Hello again! I swear I'm almost done configuring this router.
Today I've changed VDSL provider, configured using a PPPoE interface connected to a modem in bridge mode. After doing this my "APP" VLAN lost internet access and I cannot restore it in any way (I triple-checked all the settings, tried to disable the VPN and route the traffic directly to WAN but nothing).
network:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdd0:2f26:f252::/48'
config interface 'lan'
option type 'bridge'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.12.1'
list dns '192.168.12.1'
option ifname 'eth0.1 tap0'
config interface 'wan'
option proto 'pppoe'
option ipv6 'auto'
list dns '8.8.8.8'
list dns '8.8.4.4'
list dns '1.1.1.1'
option peerdns '0'
option password 'xxxx'
option username 'xxxx'
option ifname 'eth0.835'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 2 3 4'
config switch_vlan
option device 'switch0'
option vlan '2'
option vid '2'
option ports '0t 5'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '0t 1'
option vid '835'
config interface 'vpn'
option ifname 'tun0'
option proto 'dhcp'
option hostname 'Wrt-1443'
config interface 'app'
option proto 'static'
option type 'bridge'
option netmask '255.255.255.0'
option ipaddr '192.168.13.1'
option ifname 'eth0.2'
list dns '192.168.13.1'
DHCP:
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option localservice '1'
option confdir '/tmp/dnsmasq.d'
config dhcp 'lan'
option interface 'lan'
option limit '150'
option leasetime '12h'
option start '30'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'app'
option leasetime '12h'
option limit '150'
option interface 'app'
option start '30'
list dhcp_option '6,8.8.8.8,8.8.4.4,1.1.1.1'
firewall:
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option output 'ACCEPT'
option network 'lan'
option input 'ACCEPT'
option forward 'REJECT'
config zone
option network 'app'
option input 'ACCEPT'
option forward 'REJECT'
option name 'app'
option output 'ACCEPT'
config zone
option name 'wan'
option output 'ACCEPT'
option mtu_fix '1'
option network 'wan'
option input 'REJECT'
option forward 'REJECT'
option masq '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option network 'vpn'
option forward 'REJECT'
option name 'vpn'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option input 'REJECT'
config forwarding
option dest 'vpn'
option src 'app'
config forwarding
option dest 'wan'
option src 'app'
config redirect
option dest_port '12225'
option src 'wan'
option name 'HomeVPN'
option src_dport '12225'
option target 'DNAT'
option dest_ip '192.168.12.1'
option dest 'lan'
list proto 'tcp'
list proto 'udp'
vpn-policy-routing:
config vpn-policy-routing 'config'
option verbosity '2'
option src_ipset '0'
option ipv6_enabled '0'
list supported_interface ''
list ignored_interface 'vpnserver wgserver'
option iptables_rule_option 'append'
option iprule_enabled '0'
option webui_enable_column '0'
option webui_protocol_column '0'
option webui_chain_column '0'
option webui_sorting '1'
list webui_supported_protocol 'tcp'
list webui_supported_protocol 'udp'
list webui_supported_protocol 'tcp udp'
list webui_supported_protocol 'icmp'
list webui_supported_protocol 'all'
option dest_ipset 'ipset'
option strict_enforcement '0'
option boot_timeout '60'
option enabled '1'
config policy
option src_port '0-65535'
option src_addr '192.168.13.0/24'
option dest_addr '0.0.0.0/0'
option dest_port '0-65535'
option name 'APP'
option interface 'vpn'
SQM:
config queue 'eth1'
option qdisc 'fq_codel'
option script 'simple.qos'
option qdisc_advanced '0'
option linklayer 'none'
option interface 'br-app'
option debug_logging '0'
option verbosity '5'
option download '3400'
option upload '8200'
option enabled '1'
config queue
option debug_logging '0'
option verbosity '5'
option download '0'
option upload '0'
option qdisc 'cake'
option script 'piece_of_cake.qos'
option qdisc_advanced '0'
option linklayer 'ethernet'
option overhead '34'
option enabled '1'
option interface 'eth0.835'
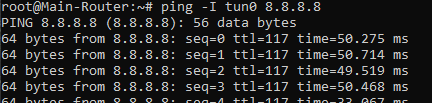
The VPN seems to be correctly connected (pinging internet though tun0 interface works in SSH), other things I tried are disabling vpn-policy-routing but no luck. Devices are getting a local IP address, but no internet access (both on WiFi and in ethernet LAN 4, which is assigned to the APP VLAN).
Note: the "HomeVPN" is a tap device that I use to get access to my LAN remotely (a tcp VPN server, UDP was not working remotely for some reason but TCP should be ok for my low use)
Any advice? I do not know what else to check
Thanks
Ps. I think I may also need to upgrade the router (with all this configured is sitting at about 20MB free RAM and 100Kb flash, it's a cheap TP-Link Archer C6). Or maybe I could keep it? (at the moment my broadband speeds are about 28 / 6 and I don't care to get full bandwidth on VPN)