it recognized this before

it recognized this before
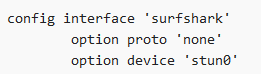
Correct me if I'm wrong, but wouldn't the name of your interface be "surfshark", not "stun"?
its the device name
Correct and you're putting the "device" type name into the "interface" name box. Is that correct? To me it seems that the field you are filling in wants the "interface" name. In your case that would be "surfshark", no?
i guess this is a question for @stangri because I know stun was the interface name that worked pre-upgrade.
@stangri I noticed that my vpn device wasn't in the list anymore, but I wasn't the only one i see  So you are already aware off the issue I asume.
So you are already aware off the issue I asume.
I added my device (vpnclient) by 'Supported Interfaces' and it works as normal now. I will wait for the fix and try again as soon as available.
Have you guys tested his latest version 0.3.4-8?
@stangri might be time to push a PR for 0.3.4-8 as it seems some changes in the recent master/stable are causing issues with 0.3.2-20 which is the latest that was pushed.
@stangri thanks for the PR's, I see the Luci component was promoted and merged. However the base package is still stuck in staging and looks like @Pepe has a handful of comments/suggestions directed towards you, not sure if you saw it. So VPR is at a mismatched state right now with higher luci component (0.3.4-8) while base is still 0.3.2-20.
I've addressed @Pepe's concerns, I hope it will get merged soon. I only have the merge rights for luci repo for now.
Yep, same issue.
Hi,
Anyone got this to work with HBO Max? I added hbo.com and hbomax.com but that does not seem to be enough.
WRT3200ACM on OpenWrt 21.02.0-rc3 r16172 & vpn-policy-routing 0.3.4-8
I have the below set-ups for VBR and my network.
Basically, I have the WAN left as the default gateway (openvpn config: list pull_filter 'ignore "redirect-gateway"') and route a couple devices via static IPs to one of the two PIA VPNs I have set up. So most traffic goes through the WAN while a few IPs go through one of the 2 VPNs.
I also have a PiHole set-up on a RP4 at 192.168.2.252 that is set-up in the dchp config on the WRT3200 as: list server '192.168.2.252'
Since I have the OpenVPN config set with List pull_filter 'ignore "redirect-gateway"', the DNS for the VPN provider (PIA) (dhcp-option DNS 10.0.0.243) is also not set along with not setting the default gateway.
When one of the devices set to go through the VPN, for a speed test for example, it works fine and routes the traffic through the VPN based on the VBR setting for its static IP.
The problem is that the DNS requests does not go to the VPN providers DNS but it goes to the PiHole I have set-up for the rest of the network.
How can I set any device selected for a VPN in VBR (i.e. not WAN) to go through the VPN Providers DNS that is 10.0.0.243.? Can this be based on the VPN Interfaces that are set-up or is there another way to do this?
I have searched around and have not been able to figure out how to do this so any help would be appreciated.
vpn-policy-routing:
config vpn-policy-routing 'config'
option enabled '1'
option verbosity '2'
option strict_enforcement '0'
option src_ipset '0'
option ipv6_enabled '0'
list ignored_interface 'vpnserver wgserver'
option boot_timeout '30'
option iptables_rule_option 'append'
option iprule_enabled '0'
option webui_enable_column '1'
option webui_chain_column '0'
option webui_sorting '1'
list webui_supported_protocol 'tcp'
list webui_supported_protocol 'udp'
list webui_supported_protocol 'tcp udp'
list webui_supported_protocol 'icmp'
list webui_supported_protocol 'all'
option resolver_ipset 'dnsmasq.ipset'
option dest_ipset '0'
option webui_show_ignore_target '0'
option webui_protocol_column '0'
config policy
option src_addr '192.168.2.162'
option interface 'wan'
option comment 'AnkerUSB-GB-Adapter'
config policy
option src_addr '192.168.2.163'
option comment 'Raspberry_Pi_3'
option interface '1_NLD_VPN'
config policy
option src_addr '192.168.2.164'
option comment 'Ford'
option interface '2_DEU_VPN'
.........
network:
config interface 'loopback'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
option device 'lo'
config globals 'globals'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.2.1'
option delegate '0'
option device 'br-lan'
config interface 'wan'
option proto 'dhcp'
option peerdns '0'
option delegate '0'
option device 'wan'
config device 'wan_wan_dev'
option name 'wan'
option macaddr 'xx:xx:xx:xx:xx:xx'
option ipv6 '0'
config interface '1_NLD_VPN'
option proto 'none'
option defaultroute '0'
option peerdns '0'
option delegate '0'
option device 'tun0'
config interface '2_DEU_VPN'
option proto 'none'
option defaultroute '0'
option peerdns '0'
option delegate '0'
option device 'tun1'
dchp:
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
list server '192.168.2.252'
option rebind_protection '0'
config dhcp 'lan'
option interface 'lan'
option leasetime '12h'
option dhcpv4 'server'
option start '25'
option limit '100'
list ra_flags 'none'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
list ra_flags 'none'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option ip '192.168.2.160'
option dns '1'
option name 'FritzExtender_2_4GHz'
option mac 'xx:xx:xx:xx:xx:xx'
.........
openvpn - 2 instances, only one shown - PIA_DEU_AES128 is same except for "list remote"
config openvpn 'PIA_NLD_AES128'
option tls_client '1'
option port '1198'
option auth_nocache '1'
option auth_user_pass '/etc/openvpn/userpass.txt'
option proto 'udp'
option resolv_retry 'infinite'
option nobind '1'
option persist_key '1'
option persist_tun '1'
option remote_cert_tls 'server'
option client '1'
option auth 'SHA1'
option dev 'tun0'
option ca '/etc/openvpn/ca.rsa.2048.crt'
option mute_replay_warnings '1'
option reneg_sec '0'
option crl_verify '/etc/openvpn/crl.rsa.2048.pem'
option disable_occ '1'
option log '/mnt/sdb1/openvpn_logs/openvpn_PIA_NLD_AES128.log'
list pull_filter 'ignore "redirect-gateway"'
list pull_filter 'ignore "ifconfig-ipv6"'
list pull_filter 'ignore "route-ipv6"'
option fast_io '1'
option enabled '1'
option verb '4'
option sndbuf '360488'
option rcvbuf '360488'
list remote 'nl-amsterdam.privacy.network'
option script_security '2'
option route_up '"/etc/init.d/vpn-policy-routing reload"'
option cipher 'AES-128-GCM'
If I understood you correctly, I don't think there's an option to do it fully within VPR, sounds like you need different instances of dnsmasq for different groups of clients and those dnsmasq instances would be using different resolvers.
PS. This comes up fairly frequently, I'll try to consider maybe making a custom user script first before trying to integrate it into VPR proper. It's not going to be high up on my list tho, so if anyone is willing to contribute code -- please do.
Thanks a lot. I understand that it is a low priority and I have lived with the DNS leaks for a while but thought someone would have done something like this already.
I figured I might share my simple hack for those with limited space on their routers and possibly for a change in the Custom User File includes. I was unable to install curl due to space limitations but wget is already installed (be default I believe). I have been able successfully use the Custom User Files after editing them. Also had issues with it failing due to lack of space in /var. I apologize in advance if this is the wrong place but here are my fixes...
...
#TARGET_FNAME="/var/vpn-policy-routing_tmp_aws_ip_ranges"
TARGET_FNAME="/tmp/vpn-policy-routing_tmp_aws_ip_ranges"
...
#curl -s "$TARGET_URL" 2>/dev/null | jsonfilter -e '@.data.ipv4_prefixes[*].prefix' > "$TARGET_FNAME"
#wget -qO- redirects "downloaded" file to stdout
wget -qO- "$TARGET_URL" 2>/dev/null | jsonfilter -e '@.data.ipv4_prefixes[*].prefix' > "$TARGET_FNAME"
...
I hope this helps at least 1 person out.
Which router/OpenWrt is it? AFAIK /var and /tmp are the same on OpenWrt.
I'll try to migrate from use of curl to the (built-in) uclient-fetch in the next release.
I would like to use vpn-policy-based routing.
i am not techie as u all guys
i am getting error
has unknown interface: 'TUN0'
i am using openvpn as vpn