For the sake of completeness, I had it all installed but I wanted to start over so I reset the router and restored to an earlier backup, after which I installed the requirements and the app using Putty. When I remove the apps, I get access to OpenVPN again as well...
If you stop OpenVPN client, do you have internet connection?
What exactly did you do?
If you stop OpenVPN client, do you have internet connection?
Wireguard, actually. If I stop the WG interface, I lose Internet access until I restart the WAN interface.
Nvermind, I reset my install, restored to another point, and installed your policy based routing app, which is working great (I do have a couple of questions about it, which I will ask in the appropriate channel).
Hello, I wonder if you can help. I use IPRedator which routes all traffic through their VPN.
I however want to exclude for example my TV so netflix works.
I have tried adding the TV Local IP Addresses to Bypass: 192.168.1.82 and setting my laptop to 192.168.1.83 and doing a ping, but it doesn't work if the service is enabled.
As soon as I do that the TV has no connection at all to the internet, nor does my laptop.
Network:
https://pastebin.com/kP7ve79a
Firewall:
https://pastebin.com/UkcadhtZ
vpnbypass:
https://pastebin.com/dFGkDarF
Can you help?
I have the same issue as you, both LUCI companions (for VPNBypass and Policy routing) disable completely my VPN tab on LUCI therefore can't view anything and get the same "Access Denied" issue with trying to enter the URL.
Is there a solution for this? Tried reinstalling everything but just doesn't work and also affects my access to OpenVPN GUI.
Having same issue since last week I update pacakages.
I thought I had posted in this thread too, but I guess I forgot. There seems to be an issue with luci-base/luci-compat on 19.07.3 (and newer), I'm waiting to hear back from senior devs on what to do.
Hello
is there any way to pass a list of ip/ranges to bypass from another file?
say file download from https://lite.ip2location.com/iran-(islamic-republic-of)-ip-address-ranges
the goal is to bypass home-country ip's from vpn
You need to use vpn-policy-routing and create a custom user file to pull the ips/ranges from an external source into an ipset.
Hi @stangri
Thank you for creating vpnbypass, I learn a lot from just using it about custom route tables.
I am facing an issue, I am running 3 VPNs, but only one is for transporting whole traffic. The other twos are for connecting to server infrastructures that I am managing.
The problem I am facing is that traffic to those two vpns is going through first one.
Here is my setup:
$ iptables-save | grep VPNBYPASS
-A PREROUTING -m mark --mark 0x0/0xff0000 -g VPNBYPASS
-A VPNBYPASS -s 192.168.1.0/24 -j MARK --set-xmark 0x10000/0xff0000
-A VPNBYPASS -m set --match-set vpnbypass dst -j MARK --set-xmark 0x10000/0xff0000
Nothing fancy here
$ ip route
0.0.0.0/1 via 10.8.0.1 dev tun10
default via 192.168.0.1 dev eth1 proto static src 192.168.0.136
10.6.0.0/24 via 10.6.0.5 dev tun1
10.6.0.5 dev tun1 proto kernel scope link src 10.6.0.6
10.7.0.0/24 via 10.7.0.9 dev tun0
10.7.0.9 dev tun0 proto kernel scope link src 10.7.0.10
10.8.0.0/24 dev tun10 proto kernel scope link src 10.8.0.2
128.0.0.0/1 via 10.8.0.1 dev tun10
185.XXX.XXX.XXX via 192.168.0.1 dev eth1
192.168.0.0/24 dev eth1 proto kernel scope link src 192.168.0.136
Nothing fancy there.
To table 200, I added two rules, so that I can connect from 192.168.1.0/24 to 10.{6,7}.0.1
$ ip route show table 200
default via 192.168.0.1 dev eth1
10.6.0.0/24 via 10.6.0.5 dev tun1
10.7.0.0/24 via 10.7.0.9 dev tun0
Everything works fine, except that when I am connecting to 10.{6,7}.0.1 it goes through 10.8.0.1. 10.7.0.1 resolves to 188.XXX.XXX.XXX
23:10:03.224855 IP 188.XXX.XXX.XXX.1194 > 10.8.0.2.60127: UDP, length 77
23:10:03.237255 IP 188.XXX.XXX.XXX.1194 > 10.8.0.2.60127: UDP, length 185
23:10:03.237310 IP 188.XXX.XXX.XXX.1194 > 10.8.0.2.60127: UDP, length 241
23:10:03.239115 IP 10.8.0.2.60127 > 188.XXX.XXX.XXX.1194: UDP, length 77
23:10:03.239161 IP 10.8.0.2.60127 > 188.XXX.XXX.XXX.1194: UDP, length 77
Any ideas?
Thanks
You may be better off using vpn-policy-routing if you're running more than one VPN connection.
I have tired to install as you say, although I do not even know my router's name (it's branded PlusNet, which is a re-branding of BT, British Telecommunications plc). Please will you see if you can help with the following problems, preferably from the GUI as my competence can only just use the command prompt:
- Domains to Bypass does work at all;
- Remote IP Addresses to Bypass seems to block them entirely.
How do we make it bypass the router when the router itself is also a torrent seedbox? I have a transmission daemon running all the time, and I've tried to bypass the router ip, the transmission ports, but nothing seems to make it "connectable".
I can bypass the VPN on other devices on my LAN, and if I shutdown the VPN, the transmission client connects just fine.
@stangri
Hi Stan, I am running Wireguard VPN client on my router - all devices on LAN go over Wireguard. I also have clients on the LAN who are using Tailscale VPN (wireguard based...) to connect to cloud servers. I don't want Tailscale over Wireguard - overkill and very slow.
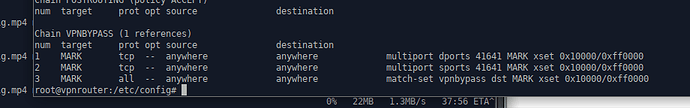
Tailscale traffic on LAN is UDP port 41641 - when I attempt VPN Bypass based on this port it does not work and I noticed the chain VPNBYPASS is triggering for tcp. Is there any way I can change it to UDP from the console/SSH?
/etc/config/vpnbypass
config vpnbypass 'config'
list localport '41641'
list remoteport '41641'
option enabled '1'
Thank you
/magnus
Try vpn-policy-routing with either the AUTO for the protocol or explicit UDP. There was some discussion how successful UDP-targeting policies can be, so please post back after you try.
No luck with UDP/auto/etc. Did get WAN interface as default/primary and could assign LAN ip's to wg0, but the filtering for Tailscale on 41641 did not work. Also, Tailscale needs to get a control key from a coordination server, which I'm assuming it can get unencrypted over WAN or over Wireguard.
Clearly, I'm way over my head here, this could be a great project to learn about Linux routing and iptables. I figured so much that the idea is to flag packages using a specific LAN port using -t mangle and then route based on this flag. Here is the output from tailscaled' systemctrl
sep 17 19:56:18 tower tailscaled[788005]: 4.8M/20.0M control: TryLogin: fetch control key: Get "https://login.tailscale.com/key": dial tcp: lookup login.tailscale.com on 127.0.0.53:53: read udp 127.0.0.1:56371->127.0.0.53>
sep 17 19:56:18 tower tailscaled[788005]: 4.8M/20.0M control: sendStatus: authRoutine1: state:authenticating
sep 17 19:56:18 tower tailscaled[788005]: 4.8M/20.0M Received error: TryLogin: fetch control key: Get "https://login.tailscale.com/key": dial tcp: lookup login.tailscale.com on 127.0.0.53:53: read udp 127.0.0.1:56371->127>
sep 17 19:56:18 tower tailscaled[788005]: 4.8M/20.0M control: authRoutine: backoff: 1404 msec
sep 17 19:56:20 tower tailscaled[788005]: 4.9M/20.0M control: authRoutine: state:authenticating
sep 17 19:56:20 tower tailscaled[788005]: 4.9M/20.0M control: direct.TryLogin(false, 0)
sep 17 19:56:20 tower tailscaled[788005]: 4.9M/20.0M control: doLogin(regen=false, hasUrl=false)
sep 17 19:56:28 tower tailscaled[788005]: logtail: dial "log.tailscale.io:443" failed: dial tcp: lookup log.tailscale.io on 127.0.0.53:53: read udp 127.0.0.1:36752->127.0.0.53:53: i/o timeout (in 20.001s)
sep 17 19:56:28 tower tailscaled[788005]: logtail: upload: log upload of 544 bytes compressed failed: Post "https://log.tailscale.io/c/tailnode.log.tailscale.io/xyxyx>
sep 17 19:56:28 tower tailscaled[788005]: logtail: backoff: 1013 msec
Thank you for you help /m
Policies order and exact settings (ipset vs iptables vs ip rules for local IPs) may play into that.
You may also want to experiment with a separate WLAN/VLAN for the tailscape clients.
Good luck!
Hi, I'm very interested in using this package, and I'm an amateur on OpenWRT (just installing it to my old pc, but 99 percent using only LuCI or GUI).
I have a question though, so when I have installed the vpnbypass via LuCI Software, somehow the gui isn't there. So how can I access the gui? Thank you.