Hi again,
After investigation, I noticed my DMZ is not going through WAN but directly to the VPN.
# cat /etc/config/vpn-policy-routing
config vpn-policy-routing 'config'
option verbosity '2'
option ipv6_enabled '0'
option strict_enforcement '1'
option boot_timeout '30'
option proto_control '1'
option chain_control '1'
option enable '1'
option enabled '1'
option dnsmasq_enabled '1'
config policy
option proto 'tcp'
option interface 'wan'
option name 'dmz-https'
option local_address '10.42.0.1/24'
option remote_address '0.0.0.0/0'
option chain 'FORWARD'
I had to use the chain 'FORWARD' otherwise DNS is not resolving.
# cat /var/vpn-policy-routing-support
vpn-policy-routing 0.0.6-0 running on OpenWrt Chaos Calmer.
============================================================
Dnsmasq version 2.78 Copyright (c) 2000-2017 Simon Kelley
Compile time options: IPv6 GNU-getopt no-DBus no-i18n no-IDN DHCP no-DHCPv6 no-Lua TFTP no-conntrack no-ipset no-auth no-DNSSEC loop-detect inotify
============================================================
Routes/IP Rules
default 10.8.0.1 128.0.0.0 UG 0 0 0 tun0
default gateway.wan 0.0.0.0 UG 0 0 0 pppoe-wan
IPv4 Table 201: default via gateway.wan dev pppoe-wan
IPv4 Table 201 Rules:
32759: from all fwmark 0x10000 lookup 201
IPv4 Table 202: default via 10.8.0.1 dev tun0
IPv4 Table 202 Rules:
32758: from all fwmark 0x20000 lookup 202
============================================================
IP Tables PREROUTING
-N VPR_PREROUTING
-A VPR_PREROUTING -m set --match-set vpn_out dst -c 0 0 -j MARK --set-xmark 0x20000/0xff0000
-A VPR_PREROUTING -m set --match-set wan dst -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
============================================================
IP Tables FORWARD
-N VPR_FORWARD
-A VPR_FORWARD -s 10.42.0.0/24 -m comment --comment dmz-https -c 98 12686 -j MARK --set-xmark 0x10000/0xff0000
============================================================
IP Tables INPUT
-N VPR_INPUT
============================================================
IP Tables OUTPUT
-N VPR_OUTPUT
============================================================
Current ipsets
create wan hash:net family inet hashsize 1024 maxelem 65536 comment
create vpn_out hash:net family inet hashsize 1024 maxelem 65536 comment
============================================================
Thanks
Some others informations:
# ip rule
0: from all lookup local
32758: from all fwmark 0x20000 lookup 202
32759: from all fwmark 0x10000 lookup 201
32766: from all lookup main
32767: from all lookup default
# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 10.8.0.1 128.0.0.0 UG 0 0 0 tun0
0.0.0.0 gateway.wan 0.0.0.0 UG 0 0 0 pppoe-wan
10.8.0.0 0.0.0.0 255.255.255.0 U 0 0 0 tun0
10.42.0.0 0.0.0.0 255.255.255.0 U 0 0 0 eth2
10.42.16.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0.3
10.42.33.0 0.0.0.0 255.255.255.0 U 0 0 0 wlan0
10.42.42.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0.1
10.42.99.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0.4
gateway.wan 0.0.0.0 255.255.255.255 UH 0 0 0 pppoe-wan
128.0.0.0 10.8.0.1 128.0.0.0 UG 0 0 0 tun0
ip.vpn gateway.wan 255.255.255.255 UGH 0 0 0 pppoe-wan
So the DMZ (eth2) goes directly to the VPN interface (rule 0x2000) but the rule above set the DMZ interface to 0x1000 so going through WAN directly. I don't know what could be wrong as the rules seem correct.
Any idea ?
EDIT: Hi again,
Problem solved by putting chain PREROUTING and..don't remember what I've done next.
But now, I can't access DMZ services (https with private IP) from LAN but, I can still PING the box and use services not submitted to VPR.
Bernd
June 24, 2019, 4:58am
462
Hello.
I can not bypass vpn, to watch Netflix.
root@OpenWrt:~# cat /etc/config/vpn-policy-routing
config policy
option chain 'PREROUTING'
option interface 'wan'
option name 'SPA112'
option local_address '192.168.1.205'
option proto 'tcp udp'
config policy
option chain 'PREROUTING'
option interface 'wan'
option name 'TC4400'
option remote_address '192.168.100.1'
option proto 'tcp udp'
config vpn-policy-routing 'config'
option verbosity '2'
option ipv6_enabled '0'
option ipset_enabled '1'
option dnsmasq_enabled '0'
option strict_enforcement '1'
option boot_timeout '30'
option enabled '1'
config policy
option chain 'PREROUTING'
option interface 'wan'
option name 'Netflix'
option remote_address 'amazonaws.com netflix.com nflxext.com nflximg.net nflxso.net nflxvideo.net dvd.netflix.com'
option proto 'tcp udp'
root@OpenWrt:~# /etc/init.d/vpn-policy-routing status
vpn-policy-routing 0.0.6-0 running on OpenWrt 18.06.2.
============================================================
Dnsmasq version 2.80 Copyright (c) 2000-2018 Simon Kelley
Compile time options: IPv6 GNU-getopt no-DBus no-i18n no-IDN DHCP DHCPv6 no-Lua TFTP conntrack ipset auth DNSSEC no-ID loop-detect inotify dumpfile
============================================================
Routes/IP Rules
default 10.3.0.2 128.0.0.0 UG 0 0 0 tun0
default ip-X-X-X-X. 0.0.0.0 UG 0 0 0 eth0.2
IPv4 Table 201: default via X.X.X.X dev eth0.2
IPv4 Table 201 Rules:
32755: from all fwmark 0x10000 lookup 201
IPv4 Table 202: default via 10.3.0.2 dev tun0
IPv4 Table 202 Rules:
32754: from all fwmark 0x20000 lookup 202
============================================================
IP Tables PREROUTING
-N VPR_PREROUTING
-A VPR_PREROUTING -d 207.45.72.201/32 -m comment --comment Netflix_dvd_netflix_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 207.45.72.201/32 -m comment --comment Netflix_dvd_netflix_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 184.73.192.76/32 -m comment --comment Netflix_nflxvideo_net -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 184.73.192.76/32 -m comment --comment Netflix_nflxvideo_net -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.17.14.207/32 -m comment --comment Netflix_nflxvideo_net -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.17.14.207/32 -m comment --comment Netflix_nflxvideo_net -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.32.140.41/32 -m comment --comment Netflix_nflxvideo_net -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.32.140.41/32 -m comment --comment Netflix_nflxvideo_net -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 50.17.247.31/32 -m comment --comment Netflix_nflxvideo_net -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 50.17.247.31/32 -m comment --comment Netflix_nflxvideo_net -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.18.140.121/32 -m comment --comment Netflix_nflxvideo_net -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.18.140.121/32 -m comment --comment Netflix_nflxvideo_net -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 54.89.245.208/32 -m comment --comment Netflix_nflxvideo_net -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 54.89.245.208/32 -m comment --comment Netflix_nflxvideo_net -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.16.244.17/32 -m comment --comment Netflix_nflxvideo_net -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.16.244.17/32 -m comment --comment Netflix_nflxvideo_net -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.32.78.165/32 -m comment --comment Netflix_nflxvideo_net -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.32.78.165/32 -m comment --comment Netflix_nflxvideo_net -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.32.240.186/32 -m comment --comment Netflix_nflxvideo_net -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.32.240.186/32 -m comment --comment Netflix_nflxvideo_net -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 207.45.72.215/32 -m comment --comment Netflix_nflxext_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 207.45.72.215/32 -m comment --comment Netflix_nflxext_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.31.145.183/32 -m comment --comment Netflix_netflix_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.31.145.183/32 -m comment --comment Netflix_netflix_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 34.249.125.167/32 -m comment --comment Netflix_netflix_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 34.249.125.167/32 -m comment --comment Netflix_netflix_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.209.79.186/32 -m comment --comment Netflix_netflix_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.209.79.186/32 -m comment --comment Netflix_netflix_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.19.56.133/32 -m comment --comment Netflix_netflix_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.19.56.133/32 -m comment --comment Netflix_netflix_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.30.128.237/32 -m comment --comment Netflix_netflix_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.30.128.237/32 -m comment --comment Netflix_netflix_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.209.224.161/32 -m comment --comment Netflix_netflix_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.209.224.161/32 -m comment --comment Netflix_netflix_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 54.77.135.19/32 -m comment --comment Netflix_netflix_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 54.77.135.19/32 -m comment --comment Netflix_netflix_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.49.6.246/32 -m comment --comment Netflix_netflix_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 52.49.6.246/32 -m comment --comment Netflix_netflix_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 72.21.210.29/32 -m comment --comment Netflix_amazonaws_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 72.21.210.29/32 -m comment --comment Netflix_amazonaws_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 207.171.166.22/32 -m comment --comment Netflix_amazonaws_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 207.171.166.22/32 -m comment --comment Netflix_amazonaws_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 72.21.206.80/32 -m comment --comment Netflix_amazonaws_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 72.21.206.80/32 -m comment --comment Netflix_amazonaws_com -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 192.168.100.1/32 -m comment --comment TC4400 -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 192.168.100.1/32 -m comment --comment TC4400 -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -s 192.168.1.205/32 -m comment --comment SPA112 -c 69 23994 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -s 192.168.1.205/32 -m comment --comment SPA112 -c 69 23994 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -m set --match-set PP_VPN dst -c 0 0 -j MARK --set-xmark 0x20000/0xff0000
-A VPR_PREROUTING -m set --match-set wan dst -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
============================================================
IP Tables FORWARD
-N VPR_FORWARD
============================================================
IP Tables INPUT
-N VPR_INPUT
============================================================
IP Tables OUTPUT
-N VPR_OUTPUT
============================================================
Current ipsets
create wan hash:net family inet hashsize 1024 maxelem 65536 comment
create PP_VPN hash:net family inet hashsize 1024 maxelem 65536 comment
============================================================
Your support details have been logged to '/var/vpn-policy-routing-support'. [✓]
Can you help?
It's notoriously difficult to bypass Netflix's proxy detection in this way. My advice would be to send all traffic from that device through your WAN interface.
I would second @tectonic 's advise. Alternatively, you can try the included custom user file for Netflix/AWS, but that would route a lot of your non-Netflix traffic over WAN as well.
Bernd
July 13, 2019, 8:11am
465
Hello stangri.
Your package works wonderfully with IPv4, but I have some issues with IPv6.
My VPN provider offers IPv6. I use 2 OpenVPN clients with one WAN and I use this script to enable NAT6.
Client1 has:
Client2 has:
Client1 or Client2 have always wrong IPv6 IP. Is it possible to choose with this package, which device uses which IPv6 with interface? Or does this package only support IPv4?
My config:
root@OpenWrt:~# cat /etc/config/vpn-policy-routing
config policy
option chain 'PREROUTING'
option interface 'wan'
option name 'TC4400'
option remote_address '192.168.100.1'
option proto 'tcp udp'
config policy
option chain 'PREROUTING'
option interface 'wan'
option name 'Fritzbox'
option local_address '192.168.1.138'
option proto 'tcp udp'
config policy
option name 'PC1'
option proto 'udp'
option local_address '192.168.1.112'
option chain 'PREROUTING'
option interface 'PP_VPN1'
config policy
option name 'PC2'
option local_address '192.168.1.141'
option proto 'udp'
option chain 'PREROUTING'
option interface 'PP_VPN2'
config vpn-policy-routing 'config'
option verbosity '2'
option ipset_enabled '1'
option dnsmasq_enabled '0'
option strict_enforcement '1'
option boot_timeout '30'
option enabled '1'
option ipv6_enabled '1'
list supported_interface 'PP_VPN1'
list supported_interface 'PP_VPN2'
root@OpenWrt:~# /etc/init.d/vpn-policy-routing status
vpn-policy-routing 0.0.6-0 running on OpenWrt 18.06.2.
============================================================
Dnsmasq version 2.80 Copyright (c) 2000-2018 Simon Kelley
Compile time options: IPv6 GNU-getopt no-DBus no-i18n no-IDN DHCP no-DHCPv6 no-Lua TFTP no-conntrack no-ipset no-auth no-DNSSEC no-ID loop-detect inotify dumpfile
============================================================
Routes/IP Rules
default 10.4.129.2 128.0.0.0 UG 0 0 0 tun2
default 10.3.0.2 128.0.0.0 UG 0 0 0 tun1
default ip-62-143-72-1. 0.0.0.0 UG 0 0 0 eth0.2
IPv4 Table 201: default via 62.143.72.1 dev eth0.2
IPv4 Table 201 Rules:
28982: from all fwmark 0x10000 lookup 201
IPv4 Table 202: default via 10.3.0.2 dev tun1
IPv4 Table 202 Rules:
28981: from all fwmark 0x20000 lookup 202
IPv4 Table 203: default via 10.4.129.2 dev tun2
IPv4 Table 203 Rules:
28980: from all fwmark 0x30000 lookup 203
============================================================
IP Tables PREROUTING
-N VPR_PREROUTING
-A VPR_PREROUTING -s 192.168.1.141/32 -m comment --comment PC2 -c 0 0 -j MARK --set-xmark 0x30000/0xff0000
-A VPR_PREROUTING -s 192.168.1.112/32 -m comment --comment PC1 -c 26 3113 -j MARK --set-xmark 0x20000/0xff0000
-A VPR_PREROUTING -s 192.168.1.138/32 -m comment --comment Fritzbox -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -s 192.168.1.138/32 -m comment --comment Fritzbox -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 192.168.100.1/32 -m comment --comment TC4400 -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -d 192.168.100.1/32 -m comment --comment TC4400 -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -m set --match-set PP_VPN2 dst -c 0 0 -j MARK --set-xmark 0x30000/0xff0000
-A VPR_PREROUTING -m set --match-set PP_VPN1 dst -c 0 0 -j MARK --set-xmark 0x20000/0xff0000
-A VPR_PREROUTING -m set --match-set wan dst -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
============================================================
IP6 Tables PREROUTING
-N VPR_PREROUTING
-A VPR_PREROUTING -m set --match-set PP_VPN26 dst -c 0 0 -j MARK --set-xmark 0x30000/0xff0000
-A VPR_PREROUTING -m set --match-set PP_VPN16 dst -c 0 0 -j MARK --set-xmark 0x20000/0xff0000
-A VPR_PREROUTING -m set --match-set wan6 dst -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
============================================================
IP Tables FORWARD
-N VPR_FORWARD
============================================================
IPv6 Tables FORWARD
-N VPR_FORWARD
============================================================
IP Tables INPUT
-N VPR_INPUT
============================================================
IPv6 Tables INPUT
-N VPR_INPUT
============================================================
IP Tables OUTPUT
-N VPR_OUTPUT
============================================================
IPv6 Tables OUTPUT
-N VPR_OUTPUT
============================================================
Current ipsets
create wan hash:net family inet hashsize 1024 maxelem 65536 comment
create wan6 hash:net family inet6 hashsize 1024 maxelem 65536 comment
create PP_VPN1 hash:net family inet hashsize 1024 maxelem 65536 comment
create PP_VPN16 hash:net family inet6 hashsize 1024 maxelem 65536 comment
create PP_VPN2 hash:net family inet hashsize 1024 maxelem 65536 comment
create PP_VPN26 hash:net family inet6 hashsize 1024 maxelem 65536 comment
============================================================
Your support details have been logged to '/var/vpn-policy-routing-support'. [✓]
Bernd:
Client1 has:
Client2 has:
Could you please elaborate on that?
Bernd
July 13, 2019, 9:34am
467
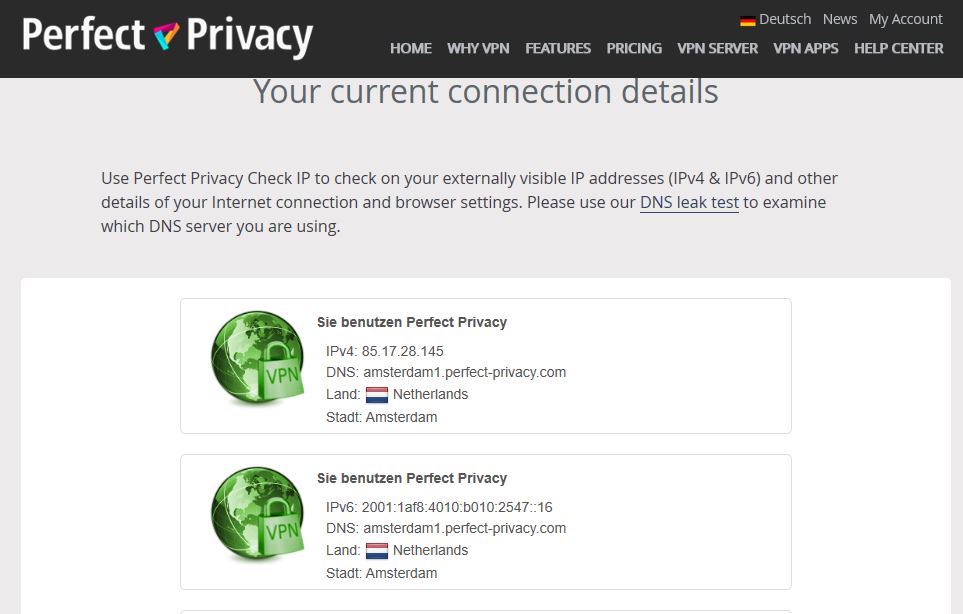
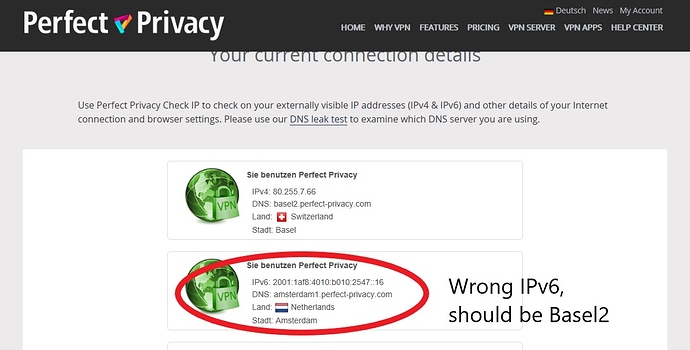
Here the connection details of 2 PCs:
PC1: IPv4 and IPv6 use Amsterdam1 servers.
PC2: IPv4 and IPv6 should use Basel2 server, but PC2 uses IPv6 from Amsterdam1 server.
That should be fixed by your vpn provider.
Bernd
July 13, 2019, 9:18pm
469
This is not an issue from vpn provider.
That may be an issue of vpn routing or OpenWRT. I do not have such issues with pfSense.
I already had the discussion here .
Hi,
First of all thanks for developing this great bit of software for openwrt.
I was wondering if you had any ideas on an odd problem I seem to have after setting up openvpn on my router and then installing the vpn-policy based routing package.
I have currently only one rule setup based on source IP subnet: 192.168.1.1/24 which as I understand it should be routing everything through my WAN interface. And it seems to be doing that based on checking my ISP with the vpn-policy based routing software enabled (shows my own ISP) Vs when disabled (shows nordvpn ISP). However the odd thing I see is that with the rule activated I cannot reach 2 domain names which are www.rtve.es and www.netflix.com . I seem to be able to ping them fine but not reach them via the browser, nor for example via the Netflix app for my firetv. At first I thought it might be a DNS issue but I can still ping the addresses just fine. If I change the rule to route through the VPN tunnel or disable vpn-policy based routing I can reach the sites via the web browser just fine.
Do you have any idea what might be causing this strange issue?
Thanks in advance!
Have you tried creating a policy which wouldn't include the router's IP itself? Like '192.168.1.81/28'?
I'm trying to build firmware and like to add this app,there is no app by default. Can anyone help me to add this app in SDK?
Use image builder rather than an SDK and check the README on my repo.
Also, please direct further SDK/image building questions to a separate thread.
stangri:
192.168.1.81/28
Hi,netflix.com .
Thanks
I need stuff mentioned in the README to accompany support requests.
Also, just to confirm -- if you stop VPR, you can access these web-sites via VPN connection?
Hi,
Yes correct, if I stop VPR service I can access both sites via the VPN provider.
I´ve posted the requested output here:
Contents of `/etc/config/vpn-policy-routing:
config vpn-policy-routing 'config'
option verbosity '2'
option ipv6_enabled '0'
option ipset_enabled '1'
option dnsmasq_enabled '0'
option strict_enforcement '1'
option boot_timeout '30'
option enabled '1'
config policy
option chain 'PREROUTING'
option proto 'tcp udp'
option interface 'wan'
option name 'LAN'
option local_address '192.168.1.81/28'
Output of /etc/init.d/vpn-policy-routing reload
Creating table 'wan/87.235.0.10' [✓]
Creating table 'nordvpntun/10.7.0.1' [✓]
Routing 'LAN' via wan [✓]
vpn-policy-routing 0.0.6-1 started on wan/87.235.0.10 nordvpntun/10.7.0.1 [✓]
vpn-policy-routing 0.0.6-1 monitoring interfaces: wan nordvpntun [✓]
root@OpenWrt:~#
I´ve uploaded the /etc/init.d/vpn-policy-routing status -p to paste.ee. Should I message you the URL?
Thanks
If you stop VPR and the VPN tunnel, can you access these sites over WAN?
Hi,
Thanks!