Originally posted here.
TL;DR: I would like this configuration with Wireguard client and server interfaces instead of OpenVPN.
Long Version:
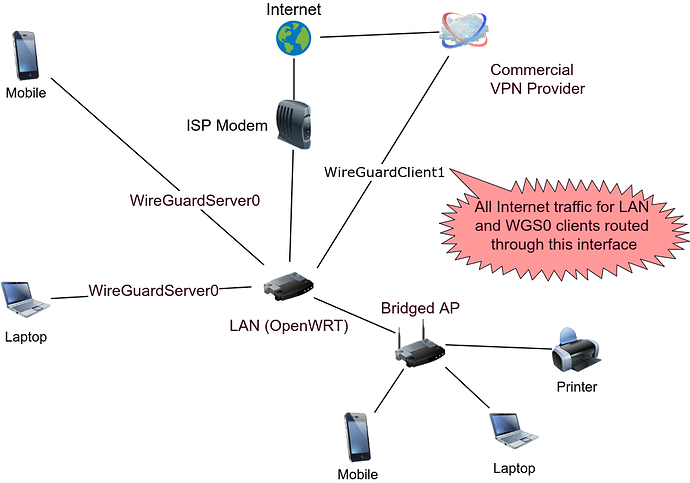
Desired Behavior: WG client device (phone, laptop, tablet, etc.) > WG0 server interface > LAN > WG1 client interface > Commercial VPN provider > Internet
In the desired setup, the WG client device has access to all LAN devices AND internet traffic is also tunneled to Commercial VPN provider.
What currently works: WG client device > WG0 server interface > LAN > WAN (ISP modem) > Internet
In this instance, the clients can connect to WG0 and have full access to LAN devices and internet (over non-VPN ISP WAN). This configuration only works if WG1 client interface is stopped. Once WG1 client interface is started, this tunnel brakes.
What also works: LAN > WG1 client interface > Commercial VPN provider > Internet
In this instance, all devices on the LAN have their internet traffic tunneled to the Commercial VPN provider. This configuration works regardless of whether WG0 server interface is running or stopped.
Here is the desired config:
Configs:
/etc/config/network
config interface 'loopback'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
option device 'lo'
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '10.10.10.1'
option device 'eth0'
option ipv6 '0'
option delegate '0'
config interface 'wan'
option proto 'dhcp'
option device 'eth1'
option ipv6 '0'
option delegate '0'
option peerdns '0'
list dns '9.9.9.9'
config device
option name 'eth1'
config device
option name 'eth0'
config interface 'WireGuardClient1'
option proto 'wireguard'
option private_key 'PRIVATE-KEY'
list addresses '10.5.0.2'
option delegate '0'
option peerdns '0'
list dns '1.1.1.1'
option auto '0'
config wireguard_WireGuardClient1
option public_key 'PUBLIC-KEY'
option persistent_keepalive '25'
option route_allowed_ips '1'
option endpoint_host 'X.X.X.X' #commercial VPN provider endpoint
option endpoint_port '51820'
list allowed_ips '0.0.0.0/0'
list allowed_ips '::0'
config interface 'WireGuardServer0'
option proto 'wireguard'
option private_key 'PRIVATE-KEY'
option listen_port '51820'
list addresses '10.14.0.1/24'
config wireguard_WireGuardServer0
option description 'MyDevice'
option public_key 'PUBLIC-KEY'
list allowed_ips '10.14.0.3/32'
option route_allowed_ips '1'
option persistent_keepalive '25'
/etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone 'lan'
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'LAN'
list network 'WireGuardServer0'
config zone 'wan'
option name 'wan'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option input 'REJECT'
list network 'wan'
list network 'WAN'
list network 'WireGuardClient1'
config forwarding 'lan_wan'
option src 'lan'
option dest 'wan'
config redirect
option target 'DNAT'
option name 'Wireguard Server'
list proto 'udp'
option src 'wan'
option src_dport '51820'
option dest 'lan'
option dest_ip '10.10.10.1'
option dest_port '51820'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
/etc/config/vpn-policy-routing
config vpn-policy-routing 'config'
option verbosity '2'
option strict_enforcement '1'
option src_ipset '0'
option dest_ipset '0'
option resolver_ipset 'dnsmasq.ipset'
option ipv6_enabled '0'
option boot_timeout '30'
option iptables_rule_option 'append'
option procd_reload_delay '1'
option webui_enable_column '0'
option webui_protocol_column '0'
option webui_chain_column '0'
option webui_show_ignore_target '0'
option webui_sorting '1'
list webui_supported_protocol 'tcp'
list webui_supported_protocol 'udp'
list webui_supported_protocol 'tcp udp'
list webui_supported_protocol 'icmp'
list webui_supported_protocol 'all'
option enabled '1'
list ignored_interface 'WireGuardServer0'
config policy
option name 'WireGuardServer'
option proto 'udp'
option chain 'OUTPUT'
option interface 'wan'
option dest_port '51820'
Support output (with public IP redacted)
root@OpenWrt:~# /etc/init.d/vpn-policy-routing support
vpn-policy-routing 0.3.4-8 running on OpenWrt 21.02.1.
============================================================
Dnsmasq version 2.85 Copyright (c) 2000-2021 Simon Kelley
Compile time options: IPv6 GNU-getopt no-DBus UBus no-i18n no-IDN DHCP no-DHCPv6 no-Lua TFTP no-conntrack no-ipset no-auth no-cryptohash no-DNSSEC no-ID loop-detect inotify dumpfile
============================================================
Routes/IP Rules
default * 0.0.0.0 U 0 0 0 WireGuardClient1
IPv4 Table 201: default via X.X.X.X dev eth1
10.10.10.0/24 dev eth0 proto kernel scope link src 10.10.10.1
10.14.0.0/24 dev WireGuardServer0 proto kernel scope link src 10.14.0.1
10.14.0.3 dev WireGuardServer0 proto static scope link
IPv4 Table 201 Rules:
32760: from all fwmark 0x10000/0xff0000 lookup wan
IPv4 Table 202: default via 10.5.0.2 dev WireGuardClient1
10.10.10.0/24 dev eth0 proto kernel scope link src 10.10.10.1
10.14.0.0/24 dev WireGuardServer1 proto kernel scope link src 10.14.0.1
10.14.0.3 dev WireGuardServer1 proto static scope link
IPv4 Table 202 Rules:
32759: from all fwmark 0x20000/0xff0000 lookup WireGuardClient1
IPv4 Table 203: 10.10.10.0/24 dev eth0 proto kernel scope link src 10.10.10.1
IPv4 Table 203 Rules:
32763: from all fwmark 0x30000/0xff0000 lookup WireGuardServer0
============================================================
Mangle IP Table: PREROUTING
-N VPR_PREROUTING
============================================================
Mangle IP Table: FORWARD
-N VPR_FORWARD
-A VPR_FORWARD -p udp -m multiport --sports 51820 -m comment --comment WireGuardServer0 -c 0 0 -g VPR_MARK0x010000
============================================================
Mangle IP Table MARK Chain: VPR_MARK0x010000
-N VPR_MARK0x010000
-A VPR_MARK0x010000 -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_MARK0x010000 -c 0 0 -j RETURN
============================================================
Mangle IP Table MARK Chain: VPR_MARK0x020000
-N VPR_MARK0x020000
-A VPR_MARK0x020000 -c 0 0 -j MARK --set-xmark 0x20000/0xff0000
-A VPR_MARK0x020000 -c 0 0 -j RETURN
============================================================
Mangle IP Table MARK Chain: VPR_MARK0x030000
-N VPR_MARK0x030000
-A VPR_MARK0x030000 -c 0 0 -j MARK --set-xmark 0x30000/0xff0000
-A VPR_MARK0x030000 -c 0 0 -j RETURN
============================================================
Current ipsets
============================================================
Your support details have been logged to '/var/vpn-policy-routing-support'.
Edit: Consolidated all configs into single post. Also @stangri, I have VPN-Bypass running on OpenWRT to create a split tunnel for two clients on an ancient WNDR3400 being used as a wired switch. Uptime is >3 years. Amazing package!