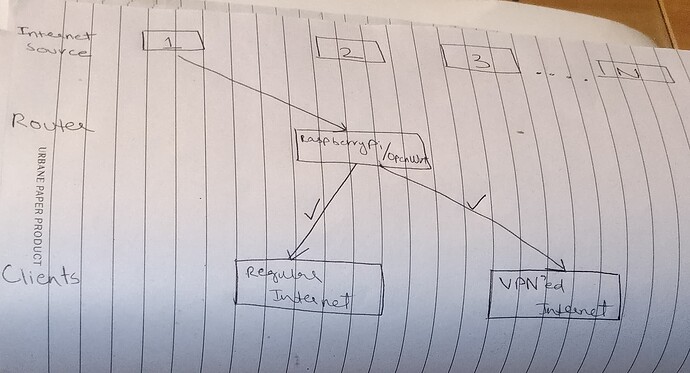
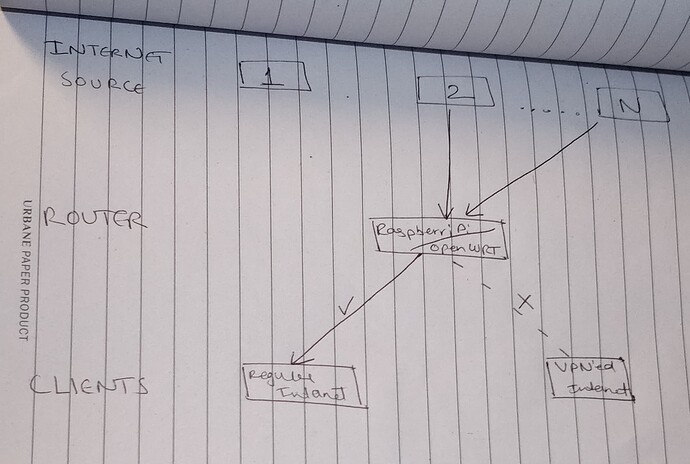
These are the logs:
Sun Jan 9 04:57:03 2022 daemon.warn openvpn(CA_expressvpn)[4325]: DEPRECATED OPTION: --cipher set to 'AES-256-CBC' but missing in --data-ciphers (AES-256-GCM:AES-128-GCM). Future OpenVPN version will ignore --cipher for cipher negotiations. Add 'AES-256-CBC' to --data-ciphers or change --cipher 'AES-256-CBC' to --data-ciphers-fallback 'AES-256-CBC' to silence this warning.
Sun Jan 9 04:57:03 2022 daemon.warn openvpn(CA_expressvpn)[4325]: WARNING: --keysize is DEPRECATED and will be removed in OpenVPN 2.6
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: OpenVPN 2.5.3 aarch64-openwrt-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD]
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: library versions: OpenSSL 1.1.1l 24 Aug 2021, LZO 2.10
Sun Jan 9 04:57:03 2022 daemon.warn openvpn(CA_expressvpn)[4325]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: TCP/UDP: Preserving recently used remote address: [AF_INET]71.19.252.124:1195
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: Socket Buffers: R=[212992->425984] S=[212992->425984]
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: UDP link local: (not bound)
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: UDP link remote: [AF_INET]71.19.252.124:1195
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: TLS: Initial packet from [AF_INET]71.19.252.124:1195, sid=e9392623 20733b18
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: VERIFY OK: depth=1, C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=ExpressVPN CA, emailAddress=support@expressvpn.com
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: VERIFY X509NAME OK: C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=Server-1630-1a, emailAddress=support@expressvpn.com
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: VERIFY OK: depth=0, C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=Server-1630-1a, emailAddress=support@expressvpn.com
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bit RSA, signature: RSA-SHA256
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: [Server-1630-1a] Peer Connection Initiated with [AF_INET]71.19.252.124:1195
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: SENT CONTROL [Server-1630-1a]: 'PUSH_REQUEST' (status=1)
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 10.167.0.1,comp-lzo no,route 10.167.0.1,topology net30,ping 10,ping-restart 60,ifconfig 10.167.0.106 10.167.0.105,peer-id 23,cipher AES-256-GCM'
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: OPTIONS IMPORT: timers and/or timeouts modified
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: OPTIONS IMPORT: compression parms modified
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: OPTIONS IMPORT: --ifconfig/up options modified
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: OPTIONS IMPORT: route options modified
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: OPTIONS IMPORT: peer-id set
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: OPTIONS IMPORT: adjusting link_mtu to 1629
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: OPTIONS IMPORT: data channel crypto options modified
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: Data Channel: using negotiated cipher 'AES-256-GCM'
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: NCP: overriding user-set keysize with default
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_route_v4_best_gw query: dst 0.0.0.0
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_route_v4_best_gw result: via 192.168.1.254 dev wlan0
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: TUN/TAP device tun0 opened
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_iface_mtu_set: mtu 1500 for tun0
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_iface_up: set tun0 up
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_addr_ptp_v4_add: 10.167.0.106 peer 10.167.0.105 dev tun0
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: /usr/libexec/openvpn-hotplug up CA_expressvpn tun0 1500 1557 10.167.0.106 10.167.0.105 init
Sun Jan 9 04:57:08 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_route_v4_add: 71.19.252.124/32 via 192.168.1.254 dev [NULL] table 0 metric -1
Sun Jan 9 04:57:08 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_route_v4_add: 0.0.0.0/1 via 10.167.0.105 dev [NULL] table 0 metric -1
Sun Jan 9 04:57:08 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_route_v4_add: 128.0.0.0/1 via 10.167.0.105 dev [NULL] table 0root@OpenWrt:~# logread -e openvpn
Sun Jan 9 04:57:03 2022 daemon.warn openvpn(CA_expressvpn)[4325]: DEPRECATED OPTION: --cipher set to 'AES-256-CBC' but missing in --data-ciphers (AES-256-GCM:AES-128-GCM). Future OpenVPN version will ignore --cipher for cipher negotiations. Add 'AES-256-CBC' to --data-ciphers or change --cipher 'AES-256-CBC' to --data-ciphers-fallback 'AES-256-CBC' to silence this warning.
Sun Jan 9 04:57:03 2022 daemon.warn openvpn(CA_expressvpn)[4325]: WARNING: --keysize is DEPRECATED and will be removed in OpenVPN 2.6
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: OpenVPN 2.5.3 aarch64-openwrt-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD]
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: library versions: OpenSSL 1.1.1l 24 Aug 2021, LZO 2.10
Sun Jan 9 04:57:03 2022 daemon.warn openvpn(CA_expressvpn)[4325]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: TCP/UDP: Preserving recently used remote address: [AF_INET]71.19.252.124:1195
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: Socket Buffers: R=[212992->425984] S=[212992->425984]
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: UDP link local: (not bound)
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: UDP link remote: [AF_INET]71.19.252.124:1195
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: TLS: Initial packet from [AF_INET]71.19.252.124:1195, sid=e9392623 20733b18
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: VERIFY OK: depth=1, C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=ExpressVPN CA, emailAddress=support@expressvpn.com
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: VERIFY X509NAME OK: C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=Server-1630-1a, emailAddress=support@expressvpn.com
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: VERIFY OK: depth=0, C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=Server-1630-1a, emailAddress=support@expressvpn.com
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bit RSA, signature: RSA-SHA256
Sun Jan 9 04:57:03 2022 daemon.notice openvpn(CA_expressvpn)[4325]: [Server-1630-1a] Peer Connection Initiated with [AF_INET]71.19.252.124:1195
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: SENT CONTROL [Server-1630-1a]: 'PUSH_REQUEST' (status=1)
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 10.167.0.1,comp-lzo no,route 10.167.0.1,topology net30,ping 10,ping-restart 60,ifconfig 10.167.0.106 10.167.0.105,peer-id 23,cipher AES-256-GCM'
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: OPTIONS IMPORT: timers and/or timeouts modified
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: OPTIONS IMPORT: compression parms modified
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: OPTIONS IMPORT: --ifconfig/up options modified
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: OPTIONS IMPORT: route options modified
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: OPTIONS IMPORT: peer-id set
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: OPTIONS IMPORT: adjusting link_mtu to 1629
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: OPTIONS IMPORT: data channel crypto options modified
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: Data Channel: using negotiated cipher 'AES-256-GCM'
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: NCP: overriding user-set keysize with default
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_route_v4_best_gw query: dst 0.0.0.0
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_route_v4_best_gw result: via 192.168.1.254 dev wlan0
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: TUN/TAP device tun0 opened
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_iface_mtu_set: mtu 1500 for tun0
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_iface_up: set tun0 up
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_addr_ptp_v4_add: 10.167.0.106 peer 10.167.0.105 dev tun0
Sun Jan 9 04:57:05 2022 daemon.notice openvpn(CA_expressvpn)[4325]: /usr/libexec/openvpn-hotplug up CA_expressvpn tun0 1500 1557 10.167.0.106 10.167.0.105 init
Sun Jan 9 04:57:08 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_route_v4_add: 71.19.252.124/32 via 192.168.1.254 dev [NULL] table 0 metric -1
Sun Jan 9 04:57:08 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_route_v4_add: 0.0.0.0/1 via 10.167.0.105 dev [NULL] table 0 metric -1
Sun Jan 9 04:57:08 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_route_v4_add: 128.0.0.0/1 via 10.167.0.105 dev [NULL] table 0 metric -1
Sun Jan 9 04:57:08 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_route_v4_add: 10.167.0.1/32 via 10.167.0.105 dev [NULL] table 0 metric -1
Sun Jan 9 04:57:08 2022 daemon.warn openvpn(CA_expressvpn)[4325]: WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Sun Jan 9 04:57:08 2022 daemon.notice openvpn(CA_expressvpn)[4325]: Initialization Sequence Completed
Sun Jan 9 04:59:57 2022 daemon.notice openvpn(CA_expressvpn)[4325]: [Server-1630-1a] Inactivity timeout (--ping-restart), restarting
Sun Jan 9 04:59:57 2022 daemon.notice openvpn(CA_expressvpn)[4325]: SIGUSR1[soft,ping-restart] received, process restarting
Sun Jan 9 04:59:57 2022 daemon.notice openvpn(CA_expressvpn)[4325]: Restart pause, 5 second(s)
Sun Jan 9 05:00:02 2022 daemon.warn openvpn(CA_expressvpn)[4325]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Sun Jan 9 05:00:02 2022 daemon.notice openvpn(CA_expressvpn)[4325]: Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Sun Jan 9 05:00:02 2022 daemon.notice openvpn(CA_expressvpn)[4325]: Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Sun Jan 9 05:00:02 2022 daemon.notice openvpn(CA_expressvpn)[4325]: TCP/UDP: Preserving recently used remote address: [AF_INET]71.19.252.124:1195
Sun Jan 9 05:00:02 2022 daemon.notice openvpn(CA_expressvpn)[4325]: Socket Buffers: R=[212992->425984] S=[212992->425984]
Sun Jan 9 05:00:02 2022 daemon.notice openvpn(CA_expressvpn)[4325]: UDP link local: (not bound)
Sun Jan 9 05:00:02 2022 daemon.notice openvpn(CA_expressvpn)[4325]: UDP link remote: [AF_INET]71.19.252.124:1195
Sun Jan 9 05:00:02 2022 daemon.err openvpn(CA_expressvpn)[4325]: event_wait : Interrupted system call (code=4)
Sun Jan 9 05:00:02 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_route_v4_del: 10.167.0.1/32 via 10.167.0.105 dev [NULL] table 0 metric -1
Sun Jan 9 05:00:02 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_route_v4_del: 71.19.252.124/32 via 192.168.1.254 dev [NULL] table 0 metric -1
Sun Jan 9 05:00:02 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_route_v4_del: 0.0.0.0/1 via 10.167.0.105 dev [NULL] table 0 metric -1
Sun Jan 9 05:00:02 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_route_v4_del: 128.0.0.0/1 via 10.167.0.105 dev [NULL] table 0 metric -1
Sun Jan 9 05:00:02 2022 daemon.notice openvpn(CA_expressvpn)[4325]: Closing TUN/TAP interface
Sun Jan 9 05:00:02 2022 daemon.notice openvpn(CA_expressvpn)[4325]: net_addr_ptp_v4_del: 10.167.0.106 dev tun0
Sun Jan 9 05:00:02 2022 daemon.notice openvpn(CA_expressvpn)[4325]: /usr/libexec/openvpn-hotplug down CA_expressvpn tun0 1500 1626 10.167.0.106 10.167.0.105 init
Sun Jan 9 05:00:02 2022 daemon.notice openvpn(CA_expressvpn)[4325]: SIGTERM[hard,] received, process exiting
Sun Jan 9 05:01:28 2022 daemon.warn openvpn(CA_expressvpn)[4810]: DEPRECATED OPTION: --cipher set to 'AES-256-CBC' but missing in --data-ciphers (AES-256-GCM:AES-128-GCM). Future OpenVPN version will ignore --cipher for cipher negotiations. Add 'AES-256-CBC' to --data-ciphers or change --cipher 'AES-256-CBC' to --data-ciphers-fallback 'AES-256-CBC' to silence this warning.
Sun Jan 9 05:01:28 2022 daemon.warn openvpn(CA_expressvpn)[4810]: WARNING: --keysize is DEPRECATED and will be removed in OpenVPN 2.6
Sun Jan 9 05:01:28 2022 daemon.notice openvpn(CA_expressvpn)[4810]: OpenVPN 2.5.3 aarch64-openwrt-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD]
Sun Jan 9 05:01:28 2022 daemon.notice openvpn(CA_expressvpn)[4810]: library versions: OpenSSL 1.1.1l 24 Aug 2021, LZO 2.10
Sun Jan 9 05:01:28 2022 daemon.warn openvpn(CA_expressvpn)[4810]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Sun Jan 9 05:01:28 2022 daemon.notice openvpn(CA_expressvpn)[4810]: Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Sun Jan 9 05:01:28 2022 daemon.notice openvpn(CA_expressvpn)[4810]: Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Sun Jan 9 05:01:28 2022 daemon.notice openvpn(CA_expressvpn)[4810]: TCP/UDP: Preserving recently used remote address: [AF_INET]71.19.252.142:1195
Sun Jan 9 05:01:28 2022 daemon.notice openvpn(CA_expressvpn)[4810]: Socket Buffers: R=[212992->425984] S=[212992->425984]
Sun Jan 9 05:01:28 2022 daemon.notice openvpn(CA_expressvpn)[4810]: UDP link local: (not bound)
Sun Jan 9 05:01:28 2022 daemon.notice openvpn(CA_expressvpn)[4810]: UDP link remote: [AF_INET]71.19.252.142:1195
Sun Jan 9 05:01:28 2022 daemon.notice openvpn(CA_expressvpn)[4810]: TLS: Initial packet from [AF_INET]71.19.252.142:1195, sid=53478e2e d9503121
Sun Jan 9 05:01:28 2022 daemon.notice openvpn(CA_expressvpn)[4810]: VERIFY OK: depth=1, C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=ExpressVPN CA, emailAddress=support@expressvpn.com
Sun Jan 9 05:01:28 2022 daemon.notice openvpn(CA_expressvpn)[4810]: VERIFY X509NAME OK: C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=Server-1632-1a, emailAddress=support@expressvpn.com
Sun Jan 9 05:01:28 2022 daemon.notice openvpn(CA_expressvpn)[4810]: VERIFY OK: depth=0, C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=Server-1632-1a, emailAddress=support@expressvpn.com
Sun Jan 9 05:01:28 2022 daemon.notice openvpn(CA_expressvpn)[4810]: Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bit RSA, signature: RSA-SHA256
Sun Jan 9 05:01:28 2022 daemon.notice openvpn(CA_expressvpn)[4810]: [Server-1632-1a] Peer Connection Initiated with [AF_INET]71.19.252.142:1195
Sun Jan 9 05:01:29 2022 daemon.notice openvpn(CA_expressvpn)[4810]: SENT CONTROL [Server-1632-1a]: 'PUSH_REQUEST' (status=1)
Sun Jan 9 05:01:29 2022 daemon.notice openvpn(CA_expressvpn)[4810]: PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 10.103.0.1,comp-lzo no,route 10.103.0.1,topology net30,ping 10,ping-restart 60,ifconfig 10.103.0.158 10.103.0.157,peer-id 7,cipher AES-256-GCM'
Sun Jan 9 05:01:29 2022 daemon.notice openvpn(CA_expressvpn)[4810]: OPTIONS IMPORT: timers and/or timeouts modified
Sun Jan 9 05:01:29 2022 daemon.notice openvpn(CA_expressvpn)[4810]: OPTIONS IMPORT: compression parms modified
Sun Jan 9 05:01:29 2022 daemon.notice openvpn(CA_expressvpn)[4810]: OPTIONS IMPORT: --ifconfig/up options modified
Sun Jan 9 05:01:29 2022 daemon.notice openvpn(CA_expressvpn)[4810]: OPTIONS IMPORT: route options modified
Sun Jan 9 05:01:29 2022 daemon.notice openvpn(CA_expressvpn)[4810]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Sun Jan 9 05:01:29 2022 daemon.notice openvpn(CA_expressvpn)[4810]: OPTIONS IMPORT: peer-id set
Sun Jan 9 05:01:29 2022 daemon.notice openvpn(CA_expressvpn)[4810]: OPTIONS IMPORT: adjusting link_mtu to 1629
Sun Jan 9 05:01:29 2022 daemon.notice openvpn(CA_expressvpn)[4810]: OPTIONS IMPORT: data channel crypto options modified
Sun Jan 9 05:01:29 2022 daemon.notice openvpn(CA_expressvpn)[4810]: Data Channel: using negotiated cipher 'AES-256-GCM'
Sun Jan 9 05:01:29 2022 daemon.notice openvpn(CA_expressvpn)[4810]: NCP: overriding user-set keysize with default
Sun Jan 9 05:01:29 2022 daemon.notice openvpn(CA_expressvpn)[4810]: Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Sun Jan 9 05:01:29 2022 daemon.notice openvpn(CA_expressvpn)[4810]: Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Sun Jan 9 05:01:29 2022 daemon.notice openvpn(CA_expressvpn)[4810]: net_route_v4_best_gw query: dst 0.0.0.0
Sun Jan 9 05:01:29 2022 daemon.notice openvpn(CA_expressvpn)[4810]: net_route_v4_best_gw result: via 192.168.1.254 dev wlan0
Sun Jan 9 05:01:29 2022 daemon.notice openvpn(CA_expressvpn)[4810]: TUN/TAP device tun0 opened
Sun Jan 9 05:01:29 2022 daemon.notice openvpn(CA_expressvpn)[4810]: net_iface_mtu_set: mtu 1500 for tun0
Sun Jan 9 05:01:29 2022 daemon.notice openvpn(CA_expressvpn)[4810]: net_iface_up: set tun0 up
Sun Jan 9 05:01:29 2022 daemon.notice openvpn(CA_expressvpn)[4810]: net_addr_ptp_v4_add: 10.103.0.158 peer 10.103.0.157 dev tun0
Sun Jan 9 05:01:29 2022 daemon.notice openvpn(CA_expressvpn)[4810]: /usr/libexec/openvpn-hotplug up CA_expressvpn tun0 1500 1557 10.103.0.158 10.103.0.157 init
Sun Jan 9 05:01:32 2022 daemon.notice openvpn(CA_expressvpn)[4810]: net_route_v4_add: 71.19.252.142/32 via 192.168.1.254 dev [NULL] table 0 metric -1
Sun Jan 9 05:01:32 2022 daemon.notice openvpn(CA_expressvpn)[4810]: net_route_v4_add: 0.0.0.0/1 via 10.103.0.157 dev [NULL] table 0 metric -1
Sun Jan 9 05:01:32 2022 daemon.notice openvpn(CA_expressvpn)[4810]: net_route_v4_add: 128.0.0.0/1 via 10.103.0.157 dev [NULL] table 0 metric -1
Sun Jan 9 05:01:32 2022 daemon.notice openvpn(CA_expressvpn)[4810]: net_route_v4_add: 10.103.0.1/32 via 10.103.0.157 dev [NULL] table 0 metric -1
Sun Jan 9 05:01:32 2022 daemon.warn openvpn(CA_expressvpn)[4810]: WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Sun Jan 9 05:01:32 2022 daemon.notice openvpn(CA_expressvpn)[4810]: Initialization Sequence Completed