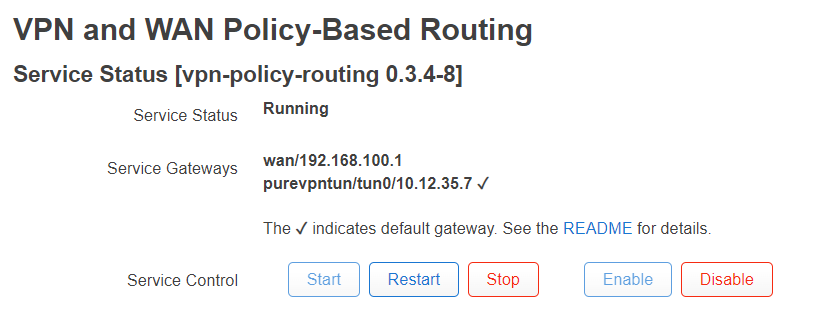
Hi, I am new to OpenWrt. I would like the 2.5G wifi to be an AP with vpn access (OpenVPN). The rest (LANs) and 1 wifi AP should be for no-vpn internet & local access. I have been trying to solve this issue over the last four days but in vain. Currently, I have only one network working, one wifi (MS_V). It connects via vpn and accepts clients. The LANs and the other wifi are not working at all. My pc connects to the router via the wifi(MS_5) but no internet. Traceroute shows "OpenWrt.lan [192.168.1.1] reports: Destination protocol unreachable." I would really appreciate any help here. Here are my configs.
dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
option start '100'
option limit '150'
option leasetime '12h'
list ra_flags 'none'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'wifi'
option interface 'wifi'
option start '100'
option limit '150'
option leasetime '12h'
list ra_flags 'none'
firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
config zone
option name 'wifi'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
list network 'wifi'
config forwarding
option src 'wifi'
option dest 'wan'
config zone
option name 'vpnfirewall'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'purevpntun'
config forwarding
option src 'wifi'
option dest 'vpnfirewall'
Network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd45:8ac9:08cf::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option device 'br-lan'
config device
option name 'wan'
option macaddr '32:23:03:db:d9:e0'
config interface 'wan'
option device 'wan'
option proto 'static'
option ipaddr '192.168.100.3'
option netmask '255.255.255.0'
option gateway '192.168.100.1'
option broadcast '192.168.100.255'
option type 'bridge'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
config interface 'purevpntun'
option proto 'none'
option device 'tun0'
option ifname 'tun0'
config interface 'wifi'
option proto 'static'
option ipaddr '192.168.20.1'
option netmask '255.255.255.0'
option gateway '192.168.100.1'
option broadcast '192.168.20.255'
option type 'bridge'
option device 'wlan1'
wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'soc/soc:pcie/pci0000:00/0000:00:01.0/0000:01:00.0'
option channel '36'
option band '5g'
option htmode 'VHT80'
option cell_density '0'
option country 'OM'
config wifi-iface 'default_radio0'
option device 'radio0'
option mode 'ap'
option macaddr '30:23:03:db:d9:e2'
option ssid 'MS_5'
option encryption 'psk2'
option key '20003000'
option network 'lan'
config wifi-device 'radio1'
option type 'mac80211'
option path 'soc/soc:pcie/pci0000:00/0000:00:02.0/0000:02:00.0'
option channel '1'
option band '2g'
option cell_density '0'
option country 'OM'
option htmode 'HT40'
config wifi-iface 'default_radio1'
option device 'radio1'
option mode 'ap'
option macaddr '30:23:03:db:d9:e1'
option ssid 'MS_V'
option encryption 'psk2'
option key '20003000'
option network 'wifi'
config wifi-device 'radio2'
option type 'mac80211'
option path 'platform/soc/soc:internal-regs/f10d8000.sdhci/mmc_host/mmc0/mmc0:0001/mmc0:0001:1'
option channel '34'
option band '5g'
option htmode 'VHT80'
option cell_density '0'
config wifi-iface 'default_radio2'
option device 'radio2'
option mode 'ap'
option encryption 'psk2'
option key '20003000'
option network 'lan'
option ssid 'MS_55'