Hello,
I'd like to ask for help in configuring traffic forward from WAN interface to OpenConnect VPN client, the task sounds not complicated, but it fact nothing works.
So i have 2 routers, main router that is connected to ISP (192.168.0.0\24) which is WAN and OpenWrt (192.168.1.0\24) that has OpenConnect VPN client configured.
Ideally the routes i need to forward to VPN are set in default route on the main router (192.168.0.1\24).
The OpenConnect VPN client is connected to the Cisco AnyConnect VPN concentrator, all good, can get an echo reply from the DNS servers (10.124.128.51, 10.124.128.52) when testing on OpenWrt router, but no response on clients behind the WAN zone.
The WAN zone has no firewall restrictions, seems here should be about routing, but i can't figure out then how it needs to be routed.
The goal is for OpenWrt to connect to the Cisco AnyConnect VPN server instead of connecting on client machines.
Here are the OpenWrt router configs:
# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default 192.168.0.1 0.0.0.0 UG 0 0 0 eth1
10.8.0.0 * 255.255.255.0 U 0 0 0 tun0
10.14.0.0 * 255.255.255.0 U 0 0 0 wg0
10.14.0.3 * 255.255.255.255 UH 0 0 0 wg0
10.124.0.0 * 255.255.255.0 U 0 0 0 vpn-dc0
10.124.126.64 * 255.255.255.192 U 0 0 0 vpn-dc0
10.124.128.51 * 255.255.255.255 UH 0 0 0 vpn-dc0
10.124.128.52 * 255.255.255.255 UH 0 0 0 vpn-dc0
10.124.146.0 * 255.255.255.0 U 0 0 0 vpn-dc0
172.26.250.26 * 255.255.255.255 UH 0 0 0 vpn-dc0
172.30.192.0 * 255.255.255.0 U 0 0 0 vpn-dc0
192.168.0.0 * 255.255.255.0 U 0 0 0 eth1
192.168.0.1 * 255.255.255.255 UH 0 0 0 eth1
192.168.1.0 * 255.255.255.0 U 0 0 0 br-lan
192.168.144.0 * 255.255.255.0 U 0 0 0 vpn-dc0
xx.xx.xx.xx 192.168.0.1 255.255.255.255 UGH 0 0 0 eth1
# ip r
default via 192.168.0.1 dev eth1 proto static src 192.168.0.2
10.8.0.0/24 dev tun0 proto kernel scope link src 10.8.0.1
10.14.0.0/24 dev wg0 proto kernel scope link src 10.14.0.1
10.14.0.3 dev wg0 proto static scope link
10.124.0.0/24 dev vpn-dc0 scope link
10.124.126.64/26 dev vpn-dc0 scope link
10.124.128.51 dev vpn-dc0 scope link
10.124.128.52 dev vpn-dc0 scope link
10.124.146.0/24 dev vpn-dc0 scope link
172.26.250.26 dev vpn-dc0 scope link
172.30.192.0/24 dev vpn-dc0 scope link
192.168.0.0/24 dev eth1 proto kernel scope link src 192.168.0.2
192.168.0.1 dev eth1 proto static scope link src 192.168.0.2
192.168.1.0/24 dev br-lan proto kernel scope link src 192.168.1.1 linkdown
192.168.144.0/24 dev vpn-dc0 scope link
xx.xx.xx.xx via 192.168.0.1 dev eth1 proto static
/etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fde9:a910:0a44::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option ifname 'eth1'
option proto 'dhcp'
config interface 'wan6'
option ifname 'eth1'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 0'
config interface 'vpn0'
option ifname 'tun0'
option proto 'none'
option auto '1'
config interface 'wg0'
option proto 'wireguard'
option listen_port '51820'
option private_key 'xxx'
list addresses '10.14.0.1/24'
config wireguard_wg0
option route_allowed_ips '1'
option persistent_keepalive '25'
option public_key 'xxx'
list allowed_ips '10.14.0.3/32'
config interface 'dc0'
option proto 'openconnect'
option port '443'
option username 'xxx'
option password 'xxx'
option auto '0'
option no_dtls '1'
option server 'xxx'
option usergroup 'xxx'
/etc/config/firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
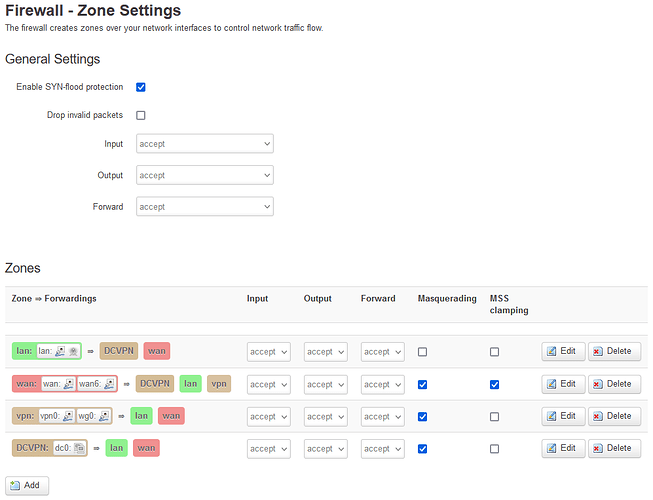
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option input 'ACCEPT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
option forward 'ACCEPT'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config rule
option name 'Allow-OpenVPN-Inbound'
option target 'ACCEPT'
option src 'wan'
option proto 'udp'
option dest_port '1194'
config zone
option name 'vpn'
option input 'ACCEPT'
option forward 'ACCEPT'
option output 'ACCEPT'
option masq '1'
option network 'vpn0 wg0'
config forwarding
option src 'vpn'
option dest 'lan'
config rule
option name 'Allow-OpenVPN-Inbound'
option target 'ACCEPT'
option src 'wan'
option proto 'tcp'
option dest_port '443'
config rule
option src '*'
option target 'ACCEPT'
option proto 'udp'
option dest_port '51820'
option name 'Allow-Wireguard-Inbound'
config zone
option name 'DCVPN'
option input 'ACCEPT'
option output 'ACCEPT'
option network 'dc0'
option masq '1'
option forward 'ACCEPT'
config forwarding
option dest 'lan'
option src 'DCVPN'
config forwarding
option dest 'DCVPN'
option src 'lan'
config forwarding
option dest 'DCVPN'
option src 'wan'
config forwarding
option dest 'lan'
option src 'wan'
config forwarding
option dest 'vpn'
option src 'wan'
config forwarding
option dest 'wan'
option src 'DCVPN'
config forwarding
option dest 'wan'
option src 'lan'
config forwarding
option dest 'wan'
option src 'vpn'
Routing table /etc/iproute2/rt_tables
#
# reserved values
#
128 prelocal
255 local
254 main
253 default
0 unspec
#
# local
#
#1 inr.ruhep
PING tests:
On OpenWrt router:
# ping 10.124.128.51
PING 10.124.128.51 (10.124.128.51): 56 data bytes
64 bytes from 10.124.128.51: seq=0 ttl=127 time=9.415 ms
64 bytes from 10.124.128.51: seq=1 ttl=127 time=8.904 ms
64 bytes from 10.124.128.51: seq=2 ttl=127 time=8.952 ms
64 bytes from 10.124.128.51: seq=3 ttl=127 time=8.884 ms
^C
--- 10.124.128.51 ping statistics ---
4 packets transmitted, 4 packets received, 0% packet loss
round-trip min/avg/max = 8.884/9.038/9.415 ms
# ping 10.124.128.52
PING 10.124.128.52 (10.124.128.52): 56 data bytes
64 bytes from 10.124.128.52: seq=0 ttl=127 time=8.908 ms
64 bytes from 10.124.128.52: seq=1 ttl=127 time=8.669 ms
64 bytes from 10.124.128.52: seq=2 ttl=127 time=8.997 ms
64 bytes from 10.124.128.52: seq=3 ttl=127 time=9.674 ms
^C
--- 10.124.128.52 ping statistics ---
4 packets transmitted, 4 packets received, 0% packet loss
round-trip min/avg/max = 8.669/9.062/9.674 ms
On another client machine:
$ ping 10.124.128.51
PING 10.124.128.51 (10.124.128.51) 56(84) bytes of data.
^C
--- 10.124.128.51 ping statistics ---
5 packets transmitted, 0 received, 100% packet loss, time 4097ms
$ traceroute 10.124.128.51
traceroute to 10.124.128.51 (10.124.128.51), 30 hops max, 60 byte packets
1 192.168.0.2 (192.168.0.2) 3.894 ms 4.282 ms 4.607 ms
2 * * *
3 * * *
4 * * *
5 * * *
6 * * *
7 * * *
8 * * *
9 * * *
10 * * *
11 * * *
12 * * *
13 * * *
14 * * *
15 * * *
16 * * *
17 * * *
18 * * *
19 * * *
20 * * *
21 * * *
22 * * *
23 * * *
24 * * *
25 * * *
26 * * *
27 * * *
28 * * *
29 * * *
30 * * *
I hope i'm not missing anything.
I'm really stuck here for some time and looking forward for any help.
Thank You.