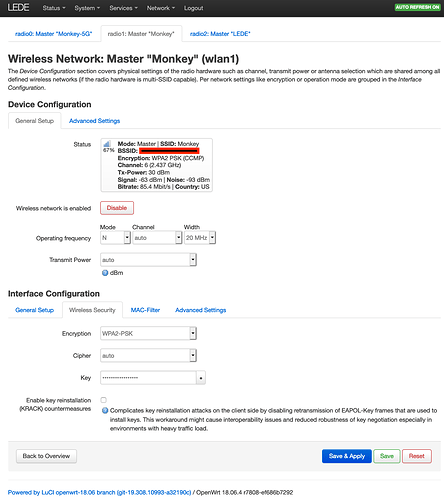
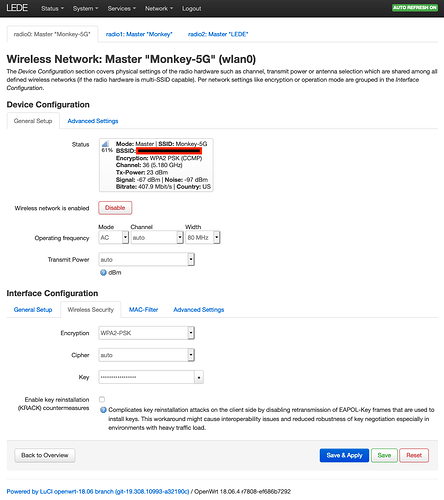
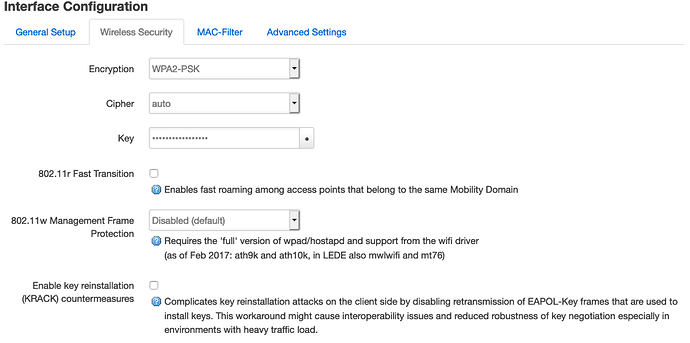
The ARP seems problematic:
$ sudo tcpdump -i any -vvn arp
Password:
tcpdump: data link type PKTAP
tcpdump: listening on any, link-type PKTAP (Packet Tap), capture size 65535 bytes
13:36:49.989536 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.170 tell 192.168.1.106, length 28
13:37:00.558418 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.133 tell 192.168.1.1, length 28
13:37:00.558463 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.1.133 is-at [MAC-REDACTED], length 28
13:37:25.682938 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.133 tell 192.168.1.1, length 28
13:37:25.682956 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.1.133 is-at [MAC-REDACTED], length 28
13:37:33.817236 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.232 tell 192.168.1.106, length 28
13:37:42.235682 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.211 tell 0.0.0.0, length 28
13:37:44.057261 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.211 tell 0.0.0.0, length 28
13:37:46.105933 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.211 tell 192.168.1.211, length 28
13:37:47.948172 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.211 tell 192.168.1.211, length 28
13:37:50.553727 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.133 tell 192.168.1.1, length 28
13:37:50.553743 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.1.133 is-at [MAC-REDACTED], length 28
13:38:15.805814 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.133 tell 192.168.1.1, length 28
13:38:15.805831 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.1.133 is-at [MAC-REDACTED], length 28
13:38:42.405823 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.133 tell 192.168.1.1, length 28
13:38:42.405836 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.1.133 is-at [MAC-REDACTED], length 28
13:39:10.721723 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.133 tell 192.168.1.1, length 28
13:39:10.721740 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.1.133 is-at [MAC-REDACTED], length 28
13:39:17.650873 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.170 tell 192.168.1.106, length 28
13:39:38.001394 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.133 tell 192.168.1.1, length 28
13:39:38.001410 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.1.133 is-at [MAC-REDACTED], length 28
13:40:05.517835 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.133 tell 192.168.1.1, length 28
13:40:05.517852 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.1.133 is-at [MAC-REDACTED], length 28
13:40:33.431246 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.133 tell 192.168.1.1, length 28
13:40:33.431264 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.1.133 is-at [MAC-REDACTED], length 28
13:41:00.641722 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.133 tell 192.168.1.1, length 28
13:41:00.641736 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.1.133 is-at [MAC-REDACTED], length 28
13:41:29.134872 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.133 tell 192.168.1.1, length 28
13:41:29.134885 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.1.133 is-at [MAC-REDACTED], length 28
13:41:50.023947 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.170 tell 192.168.1.106, length 28
13:41:56.235081 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.133 tell 192.168.1.1, length 28
13:41:56.235098 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.1.133 is-at [MAC-REDACTED], length 28
13:42:23.407511 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.221 tell 192.168.1.233, length 28
13:42:23.413413 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.218 tell 192.168.1.233, length 28
13:42:23.414244 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.220 tell 192.168.1.233, length 28
13:42:23.415111 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.219 tell 192.168.1.233, length 28
13:42:23.415990 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.222 tell 192.168.1.233, length 28
13:42:23.416862 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.223 tell 192.168.1.233, length 28
13:42:23.422243 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.228 tell 192.168.1.233, length 28
13:42:23.423061 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.229 tell 192.168.1.233, length 28
13:42:23.426710 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.230 tell 192.168.1.233, length 28
13:42:23.427576 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.231 tell 192.168.1.233, length 28
13:42:23.428476 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.224 tell 192.168.1.233, length 28
13:42:23.429363 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.225 tell 192.168.1.233, length 28
13:42:23.430254 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.239 tell 192.168.1.233, length 28
13:42:23.432782 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.235 tell 192.168.1.233, length 28
13:42:23.433756 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.236 tell 192.168.1.233, length 28
13:42:23.434835 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.234 tell 192.168.1.233, length 28
13:42:23.435716 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.238 tell 192.168.1.233, length 28
13:42:23.436615 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.237 tell 192.168.1.233, length 28
13:42:23.437503 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.241 tell 192.168.1.233, length 28
13:42:23.438539 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.240 tell 192.168.1.233, length 28
13:42:23.441346 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.242 tell 192.168.1.233, length 28
13:42:23.442225 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.245 tell 192.168.1.233, length 28
13:42:23.443097 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.244 tell 192.168.1.233, length 28
13:42:23.445015 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.246 tell 192.168.1.233, length 28
13:42:23.445887 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.247 tell 192.168.1.233, length 28
13:42:25.040995 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.133 tell 192.168.1.1, length 28
13:42:25.041045 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.1.133 is-at [MAC-REDACTED], length 28
13:42:52.650403 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.133 tell 192.168.1.1, length 28
13:42:52.650412 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.1.133 is-at [MAC-REDACTED], length 28
13:42:55.153682 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.211 tell 0.0.0.0, length 28
13:43:00.699802 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.211 tell 192.168.1.211, length 28
13:43:02.727978 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.211 tell 192.168.1.211, length 28
13:43:20.088463 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.1.133 tell 192.168.1.1, length 28
13:43:20.088480 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.1.133 is-at [MAC-REDACTED], length 28
^C^C
66 packets captured
32019 packets received by filter
0 packets dropped by kernel
The reply only contains the info for 192.168.1.133
Besides, it was good with LEDE 17.01.X. And I upgraded to OpenWRT 18.06.X in middle 2019. Not sure if it's related.
Thanks!