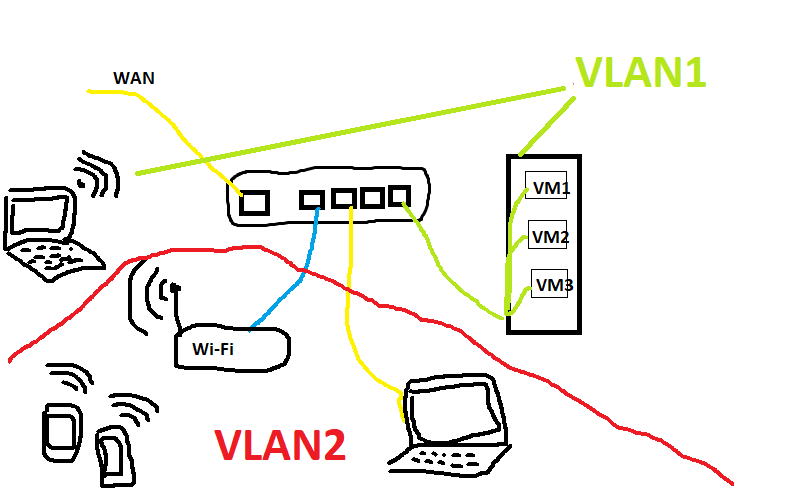
Hi,
The router has 2 physical devices: 1-port eth1 and 4-ports eth0.
ls -l /sys/class/net
lrwxrwxrwx 1 root root 0 Jan 19 12:04 br-lan -> ../../devices/virtual/net/br-lan
lrwxrwxrwx 1 root root 0 Jan 21 14:50 br-vlan1 -> ../../devices/virtual/net/br-vlan1
lrwxrwxrwx 1 root root 0 Jan 21 14:50 br-vlan2 -> ../../devices/virtual/net/br-vlan2
lrwxrwxrwx 1 root root 0 Dec 31 1969 eth0 -> ../../devices/platform/ixp4xx_eth.32/net/eth0
lrwxrwxrwx 1 root root 0 Jan 21 14:50 eth0.1 -> ../../devices/virtual/net/eth0.1
lrwxrwxrwx 1 root root 0 Jan 21 14:50 eth0.2 -> ../../devices/virtual/net/eth0.2
lrwxrwxrwx 1 root root 0 Dec 31 1969 eth1 -> ../../devices/platform/ixp4xx_eth.16/net/eth1
lrwxrwxrwx 1 root root 0 Jan 21 15:00 gre0 -> ../../devices/virtual/net/gre0
lrwxrwxrwx 1 root root 0 Jan 21 15:00 gretap0 -> ../../devices/virtual/net/gretap0
lrwxrwxrwx 1 root root 0 Jan 21 15:00 ip_vti0 -> ../../devices/virtual/net/ip_vti0
lrwxrwxrwx 1 root root 0 Dec 31 1969 lo -> ../../devices/virtual/net/lo
lrwxrwxrwx 1 root root 0 Jan 19 11:10 vti0 -> ../../devices/virtual/net/vti0
Configs are:
config interface 'lan'
option ifname 'eth0'
option proto 'static'
option ip6assign '60'
option delegate '0'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option type 'bridge'
config interface 'vlan1'
option proto 'static'
option netmask '255.255.255.0'
option delegate '0'
option type 'bridge'
option ifname 'eth0 eth0.1'
option ipaddr '192.168.222.1'
config interface 'vlan2'
option proto 'static'
option netmask '255.255.255.0'
option delegate '0'
option type 'bridge'
option ifname 'eth0 eth0.2'
option ipaddr '192.168.223.1'
I can ping both 222.1 and 223.1 from 1.0 subnet.
I can't assign to any PC an ip-address from 222.1 or 223.1? (in other words how to connect to that VLANs?)
Point is physically connected devices to any of 4 eth0 ports results nothing - IP is not assigned.
Installing switch not working (message is - switch0 has unknown topology....)
What am I missing?