Use VPN Policy Routing, VPN Bypass only supports very simple rules.
Good god man, thank you so much for this. My static routes want to buy you some beers!
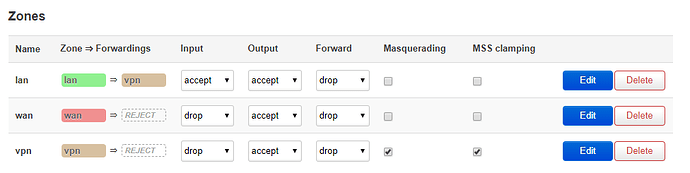
Hello, I'm having trouble to make this work using firewall setup below (do not allow traffic if VPN is down)
iptables -t mangle -vnL shows that packets are market correctly in chain VPNBYPASS but I believe some other firewall rule blocks connection. If I add custom firewall rule to destination address for zone_wan_dest_ACCEPT connection timeout is much longer than without custom rule, but I still can't connect.
Any advice?
EDIT: OK it works now,
- Added masquare check for wan firewall zone
- Added /etc/init.d/vpnbypass line (after other rules)
for ll in ${routes}; do ipt -I FORWARD -d "$ll" -j ACCEPT; done
Hi
I’m getting the following error message from the luci app when I apply settings:
Failed to execute cbi dispatcher target for entry '/admin/services/vpnbypass'.
The called action terminated with an exception:
/usr/lib/lua/luci/model/cbi/vpnbypass.lua:72: attempt to call field 'restart' (a nil value)
stack traceback:
/usr/lib/lua/luci/model/cbi/vpnbypass.lua:72: in function '?'
/usr/lib/lua/luci/cbi.lua:226: in function '_run_hooks'
/usr/lib/lua/luci/cbi.lua:403: in function 'parse'
/usr/lib/lua/luci/dispatcher.lua:853: in function </usr/lib/lua/luci/dispatcher.lua:832>
My device is glinet ar300m running OpenWrt 18.06.1 r7258-5eb055306f.
Here is my dhcp confit:
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option nonwildcard '1'
option localservice '1'
list ipset '/github.com/plex.tv/google.com/vpnbypass'
list ipset '/whatsmyip.com/vpnbypass'
list ipset '/facebook.com/vpnbypass'
option resolvfile '/tmp/resolv.conf.vpn'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option force '1'
option dhcpv6 'server'
option ra 'server'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config dhcp 'guest'
option interface 'guest'
option start '100'
option leasetime '12h'
option limit '150'
option dhcpv6 'server'
option ra 'server'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config domain 'localhost'
option name 'console.gl-inet.com'
option ip '192.168.9.1'
Welcome to the forum and thank you for the report!
Could you please test the version from my repo and confirm it works before I submit PR to the main OpenWrt repo? Installed luci-app-vpnbypass version should end with 8 and not 7.
Thanks!
I installed it from your repo. My luci-app-vpnbypass version is git-19.137.50186-a7d35ed-8. Still not working.
Are you running official OpenWrt release or GL-iney version?
It's the Gl.Inet firmware.
It is incompatible with my apps.
Thank you. So I can't use your VPN policy app either?
You should be able to use either vpnbypass or VPR from command line, but the web ui apps would most likely not work.
You can probably install official OpenWrt release on your GLI net device and then use the web ui apps.
Hello @stangri, I am new to the world of VPNs, just purchased a subscription to CyberGhost and set it up on my Linksys WRT1900AC running DD-WRT, and now have run into a problem that when I try to use Netflix Hulu or amazon Prime Video it tells me I am behind a VPN and I must disable it to use these services... I was looking around the internet to see if I could find a solution and it looks like you may have a solution that would work, it looks like your solution runs on OpenWRT so my question is would this work to route just the traffic for these 3 services around the firewall or can you only selectively route based on the Device that it is running on for example I would have to route all the traffic from the PC hosting these services around the VPN?
Welcome to the community Chris!
Outside of creating a policy for the device to go thru WAN and not the VPN, there is no known solution for Netflix at least.
With my other app -- vpn-policy-routing, you can, however, try to not set the default routing for the VPN, so most of the traffic will go via WAN and then you can create policies for domains/devices to go via VPN.
Thank you for the reply. I found a Similar Thread that claims to have a solution for all these Streaming Services (Hulu, Amazon Prime Video, and Netflix), the problem is their script only works on ASUS Routers running ASUSWRT Merlin, The reason that it only works on ASUS running ASUSWRT Merlin has to do with something with having to sideload ipset on other third party firmwares, I guess that is not the case with ASUSWRT Merlin. One option is to purchases an Asus router and load the third party firmware and this script to make it work, but I would like to exhaust all my options on my current hardware before I start investing in new hardware. Not sure if the method that they use can be adopted to work with your bypass Script (Programming is not a strong point for me). But thought it might be worth sharing to see if this could work.
Thanks!
The VPN Bypass is intentionally too simple to make use of some of these, but if you're willing to migrate to the VPN Policy Routing, I've added support for custom user files: https://github.com/stangri/openwrt_packages/blob/master/vpn-policy-routing/files/README.md#custom-user-files
BTW, even with the VPN Bypass you can start by trying to add the following ipset: /amazonaws.com/netflix.com/nflxext.com/nflximg.net/nflxso.net/nflxvideo.net/dvd.netflix.com/vpnbypass.
Hello!
I'm fairly new to all this, just setup my MIR3G with OpenWrt (18.6.4) over the weekend and seriously loving the control it gives so far.
I've setup an Open VPN client on the router to direct all my traffic through it which is working as intended, but I was curious about how I disable the VPN should need be and stumbled across this package which looked perfect for my needs.
I've run the basic setup as outlined in the README and enabled the package via the Luci UI but it doesn't seem to be working. To test I added the local address of the bridged ISP cable router I'm running at home (192.168.100.1/32) which I have been unable to access on it's local address since setting up the VPN and still cannot access even with this package. I also attempted to add my VPN provider's domain (/nordvpn.com) to the bypassed domain to test using their site widget that highlights whether you are using their service or not when you navigate to it, but it also doesn't seem to work, still saying I'm 'Protected'.
I'm wondering if there is something peculiar about my particular setup that is causing this issue, I followed this guide to setup the VPN on OpenWrt. As mentioned I'm fairly new to all this so I'd really appreciate any help any one can give on this.
Cheers!
If you stop the OpenVPN client, can you access your cable modem?
Also, post the vpnbypass and dhcp configs.
No I can't access 192.168.100.1, or anything else actually, if I stop openvpn (/etc/init.d/openvpn stop), should I be able to given the firewall rules put in place for the VPN?
# cat /etc/config/vpnbypass
config vpnbypass 'config'
option enabled '1'
list localsubnet '192.168.100.1/32'
# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
Really appreciate your help btw @stangri , thanks heaps!
If the cable modem is inaccessible with the VPN client stopped, this package cannot help you.
You may want to create a separate thread to ask for assistance with configuring VPN client properly, so that you still have working connection when the VPN client is stopped and when you achieve that, try this package again.
Thanks @stangri will do. I honestly just followed the tutorial provided by the VPN so I assumed that this was a 'standard' setup, guess not.
Cheers!