voila and thank you ... heavy output / 
"kernel": "4.14.195",
"hostname": "OpenWrt",
"system": "ARMv7 Processor rev 1 (v7l)",
"model": "Linksys WRT1900ACS",
"board_name": "linksys,shelby",
"release": {
"distribution": "OpenWrt",
"version": "19.07.4",
"revision": "r11208-ce6496d796",
"target": "mvebu/cortexa9",
"description": "OpenWrt 19.07.4 r11208-ce6496d796
********
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdad:993d:9eff::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.2.1'
config interface 'wan'
option ifname 'eth1.2'
option proto 'dhcp'
config interface 'wan6'
option ifname 'eth1.2'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 1 2 3 5t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6t'
config interface 'WG1'
option proto 'wireguard'
list addresses 'x.x.x.x'
option private_key 'xxxx'
option force_link '1'
config interface 'WG2'
option proto 'wireguard'
list addresses 'x.x.x.x'
option private_key 'xxxx'
option force_link '1'
config wireguard_WG2
option persistent_keepalive '25'
option route_allowed_ips '1'
option endpoint_host 'xxx-wireguard.mullvad.net'
option public_key 'I02LwBnTb7aFrZSWvg4kb7zNW9/+rS6alnWy'
option description 'xxx'
list allowed_ips '0.0.0.0/0'
config interface 'guest'
option proto 'static'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
config wireguard_WG1
option public_key 'kWQ65FV7saXDZazA5htM0Fr/01FrUa5Mgyg4'
option description 'xxx'
option persistent_keepalive '25'
list allowed_ips '0.0.0.0/0'
option route_allowed_ips '1'
option endpoint_host 'xxx-wireguard.mullvad.net'
********
package wireless
config wifi-device 'radio0'
option type 'mac80211'
option hwmode '11a'
option path 'soc/soc:pcie/pci0000:00/0000:00:01.0/0000:01:00.0'
option country 'DE'
option channel 'auto'
option htmode 'VHT40'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option macaddr 'xx:xx:xx:xx:xx:xx'
option key 'password'
option ssid 'xxxx'
option encryption 'psk2'
config wifi-device 'radio1'
option type 'mac80211'
option hwmode '11g'
option path 'soc/soc:pcie/pci0000:00/0000:00:02.0/0000:02:00.0'
option country 'DE'
option htmode 'HT20'
option channel 'auto'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
option macaddr 'xx:xx:xx:xx:xx:xx'
option disabled '1'
config wifi-iface 'wifinet2'
option device 'radio1'
option mode 'ap'
option network 'lan'
option key 'password'
option ssid 'xxx'
option encryption 'psk2'
config wifi-iface 'wifinet3'
option device 'radio1'
option mode 'ap'
option network 'guest'
option key 'password'
option ssid 'xxxx'
option encryption 'psk2'
********
package dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option localservice '1'
list server 'wireguard DNS1'
list server 'wireguard DNS2'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
list dhcp_option '6,wireguard DNS1,wireguard DNS2'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config dhcp 'guest'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'guest'
list dns 'wireguard DNS1'
list dns 'wireguard DNS2'
list dhcp_option '6,wireguard DNS1,wireguard DNS2'
********
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
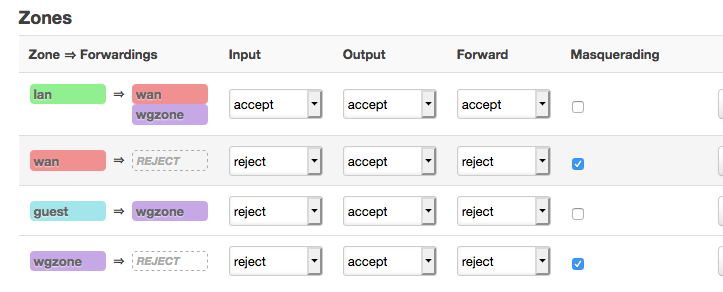
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option name 'guest'
option input 'REJECT'
option forward 'REJECT'
option output 'ACCEPT'
option network 'guest'
config rule
option dest_port '53'
option src 'guest'
option name 'Guest DNS'
option target 'ACCEPT'
config rule
option dest_port '67'
list proto 'udp'
option name 'Guest DHCP'
option target 'ACCEPT'
option src 'guest'
config forwarding
option dest 'wan'
option src 'lan'
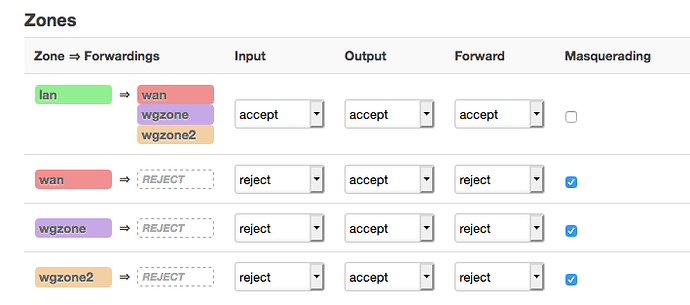
config zone
option mtu_fix '1'
option input 'REJECT'
option forward 'REJECT'
option masq '1'
option output 'ACCEPT'
option name 'wgzone1'
option network 'WG1'
config forwarding
option src 'lan'
option dest 'wgzone1'
config zone
option name 'wgzone2'
option mtu_fix '1'
option input 'REJECT'
option forward 'REJECT'
option masq '1'
option output 'ACCEPT'
option network 'WG2'
config forwarding
option dest 'wgzone2'
option src 'guest'
********
package vpn-policy-routing
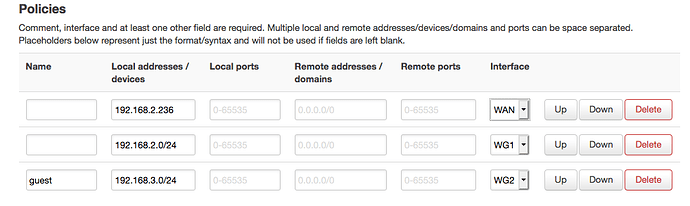
config policy
option src_addr '192.168.2.xxx'
option interface 'WG1'
config policy
option src_addr '192.168.2.0/24'
option interface 'WG1'
config vpn-policy-routing 'config'
option verbosity '2'
option strict_enforcement '1'
option src_ipset '0'
option dest_ipset 'dnsmasq.ipset'
option ipv6_enabled '0'
list supported_interface ''
list ignored_interface 'vpnserver wgserver'
option boot_timeout '30'
option iptables_rule_option 'append'
option iprule_enabled '0'
option webui_enable_column '0'
option webui_protocol_column '0'
option webui_chain_column '0'
option webui_sorting '1'
list webui_supported_protocol 'tcp'
list webui_supported_protocol 'udp'
list webui_supported_protocol 'tcp udp'
list webui_supported_protocol 'icmp'
list webui_supported_protocol 'all'
option enabled '1'
config include
option path '/etc/vpn-policy-routing.netflix.user'
option enabled '0'
config include
option path '/etc/vpn-policy-routing.aws.user'
option enabled '0'
config policy
option src_addr '192.168.3.0/24'
option interface 'WG2'
********
head -n -0 /etc/firewall.user;
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
********
# Generated by iptables-save v1.8.3 on Sat Sep 19 19:42:54 2020
*nat
:PREROUTING ACCEPT [1061:118543]
:INPUT ACCEPT [46:4292]
:OUTPUT ACCEPT [156:11447]
:POSTROUTING ACCEPT [53:3719]
:postrouting_guest_rule - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:postrouting_wgzone1_rule - [0:0]
:postrouting_wgzone2_rule - [0:0]
:prerouting_guest_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:prerouting_wgzone1_rule - [0:0]
:prerouting_wgzone2_rule - [0:0]
:zone_guest_postrouting - [0:0]
:zone_guest_prerouting - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
:zone_wgzone1_postrouting - [0:0]
:zone_wgzone1_prerouting - [0:0]
:zone_wgzone2_postrouting - [0:0]
:zone_wgzone2_prerouting - [0:0]
[1061:118543] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[402:65120] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[92:6510] -A PREROUTING -i eth1.2 -m comment --comment "!fw3" -j zone_wan_prerouting
[557:40847] -A PREROUTING -i wlan1-1 -m comment --comment "!fw3" -j zone_guest_prerouting
[10:6066] -A PREROUTING -i WG1 -m comment --comment "!fw3" -j zone_wgzone1_prerouting
[0:0] -A PREROUTING -i WG2 -m comment --comment "!fw3" -j zone_wgzone2_prerouting
[1015:91824] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[1:40] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[0:0] -A POSTROUTING -o eth1.2 -m comment --comment "!fw3" -j zone_wan_postrouting
[12:769] -A POSTROUTING -o wlan1-1 -m comment --comment "!fw3" -j zone_guest_postrouting
[312:46107] -A POSTROUTING -o WG1 -m comment --comment "!fw3" -j zone_wgzone1_postrouting
[650:41998] -A POSTROUTING -o WG2 -m comment --comment "!fw3" -j zone_wgzone2_postrouting
[12:769] -A zone_guest_postrouting -m comment --comment "!fw3: Custom guest postrouting rule chain" -j postrouting_guest_rule
[557:40847] -A zone_guest_prerouting -m comment --comment "!fw3: Custom guest prerouting rule chain" -j prerouting_guest_rule
[1:40] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[402:65120] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[0:0] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[0:0] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[92:6510] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j rerouting_wan_rule
[312:46107] -A zone_wgzone1_postrouting -m comment --comment "!fw3: Custom wgzone1 postrouting rule chain" -j postrouting_wgzone1_rule
[312:46107] -A zone_wgzone1_postrouting -m comment --comment "!fw3" -j MASQUERADE
[10:6066] -A zone_wgzone1_prerouting -m comment --comment "!fw3: Custom wgzone1 prerouting rule chain" -j prerouting_wgzone1_rule
[650:41998] -A zone_wgzone2_postrouting -m comment --comment "!fw3: Custom wgzone2 postrouting rule chain" -j postrouting_wgzone2_rule
[650:41998] -A zone_wgzone2_postrouting -m comment --comment "!fw3" -j MASQUERADE
[0:0] -A zone_wgzone2_prerouting -m comment --comment "!fw3: Custom wgzone2 prerouting rule chain" -j prerouting_wgzone2_rule
COMMIT
# Completed on Sat Sep 19 19:42:54 2020
# Generated by iptables-save v1.8.3 on Sat Sep 19 19:42:54 2020
*mangle
:PREROUTING ACCEPT [1075761:1586062923]
:INPUT ACCEPT [641457:727674760]
:FORWARD ACCEPT [434240:858371037]
:OUTPUT ACCEPT [634628:544617589]
:POSTROUTING ACCEPT [1068847:1402987250]
:VPR_FORWARD - [0:0]
:VPR_INPUT - [0:0]
:VPR_OUTPUT - [0:0]
:VPR_PREROUTING - [0:0]
[1075804:1586083807] -A PREROUTING -m mark --mark 0x0/0xff0000 -j VPR_PREROUTING
[640329:727574739] -A INPUT -m mark --mark 0x0/0xff0000 -j VPR_INPUT
[0:0] -A FORWARD -o eth1.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[0:0] -A FORWARD -i eth1.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[139:8340] -A FORWARD -o WG1 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wgzone1 MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[139:8340] -A FORWARD -i WG1 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wgzone1 MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[2188:139916] -A FORWARD -o WG2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wgzone2 MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[61:3660] -A FORWARD -i WG2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wgzone2 MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[160185:534530142] -A FORWARD -m mark --mark 0x0/0xff0000 -j VPR_FORWARD
[634642:544620573] -A OUTPUT -m mark --mark 0x0/0xff0000 -j VPR_OUTPUT
[0:0] -A VPR_FORWARD -m set --match-set WG2 dst -j MARK --set-xmark 0x30000/0xff0000
[0:0] -A VPR_FORWARD -m set --match-set WG1 dst -j MARK --set-xmark 0x20000/0xff0000
[0:0] -A VPR_FORWARD -m set --match-set wan dst -j MARK --set-xmark 0x10000/0xff0000
[0:0] -A VPR_INPUT -m set --match-set WG2 dst -j MARK --set-xmark 0x30000/0xff0000
[0:0] -A VPR_INPUT -m set --match-set WG1 dst -j MARK --set-xmark 0x20000/0xff0000
[0:0] -A VPR_INPUT -m set --match-set wan dst -j MARK --set-xmark 0x10000/0xff0000
[0:0] -A VPR_OUTPUT -m set --match-set WG2 dst -j MARK --set-xmark 0x30000/0xff0000
[0:0] -A VPR_OUTPUT -m set --match-set WG1 dst -j MARK --set-xmark 0x20000/0xff0000
[0:0] -A VPR_OUTPUT -m set --match-set wan dst -j MARK --set-xmark 0x10000/0xff0000
[159367:163883372] -A VPR_PREROUTING -s 192.168.3.0/24 -m comment --comment blank -j MARK --set-xmark 0x30000/0xff0000
[115911:160088686] -A VPR_PREROUTING -s 192.168.2.0/24 -m comment --comment blank -j MARK --set-xmark 0x20000/0xff0000
[115575:159957578] -A VPR_PREROUTING -s 192.168.2.236/32 -m comment --comment blank -j MARK --set-xmark 0x20000/0xff0000
[0:0] -A VPR_PREROUTING -m set --match-set WG2 dst -j MARK --set-xmark 0x30000/0xff0000
[0:0] -A VPR_PREROUTING -m set --match-set WG1 dst -j MARK --set-xmark 0x20000/0xff0000
[0:0] -A VPR_PREROUTING -m set --match-set wan dst -j MARK --set-xmark 0x10000/0xff0000
COMMIT
# Completed on Sat Sep 19 19:42:54 2020
# Generated by iptables-save v1.8.3 on Sat Sep 19 19:42:54 2020
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_guest_rule - [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:forwarding_wgzone1_rule - [0:0]
:forwarding_wgzone2_rule - [0:0]
:input_guest_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:input_wgzone1_rule - [0:0]
:input_wgzone2_rule - [0:0]
:output_guest_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:output_wgzone1_rule - [0:0]
:output_wgzone2_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_guest_dest_ACCEPT - [0:0]
:zone_guest_dest_REJECT - [0:0]
:zone_guest_forward - [0:0]
:zone_guest_input - [0:0]
:zone_guest_output - [0:0]
:zone_guest_src_REJECT - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
:zone_wgzone1_dest_ACCEPT - [0:0]
:zone_wgzone1_dest_REJECT - [0:0]
:zone_wgzone1_forward - [0:0]
:zone_wgzone1_input - [0:0]
:zone_wgzone1_output - [0:0]
:zone_wgzone1_src_REJECT - [0:0]
:zone_wgzone2_dest_ACCEPT - [0:0]
:zone_wgzone2_dest_REJECT - [0:0]
:zone_wgzone2_forward - [0:0]
:zone_wgzone2_input - [0:0]
:zone_wgzone2_output - [0:0]
:zone_wgzone2_src_REJECT - [0:0]
[196:19018] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[641341:727741368] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[641111:727720390] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[58:2796] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[20:2098] -A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
[153:9554] -A INPUT -i eth1.2 -m comment --comment "!fw3" -j zone_wan_input
[47:3260] -A INPUT -i wlan1-1 -m comment --comment "!fw3" -j zone_guest_input
[10:6066] -A INPUT -i WG1 -m comment --comment "!fw3" -j zone_wgzone1_input
[0:0] -A INPUT -i WG2 -m comment --comment "!fw3" -j zone_wgzone2_input
[434349:858466068] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[431722:858254786] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[366:66084] -A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i eth1.2 -m comment --comment "!fw3" -j zone_wan_forward
[2261:145198] -A FORWARD -i wlan1-1 -m comment --comment "!fw3" -j zone_guest_forward
[0:0] -A FORWARD -i WG1 -m comment --comment "!fw3" -j zone_wgzone1_forward
[0:0] -A FORWARD -i WG2 -m comment --comment "!fw3" -j zone_wgzone2_forward
[25:8123] -A FORWARD -m comment --comment "!fw3" -j reject
[196:19018] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[634493:544616359] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[634353:544605974] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[1:337] -A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
[0:0] -A OUTPUT -o eth1.2 -m comment --comment "!fw3" -j zone_wan_output
[1:329] -A OUTPUT -o wlan1-1 -m comment --comment "!fw3" -j zone_guest_output
[0:0] -A OUTPUT -o WG1 -m comment --comment "!fw3" -j zone_wgzone1_output
[138:9719] -A OUTPUT -o WG2 -m comment --comment "!fw3" -j zone_wgzone2_output
[76:3875] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[92:19176] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[58:2796] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[1:329] -A zone_guest_dest_ACCEPT -o wlan1-1 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_guest_dest_REJECT -o wlan1-1 -m comment --comment "!fw3" -j reject
[2261:145198] -A zone_guest_forward -m comment --comment "!fw3: Custom guest forwarding rule chain" -j forwarding_guest_rule
[2261:145198] -A zone_guest_forward -m comment --comment "!fw3: Zone guest to wgzone2 forwarding policy" -j zone_wgzone2_dest_ACCEPT
[0:0] -A zone_guest_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_guest_forward -m comment --comment "!fw3" -j zone_guest_dest_REJECT
[47:3260] -A zone_guest_input -m comment --comment "!fw3: Custom guest input rule chain" -j input_guest_rule
[0:0] -A zone_guest_input -p tcp -m tcp --dport 53 -m comment --comment "!fw3: Guest DNS" -j ACCEPT
[0:0] -A zone_guest_input -p udp -m udp --dport 53 -m comment --comment "!fw3: Guest DNS" -j ACCEPT
[1:328] -A zone_guest_input -p udp -m udp --dport 67 -m comment --comment "!fw3: Guest DHCP" -j ACCEPT
[0:0] -A zone_guest_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[46:2932] -A zone_guest_input -m comment --comment "!fw3" -j zone_guest_src_REJECT
[1:329] -A zone_guest_output -m comment --comment "!fw3: Custom guest output rule chain" -j output_guest_rule
[1:329] -A zone_guest_output -m comment --comment "!fw3" -j zone_guest_dest_ACCEPT
[46:2932] -A zone_guest_src_REJECT -i wlan1-1 -m comment --comment "!fw3" -j reject
[1:337] -A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
[366:66084] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[366:66084] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[366:66084] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wgzone1 forwarding policy" -j zone_wgzone1_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[25:8123] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[20:2098] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[20:2098] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[1:337] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[1:337] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[20:2098] -A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_ACCEPT -o eth1.2 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[0:0] -A zone_wan_dest_ACCEPT -o eth1.2 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o eth1.2 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[153:9554] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[26:2184] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[40:1440] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[87:5930] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[0:0] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[0:0] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[87:5930] -A zone_wan_src_REJECT -i eth1.2 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wgzone1_dest_ACCEPT -o WG1 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[341:57961] -A zone_wgzone1_dest_ACCEPT -o WG1 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wgzone1_dest_REJECT -o WG1 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wgzone1_forward -m comment --comment "!fw3: Custom wgzone1 forwarding rule chain" -j forwarding_wgzone1_rule
[0:0] -A zone_wgzone1_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wgzone1_forward -m comment --comment "!fw3" -j zone_wgzone1_dest_REJECT
[10:6066] -A zone_wgzone1_input -m comment --comment "!fw3: Custom wgzone1 input rule chain" -j input_wgzone1_rule
[0:0] -A zone_wgzone1_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[10:6066] -A zone_wgzone1_input -m comment --comment "!fw3" -j zone_wgzone1_src_REJECT
[0:0] -A zone_wgzone1_output -m comment --comment "!fw3: Custom wgzone1 output rule chain" -j output_wgzone1_rule
[0:0] -A zone_wgzone1_output -m comment --comment "!fw3" -j zone_wgzone1_dest_ACCEPT
[10:6066] -A zone_wgzone1_src_REJECT -i WG1 -m comment --comment "!fw3" -j reject
[21:1376] -A zone_wgzone2_dest_ACCEPT -o WG2 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[2378:153541] -A zone_wgzone2_dest_ACCEPT -o WG2 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wgzone2_dest_REJECT -o WG2 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wgzone2_forward -m comment --comment "!fw3: Custom wgzone2 forwarding rule chain" -j forwarding_wgzone2_rule
[0:0] -A zone_wgzone2_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wgzone2_forward -m comment --comment "!fw3" -j zone_wgzone2_dest_REJECT
[0:0] -A zone_wgzone2_input -m comment --comment "!fw3: Custom wgzone2 input rule chain" -j input_wgzone2_rule
[0:0] -A zone_wgzone2_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[0:0] -A zone_wgzone2_input -m comment --comment "!fw3" -j zone_wgzone2_src_REJECT
[138:9719] -A zone_wgzone2_output -m comment --comment "!fw3: Custom wgzone2 output rule chain" -j output_wgzone2_rule
[138:9719] -A zone_wgzone2_output -m comment --comment "!fw3" -j zone_wgzone2_dest_ACCEPT
[0:0] -A zone_wgzone2_src_REJECT -i WG2 -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Sat Sep 19 19:42:54 2020
********
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
7: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.2.1/24 brd 192.168.2.255 scope global br-lan
valid_lft forever preferred_lft forever
9: eth1.2@eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.1.246/24 brd 192.168.1.255 scope global eth1.2
valid_lft forever preferred_lft forever
18: wlan1-1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
inet 192.168.3.1/24 brd 192.168.3.255 scope global wlan1-1
valid_lft forever preferred_lft forever
21: WG1: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN group default qlen 1000
inet xx.xxx.149.36/32 brd 255.255.255.255 scope global WG1
valid_lft forever preferred_lft forever
23: WG2: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN group default qlen 1000
inet xx.xxx.228.64/32 brd 255.255.255.255 scope global WG2
valid_lft forever preferred_lft forever
default via 192.168.1.1 dev eth1.2 table 201
192.168.3.0/24 dev wlan1-1 table 201 proto kernel scope link src 192.168.3.1
default via xx.xxx.149.36 dev WG1 table 202
192.168.3.0/24 dev wlan1-1 table 202 proto kernel scope link src 192.168.3.1
default via xx.xxx.228.64 dev WG2 table 203
192.168.3.0/24 dev wlan1-1 table 203 proto kernel scope link src 192.168.3.1
default dev WG2 proto static scope link
x.x.x.x via 192.168.1.1 dev eth1.2 proto static
192.168.1.0/24 dev eth1.2 proto kernel scope link src 192.168.1.246
192.168.2.0/24 dev br-lan proto kernel scope link src 192.168.2.1
192.168.3.0/24 dev wlan1-1 proto kernel scope link src 192.168.3.1
x.x.x.x dev WG1 proto static scope link
local x.x.x.x dev WG1 table local proto kernel scope host src x.x.x.x
local x.x.x.x dev WG2 table local proto kernel scope host src x.x.x.x
broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
broadcast 192.168.1.0 dev eth1.2 table local proto kernel scope link src 192.168.1.246
local 192.168.1.246 dev eth1.2 table local proto kernel scope host src 192.168.1.246
broadcast 192.168.1.255 dev eth1.2 table local proto kernel scope link src 192.168.1.246
broadcast 192.168.2.0 dev br-lan table local proto kernel scope link src 192.168.2.1
local 192.168.2.1 dev br-lan table local proto kernel scope host src 192.168.2.1
broadcast 192.168.2.255 dev br-lan table local proto kernel scope link src 192.168.2.1
broadcast 192.168.3.0 dev wlan1-1 table local proto kernel scope link src 192.168.3.1
local 192.168.3.1 dev wlan1-1 table local proto kernel scope host src 192.168.3.1
broadcast 192.168.3.255 dev wlan1-1 table local proto kernel scope link src 192.168.3.1
0: from all lookup local
32748: from all fwmark 0x30000/0xff0000 lookup 203
32749: from all fwmark 0x20000/0xff0000 lookup 202
32750: from all fwmark 0x10000/0xff0000 lookup 201
32766: from all lookup main
32767: from all lookup default
********