Hi,
I'm trying to configure some kind of weird network setup and I'd like to get suggestions whether this is possible at all and -if so- how...
My Problem can be described as follows:
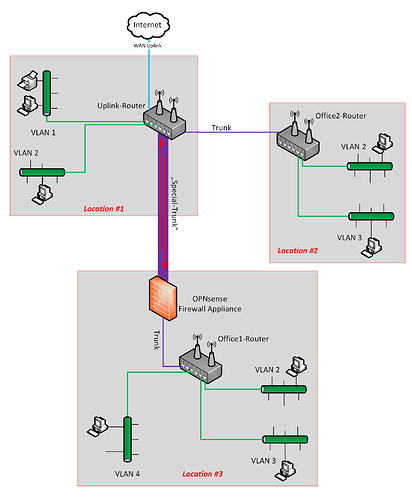
- I have some VLAN capable OpenWRT Routers with Wifi (e.g. TP-Link AC1750 Archer C7). These are located in different "buildings" (Location #1 .. #3 in my picture).
- I need multiple different VLANs that are (kind of) arbitrary distributed through the locations
- I have a (VLAN capable) Firewall Appliance (based on OPNsense) which should do routing and firewalling
a) From/To WAN and all internal VLANs
b) Among the VLANs
- Location#2 and Location #3 both have a single cable connection to Location #1 (the purple ones in my image)
- Any VLAN itself must appear as a single network (= broadcast domain) - no matter where the endpoints are physically located. In other words: VLAN2 is (from an endpoint device point of view) identic to VLAN2 in another location.
The challenge:
I'd really like to manage all my firewalling on OPNsense (there will be frequent changes and maintenance should be kept a) as simple as possible and b) at a single point. That leads to the following problem, that I tried to paint with the red arrows in my "Special-Trunk":
- Any traffic from WAN should pass the Uplink Router, be "forwarded" to the firewall and then be "distributed" to the appropriate VLAN. The same way backwards should be followed for the opposite direction (VLAN x to WAN).
- Any traffic from a VLAN that is addressed to another VLAN must be firewalled/routed, too.
The problem where I'm currently stumbling is, that the Uplink-Router should not directly e.g. VLAN 1 from Location #1 and VLAN 2 from Location #2, but that seems to happen when setting up the managed switch and configuring the tagged / untagged ports for the network links...
Any suggestions? Further questions?
Thanks in advance,
Bart Simpson
yes, the concept is sound.
architecturally, the opnsense device;
- would be more efficient higher up the chain
- will need to handle the performance demands
- may need 'intermediate vlans' if kept in it's current position to logically direct traffic through it ( based on your hardware + topology this might be your only option )
your actually mentally picturing two isolated trunks from the opnsense back to the core switch/router... some hardware offers functionality to deliver equivalent flows... but the way it is drawn, there is no enforced directivity from the core router/switch via opnsense...
2 Likes
For some reason, geographically dispersed L2 configurations give me concerns about latency.
2 Likes
Hi @anon50098793,
I'm not sure if I understood your answer correctly (I'm not a native speaker though)...
I already thought about putting the OPNsense device to Location #1 (maybe intercepting the WAN uplink). That would solve many of the problems - including performance. But...
- ...performance isn't a big concern in my use case for multiple reasons (e.g. ~95% of traffic will be inside a VLAN in a single location, which is "backboned" by a switch - i.e. the fat green lines in my image)
- ...I think this does not solve all the problems, especially the biggest challenge will (as far as I understand it right now) only be moved, but not solved: E.g. the Office1-Router still needs to be configured in a way that any "inter-VLAN-traffic" will be routed through the firewall and not directly be outputted to the matching switch-port.
What do you mean by "intermediate vlans"? Could you explain that a little more?
About the two "isolated trunks": You could imagine my setup that way, I think. But I thought, it would not be neccessary to get special hardware for this. In my (current and not well-educated) opinion, it should be possible to handle the problem solely through "correct" routing - maybe with one drawback that I might be able to get over: Loosing the single broadcast domain for a complete VLAN (i.e. across multiple locations) by separating them into more (to keep my picture: each fat green segment could be a separate VLAN).
Could this solve the problems?
Bart Simpson
1 Like
dont know enough about opensense (or your other hardware) or how it's setup to give much more detail...
but yes... either opnsense or a l3 device behind it would provide core routing forcing all L2 handover to happen there. i.e. all LANs are reachable via .200@200.1
in addition to vgaetera's point... you'll have double-point of failure.. trunk + all devices in the path to l3 handover.
read some CCNP docs re: CORE/ACCESS architecture... they design this way... although they have advanced L2 functionality and place a huge emphasis on redundancy.