Heheh, fair enough. I guess it has been a while since I posted them.
I'll attach them as follows:
/etc/config/dhcp
config dnsmasq
option domainneeded '1'
option noresolv '1'
option port '53'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option localservice '1'
option ednspacket_max '1232'
option dnsforwardmax '2300'
option min_cache_ttl '270'
option cachesize '5000'
list address '/router/192.168.1.1'
option sequential_ip '1'
option dnssec '1'
option allservers '1'
option confdir '/tmp/dnsmasq.d'
option enable_tftp '1'
option tftp_root '/usbstick/tftp'
list server '127.0.0.1#1053'
list server '::1#1053'
list server '172.18.0.6#1054'
list server '2001:3984:3989::6#1054'
list server '127.0.0.1#5054'
list server '127.0.0.1#5053'
list doh_backup_server '127.0.0.1#1053'
list doh_backup_server '::1#1053'
list doh_backup_server '172.18.0.6#1054'
list doh_backup_server '2001:3984:3989::6#1054'
config boot 'linux'
option filename 'pxelinux.0'
option serveraddress '192.168.1.1'
option servername 'router'
list dhcp_option '209,pxelinux.cfg/default'
option force '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
list ra_flags 'none'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option name 'OVERNET-ASUSWRT'
option ip '192.168.1.2'
option mac '40:B0:76:C1:B8:20'
config host
option name 'UNDERNET-ASUSWRT'
option ip '192.168.1.3'
option mac 'FC:34:97:38:96:08'
config host
option name 'SteamLink'
option ip '192.168.1.5'
option mac 'E0:31:9E:3B:21:73'
config host
option name 'HomePrinter'
option ip '192.168.1.6'
option mac 'DC:4A:3E:BC:67:92'
config host
option name 'SamsungLEDBedroom'
option ip '192.168.1.7'
option mac '0C:89:10:16:15:62'
config host
option name 'BedroomTV'
option ip '192.168.1.8'
option mac '00:0E:C6:6B:4E:9F'
config host
option name 'HabitaciondeCeliaTV'
option ip '192.168.1.9'
option mac '00:0E:C6:6B:4E:A7'
config host
option name 'SaladeEstar'
option ip '192.168.1.10'
option mac '00:0E:C6:74:4D:31'
config host
option name 'NSW-ETH'
option ip '192.168.1.11'
option mac '00:0E:C6:BC:78:34'
config host
option name 'NSW-WiFi'
option ip '192.168.1.12'
option mac '64:B5:C6:70:C9:B9'
config host
option name 'MotoOneActiondeCelia'
option ip '192.168.1.100'
option mac '08:CC:27:5D:91:18'
config host
option name 'MotoOneActiondeLiz'
option ip '192.168.1.110'
option mac '8C:F1:12:58:02:EB'
config host
option name 'LIZ-PC'
option ip '192.168.1.115'
option mac 'F8:E4:E3:6D:F1:23'
config host
option name 'ToastyPen10'
option ip '192.168.1.210'
option mac '8C:B8:4A:45:F5:90'
config host
option name 'ToastySport'
option ip '192.168.1.211'
option mac '74:EB:80:68:AC:54'
config host
option name 'TOASTYTUF-WiFi'
option ip '192.168.1.250'
option mac '84:C5:A6:85:4C:FB'
config host
option name 'TOASTYTUF-GbE'
option ip '192.168.1.251'
option mac '04:D4:C4:E9:4E:21'
config host
option name 'TOASTYTUF-UGREEN'
option mac '00:E0:4C:74:F6:18'
option ip '192.168.1.253'
config host
option name 'HomePrinter'
option duid '00030001DC4A3EBC6792'
option mac 'DC:4A:3E:BC:67:92'
option hostid '6'
config host
option name 'SaladeEstar'
option duid '00030001546009C28DD6'
option mac '54:60:09:C2:8D:D6'
option hostid '10'
config host
option name 'TOASTYTUF-GbE'
option duid '000100012872C85B04D4C4E94E21'
option mac '04:D4:C4:E9:4E:21'
option hostid '251'
config host
option name 'ToastySport'
option duid '000100012655CE3274EB8068AC54'
option mac '74:EB:80:68:AC:54'
option hostid '211'
config host
option ip '192.168.1.116'
option mac '00:0E:C6:75:72:DC'
option name 'LIZ-PC-ETH'
option dns '1'
config host
option name 'TOASTYTUF-KILLER'
option dns '1'
option mac '9C:B6:D0:3C:20:58'
option ip '192.168.1.252'
option duid '000100012872c85b04d4c4e94e21'
config host
option name 'SaladeEstar'
option duid '00030001000EC6744D31'
option mac '00:0E:C6:74:4D:31'
option hostid '10'
config host
option name 'LIZ-PC'
option duid '0001000128585C2D54BF643CDB58'
option mac '54:BF:64:3C:DB:58'
option hostid 'be2'
/etc/config/firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
option reload '1'
config zone 'docker'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option name 'docker'
list network 'docker'
config rule
option name 'AllowNGINXPMAdmin'
option src_port '81'
option dest 'lan'
option dest_port '81'
option target 'ACCEPT'
option src 'lan'
list dest_ip '172.18.0.2'
config redirect
option target 'DNAT'
option name 'RProxy'
option src 'wan'
option src_dport '80'
option dest 'lan'
option dest_port '80'
option dest_ip '172.18.0.2'
config redirect
option target 'DNAT'
option name 'RProxy-SSL'
option src 'wan'
option src_dport '443'
option dest 'lan'
option dest_port '443'
option dest_ip '172.18.0.2'
config redirect 'adblock_docker53'
option name 'Adblock DNS (docker, 53)'
option src 'docker'
option proto 'tcp udp'
option src_dport '53'
option dest_port '53'
option target 'DNAT'
config redirect 'adblock_docker853'
option name 'Adblock DNS (docker, 853)'
option src 'docker'
option proto 'tcp udp'
option src_dport '853'
option dest_port '853'
option target 'DNAT'
config redirect 'adblock_docker5353'
option name 'Adblock DNS (docker, 5353)'
option src 'docker'
option proto 'tcp udp'
option src_dport '5353'
option dest_port '5353'
option target 'DNAT'
config redirect 'adblock_lan53'
option name 'Adblock DNS (lan, 53)'
option src 'lan'
option proto 'tcp udp'
option src_dport '53'
option dest_port '53'
option target 'DNAT'
config redirect 'adblock_lan853'
option name 'Adblock DNS (lan, 853)'
option src 'lan'
option proto 'tcp udp'
option src_dport '853'
option dest_port '853'
option target 'DNAT'
config redirect 'adblock_lan5353'
option name 'Adblock DNS (lan, 5353)'
option src 'lan'
option proto 'tcp udp'
option src_dport '5353'
option dest_port '5353'
option target 'DNAT'
config redirect 'adblock_wan53'
option name 'Adblock DNS (wan, 53)'
option src 'wan'
option proto 'tcp udp'
option src_dport '53'
option dest_port '53'
option target 'DNAT'
config redirect 'adblock_wan853'
option name 'Adblock DNS (wan, 853)'
option src 'wan'
option proto 'tcp udp'
option src_dport '853'
option dest_port '853'
option target 'DNAT'
config redirect 'adblock_wan5353'
option name 'Adblock DNS (wan, 5353)'
option src 'wan'
option proto 'tcp udp'
option src_dport '5353'
option dest_port '5353'
option target 'DNAT'
config redirect
option target 'DNAT'
option name 'RProxy-Admin'
option src 'lan'
option src_dport '81'
option dest 'lan'
option dest_port '81'
option dest_ip '172.18.0.2'
config rule
option name 'RClone-GUI'
option src 'lan'
option src_port '5572'
option dest 'lan'
option dest_port '5572'
option target 'ACCEPT'
list dest_ip '192.168.1.1'
list dest_ip 'fd04:52a5:a38a::1'
config rule
option name 'HomeAssistant'
option src 'lan'
option src_port '8123'
option dest 'lan'
option dest_port '8123'
option target 'ACCEPT'
list dest_ip '192.168.1.1'
list dest_ip 'fd04:52a5:a38a::1'
config rule
option name 'Allow-NFS-RPC'
option src 'lan'
option proto 'tcp udp'
option dest_port '111'
option target 'ACCEPT'
config rule
option name 'Allow-NFS'
option src 'lan'
option proto 'tcp udp'
option dest_port '2049'
option target 'ACCEPT'
config rule
option name 'Allow-NFS-Lock'
option src 'lan'
option proto 'tcp udp'
option dest_port '32777:32780'
option target 'ACCEPT'
config rule
option name 'Tautulli'
option src 'lan'
option src_port '8181'
option dest 'lan'
list dest_ip '172.18.0.5'
option dest_port '8181'
option target 'ACCEPT'
config rule
option name 'PiHole-Admin'
option src_port '82'
option dest 'lan'
option dest_port '82'
option target 'ACCEPT'
option src 'lan'
list dest_ip '192.168.1.1'
list dest_ip 'fd04:52a5:a38a::1'
config nat
option name 'PiHole-DNAT'
list proto 'tcp'
list proto 'udp'
list proto 'icmp'
option src 'lan'
option dest_ip '192.168.0.2'
option dest_port '80'
option target 'SNAT'
option snat_ip '192.168.1.1'
option snat_port '82'
config rule
option name 'Transmission-GUI'
option src 'lan'
option dest 'lan'
option target 'ACCEPT'
list dest_ip '192.168.1.1'
list dest_ip 'fd04:52a5:a38a::1'
option src_port '9091'
option dest_port '9091'
/etc/config/network
config interface 'vpn_usa'
option proto 'none'
option device 'ovpnc0'
config interface 'vpn_uk'
option proto 'none'
option device 'ovpnc1'
config interface 'vpn_spa'
option proto 'none'
option device 'ovpnc2'
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd04:52a5:a38a::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option proto 'pppoe'
option device 'eth0'
option username 'REDACTED'
option password 'REDACTED'
option ipv6 'auto'
option hostname 'router'
config interface 'docker'
option device 'docker0'
option proto 'none'
option auto '0'
config device
option type 'bridge'
option name 'docker0'
/etc/config/vpn-policy-routing
config vpn-policy-routing 'config'
option verbosity '2'
option strict_enforcement '1'
option resolver_ipset 'dnsmasq.ipset'
list ignored_interface 'vpnserver wgserver'
option boot_timeout '30'
option iptables_rule_option 'append'
option procd_reload_delay '1'
option webui_sorting '1'
list webui_supported_protocol 'tcp'
list webui_supported_protocol 'udp'
list webui_supported_protocol 'tcp udp'
list webui_supported_protocol 'icmp'
list webui_supported_protocol 'all'
option enabled '1'
option ipv6_enabled '0'
list supported_interface 'pppoe-wan'
list supported_interface 'ovpnc0'
list supported_interface 'ovpnc1'
list supported_interface 'ovpnc2'
option webui_enable_column '1'
option webui_protocol_column '1'
option webui_chain_column '1'
option webui_show_ignore_target '1'
option dest_ipset '1'
option src_ipset '1'
config include
option enabled '0'
option path '/usbstick/vpn-pbr/vpn-policy-routing.netflix.user'
config include
option enabled '0'
option path '/usbstick/vpn-pbr/vpn-policy-routing.aws.user'
config include
option path '/usbstick/vpn-pbr/vpn-policy-routing.vrv.user'
option enabled '0'
config include
option enabled '0'
option path '/usbstick/vpn-pbr/vpn-policy-routing.disney.user'
config include
option enabled '0'
option path '/usbstick/vpn-pbr/vpn-policy-routing.disney2.user'
config include
option enabled '0'
option path '/usbstick/vpn-pbr/vpn-policy-routing.disney3.user'
config include
option enabled '0'
option path '/usbstick/vpn-pbr/vpn-policy-routing.disney4.user'
config include
option enabled '0'
option path '/usbstick/vpn-pbr/vpn-policy-routing.disney5.user'
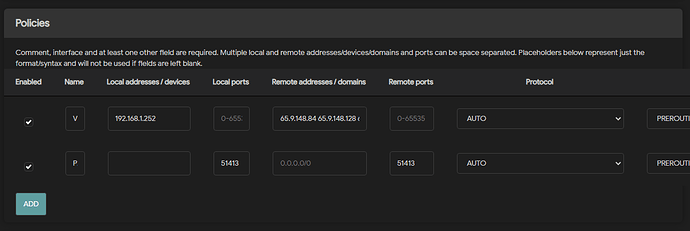
config policy
option name 'VRV'
option dest_addr '65.9.148.84 65.9.148.128 65.9.148.62 65.9.148.37 65.9.148.101 65.9.148.122 65.9.148.121 65.9.148.28 65.9.148.10 65.9.148.117 65.9.148.121 65.9.148.110'
option interface 'vpn_usa'
option src_addr '192.168.1.252'
option enabled '0'
config policy
option name 'P2P'
option src_port '51413'
option dest_port '51413'
option interface 'vpn_usa'
/etc/init.d/vpn-policy-routing support
Wouldn't let me post as text due to sheer size (In fact, I think it didn't even fit in my terminal's buffer), so I'll attach both output and /var/vpn-policy-routing-support in a zip file here.
/etc/init.d/vpn-policy-routing reload
[root@OpenWRT-RPi /]# /etc/init.d/vpn-policy-routing reload
Creating table 'vpn_usa/ovpnc0/REDACTED' [✓]
Creating table 'vpn_uk/ovpnc1/REDACTED' [✓]
Creating table 'vpn_spa/ovpnc2/REDACTED' [✓]
Creating table 'wan/pppoe-wan/REDACTED' [✓]
Routing 'P2P' via vpn_usa [✓]
vpn-policy-routing 0.3.4-8 monitoring interfaces: vpn_usa vpn_uk vpn_spa wan [✓]
vpn-policy-routing 0.3.4-8 started with gateways:
vpn_usa/ovpnc0/REDACTED
vpn_uk/ovpnc1/REDACTED
vpn_spa/ovpnc2/REDACTED
wan/pppoe-wan/REDACTED [✓]
If you need me to post anything else, please let me know.