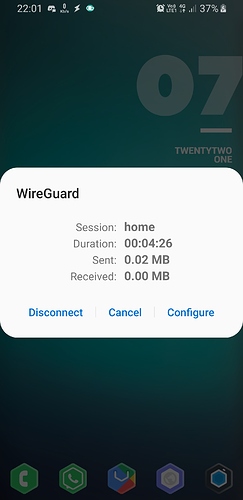
Handshake (server & client) is successful and there is transfer of minute data too in KBs but I'm unable to access internet nor LAN.
Server /etc/config/network (OpenWRT):
config interface 'wg0'
option proto 'wireguard'
option private_key 'xxxx'
option listen_port '1234'
list addresses '10.200.200.1/24'
config wireguard_wg0
option public_key 'qeGAK7sDFXVsiErMBEnR5N49YALbSzsPOcB37nfBFBw='
option route_allowed_ips '1'
option persistent_keepalive '25'
list allowed_ips '10.200.200.0/24'
option description 'home'
Client (Android):
[Interface]
Address = 10.200.200.2/24
DNS = 192.168.31.1
PrivateKey = xxxx
[Peer]
PublicKey = xxxx
AllowedIPs = 0.0.0.0/0, ::/0
Endpoint = [server]: ~~53591~~ 1234
PersistentKeepalive = 25
Output of wg
# wg show
interface: wg0
public key: Zgtbfjad3DG5DNS4G4txoswOR3smFAi9FeJVklhAET0=
private key: (hidden)
listening port: 1234
peer: qeGAK7sDFXVsiErMBEnR5N49YALbSzsPOcB37nfBFBw=
endpoint: 192.168.31.197:53591
allowed ips: 10.200.200.0/24
latest handshake: 3 minutes, 2 seconds ago
transfer: 11.94 KiB received, 29.75 KiB sent
persistent keepalive: every 25 seconds
Output of iptable -L -v i dont have much idea about iptables I've read it helped someone but I don't think I made any changes here.
I am been struggling to setup wireguard since long, please help!
Have you tried adding interface wg0 to a firewall zone and allow forwarding from there to both lan and wan?
2 Likes
Shouldn't the port number be 1234?
Change to 10.200.200.2/32.
Where is your firewall config for this?
If you didn't configure the Wireguard interface in the firewall, that's likely your issue.
You probably need to allow forwarding from WG-to-WAN and WG-to-LAN. Also, to open port 1234/udp on the OpenWrt
Look in /etc/config/firewall, no need to run the iptables command.
1 Like
Here is my complete firewall rules, I have added wg rule.
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan wg0'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config rule
option src 'lan'
option proto 'udp'
option dest_port '137-138'
option target 'ACCEPT'
config rule
option src 'lan'
option proto 'tcp'
option dest_port '139'
option target 'ACCEPT'
config rule
option src 'lan'
option proto 'tcp'
option dest_port '445'
option target 'ACCEPT'
config redirect 'adblock_dns_53'
option name 'Adblock DNS, port 53'
option src 'lan'
option proto 'tcp udp'
option src_dport '53'
option dest_port '53'
option target 'DNAT'
config redirect 'adblock_dns_853'
option name 'Adblock DNS, port 853'
option src 'lan'
option proto 'tcp udp'
option src_dport '853'
option dest_port '853'
option target 'DNAT'
config redirect 'adblock_dns_5353'
option name 'Adblock DNS, port 5353'
option src 'lan'
option proto 'tcp udp'
option src_dport '5353'
option dest_port '5353'
option target 'DNAT'
config zone
option name 'wg'
list network 'wg0'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
config forwarding
option src 'wg'
option dest 'wan'
config forwarding
option src 'wan'
option dest 'wg'
config forwarding
option src 'lan'
option dest 'wg'
config forwarding
option src 'wg'
option dest 'lan'
config rule
option name 'Allow-Wireguard-Inbound'
option target 'ACCEPT'
option src '*'
option proto 'udp'
option dest_port '1234'
It is 1234 I was messing aroung trying whatever I could, forgot to change before posting.
lleachii:
/etc/config/firewall
I have shared whole firewall rules in above comment, I guess I'm covering the points you mentioned.
1 Like
That seems quite dangerous.
OK, did you make the changes I noted about IPs addressing at the OpenWrt device?
1 Like
oops! What should I change it to?
Yes, on android I changed it to [publicIP]:1234
Yes done.
Now I think even handshake isn't happening
NoobestNoob:
Output of wg
Are you sure??? You change the allowed IPs under the peer, the interface should remain 10.200.200.1/24.
Remove it, you don't want people on the Internet access your tunnel.
NoobestNoob:
option masq '1'
Remove this from the WG zone if all IPs are addressed on your router (i.e. no downstream routers needed a static route). This could be the reason you can't access LAN.
You may wish to post your updated configs.
1 Like
/etc/config/network
config interface 'wg0'
option proto 'wireguard'
option private_key 'xxx'
option listen_port '1234'
list addresses '10.200.200.1/24'
config wireguard_wg0
option public_key 'xxx'
option route_allowed_ips '1'
option persistent_keepalive '25'
list allowed_ips '10.200.200.2
Completely removed this.
config forwarding
option src 'wan'
option dest 'wg'
config zone
option name 'wg'
list network 'wg0'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
Do you mean make it in to '0' or just simply remove it or change the zone?
I've never worked on FW ever please bare with me
Edit : I just noticed my mobile service provide is providing IPv6 on 4G network, does that need anything different method to config?
The principle is a bit different, but the result is similar , so try to use a more fault-tolerant method:
uci show config_name
NoobestNoob:
Completely removed this.
Fine.
In general case IPv4 and IPv6 should be tested independently to ensure they both work properly.
It doesn't look right to add an IPv6 route to the client with no IPv6 VPN address pool.
See also:
1 Like
I just realised that I am behind Carrier Grade NAT (CGNAT) is this the reason I am unable to connect?
What option do I have now?
FYI.. @lleachii @yousong @vgaetera
This is a problem in general case.
1 Like