Hello there!
I am trying to switch to wireguard as my go-to tunneling option since I'm very impressed with the speeds I get when connected to my wireguard server. Basically, I had setup openvpn on my server and my openwrt router would connect to it as a client and use that as the default interface for internet connections. I followed mullvad's guide and I can basically ping and get connected when in CLI in the openwrt router but the clients connected over WiFi are not able to access any internet services, even though I can resolve hostnames. I basically copied the firewall part of the working vpn interface and applied it to the wireguard interface but still I get no connection when connected on WiFi. I cannot confirm if the LAN interface is working since I only have one ethernet cable and that's hooked to the WAN interface which is connected to my ISP's router on the other end.
I'm I missing anything? Been scratching my head the last two days and none of the posts helped me out. I even tried the routing suggestion but none worked.
Best regards
root@OpenWrt:/etc/config# cat network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdcf:1010:1010:1010:/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device 'lan_dev'
option name 'eth0.1'
option macaddr '60:ZZ:ZZ:ZZ:ZZ:ec'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
option peerdns '0'
option dns '84.200.70.40'
config device 'wan_dev'
option name 'eth0.2'
option macaddr '60:ZZ:ZZ:ZZ:ZZ:ed'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0 6t'
config interface 'vpnclient'
option ifname 'tun0'
option proto 'none'
option delegate '0'
config interface 'wireguard'
option proto 'wireguard'
option private_key 'yAu...X='
option listen_port '44444'
list addresses '10.10.1.20/30'
list addresses '10.10.2.20/30'
option delegate '0'
option force_link '1'
config wireguard_wireguard
option public_key 'K...EY='
list allowed_ips '0.0.0.0/0'
option endpoint_host 'my.wg.srv'
option endpoint_port '44444'
option persistent_keepalive '15'
option route_allowed_ips '1'
root@OpenWrt:/etc/config# cat firewall
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option src '*'
option target 'ACCEPT'
option dest_port '44444'
option name 'Allow-Wireguard-Inbound'
option proto 'tcp udp'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config include
option path '/etc/firewall.user'
config zone
option name 'vpnclient'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'vpnclient'
config zone
option name 'wireguard'
option forward 'REJECT'
option output 'ACCEPT'
option network 'wireguard'
option input 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option dest 'wireguard'
option src 'lan'
root@OpenWrt:/etc/config# cat vpn-policy-routing
config vpn-policy-routing 'config'
option verbosity '2'
option ipv6_enabled '0'
option ipset_enabled '1'
option dnsmasq_enabled '0'
option strict_enforcement '1'
option enabled '1'
config policy
option name '1.1'
option local_addresses '10.10.1.1/24'
option remote_addresses '0.0.0.0/0'
option proto 'tcp udp'
option chain 'FORWARD'
option interface 'wireguard'
config policy
option name '2.1'
option local_addresses '10.10.2.1/24'
option remote_addresses '0.0.0.0/0'
option proto 'tcp udp'
option chain 'FORWARD'
option interface 'wireguard'
root@OpenWrt:/etc/config# cat dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option nonwildcard '1'
option localservice '1'
list server '172.31.100.1'
list server '10.10.1.1'
list server '1.1.1.1'
option noresolv '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
root@OpenWrt:/etc/config# ip route show
default dev wireguard proto static scope link
10.10.1.20/30 dev wireguard proto kernel scope link src 10.10.1.20
10.10.2.20/30 dev wireguard proto kernel scope link src 10.10.2.20
my.wg.srv via 192.168.2.1 dev eth0.2 proto static
192.168.1.0/24 dev br-lan proto kernel scope link src 192.168.1.1
192.168.2.0/24 dev eth0.2 proto kernel scope link src 192.168.2.101
root@OpenWrt:/etc/config# route -ne
Kernel IP routing table
Destination Gateway Genmask Flags MSS Window irtt Iface
0.0.0.0 0.0.0.0 0.0.0.0 U 0 0 0 wireguard
10.10.1.20 0.0.0.0 255.255.255.252 U 0 0 0 wireguard
10.10.2.20 0.0.0.0 255.255.255.252 U 0 0 0 wireguard
my.wg.srv 192.168.2.1 255.255.255.255 UGH 0 0 0 eth0.2
192.168.1.0 0.0.0.0 255.255.255.0 U 0 0 0 br-lan
192.168.2.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0.2
root@OpenWrt:/etc/config# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN group default qlen 1000
link/ether 60:ZZ:ZZ:ZZ:ZZ:ec brd ff:ff:ff:ff:ff:ff
inet6 fe80:ff:ff:ff:ff:6dec/64 scope link
valid_lft forever preferred_lft forever
18: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 60:ZZ:ZZ:ZZ:ZZ:ec brd ff:ff:ff:ff:ff:ff
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
inet6 fdcf:1c21:6539::1/60 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 fe80:ff:ff:ff:ff:6dec/64 scope link
valid_lft forever preferred_lft forever
19: eth0.1@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP group default qlen 1000
link/ether 60:ZZ:ZZ:ZZ:ZZ:ec brd ff:ff:ff:ff:ff:ff
20: eth0.2@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 60:ZZ:ZZ:ZZ:ZZ:ed brd ff:ff:ff:ff:ff:ff
inet 192.168.2.101/24 brd 192.168.2.255 scope global eth0.2
valid_lft forever preferred_lft forever
inet6 fe80:ff:ff:ff:ff:6ded/64 scope link
valid_lft forever preferred_lft forever
22: wlan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP group default qlen 1000
link/ether 60:ZZ:ZZ:ZZ:ZZ:eb brd ff:ff:ff:ff:ff:ff
inet6 fe80:ff:ff:ff:ff:6deb/64 scope link
valid_lft forever preferred_lft forever
23: wlan1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq master br-lan state UP group default qlen 1000
link/ether 60:ZZ:ZZ:ZZ:ZZ:ea brd ff:ff:ff:ff:ff:ff
inet6 fe80:ff:ff:ff:ff:6dea/64 scope link
valid_lft forever preferred_lft forever
24: wireguard: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN group default qlen 1000
link/none
inet 10.10.1.20/30 brd 10.10.1.23 scope global wireguard
valid_lft forever preferred_lft forever
inet 10.10.2.20/30 brd 10.10.2.23 scope global wireguard
valid_lft forever preferred_lft forever
root@OpenWrt:/etc/config# ip route show table all
default via 192.168.2.1 dev eth0.2 table 201
unreachable default table 202
default via 10.10.1.20 dev wireguard table 203
default dev wireguard proto static scope link
10.10.1.20/30 dev wireguard proto kernel scope link src 10.10.1.20
10.10.2.20/30 dev wireguard proto kernel scope link src 10.10.2.20
my.wg.srv via 192.168.2.1 dev eth0.2 proto static
192.168.1.0/24 dev br-lan proto kernel scope link src 192.168.1.1
192.168.2.0/24 dev eth0.2 proto kernel scope link src 192.168.2.101
local 10.10.1.20 dev wireguard table local proto kernel scope host src 10.10.1.20
broadcast 10.10.1.20 dev wireguard table local proto kernel scope link src 10.10.1.20
broadcast 10.10.1.23 dev wireguard table local proto kernel scope link src 10.10.1.20
local 10.10.2.20 dev wireguard table local proto kernel scope host src 10.10.2.20
broadcast 10.10.2.20 dev wireguard table local proto kernel scope link src 10.10.2.20
broadcast 10.10.2.23 dev wireguard table local proto kernel scope link src 10.10.2.20
broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
broadcast 192.168.1.0 dev br-lan table local proto kernel scope link src 192.168.1.1
local 192.168.1.1 dev br-lan table local proto kernel scope host src 192.168.1.1
broadcast 192.168.1.255 dev br-lan table local proto kernel scope link src 192.168.1.1
broadcast 192.168.2.0 dev eth0.2 table local proto kernel scope link src 192.168.2.101
local 192.168.2.101 dev eth0.2 table local proto kernel scope host src 192.168.2.101
broadcast 192.168.2.255 dev eth0.2 table local proto kernel scope link src 192.168.2.101
fdcf:1010:1010:1010:/64 dev br-lan proto static metric 1024 pref medium
unreachable fdcf:1010:1010:1010:/48 dev lo proto static metric 2147483647 error -148 pref medium
fe80::/64 dev eth0 proto kernel metric 256 pref medium
fe80::/64 dev eth0.2 proto kernel metric 256 pref medium
fe80::/64 dev br-lan proto kernel metric 256 pref medium
fe80::/64 dev wlan1 proto kernel metric 256 pref medium
fe80::/64 dev wlan0 proto kernel metric 256 pref medium
local ::1 dev lo table local proto kernel metric 0 pref medium
anycast fdcf:1c21:6539:: dev br-lan table local proto kernel metric 0 pref medium
local fdcf:1c21:6539::1 dev br-lan table local proto kernel metric 0 pref medium
anycast fe80:: dev eth0.2 table local proto kernel metric 0 pref medium
anycast fe80:: dev eth0 table local proto kernel metric 0 pref medium
anycast fe80:: dev br-lan table local proto kernel metric 0 pref medium
anycast fe80:: dev wlan1 table local proto kernel metric 0 pref medium
anycast fe80:: dev wlan0 table local proto kernel metric 0 pref medium
local fe80:ff:ff:ff:ff:6dea dev wlan1 table local proto kernel metric 0 pref medium
local fe80:ff:ff:ff:ff:6deb dev wlan0 table local proto kernel metric 0 pref medium
local fe80:ff:ff:ff:ff:6dec dev eth0 table local proto kernel metric 0 pref medium
local fe80:ff:ff:ff:ff:6dec dev br-lan table local proto kernel metric 0 pref medium
local fe80:ff:ff:ff:ff:6ded dev eth0.2 table local proto kernel metric 0 pref medium
ff00::/8 dev eth0 table local metric 256 pref medium
ff00::/8 dev br-lan table local metric 256 pref medium
ff00::/8 dev eth0.2 table local metric 256 pref medium
ff00::/8 dev wireguard table local metric 256 pref medium
ff00::/8 dev wlan1 table local metric 256 pref medium
ff00::/8 dev wlan0 table local metric 256 pref medium
root@OpenWrt:/etc/config# ip rule show
0: from all lookup local
32760: from all fwmark 0x30000 lookup 203
32761: from all fwmark 0x20000 lookup 202
32762: from all fwmark 0x10000 lookup 201
32766: from all lookup main
32767: from all lookup default
root@OpenWrt:/etc/config# ip netconf
ipv4 dev lo forwarding on rp_filter off mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off
ipv4 dev eth0 forwarding on rp_filter off mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off
ipv4 dev br-lan forwarding on rp_filter off mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off
ipv4 dev eth0.1 forwarding on rp_filter off mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off
ipv4 dev eth0.2 forwarding on rp_filter off mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off
ipv4 dev wlan0 forwarding on rp_filter off mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off
ipv4 dev wlan1 forwarding on rp_filter off mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off
ipv4 dev wireguard forwarding on rp_filter off mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off
ipv4 all forwarding on rp_filter off mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off
ipv4 default forwarding on rp_filter off mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off
ipv6 dev lo forwarding on mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off
ipv6 dev eth0 forwarding on mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off
ipv6 dev br-lan forwarding on mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off
ipv6 dev eth0.1 forwarding on mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off
ipv6 dev eth0.2 forwarding on mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off
ipv6 dev wlan0 forwarding on mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off
ipv6 dev wlan1 forwarding on mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off
ipv6 dev wireguard forwarding on mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off
ipv6 all forwarding on mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off
ipv6 default forwarding on mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off
root@OpenWrt:/etc/config# wg
interface: wireguard
public key: Nk...UU=
private key: (hidden)
listening port: 44444
peer: K...EY=
endpoint: my.wg.srv:44444
allowed ips: 0.0.0.0/0
transfer: 579.97 KiB received, 78.79 KiB sent
persistent keepalive: every 15 seconds
root@OpenWrt:/etc/config# ifconfig -a
br-lan Link encap:Ethernet HWaddr 60:ZZ:ZZ:ZZ:ZZ:EC
inet addr:192.168.1.1 Bcast:192.168.1.255 Mask:255.255.255.0
inet6 addr: fdcf:1010:1010:1010:1/60 Scope:Global
inet6 addr: fe80:ff:ff:ff:ff:6dec/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:4043 errors:0 dropped:0 overruns:0 frame:0
TX packets:3282 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:335485 (327.6 KiB) TX bytes:858898 (838.7 KiB)
eth0 Link encap:Ethernet HWaddr 60:ZZ:ZZ:ZZ:ZZ:EC
inet6 addr: fe80:ff:ff:ff:ff:6dec/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:2032 errors:0 dropped:0 overruns:0 frame:0
TX packets:1426 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:891010 (870.1 KiB) TX bytes:225942 (220.6 KiB)
Interrupt:5
eth0.1 Link encap:Ethernet HWaddr 60:ZZ:ZZ:ZZ:ZZ:EC
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:66 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:9402 (9.1 KiB)
eth0.2 Link encap:Ethernet HWaddr 60:ZZ:ZZ:ZZ:ZZ:ED
inet addr:192.168.2.101 Bcast:192.168.2.255 Mask:255.255.255.0
inet6 addr: fe80:ff:ff:ff:ff:6ded/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:1318 errors:0 dropped:0 overruns:0 frame:0
TX packets:790 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:763251 (745.3 KiB) TX bytes:117084 (114.3 KiB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:7 errors:0 dropped:0 overruns:0 frame:0
TX packets:7 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:816 (816.0 B) TX bytes:816 (816.0 B)
wireguard Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.10.1.20 P-t-P:10.10.1.20 Mask:255.255.255.252
UP POINTOPOINT RUNNING NOARP MTU:1420 Metric:1
RX packets:743 errors:0 dropped:54 overruns:0 frame:0
TX packets:756 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:594876 (580.9 KiB) TX bytes:82188 (80.2 KiB)
wlan0 Link encap:Ethernet HWaddr 60:ZZ:ZZ:ZZ:ZZ:EB
inet6 addr: fe80:ff:ff:ff:ff:6deb/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:34 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:6904 (6.7 KiB)
wlan1 Link encap:Ethernet HWaddr 60:ZZ:ZZ:ZZ:ZZ:EA
inet6 addr: fe80:ff:ff:ff:ff:6dea/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:4042 errors:0 dropped:0 overruns:0 frame:0
TX packets:3326 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:392067 (382.8 KiB) TX bytes:932958 (911.0 KiB)
Here is the output of wg show on the "server side"
# wg show
interface: wg0
public key: K...EY=
private key: (hidden)
listening port: 13582
peer: Nk...UU=
endpoint: <MY ISP IP HERE>:44444
allowed ips: 10.10.2.20/30, 10.10.1.20/30
latest handshake: 54 seconds ago
transfer: 109.54 KiB received, 677.35 KiB sent
peer: I...iDk=
allowed ips: 10.10.2.8/30, 10.10.1.8/30
I can connect directly to the "server" from my pc using wireguard and can use it as my "vpn tunnel", i.e. I am seen as using the "server" ip and dns.
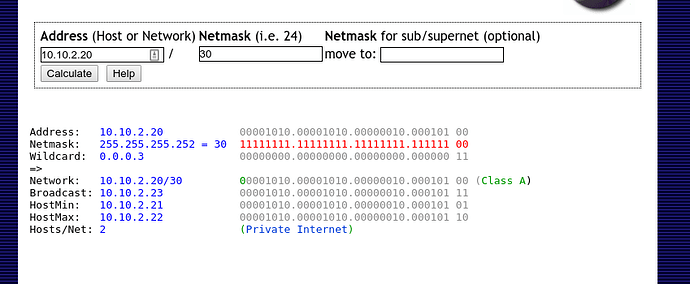

 One day I will read up on how addressing works and get a better config that can handle more clients dynamically.
One day I will read up on how addressing works and get a better config that can handle more clients dynamically. thanks a lot! Have a nice one and keep on doing the good work you are doing here!
thanks a lot! Have a nice one and keep on doing the good work you are doing here!