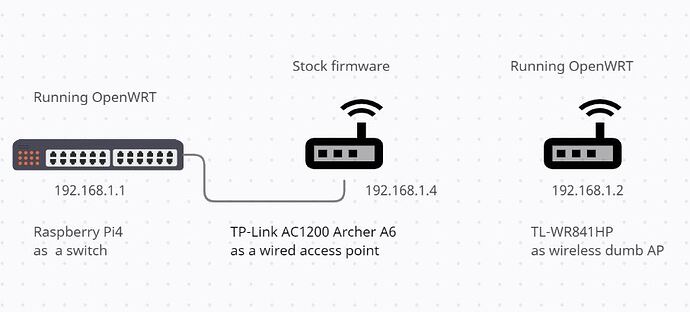
Network setup:
Raspberry Pi 4 Model B Rev 1.2 running on latest master snapshot setup as a switch which forwards WAN traffic to Archer A4 connected as an wired Access Point to Pi. DHCP off. Finally TP-LINK WR841HP v3.2 installed with the master snapshot capable of using only 2.4 GHz radio frequency wirelessly connected to Archer A6. It is set as dumb wireless access point (firewall, dnsmasq, odhcpd disabled). Absolutely no problem on other two devices and wifi so far.
Problem:
TL-WR841HP randomly gives huge ping spikes both on lan and wifi like shown below:
Reply from 1.1.1.1: bytes=32 time=104ms TTL=58
Reply from 1.1.1.1: bytes=32 time=554ms TTL=58
Reply from 1.1.1.1: bytes=32 time=3249ms TTL=58
Reply from 1.1.1.1: bytes=32 time=40ms TTL=58
Reply from 1.1.1.1: bytes=32 time=139ms TTL=58
Reply from 1.1.1.1: bytes=32 time=35ms TTL=58
Reply from 1.1.1.1: bytes=32 time=37ms TTL=58
Reply from 1.1.1.1: bytes=32 time=6ms TTL=58
Reply from 1.1.1.1: bytes=32 time=6ms TTL=58
Reply from 1.1.1.1: bytes=32 time=96ms TTL=58
Reply from 1.1.1.1: bytes=32 time=4ms TTL=58
Reply from 1.1.1.1: bytes=32 time=5ms TTL=58
Reply from 1.1.1.1: bytes=32 time=58ms TTL=58
Reply from 1.1.1.1: bytes=32 time=251ms TTL=58
Reply from 1.1.1.1: bytes=32 time=375ms TTL=58
Reply from 1.1.1.1: bytes=32 time=486ms TTL=58
Reply from 1.1.1.1: bytes=32 time=918ms TTL=58
Reply from 1.1.1.1: bytes=32 time=629ms TTL=58
Reply from 1.1.1.1: bytes=32 time=33ms TTL=58
Reply from 1.1.1.1: bytes=32 time=113ms TTL=58
Happens even if there's no network load on any side of the network. I don't have a spare router to try and test error but this is all I got.
Network on 192.168.1.1
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
config interface 'wan'
option proto 'pppoe'
option device 'eth1'
option username 'username'
option password 'password'
option peerdns '0'
config device
option name 'eth1'
option macaddr '64:66:XX:XX:XX:XX'
Firewall on 192.168.1.1
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
option flow_offloading '1'
option flow_offloading_hw '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
config redirect
option target 'DNAT'
option name 'DMZ'
option src 'wan'
option dest 'lan'
list proto 'tcp'
list proto 'udp'
option src_dport '0-65535'
DHCP on 192.168.1.1
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option localservice '1'
option ednspacket_max '1232'
option noresolv '1'
option doh_backup_noresolv '-1'
list doh_backup_server ''
list server '127.0.0.1#5054'
list server '127.0.0.1#5053'
option confdir '/tmp/dnsmasq.d'
option sequential_ip '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
list ra_flags 'none'
config host
option name 'Router'
option dns '1'
option mac '84:XX:XX:XX:XX'
option ip '192.168.1.2'
// more static addresses assigned
wireless on 192.168.1.2
config wifi-device 'radio0'
option type 'mac80211'
option path 'platform/ahb/18100000.wmac'
option band '2g'
option channel 'auto'
option country 'IN'
option cell_density '0'
option htmode 'HT20'
config wifi-iface 'default_radio0'
option device 'radio0'
option mode 'ap'
option ssid 'wifiname'
option network 'lan'
option key 'password'
option encryption 'psk2'
option disassoc_low_ack '0'
option short_preamble '0'
config wifi-iface 'wifinet1'
option device 'radio0'
option mode 'sta'
option ssid 'wifiname'
option bssid '3C:84:XX:XX:XX:XX'
option encryption 'psk2'
option key 'password'
option network 'wwan lan'
option disassoc_low_ack '0'
option short_preamble '0'
network on 192.168.1.2
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.1.2'
option defaultroute '0'
list dns '192.168.1.1'
option gateway '192.168.1.1'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 0t'
config interface 'wwan'
option proto 'dhcp'
config interface 'repeater_bridge'
option proto 'relay'
option ipaddr '192.168.1.2'
list network 'lan'
list network 'wwan'
firewall on 192.168.1.2
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'wwan'
list network 'repeater_bridge'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
I suspect it's a hardware problem? But maybe I'm wrong. What do you guys think?