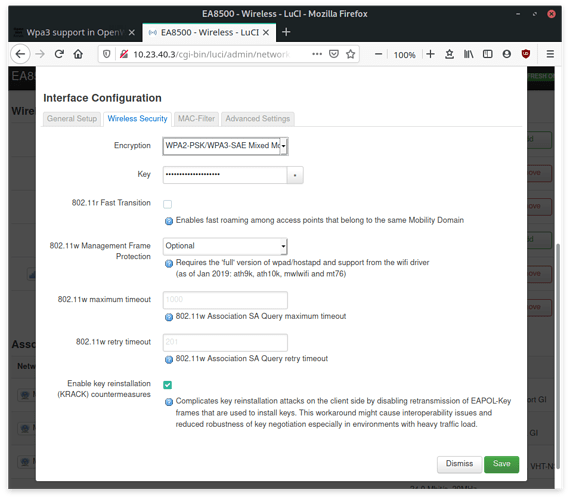
It seems like wpad-openssl is working in general better then wpad-wolfssl: https://bugs.openwrt.org/index.php?do=details&task_id=2571
I can confirm that WPA3 works when using openssl.
Commands to enable WPA3:
opkg update && opkg remove wpad-basic && opkg install wpad-openssl
ImageBuilder command for generating custom image for MR24 with luci and WPA3 (replace meraki_mr24 with your device):
make image PROFILE=meraki_mr24 PACKAGES="wpad-openssl luci -wpad-basic"
Does the full wpad package support wpa3, or will either wpad-openssl or wpad-wolfssl need to be installed? If so, what's the difference between the full wpad packages and the specific SSL packages? The full wpad package has the largest size, so apparently it has something those specific packages do not have.
Also, has anyone made a performance comparison between using openssl vs wolfssl?
As mentioned earlier in this thread.
wpad-full is not sufficient.
The full package is larger than either wpad-openssl and wpad-wolfssl though. What does it have that the other two packages do not? ie, am I giving anything up by moving from wpad-full to wpad-openssl or wpad-wolfssl?
I think the way it used to work is that the full variant baked in the required SSL functions, and therefore had no external library required, but had the biggest size.
Looking now, it looks as though FULL is the parent variant, and then you select either OPENSSL or WOLFSSL as the child variants. Either of those will enable things like SAE and OWE (many reports of better success on openssl rather than wolfssl).
This is just my guess based on the makefile, which is a little hard to read given how many variants there are.
SSL has always been a separate library package.
Earlier it was a dependency hell and plain wpad could require either openssl, mdedtls or wolfssl, depending on the compile time options used. That was clarified by declaring the SSL dependency already in the package name. Thus there is now wpad-openssl etc.
Functional wise it is also wpad, wpad-basic (without eap/radius), wpad-mini (without 80211r and w, thus no wpa3, without eap radius).
I suppose i misspoke, and should have said "crypto" rather than "ssl".
From hostap git:
* This file defines the cryptographic functions that need to be implemented
* for wpa_supplicant and hostapd. When TLS is not used, internal
* implementation of MD5, SHA1, and AES is used and no external libraries are
* required. When TLS is enabled (e.g., by enabling EAP-TLS or EAP-PEAP), the
* crypto library used by the TLS implementation is expected to be used for
* non-TLS needs, too, in order to save space by not implementing these
* functions twice.
Which is what i was referring to before. So if you don't include an SSL library, it reverts back to its own internal crypto functions (e.g. for hashing) and these all get linked in and make the resulting binary bigger. If you select an SSL library, these libraries provide the necessary crypto functions, and you get a smaller binary.
Looping back to the original question, as suggested, you need an SSL library to get WPA3 functionality. Additionally, the above explanation is why the binary is bigger when no SSL library is included (which may seem counter intuitive at first).
I have reported the WPA3 bug in iOS and iPadOS to Apple, and I think it would be a good idea if other people who have experienced the bug would report it as well. You can report iPhone bugs here, and iPad bugs here.
WPA3 in iOS is working for me on 2.4ghz if I manually add the network and choose WPA3, with no need for auth_cache. I can’t get it working on 5ghz, with or without manually adding the network or changing auth_cache. This is on an Archer C7v2
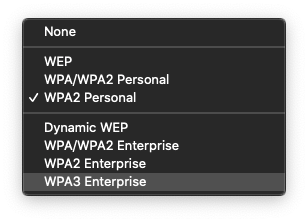
Got mixed results here using Fritzbox 4040 (ath10k) and wpad-openssl on both stable and snapshot. macOS doesn't want to connect in wpa3 or wpa2/wpa3 mode it says password wrong or some vague message about not being able to connect. Manually adding a connection shows it only seems to support wpa3 enterprise (see image). On iOS/iPadOS connections went ok in mixed mode but I think they fell back on wpa2.
Don't really know where to check in iOS or OpenWrt what the active encryption is. In wpa3 only mode iOS said the password was wrong. Windows10 also said the password was wrong in wpa3 only mode and in mixed mode it said it couldn't connect.
Same results on both 2.4 and 5ghz bands.
Not sure if trying wpad-wolfssl will yield any different results but I can try if anyone here thinks its useful. Any logs or info I can share or other things to test or try are welcomed. I'll also report this to Apple if this is due to them. Running iOS/iPadOS 13.3.1 and Catalina 10.15.3.
It looks like on openwrt-19.07.2,
wpa3 is not fully supported.
wpa3-enterprising (WPA3-EAP) is not ready yet.
see
Client Devices which does not support Management Frame Protection cannot connect to WPA3-SAE
I have it on both my EA6350v3 and EA8500 running 19.07.02. I am not using it - my clients do not support it yet - but it is available.
It is not included by default. Did you install the necessary package ( i.e., replace wpad with wpad-openssl)?
Thanks for you replay. I did install wapd-openssl.
wpa3-enterprise or wpa3-eap , this is a method for radius, it's mainly used for small bussiness and enterprise.
Some news here. With the release of iOS 13.4.1 and macOS 10.15.4 I decided to give WPA3 another go. Only my iPad can connect, which is kind of odd because iOS and iPadOS are pretty much the same. My MacBook was also unable to connect. Just like last time only the iPad can connect to it (running WPA3 mode only).
I hope Apple sorts this out soon.
I also wanted to add that after removing wpad and installing wpad-OpenSSL and setting up a mixed and/or wpa3 only network on 19.07.2, my iPhone SE (iOS 13.3.1) would not connect, the error was “wrong password” too.
*I also found it strange that when trying to manually add a wireless network on the iPhone that wpa3 personal was not an option, only “enterprise” was listed. Apple’s claims of supporting wpa3 only seem to be for enterprise use for now ..
Apple seems to have made a partially wrong claim when they are talking about WPA3 compatibility. From my experience, WPA3 personal works from the iPhone 7 onwards, while the 6s does not connect.
On the MacBook side of things, a MacBook Pro from early 2016 was also not able to connect when 802.11w (required per spec) was enabled. This is kind of interesting, as for WiFi certification 802.11w is mandatory.
Some possible improvement was done yesterday https://github.com/openwrt/openwrt/commit/631c437a91c20df678b25dcc34fe23636116a35a
Is there a list somewhere of what devices should be able to support WPA3? Or could such a category be added on the wiki?
I have ea6350 but I'm experiencing unstability and inability of some devices to connect, this may be related to vlans (I'm still checking that) but knowing whether the device should be able to handle it would be cool.