You can't set your WAN's DHCP lease time (unless the WAN is connected to an upstream router that you control). If the WAN is directly connected to the ISP's network, it is the DHCP server from the ISP that controls this value. If your ISP is really issuing 1h leases, that is pretty short.
wan lease times of 5 minutes are common with ISP's that have pool contraints.
while not to spec. it's possible and often a feasible workaround for upstream renewal congestion on short leases to alter the lease times client side (lower).
usually there are no problem with the lease time, I've tried restarting the wan from UCI under normal condition after restart and it gets the IP address, only in random after almost a day or sometimes more the problem occured (I try to get the log when it occured again).
Ouch! If they're so constrained that they need to renew leases at that rate, it doesn't bode well for their service reliability since it would potentially imply that a certain percentage of clients would be bumped off the network with some regularity. I can totally understand this in a cafe type setting, but from an ISP, it just seems nuts. But I can believe it.
yeah... it's only just while checking this thread i see my ISP bumped theirs back up from 5 mins to 30. no wonder the issues mostly disappeared.
Here's the system log I get before suddenly losing wan connection :
Mon Jul 6 19:43:27 2020 daemon.notice netifd: wan (1548): udhcpc: sending renew to 10.x.x.x
Mon Jul 6 19:43:27 2020 daemon.notice netifd: wan (1548): udhcpc: lease of 10.x.x.x obtained, lease time 3600
the above log kept repeating and I still get wan ip address but no internet at all, so I restart the wan interface from luci and get this log :
Mon Jul 6 19:52:41 2020 daemon.notice netifd: wan (1548): udhcpc: received SIGTERM
Mon Jul 6 19:52:41 2020 daemon.notice netifd: wan (1548): udhcpc: unicasting a release of 10.88.205.47 to 10.88.192.1
Mon Jul 6 19:52:41 2020 daemon.notice netifd: wan (1548): udhcpc: sending release
Mon Jul 6 19:52:41 2020 daemon.notice netifd: wan (1548): udhcpc: entering released state
Mon Jul 6 19:52:41 2020 daemon.notice netifd: wan (1548): Command failed: Permission denied
Mon Jul 6 19:52:41 2020 daemon.notice netifd: Interface 'wan' is now down
Mon Jul 6 19:52:41 2020 daemon.notice netifd: Interface 'wan' is setting up now
Mon Jul 6 19:52:41 2020 daemon.info dnsmasq[417]: reading /tmp/resolv.conf.d/resolv.conf.auto
Mon Jul 6 19:52:41 2020 daemon.info dnsmasq[417]: using only locally-known addresses for domain test
Mon Jul 6 19:52:41 2020 daemon.info dnsmasq[417]: using only locally-known addresses for domain onion
Mon Jul 6 19:52:41 2020 daemon.info dnsmasq[417]: using only locally-known addresses for domain localhost
Mon Jul 6 19:52:41 2020 daemon.info dnsmasq[417]: using only locally-known addresses for domain local
Mon Jul 6 19:52:41 2020 daemon.info dnsmasq[417]: using only locally-known addresses for domain invalid
Mon Jul 6 19:52:41 2020 daemon.info dnsmasq[417]: using only locally-known addresses for domain bind
Mon Jul 6 19:52:41 2020 daemon.info dnsmasq[417]: using only locally-known addresses for domain lan
Mon Jul 6 19:52:41 2020 daemon.info dnsmasq[417]: using nameserver 192.x.x.x#53
Mon Jul 6 19:52:41 2020 daemon.notice netifd: wan (24595): udhcpc: started, v1.31.1
Mon Jul 6 19:52:41 2020 daemon.notice netifd: wan (24595): udhcpc: sending discover
Mon Jul 6 19:52:44 2020 daemon.notice netifd: wan (24595): udhcpc: sending discover
Mon Jul 6 19:52:47 2020 daemon.notice netifd: wan (24595): udhcpc: sending discover
Only after I reboot the router that the internet connection restored.
What is your OpenWrt lan address set to?
wan address set to another private ip address 10.x.x.x.x (NAT by ISP gateway) which changes everytime both the ip and gateway, currently it's 10.88.205.47/19. I might want to test back to old config which sets the ISP modem not as bridge (default), but that will make it triple NAT'ed.
If you are observing that the ISP is using 10.0.0.0/8 for the addresses they hand out to the customers, try making your router 192.168.x.0/24 -- this will avoid the situation where both your LAN and your WAN have the same subnet.
actually my LAN already set to 192.168.x.0/24
ah... gottcha. Forget that one 
While I wouldn't recommend triple NAT (double NAT on your end + NAT from the ISP), I honestly don't think it'll be much of an issue since you already don't have a public IP in the first place. It would be interesting to see if the same problem WAN drop occurs on the ISP's router.
also would be good to know what exact release/version you are currently running...?
I'm using openwrt snapshot version for raspberry pi 4, just sysupgrade to july 5th version (kernel 5.4.50) and the problem still persist although I suspect the problem maybe in my ISP since I've used snapshot version for almost 2 months and the problem only appear this last week and almost everyday.
I think I found the problem, not the ISP as I thought, but after unplugging usb ethernet (which act as eth1 / wan) and plugging it again, the connection restored, I use asix-ax88179 based usb to gigabit chipset.
Now to check why it does like that (usually it doesn't behave like this).
My router seemed to behaving itself, then we had a glitch today when I was at my laptop and so I could capture the logs: Does anything in here offer a clue?
Tue Jul 14 18:59:51 2020 daemon.info pppd[14928]: No response to 5 echo-requests
Tue Jul 14 18:59:51 2020 daemon.notice pppd[14928]: Serial link appears to be disconnected.
Tue Jul 14 18:59:51 2020 daemon.info pppd[14928]: Connect time 3910.8 minutes.
Tue Jul 14 18:59:51 2020 daemon.info pppd[14928]: Sent 2380758582 bytes, received 1112916776 bytes.
Tue Jul 14 18:59:51 2020 daemon.debug pppd[14928]: Script /lib/netifd/ppp-down started (pid 21503)
Tue Jul 14 18:59:51 2020 daemon.notice netifd: Network device 'pppoe-wan' link is down
Tue Jul 14 18:59:51 2020 daemon.notice netifd: Network alias 'pppoe-wan' link is down
Tue Jul 14 18:59:51 2020 daemon.notice netifd: Interface 'wan6' has link connectivity loss
Tue Jul 14 18:59:51 2020 daemon.err odhcp6c[15094]: Failed to send RS (Permission denied)
Tue Jul 14 18:59:51 2020 daemon.err odhcp6c[15094]: Failed to send DHCPV6 message to ff02::1:2 (Permission denied)
Tue Jul 14 18:59:51 2020 daemon.debug pppd[14928]: Script /lib/netifd/ppp-down started (pid 21507)
Tue Jul 14 18:59:51 2020 daemon.debug pppd[14928]: sent [LCP TermReq id=0x2 "Peer not responding"]
Tue Jul 14 18:59:52 2020 daemon.notice netifd: Interface 'wan' has lost the connection
Tue Jul 14 18:59:52 2020 daemon.notice netifd: Interface 'wan6' is disabled
Tue Jul 14 18:59:52 2020 daemon.warn dnsmasq[30025]: no servers found in /tmp/resolv.conf.auto, will retry
Tue Jul 14 18:59:52 2020 daemon.debug pppd[14928]: Script /lib/netifd/ppp-down finished (pid 21507), status = 0x1
Tue Jul 14 18:59:52 2020 daemon.debug pppd[14928]: Script /lib/netifd/ppp-down finished (pid 21503), status = 0x1
Tue Jul 14 18:59:52 2020 daemon.notice netifd: wan6 (15094): Command failed: Permission denied
Tue Jul 14 18:59:52 2020 daemon.err odhcp6c[15094]: Failed to send DHCPV6 message to ff02::1:2 (Permission denied)
Tue Jul 14 18:59:54 2020 daemon.debug pppd[14928]: sent [LCP TermReq id=0x3 "Peer not responding"]
Tue Jul 14 18:59:57 2020 kern.warn kernel: [2104898.681296] leave showtime
Tue Jul 14 18:59:57 2020 daemon.notice netifd: Network device 'dsl0' link is down
Tue Jul 14 18:59:57 2020 daemon.notice netifd: VLAN 'dsl0.101' link is down
Tue Jul 14 18:59:57 2020 daemon.notice netifd: Interface 'wan' has link connectivity loss
Tue Jul 14 18:59:57 2020 daemon.info dnsmasq-dhcp[30025]: DHCPREQUEST(br-lan) 192.168.157.197 00:df:00:00:0e:1a
Tue Jul 14 18:59:57 2020 daemon.info dnsmasq-dhcp[30025]: DHCPACK(br-lan) 192.168.157.197 00:df:00:00:0e:1a
Tue Jul 14 18:59:57 2020 daemon.info pppd[14928]: Terminating on signal 15
Tue Jul 14 18:59:57 2020 daemon.notice pppd[14928]: Connection terminated.
Tue Jul 14 18:59:57 2020 daemon.debug pppd[14928]: Send PPPOE Discovery V1T1 PADT session 0xcfa length 20
Tue Jul 14 18:59:57 2020 daemon.debug pppd[14928]: dst 40:7c:7d:49:fc:35 src 00:37:b7:27:68:ed
Tue Jul 14 18:59:57 2020 daemon.debug pppd[14928]: [AC-cookie 48 54 56 00 d9 4e b7 8c e9 23 01 23 49 86 0b 71]
Tue Jul 14 18:59:57 2020 daemon.info pppd[14928]: Sent PADT
Tue Jul 14 18:59:57 2020 daemon.notice pppd[14928]: Modem hangup
Tue Jul 14 18:59:57 2020 daemon.info pppd[14928]: Exit.
Tue Jul 14 19:00:32 2020 daemon.notice netifd: Network device 'dsl0' link is up
Tue Jul 14 19:00:32 2020 daemon.notice netifd: VLAN 'dsl0.101' link is up
Tue Jul 14 19:00:32 2020 daemon.notice netifd: Interface 'wan' has link connectivity
Tue Jul 14 19:00:32 2020 daemon.notice netifd: Interface 'wan' is setting up now
Tue Jul 14 19:00:32 2020 kern.warn kernel: [2104934.206879] enter showtime
Tue Jul 14 19:00:32 2020 kern.warn kernel: [2104934.218306] enter showtime
Tue Jul 14 19:00:32 2020 daemon.err insmod: module is already loaded - slhc
Tue Jul 14 19:00:32 2020 daemon.err insmod: module is already loaded - ppp_generic
Tue Jul 14 19:00:32 2020 daemon.err insmod: module is already loaded - pppox
Tue Jul 14 19:00:32 2020 daemon.err insmod: module is already loaded - pppoe
Tue Jul 14 19:00:32 2020 daemon.info pppd[21836]: Plugin rp-pppoe.so loaded.
Tue Jul 14 19:00:32 2020 daemon.info pppd[21836]: RP-PPPoE plugin version 3.8p compiled against pppd 2.4.7
Tue Jul 14 19:00:33 2020 daemon.notice pppd[21836]: pppd 2.4.7 started by root, uid 0
Tue Jul 14 19:00:33 2020 daemon.debug pppd[21836]: Send PPPOE Discovery V1T1 PADI session 0x0 length 4
Tue Jul 14 19:00:33 2020 daemon.debug pppd[21836]: dst ff:ff:ff:ff:ff:ff src 00:37:b7:27:68:ed
Tue Jul 14 19:00:33 2020 daemon.debug pppd[21836]: [service-name]
Tue Jul 14 19:00:38 2020 daemon.debug pppd[21836]: Send PPPOE Discovery V1T1 PADI session 0x0 length 4
Tue Jul 14 19:00:38 2020 daemon.debug pppd[21836]: dst ff:ff:ff:ff:ff:ff src 00:37:b7:27:68:ed
Tue Jul 14 19:00:38 2020 daemon.debug pppd[21836]: [service-name]
Tue Jul 14 19:00:43 2020 daemon.debug pppd[21836]: Send PPPOE Discovery V1T1 PADI session 0x0 length 4
Tue Jul 14 19:00:43 2020 daemon.debug pppd[21836]: dst ff:ff:ff:ff:ff:ff src 00:37:b7:27:68:ed
Tue Jul 14 19:00:43 2020 daemon.debug pppd[21836]: [service-name]
Tue Jul 14 19:00:43 2020 daemon.info dnsmasq-dhcp[30025]: DHCPINFORM(br-lan) 192.168.157.162 c8:5b:76:8b:ac:a3
Tue Jul 14 19:00:43 2020 daemon.info dnsmasq-dhcp[30025]: DHCPACK(br-lan) 192.168.157.162 c8:5b:76:8b:ac:a3 L17-00136
Tue Jul 14 19:00:43 2020 daemon.info dnsmasq-dhcp[30025]: DHCPINFORM(br-lan) 192.168.157.162 c8:5b:76:8b:ac:a3
Tue Jul 14 19:00:43 2020 daemon.info dnsmasq-dhcp[30025]: DHCPACK(br-lan) 192.168.157.162 c8:5b:76:8b:ac:a3 L17-00136
Tue Jul 14 19:00:48 2020 daemon.warn pppd[21836]: Timeout waiting for PADO packets
Tue Jul 14 19:00:48 2020 daemon.err pppd[21836]: Unable to complete PPPoE Discovery
Tue Jul 14 19:00:48 2020 daemon.info pppd[21836]: Exit.
Tue Jul 14 19:00:48 2020 daemon.notice netifd: Interface 'wan' is now down
Tue Jul 14 19:00:48 2020 daemon.notice netifd: Interface 'wan' is disabled
Tue Jul 14 19:00:48 2020 daemon.notice netifd: Interface 'wan' is enabled
Tue Jul 14 19:00:48 2020 daemon.notice netifd: Interface 'wan' is setting up now
Tue Jul 14 19:00:48 2020 daemon.err insmod: module is already loaded - slhc
Tue Jul 14 19:00:48 2020 daemon.err insmod: module is already loaded - ppp_generic
Tue Jul 14 19:00:48 2020 daemon.err insmod: module is already loaded - pppox
Tue Jul 14 19:00:48 2020 daemon.err insmod: module is already loaded - pppoe
Tue Jul 14 19:00:48 2020 daemon.info pppd[21947]: Plugin rp-pppoe.so loaded.
Tue Jul 14 19:00:48 2020 daemon.info pppd[21947]: RP-PPPoE plugin version 3.8p compiled against pppd 2.4.7
Tue Jul 14 19:00:48 2020 daemon.notice pppd[21947]: pppd 2.4.7 started by root, uid 0
Tue Jul 14 19:00:48 2020 daemon.debug pppd[21947]: Send PPPOE Discovery V1T1 PADI session 0x0 length 4
Tue Jul 14 19:00:48 2020 daemon.debug pppd[21947]: dst ff:ff:ff:ff:ff:ff src 00:37:b7:27:68:ed
Tue Jul 14 19:00:48 2020 daemon.debug pppd[21947]: [service-name]
Tue Jul 14 19:00:53 2020 daemon.debug pppd[21947]: Send PPPOE Discovery V1T1 PADI session 0x0 length 4
Tue Jul 14 19:00:53 2020 daemon.debug pppd[21947]: dst ff:ff:ff:ff:ff:ff src 00:37:b7:27:68:ed
Tue Jul 14 19:00:53 2020 daemon.debug pppd[21947]: [service-name]
Tue Jul 14 19:00:57 2020 daemon.info dnsmasq-dhcp[30025]: DHCPREQUEST(br-lan) 192.168.157.197 00:df:00:00:0e:1a
Tue Jul 14 19:00:57 2020 daemon.info dnsmasq-dhcp[30025]: DHCPACK(br-lan) 192.168.157.197 00:df:00:00:0e:1a
Tue Jul 14 19:00:58 2020 daemon.debug pppd[21947]: Send PPPOE Discovery V1T1 PADI session 0x0 length 4
Tue Jul 14 19:00:58 2020 daemon.debug pppd[21947]: dst ff:ff:ff:ff:ff:ff src 00:37:b7:27:68:ed
Tue Jul 14 19:00:58 2020 daemon.debug pppd[21947]: [service-name]
Tue Jul 14 19:01:03 2020 daemon.warn pppd[21947]: Timeout waiting for PADO packets
Tue Jul 14 19:01:03 2020 daemon.err pppd[21947]: Unable to complete PPPoE Discovery
Tue Jul 14 19:01:03 2020 daemon.info pppd[21947]: Exit.
Tue Jul 14 19:01:03 2020 daemon.notice netifd: Interface 'wan' is now down
Tue Jul 14 19:01:03 2020 daemon.notice netifd: Interface 'wan' is disabled
Tue Jul 14 19:01:03 2020 daemon.notice netifd: Interface 'wan' is enabled
Tue Jul 14 19:01:03 2020 daemon.notice netifd: Interface 'wan' is setting up now
Tue Jul 14 19:01:04 2020 daemon.err insmod: module is already loaded - slhc
Tue Jul 14 19:01:04 2020 daemon.err insmod: module is already loaded - ppp_generic
Tue Jul 14 19:01:04 2020 daemon.err insmod: module is already loaded - pppox
Tue Jul 14 19:01:04 2020 daemon.err insmod: module is already loaded - pppoe
Tue Jul 14 19:01:04 2020 daemon.info pppd[22096]: Plugin rp-pppoe.so loaded.
Tue Jul 14 19:01:04 2020 daemon.info pppd[22096]: RP-PPPoE plugin version 3.8p compiled against pppd 2.4.7
Tue Jul 14 19:01:04 2020 daemon.notice pppd[22096]: pppd 2.4.7 started by root, uid 0
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: Send PPPOE Discovery V1T1 PADI session 0x0 length 4
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: dst ff:ff:ff:ff:ff:ff src 00:37:b7:27:68:ed
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: [service-name]
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: Recv PPPOE Discovery V1T1 PADO session 0x0 length 41
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: dst 00:37:b7:27:68:ed src 40:7c:7d:49:fc:35
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: [service-name] [AC-name acc-aln3.bb-c] [AC-cookie 48 54 56 00 d9 4e b7 8c e9 23 01 23 49 86 0b 71]
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: Send PPPOE Discovery V1T1 PADR session 0x0 length 24
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: dst 40:7c:7d:49:fc:35 src 00:37:b7:27:68:ed
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: [service-name] [AC-cookie 48 54 56 00 d9 4e b7 8c e9 23 01 23 49 86 0b 71]
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: Recv PPPOE Discovery V1T1 PADS session 0x16d9 length 4
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: dst 00:37:b7:27:68:ed src 40:7c:7d:49:fc:35
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: [service-name]
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: PADS: Service-Name: ''
Tue Jul 14 19:01:04 2020 daemon.info pppd[22096]: PPP session is 5849
Tue Jul 14 19:01:04 2020 daemon.warn pppd[22096]: Connected to 40:7c:7d:49:fc:35 via interface dsl0.101
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: using channel 20
Tue Jul 14 19:01:04 2020 kern.info kernel: [2104966.049327] pppoe-wan: renamed from ppp0
Tue Jul 14 19:01:04 2020 daemon.info pppd[22096]: Using interface pppoe-wan
Tue Jul 14 19:01:04 2020 daemon.notice pppd[22096]: Connect: pppoe-wan <--> dsl0.101
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: sent [LCP ConfReq id=0x1 <mru 1492> <magic 0x512c892c>]
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: rcvd [LCP ConfReq id=0x65 <mru 1492> <auth chap MD5> <magic 0x7fb944cd>]
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: sent [LCP ConfAck id=0x65 <mru 1492> <auth chap MD5> <magic 0x7fb944cd>]
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: rcvd [LCP ConfAck id=0x1 <mru 1492> <magic 0x512c892c>]
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: sent [LCP EchoReq id=0x0 magic=0x512c892c]
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: rcvd [CHAP Challenge id=0x1 <3deeb871269b1cd4b87af6bc9d3d0b5cc9c584e3bd801bcacd3c61e606edc0c25cf8b38394cfd74dca4f8ae7>, name = "acc-aln3.bb-c"]
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: sent [CHAP Response id=0x1 <8ea2c843eb5d5ea527fc652f8511d139>, name = "mjh5@a.1"]
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: rcvd [LCP EchoRep id=0x0 magic=0x7fb944cd]
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: rcvd [CHAP Success id=0x1 "BBEU31663741"]
Tue Jul 14 19:01:04 2020 daemon.info pppd[22096]: CHAP authentication succeeded: BBEU31663741
Tue Jul 14 19:01:04 2020 daemon.notice pppd[22096]: CHAP authentication succeeded
Tue Jul 14 19:01:04 2020 daemon.notice pppd[22096]: peer from calling number 40:7C:7D:49:FC:35 authorized
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: sent [IPCP ConfReq id=0x1 <addr 0.0.0.0> <ms-dns1 0.0.0.0> <ms-dns2 0.0.0.0>]
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: sent [IPV6CP ConfReq id=0x1 <addr fe80::74a7:5be3:d357:d5ff>]
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: rcvd [IPCP ConfReq id=0x0 <addr 81.187.81.187>]
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: sent [IPCP ConfAck id=0x0 <addr 81.187.81.187>]
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: rcvd [IPCP ConfNak id=0x1 <addr 81.187.65.134> <ms-dns1 217.169.20.20> <ms-dns2 217.169.20.21>]
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: sent [IPCP ConfReq id=0x2 <addr 81.187.65.134> <ms-dns1 217.169.20.20> <ms-dns2 217.169.20.21>]
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: rcvd [IPV6CP ConfAck id=0x1 <addr fe80::74a7:5be3:d357:d5ff>]
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: rcvd [IPCP ConfAck id=0x2 <addr 81.187.65.134> <ms-dns1 217.169.20.20> <ms-dns2 217.169.20.21>]
Tue Jul 14 19:01:04 2020 daemon.notice pppd[22096]: local IP address 81.187.65.134
Tue Jul 14 19:01:04 2020 daemon.notice pppd[22096]: remote IP address 81.187.81.187
Tue Jul 14 19:01:04 2020 daemon.notice pppd[22096]: primary DNS address 217.169.20.20
Tue Jul 14 19:01:04 2020 daemon.notice pppd[22096]: secondary DNS address 217.169.20.21
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: Script /lib/netifd/ppp-up started (pid 22164)
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: rcvd [IPV6CP ConfReq id=0x0 <addr fe80::0203:97ff:fe40:4000>]
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: sent [IPV6CP ConfAck id=0x0 <addr fe80::0203:97ff:fe40:4000>]
Tue Jul 14 19:01:04 2020 daemon.notice pppd[22096]: local LL address fe80::74a7:5be3:d357:d5ff
Tue Jul 14 19:01:04 2020 daemon.notice pppd[22096]: remote LL address fe80::0203:97ff:fe40:4000
Tue Jul 14 19:01:04 2020 daemon.debug pppd[22096]: Script /lib/netifd/ppp6-up started (pid 22167)
Tue Jul 14 19:01:05 2020 daemon.notice netifd: Network device 'pppoe-wan' link is up
Tue Jul 14 19:01:05 2020 daemon.notice netifd: Interface 'wan6' is enabled
Tue Jul 14 19:01:05 2020 daemon.notice netifd: Network alias 'pppoe-wan' link is up
Tue Jul 14 19:01:05 2020 daemon.notice netifd: Interface 'wan6' has link connectivity
Tue Jul 14 19:01:05 2020 daemon.notice netifd: Interface 'wan6' is setting up now
Tue Jul 14 19:01:05 2020 daemon.notice netifd: Interface 'wan' is now up
Tue Jul 14 19:01:05 2020 daemon.debug pppd[22096]: Script /lib/netifd/ppp6-up finished (pid 22167), status = 0x0
Tue Jul 14 19:01:05 2020 daemon.info dnsmasq[30025]: reading /tmp/resolv.conf.auto
Tue Jul 14 19:01:05 2020 daemon.info dnsmasq[30025]: using local addresses only for domain test
Tue Jul 14 19:01:05 2020 daemon.info dnsmasq[30025]: using local addresses only for domain onion
Tue Jul 14 19:01:05 2020 daemon.info dnsmasq[30025]: using local addresses only for domain localhost
Tue Jul 14 19:01:05 2020 daemon.debug pppd[22096]: Script /lib/netifd/ppp-up finished (pid 22164), status = 0x1
Tue Jul 14 19:01:05 2020 daemon.info dnsmasq[30025]: using local addresses only for domain local
Tue Jul 14 19:01:05 2020 daemon.info dnsmasq[30025]: using local addresses only for domain invalid
Tue Jul 14 19:01:05 2020 daemon.info dnsmasq[30025]: using local addresses only for domain bind
Tue Jul 14 19:01:05 2020 daemon.info dnsmasq[30025]: using nameserver 8.8.8.8#53
Tue Jul 14 19:01:05 2020 daemon.info dnsmasq[30025]: using nameserver 192.168.157.5#53
Tue Jul 14 19:01:05 2020 daemon.info dnsmasq[30025]: using local addresses only for domain lan
Tue Jul 14 19:01:05 2020 daemon.info dnsmasq[30025]: using nameserver 217.169.20.20#53
Tue Jul 14 19:01:05 2020 daemon.info dnsmasq[30025]: using nameserver 217.169.20.21#53
Tue Jul 14 19:01:05 2020 user.notice firewall: Reloading firewall due to ifup of wan (pppoe-wan)
Tue Jul 14 19:01:06 2020 user.notice firewall: Reloading firewall due to ifupdate of wan (pppoe-wan)
Tue Jul 14 19:01:06 2020 daemon.err odhcp6c[22251]: Failed to send DHCPV6 message to ff02::1:2 (Operation not permitted)
Tue Jul 14 19:01:08 2020 daemon.err uhttpd[1245]: luci: accepted login on / for root from 192.168.157.177
Tue Jul 14 19:01:10 2020 daemon.notice netifd: Interface 'wan6' is now up
Tue Jul 14 19:01:10 2020 daemon.info dnsmasq[30025]: reading /tmp/resolv.conf.auto
Tue Jul 14 19:01:10 2020 daemon.info dnsmasq[30025]: using local addresses only for domain test
Tue Jul 14 19:01:10 2020 daemon.info dnsmasq[30025]: using local addresses only for domain onion
Tue Jul 14 19:01:10 2020 daemon.info dnsmasq[30025]: using local addresses only for domain localhost
Tue Jul 14 19:01:10 2020 daemon.info dnsmasq[30025]: using local addresses only for domain local
Tue Jul 14 19:01:10 2020 daemon.info dnsmasq[30025]: using local addresses only for domain invalid
Tue Jul 14 19:01:10 2020 daemon.info dnsmasq[30025]: using local addresses only for domain bind
Tue Jul 14 19:01:10 2020 daemon.info dnsmasq[30025]: using nameserver 8.8.8.8#53
Tue Jul 14 19:01:10 2020 daemon.info dnsmasq[30025]: using nameserver 192.168.157.5#53
Tue Jul 14 19:01:10 2020 daemon.info dnsmasq[30025]: using local addresses only for domain lan
Tue Jul 14 19:01:10 2020 daemon.info dnsmasq[30025]: using nameserver 217.169.20.20#53
Tue Jul 14 19:01:10 2020 daemon.info dnsmasq[30025]: using nameserver 217.169.20.21#53
Tue Jul 14 19:01:10 2020 daemon.info dnsmasq[30025]: using nameserver 2001:8b0::2020#53
Tue Jul 14 19:01:10 2020 daemon.info dnsmasq[30025]: using nameserver 2001:8b0::2021#53
Tue Jul 14 19:01:10 2020 user.notice firewall: Reloading firewall due to ifup of wan6 (pppoe-wan)
Tue Jul 14 19:01:13 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:13 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:13 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:13 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:13 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:13 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:13 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:13 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:13 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:13 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:13 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:15 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:15 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:15 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:15 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:15 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:16 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:17 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:17 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:17 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:17 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:18 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:18 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:18 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:18 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:18 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:18 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:18 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:18 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:18 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:18 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:18 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:18 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:19 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:19 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
Tue Jul 14 19:01:19 2020 daemon.err uhttpd[1245]: sh: write error: Broken pipe
I'm not sure what it means by broken pipe, but by this point we were back online.
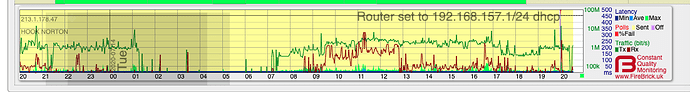
Attach is activity as reported by my ISP - the router reports 1 hrs in the past, incident was actually 20:01
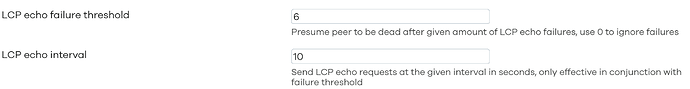
Try in the config interface 'wan' section of /etc/config/network:
option keepalive '6 10'
option pppd_options 'passive'
option padi_timeout '30'
and after saving ubus -v call network reload
Can these be accessed via the web interface as I cannot connect via SSH for some reason.
OK, I'll try 6,10 and see what happens - it's very intermittent so it may be weeks before it happens again!