Hi all,
I just finished setting up a number of vlans inside openwrt running in ap mode from a netgear r7800 in combination with a pfsense firewall and a couple of netgear switches in the middle of the two. Everything works well or so it seems to me; but I would really appreciate if you knowledgeable guys here could confirm what I did is correct since I am not totally sure.
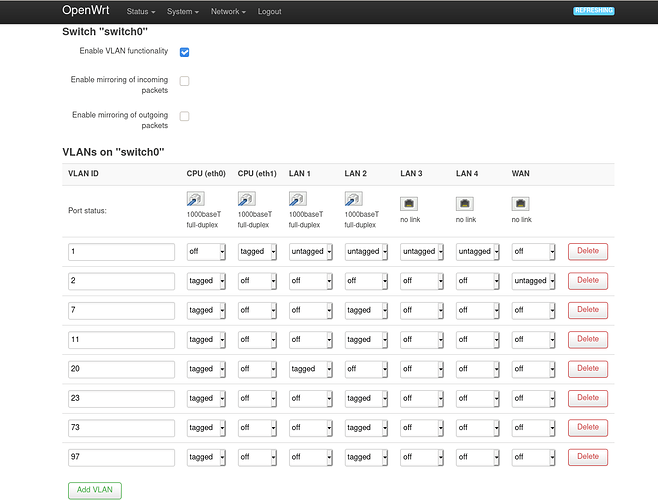
While the vlan configuration at the pfsense and netgear switches level is quite clear to me now, it is not really the case for the openwrt part; I still have some doubts on why things are the way they are and I am not sure whether my settings are safe and optimal. This is notably the case when it comes to the Switch configuration. Here is a screenshot https://postimg.cc/4mvNVhWb and below:
My network configuration is as follows: I have about 10 vlans distributed between two physical networks/nics at the pfsense router level (out of the 5 available, plus the WAN): LAN and OPT1. Ethernet cables connect the 2 nics with two switches, and the 2 switches with the openwrt ap lan ports 1 and 2 respectively. I assigned (tagged) the vlans to lan1 or lan2 depending on whether these ports are connected to LAN/switch 1 or to OPT1/switch 2. So 20 runs from lan 1, the rest from lan 2.
As for the interfaces, they all are unmanaged except for the one through which I access the openwrt web management page, which is my fully "trusted" vlan (20). All have the "bridge interfaces" under physical settings enabled and the firewall is always unspecified. Needless to say that dnsmasq, firewall and odhcpd are disabled under system/startup.
Here are the questions I am asking myself:
1- Is this configuration globally acceptable/correct/safe?
2- Is it optimal?
3- By default, openwrt comes with vlans 1 and 2. My understanding from the openwrt documentation is that vlan 1 corresponds to lan network and vlan 2 to the wan one. Is this right? Do I still need these two in my current configuration?
4- Inspired by some post I found in the net for a similar router with openwrt as an ap, I decided to tag all my vlans under "CPU (eth0)" but my understanding ti that I could also tag them under "CPU (eth1)", right? Any difference? Should I use both combined?
5- Can I get rid of the default lan interface (vlan 1)? I have disabled it for the moment.
6- What about the WAN port? Is there something I could/should be doing with it?
Thanks!