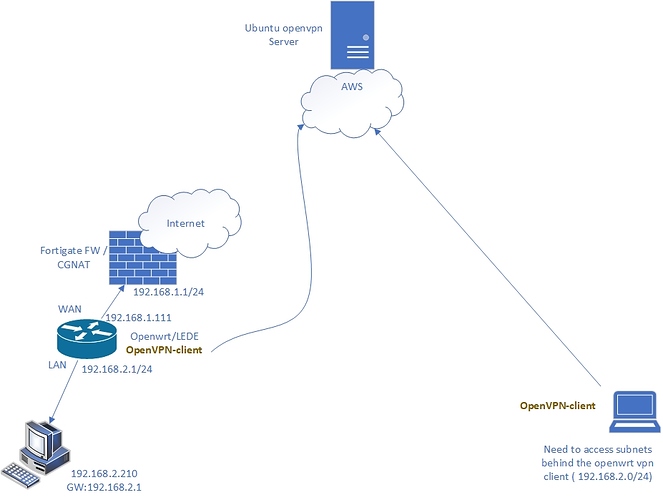
Hi Guys , I have a custom home setup that I would like to work to be able to access my computer/server VMs thru openvpn . The not helping part is that my carrier uses CGnat so that is why I actually decided to do this in the first place.the openvpn client on the LEDE is causing me some issues that i think is related to routing , but before that I would like you to take a look and advise if you think what am trying to acheive is doable. I am using an EC2 AWS machine as the openvpn server.
https://openwrt.org/docs/guide-user/services/vpn/openvpn/extras#site-to-site
It's almost the same, just use routed mode.
Push OpenWrt client-LAN route with increased metric for all VPN-clients.
This is very possible, but consider if using wireguard is possible, it's substantially easier and faster
thanks @vgaetera . I will review this config and advise. Currently with my config , i have the tunnel up but i cannot ping the server(gateway) , while from another vpn client i can pnig the gateway fine. I think i have to focus again on using the details iroute/route/push route. I will check and post any problem later this evening. Thanks
Reading good stuff about wireguard. Any docos for server config ubuntu linux , client on led
Did you open the firewall?
Just follow the same manual for both.
opkg update
opkg install kmod-udptunnel4 kmod-udptunnel6 kmod-wireguard wireguard-tools wireguard luci-proto-wireguard luci-app-wireguard
Thanks I will try it out . But since I started with openvpn . I thought id see where it goes. I can ping client to client , but i cannot ping subnets behind the openvpn client "192.168.2.200" ,, below is my config:
thats under server ```
root@ip-172-31-31-96:/etc/openvpn/ccd# cat openwrt
iroute 192.168.2.0 255.255.255.0
ifconfig-push 10.8.0.9 10.8.0.10
relevant part from the server.conf is :slight_smile:
client-config-dir ccd
route 192.168.2.0 255.255.255.0 10.8.0.9
client-config-dir ccd
route 10.8.0.8 255.255.255.252
am confused as i cannot see a route for 192.168.2.0/24 on the linux machine , havent added that . is that the problem
default via 172.31.16.1 dev eth0 proto dhcp src 172.31.31.96 metric 100
10.8.0.0/24 via 10.8.0.2 dev tun0
10.8.0.2 dev tun0 proto kernel scope link src 10.8.0.1
10.8.0.8/30 via 10.8.0.2 dev tun0
172.31.16.0/20 dev eth0 proto kernel scope link src 172.31.31.96
172.31.16.1 dev eth0 proto dhcp scope link src 172.31.31.96 metric 100Use network mask instead of peer address.
Utilize topology subnet on VPN-server.
Remove duplicates.
Specify full path to CCD-directory.
Make sure your client certificate CN is openwrt.
its confusing. I can ping from 192.168.2.200 ( machine after openwrt client) to 10.8.0.8 ( another opevpn client)
but i cannot ping from the 10.8.0.8 to 192.168.2.200
server.conf 
client-config-dir /etc/openvpn/ccd
route 10.8.0.8 255.255.255.252
route 192.168.2.0 255.255.255.0 10.8.0.9
topology subnet
for LEDE:
root@LEDE:/etc/openvpn# ls -l
-rw------- 1 root root 5023 Mar 6 12:01 openwrt.conf
root@LEDE:/etc/openvpn#
for ccd directory:
ubuntu@ip-172-31-31-96:/etc/openvpn/ccd$ cat openwrt
ifconfig-push 10.8.0.9 255.255.255.0
iroute 192.168.2.0 255.255.255.0
ubuntu@ip-172-31-31-96:/etc/openvpn/ccd$
i added the last route to the linux machine but no luck too :
ubuntu@ip-172-31-31-96:/etc/openvpn/ccd$ route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 172.31.16.1 0.0.0.0 UG 100 0 0 eth0
10.8.0.0 0.0.0.0 255.255.255.0 U 0 0 0 tun0
10.8.0.8 10.8.0.2 255.255.255.252 UG 0 0 0 tun0
172.31.16.0 0.0.0.0 255.255.240.0 U 0 0 0 eth0
172.31.16.1 0.0.0.0 255.255.255.255 UH 100 0 0 eth0
192.168.2.0 10.8.0.9 255.255.255.0 UG 0 0 0 tun0
Looks like a firewall issue. Can you verify that flows are open for the return traffic and that no NAT is applied?
Also make sure you have done this:
so I should create another ccd file for the other client ? can you please give an example ?
shouldnt "
route 192.168.2.0 255.255.255.0 10.8.0.9
in the server.conf do the needful ?
cat << EOF >> /etc/openvpn/vpnserver.conf
push "route 192.168.2.0 255.255.255.0 10.8.0.9 2048"
EOF
Or ensure that other VPN-clients use redirect-gateway def1.
the route 192.168.2.0 255.255.255.0 10.8.0.9 is already in the server.conf
If VPN-clients don't use redirect-gateway def1, they don't know about that route.
Can I push it with ccd file , because i dont want all the traffic goes thru the tunnel. But its confusing, if the client doesnt know the route , then I wouldnt be able to ping from 192.168.2.200 to 10.8.0.8 ( the other openvpn client) , but i cannot do the opposite .
the sysmptom is firewall as you said, but the return traffic is opened and no NAT applied. I can ping from the lan behind the client to the other client. But i cannot ping from the client to the LAN behind the openwrt client.
You can also add the route to VPN-client profile.
Anyway, use traceroute/tracepath and tcpdump for troubleshooting.
You can post here the firewall configurations for both openwrt and ubuntu to check if you have missed something.
I am not sure why it was not pushed by the server to the other host . looks like i need ccd for the other client too. I edited the ovpn file and added " route 192.168.2.0 255.255.255.0 10.8.0.9" and the route solved the issue.
Thanks alot for all the support.