Researchers have since discovered a flaw in WPA that relied on older weaknesses in WEP and the limitations of the message integrity code hash function, named Michael, to retrieve the keystream from short packets to use for re-injection and spoofing.[5][6]
Well, WEP ![]() isn't supported anymore by openwrt but by that would indicate that
isn't supported anymore by openwrt but by that would indicate that WEP would also be considered "medium security"? by openwrt? ![]()
Yes, it does still stand and no, there isn't really any good reason to use WPA in 2022. Use WPA2, unless you literally cannot, because you have some fricking ancient system that doesn't support it.
What I don't understand then why to "promote" it in the way that it would be enough secure ("medium security")? From my point of view that means it is actually secure because it's not weak. But in reality it just all comes down to the complexity and length of the key (which isn't mentioned) and there is also no hint that a 8 digit key for example is weak - like the hint you get when filling out the router password form:

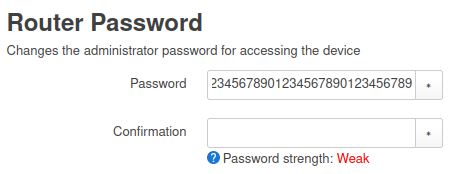
So I could choose the "medium security" WPA-PSK with a (weak) 8-digit long key that can be "hacked" in maybe 100 seconds by just sniffing a handshake and cracking it locally against a wordlist. For me this is like the opposite from secure.
You might wanna laugh but I used to own a device that was only capable of working with WEP ![]() and well, no fricking way that I would downgrade my wifi to make it work for it. Same would apply for me to WPA too.
and well, no fricking way that I would downgrade my wifi to make it work for it. Same would apply for me to WPA too.
I would say use WPA3, unless you cannot. In that case WPA2 is still a viable option. But WPA or even WEP in 2022 shouldn't really be promoted by any means IMHO.
In my experience, WPA3 is unuseable still. At least most of my devices refuse to function with it, while WPA2 works perfectly well. Most people have an older device here and there that won't work with WPA3, which is why I don't yet recommend it.
Same for me, so I stick with WPA2 at the moment which should be a secure option specially when also opting in for some additional protection (like 802.11w Management Frame Protection or key reinstallation (KRACK) countermeasures).
But to tell someone to downgrade his WIFI to WPA (with the same weak RC4 cipher base that WEP used btw.) because a device can't speak WPA2?
I would say no way! ![]()
If your device can't connect to a WPA2 AP than just wire that device or replace it with a more recent one (from like the last ~18 years) that supports WPA2 but don't ever downgrade your wifi to WPA or WEP, better than just go with a open network (no encryption) because than there is no doubt about any "security" ![]()
So I just made a test setup with the "medium security" settings exactly like in the screenshot using a ready made python script which possession could be already a crime in various countries (so I don't bother naming or linking it here) and it took around 80 seconds to have the pre shared key printed in the terminal. Cracking the captured handshake was blazing fast (Cracking WPA Handshake: 100.00% ETA: 0s @ 18711.5kps) and most time consuming is actually the script running and de-authing of the clients (not sure why but the script waits quite a long time before doing that).
Also mentioning that this is probably not the most efficient way - some preferred methods like the PMKID attack were skipped by the script b because missing tools installed on my system.
So should this still really still be called medium security without even checking for a weak key (like it is done already with the router password)![]()
I always thought it was naught but a reminder to the user to employ the most secure method capable with his/her situation and equipment. In my user case Open works just fine.
did you try emojis in the password ? ![]()
I didn't because...
and if you look closely you will see that the key field ![]()

only contains numbers (![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]() )
)
It's also not really about how to improve the strength of the pre shared key here (that can be done reasonable well within the 63 character limit) but why the "false impression" by the openwrt luci gui is given that such a setup with a 8-digit-key (which can be "hacked" in 80 seconds) is considered still in the category "medium security" ![]()
Just thinking that this RC4 encryption algorithm used by WPA (and WEP) is already considered unsafe since many years and probably all major browser have it treated as "unsecure" or even disabled by default already for TLS ![]()
So others asked already (years ago) to add "weak" or "insecure" instead of the misleading "medium security" to WPA-PSK (with it's default RC4 based TKIP cipher).
http://dev.archive.openwrt.org/ticket/18120
Same is true for the WPA-PSK/WPA2-PSK mixed mode because it's always about the weakest link
Turns out the year was 2016 (that was 6 years ago!) were all major browsers (firefox, chrome, edge/ie) disabled RC4 because it was considered already insecure back then. Guess the "Numerous Occurrence MOnitoring & Recovery Exploit" from 2015 was the last nail in the ![]() for this chiper.... or not quite yet when using openwrt
for this chiper.... or not quite yet when using openwrt ![]()
We can break a WPA-TKIP network within an hour. More precisely, after successfully executing the attack, an attacker can decrypt and inject arbitrary packets
https://www.rc4nomore.com/#faq
Guess because of the weak cipher even with a 63 long and very complex passphrase a WPA-PSK (with default TKIP cipher) setup openwrt device can be exploited within an hour ![]() (yes, the one with the "medium security"
(yes, the one with the "medium security" ![]() )
)
As there is apparently no interest in changing this "situation" this topic can get closed ![]()
meaning you are not interested in changing the situation?
I don't have the rights to do so and the only thing some one holding that power was doing in this thread was to change the wording from openwrt to OpenWrt. For me that indicates lack of interest ![]()
For sure the step of marking WPA insecure could also be directly omitted and it could be directly be deleted from the official builds (like WEP). I'm not aware of any device that does support WPA but at the same time doesn't support WPA2 (for WEP that was a different case but it is already long gone....) ![]()
why not make your own build with that option?
I don't need that because I'm aware of the (in)security of WPA and would never consider it a option to use.
This was mend for a broader audience (official builds) who one may will think - "medium security" sounds good I'll take that - without knowing that they have choosen the weakest possible option which could be defeated within an hour (with the default RC4 encryption algorithm) even when they choose a very complex 63 long pre shared key ![]()
anyone with their head on their shoulder will obviously choose strong security if they aren't using really old devices.
I only came to know devices that only supported WEP and not WPA.
At the same time all devices (I touched) that supported WPA also supported WPA2 (which was shortly introduced after WPA btw.)
So "really old devices" (WEP only) are not supported anymore because WEP is gone already from openwrt.
I wonder what leads to the decision to remove WEP but keep RC4 based WPA at the same time ![]()
These labels were added a while ago because people complained that all crypto choices were listed without giving any indication of their strength. Back then, the range was WEP to WPA2, so WEP was dubbed low, WPA medium and WPA2 strong.
That clarifies a lot! Thank's for this information. So it's just "out of date" (like 10 years or more) some one could say ![]()