I don't think eduroam qualifies as an ISP
Spot on.
"eduroam", as an entity, is a federated authentication platform that spans the EU and UK higher (and further, in some cases) education networks. In simple terms it permits the use of network resources at participating sites via the use of (usually, but not exclusively) certificate-based authentication from the home site.
TL;DR - if you're a student whose home institution participates in eduroam, you can visit other sites and transparently connect to their networks.
You do, however, remain bound by the terms and conditions of the cascaded networks - both your home site, the site you're connected to, their upstream network, and so on all the way up to the country you're in at the time. As most HE sites are in receipt of public funding, they're not treated as commercial carriers and have additional laws to abide by (the most obvious for me being the UK's "PREVENT" ant-terrorism laws). The net neutrality laws do not apply.
I've got SoftEther up and running on OpenWRT and works fine on my Windows client but I seem to face trouble with configuring SSTP on Android... I'm currently using this for reference
But it seem really confusing. Not sure if anyone here has setup SSTP with Android?
unfortunately we can't really help you with the android setup as it's not related to what is forum is about - openwrt ![]() - maybe try opening an issue on that github repo or a topic on xda-developers forum
- maybe try opening an issue on that github repo or a topic on xda-developers forum
...
LE: and there is the SoftEther VPN User Forum (vpnusers.com)
Okay, I feel like I'm completely stranded. I didn't check it with Windows's built-in MS-SSTP and now it's just saying the signature of the certificate cannot be verified. Seems much harder to diagnose it compared to Wireguard...
there is a nice softethervpn app gui for windows using their own ssl backed vpn protocol that should be easier to use than SSTP there but unfortunately no client for android/ios - only option there is SSTP for bypassing DPI firewalls
It really is frustrating. I've sent a ticket to my IT support and still no response yet. I've only found X-ray core and TUIC protocols working just fine bypassing the firewall.
Is it possible to use this script? https://github.com/mack-a/v2ray-agent
yeap - showsocks forks (or even the original update one) can be successfully used (they have easy to use mobile apps as well)
as for apps written for the users behind GFW (China) I wouldn't use it for the simple fact we (people not speaking chinease) are not the intended audience ![]()
I've tried and tested this script on a VPS and it just worked fine but I'm not sure how well it can co-relate it with an OpenWRT router as there are iptables and other related commands.
This is the English version which is a bit outdated but does the same job. Just paranoid that this script might break some functionality without my knowledge...
better use this Guide: Shadowsocks setup on OpenWrt for beginners
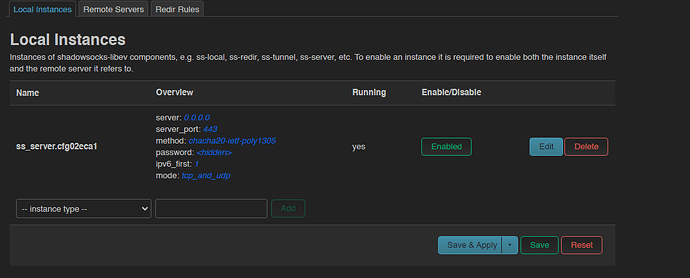
I've currently only setup Local Instances as follows
root@OpenWrt:~# cat /var/etc/shadowsocks-libev/ss_server.cfg02eca1.json
{
"server": "0.0.0.0",
"server_port": 443,
"method": "chacha20-ietf-poly1305",
"password": "test",
"use_syslog": true,
"ipv6_first": true,
"fast_open": false,
"reuse_port": false,
"no_delay": false,
"mode": "tcp_and_udp"
}
I've removed the rest of the dummy configs on Local and Remote interfaces.
Do I need to configure anything else like Plugin options?
Also in this guide when setting up the server
On the Luci panel, I cannot seem to bind it to listen on both IPv6 and IPv4 addresses. But on that guide, it says how to enable so. I'm a bit confused as to whether I should delete the LuCI config and just create my own in the terminal and use ss-server to run that instead.
May I add something else here please. Now we've established that the problem isn't with eduroam but with the firewall policies your university has set up, you may want to consider the reasons they are doing that.
The problem with lots of enthousiastic young minds is that more often than one hopes, they result in network security incidents, which may take a lot of time to address. To reduce the amount of effort to keep a student-network running, firewalls are typically set up to reduce the chance of these security incidents.
Wireguard is a VPN tool. You are trying to use a tool to bypass the firewall limits your university has set up. If you are "found out" (and keep in mind your network access isn't anonymous!), chances are you will receive a royal slap on the wrist for bypassing these measures. And that slap on your wrist may impact your ability to access university resources, i.e. it may affect your university career.
You may want to reflect why you want to bypass the university firewall. My experience is that if you step forward, tell what you want to do and why, you will find network operators willing to cooperate and collaborate and no need to run firewall bypass VPN tricks. As posted by greem, give the admin a positive surprise by reaching out.
At the same time, if you want to run wireguard for something illicit, whether you get wireguard or similar working, if you are caught doing something illicit, don't be surprised if the university simply removes network access to you. And you will have to deal with the consequences of not being able to continue your study.
When you were issued your network access, I'm sure that at some point in time you were asked to review and acknowledge some Network Access Policy. Before spending more time in trying to bypass the university firewall, my advice to you would be to review that policy so that it is clear what the consequences of your actions might be and how this might impact your study.
I sugest opening a new thread with your shadowsocks issue
I've put forward a constructive ticket to my university's IT support team and they've replied saying they don't provide VPN access to unmanaged devices and to use a key server to access university resources from outside network (which I'm not sure how it's relevant to unblocking Wireguard or maybe other VPN services from the university's firewall to access my home devices).
The firewall rules keep changing, they've blocked Steam in an attempt to prevent people from using their network to play in hopes that it would boost student engagement but this year they've unblocked it which I'm not sure why. nothing is set in stone.
The usage of VPN here in this country is an offence but it's sort of a grey area here where unless you're going to broadcast outside that you using a VPN and for downloading banned content here the police wouldn't bother knocking you're door down. Anyway, my main purpose is to access my home devices and not to access restricted content whether it's at my home or university's ground.
I could always just port forward my applications and access it within the university and be done with it but that would expose a much larger attack surface to the internet. It's only worth using this as a last resort.
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.