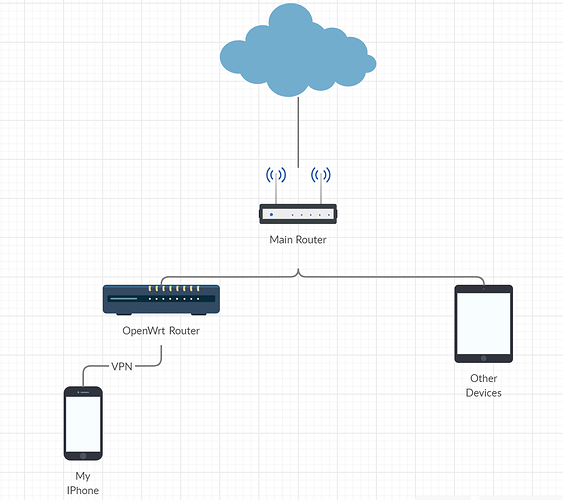
Hello,
I set up Wireguard on my OpenWRT and it did not work as intended.
I can connect and it shows my Wireguard connection in LuCI, but only some Bytes are transmitted.
I can also not ping any IP in my local network when connected via Wireguard.
What could be the issue here?
Thanks.
Network Config
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
option ula_prefix 'fddd:bb51:757f::/48'
config interface 'lan'
option type 'bridge'
option proto 'static'
option ipaddr '192.168.1.200'
option netmask '255.255.255.0'
option gateway '192.168.1.254'
option ifname 'eth0 lan1 lan2 lan3 lan4 wan'
list dns '192.168.1.254'
config device 'lan_lan1_dev'
option name 'lan1'
option macaddr '58:ef:68:fe:a5:e8'
config device 'lan_lan2_dev'
option name 'lan2'
option macaddr '58:ef:68:fe:a5:e8'
config device 'lan_lan3_dev'
option name 'lan3'
option macaddr '58:ef:68:fe:a5:e8'
config device 'lan_lan4_dev'
option name 'lan4'
option macaddr '58:ef:68:fe:a5:e8'
config device 'wan_wan_dev'
option name 'wan'
option macaddr '58:ef:68:fe:a5:e8'
config interface 'VPN'
option proto 'wireguard'
option private_key 'xxx='
option listen_port '55653'
config wireguard_VPN
option route_allowed_ips '1'
option endpoint_port '48136'
option public_key 'xxx='
option description 'Iphone'
list allowed_ips '192.168.1.50/32'
Firewall Config
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan VPN'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
option src 'lan'
config rule
option name 'Allow-Ping'
option proto 'icmp'
option family 'ipv4'
option target 'ACCEPT'
list icmp_type 'echo-request'
option src 'lan'
config rule
option name 'Allow-IGMP'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
option src 'lan'
config rule
option name 'Allow-DHCPv6'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
option src 'lan'
list src_ip 'fc00::/6'
list dest_ip 'fc00::/6'
config rule
option name 'Allow-MLD'
option proto 'icmp'
option family 'ipv6'
option target 'ACCEPT'
option src 'lan'
list src_ip 'fe80::/10'
config rule
option name 'Allow-ICMPv6-Input'
option proto 'icmp'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
list icmp_type 'destination-unreachable'
list icmp_type 'echo-reply'
list icmp_type 'echo-request'
list icmp_type 'neighbour-advertisement'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'router-solicitation'
list icmp_type 'time-exceeded'
option src 'lan'
config rule
option name 'Allow-ICMPv6-Forward'
option dest '*'
option proto 'icmp'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
list icmp_type 'destination-unreachable'
list icmp_type 'echo-reply'
list icmp_type 'echo-request'
list icmp_type 'time-exceeded'
option src 'lan'
config rule
option name 'Support-UDP-Traceroute'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
option src 'lan'
option dest_port '33434-33689'
config include
option path '/etc/firewall.user'
config redirect 'adblock_dns_53'
option name 'Adblock DNS, port 53'
option src 'lan'
option proto 'tcp udp'
option src_dport '53'
option dest_port '53'
option target 'DNAT'
config redirect 'adblock_dns_853'
option name 'Adblock DNS, port 853'
option src 'lan'
option proto 'tcp udp'
option src_dport '853'
option dest_port '853'
option target 'DNAT'
config redirect 'adblock_dns_5353'
option name 'Adblock DNS, port 5353'
option src 'lan'
option proto 'tcp udp'
option src_dport '5353'
option dest_port '5353'
option target 'DNAT'
config rule
option src 'lan'
option target 'ACCEPT'
NOTE: I know that that one firewall rule is a bad idea but it is only temporary.