You need to assign the guest interface in a separate firewall zone.
ok got it, thanks for that advice.
network:
config interface 'lan'
option type 'bridge'
option ifname 'eth0'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.0.1'
list dns '192.168.0.10'
config interface 'wan'
option ifname 'eth1'
option proto 'dhcp'
config interface 'lan_guest'
option proto 'static'
option ifname 'eth0.30'
option ipaddr '10.0.0.1'
option netmask '255.255.255.0'
option gateway '10.0.0.1'
list dns '192.168.0.10'
firewall:
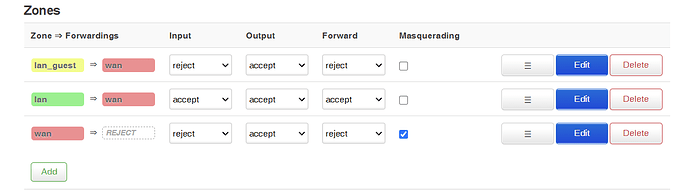
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'lan_guest'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan_guest'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config forwarding
option src 'lan'
option dest 'wan'
config forwarding
option src 'lan_guest'
option dest 'wan'
i guess this is right, or ? 
Better, remove the gateway and dns from guest.
Hi,
i removed gateway, but dns i want that my guests use this dns server (pihole), isnt it allowed?
or are you see any problems ?
It definitely puts at least a pinhole in your separation. If someone exploits your pinhole and gets access to your pihole, then they're on your main network uninhibited. This may or may not be a problem worth considering. You might consider putting the PiHole on its own zone, maybe a pihole zone and then allow forwarding between lan -> pihole and lan_guest -> pihole. On the other hand, it might not be worth the trouble, and you just poke the pinhole allowing the guests to hit the pihole.
This is not the way to configure that.
By default OpenWrt advertises itself as nameserver to the hosts in lan or guest with dhcp. Then you have configured the pihole on lan interface as nameserver, so it forwards the queries there.
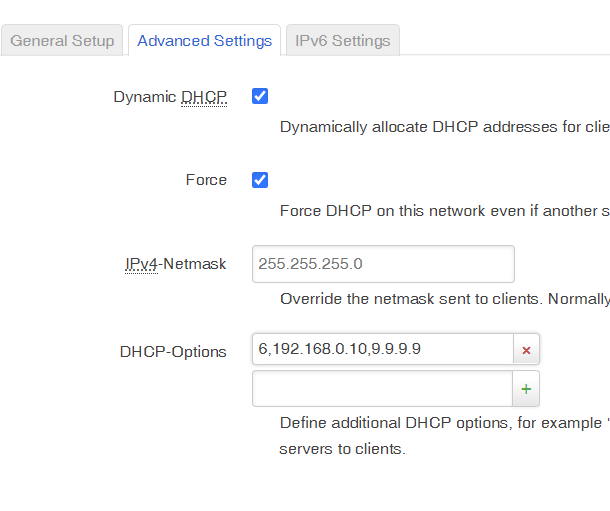
You could change the dhcp packet to advertise the pihole directly as a dns, with option 6. But then you'd need additional rules to allow the flow in firewall.
Also depending on how much you trust the guests, the guest firewall zone is too open. As per guide in the wiki, INPUT and FORWARD are rejected, and there are 2 rules to allow incoming DNS and DHCP.
Ok, here we go  Im still learning, please be patient with me
Im still learning, please be patient with me 
And sorry for some late response, i have to translate the answer first and try to understand 
I changed now my Guest Network:
PiHole DNS
i put the option 6 as you said.
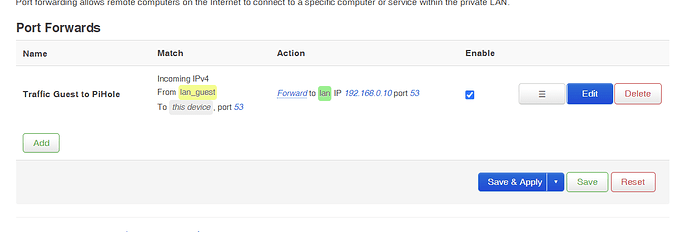
but i doesnt work without port forward.
Rule:
summary:
i can connect to guest wifi, i cant access local network, and tracking block with pihole works.
internet access works also 
to answer your, i trust all my guests its just familiy and friends, nothing special. noone with a IT brain.
i gues my solution couple of threads ago works too, but im here to learn and do it like the "right" way.
i know usually there are many ways.
What do you think now? Better ? anything to change ?
Because you need a rule to allow udp/53 from lan_guest zone towards lan IP 192.168.0.10. The port forward is not needed.
Also you are advertising the quad9 nameserver to the lan hosts which is bypassing the pihole.
Remove source port 53 from the rule. Also only udp is enough.
It is not used as fallback in case the first one fails, but in parallel with pihole.
hmm still not working. 
Post here the output of uci export firewall; iptables-save -c
uci export firewall; iptables-save -c
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan_guest'
option output 'ACCEPT'
option forward 'REJECT'
option input 'REJECT'
option networ 'lan_guest'
list device 'eth0.30'
option network 'lan_guest'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option proto 'esp'
option target 'ACCEPT'
option dest 'lan'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
option dest 'lan'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
config rule
option target 'ACCEPT'
option name 'Sonos upnp discover returns'
option proto 'udp'
option dest_port '1900-1905'
option family 'ipv4'
option src 'lan'
option enabled '0'
config rule
option src_port '5353'
option src 'lan'
option name 'Spotify Connect - from LAN'
option family 'ipv4'
option target 'ACCEPT'
option dest_port '5353'
list proto 'udp'
option enabled '0'
config rule
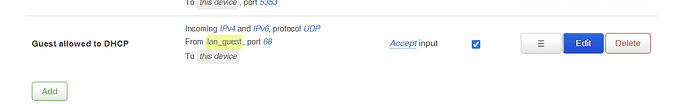
option src 'lan_guest'
option target 'ACCEPT'
option name 'Guest allowed to DHCP'
list proto 'udp'
option src_port '68'
config rule
option name 'Guest allowed PiHole'
option src 'lan_guest'
option dest_port '53'
option target 'ACCEPT'
list proto 'udp'
list dest_ip '192.168.0.10'
config redirect
option target 'DNAT'
option name 'Guest to PiHole'
list proto 'udp'
option src 'lan_guest'
option src_dport '53'
option dest_ip '192.168.0.10'
option dest_port '53'
option dest 'lan'
config rule 'ovpn'
option name 'Allow-OpenVPN'
option src 'wan'
option dest_port '1194'
option proto 'udp'
option target 'ACCEPT'
option enabled '0'
config forwarding
option src 'lan_guest'
option dest 'wan'
config forwarding
option src 'lan'
option dest 'wan'
# Generated by iptables-save v1.8.4 on Sat Jan 16 17:13:57 2021
*raw
:PREROUTING ACCEPT [27208:19748580]
:OUTPUT ACCEPT [1473:2018884]
:zone_lan_guest_helper - [0:0]
:zone_lan_helper - [0:0]
[8529:796140] -A PREROUTING -i eth0.30 -m comment --comment "!fw3: lan_guest CT helper assignment" -j zone_lan_guest_helper
[3415:566695] -A PREROUTING -i br-lan -m comment --comment "!fw3: lan CT helper assignment" -j zone_lan_helper
COMMIT
# Completed on Sat Jan 16 17:13:57 2021
# Generated by iptables-save v1.8.4 on Sat Jan 16 17:13:57 2021
*nat
:PREROUTING ACCEPT [821:168474]
:INPUT ACCEPT [109:9469]
:OUTPUT ACCEPT [93:6368]
:POSTROUTING ACCEPT [112:7439]
:postrouting_lan_guest_rule - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_guest_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_guest_postrouting - [0:0]
:zone_lan_guest_prerouting - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[917:174928] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[199:52238] -A PREROUTING -i eth0.30 -m comment --comment "!fw3" -j zone_lan_guest_prerouting
[664:113845] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[54:8845] -A PREROUTING -i br-wan -m comment --comment "!fw3" -j zone_wan_prerouting
[569:92712] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[0:0] -A POSTROUTING -o eth0.30 -m comment --comment "!fw3" -j zone_lan_guest_postrouting
[97:6512] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[457:85273] -A POSTROUTING -o br-wan -m comment --comment "!fw3" -j zone_wan_postrouting
[0:0] -A zone_lan_guest_postrouting -m comment --comment "!fw3: Custom lan_guest postrouting rule chain" -j postrouting_lan_guest_rule
[199:52238] -A zone_lan_guest_prerouting -m comment --comment "!fw3: Custom lan_guest prerouting rule chain" -j prerouting_lan_guest_rule
[96:6454] -A zone_lan_guest_prerouting -p udp -m udp --dport 53 -m comment --comment "!fw3: Guest to PiHole" -j DNAT --to-destination 192.168.0.10:53
[97:6512] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[664:113845] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[457:85273] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[457:85273] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[54:8845] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Sat Jan 16 17:13:57 2021
# Generated by iptables-save v1.8.4 on Sat Jan 16 17:13:57 2021
*mangle
:PREROUTING ACCEPT [27214:19748820]
:INPUT ACCEPT [1348:198598]
:FORWARD ACCEPT [25542:19478112]
:OUTPUT ACCEPT [1487:2023108]
:POSTROUTING ACCEPT [26924:21496560]
[101:5892] -A FORWARD -o br-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[105:6012] -A FORWARD -i br-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Sat Jan 16 17:13:57 2021
# Generated by iptables-save v1.8.4 on Sat Jan 16 17:13:57 2021
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_guest_rule - [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_guest_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_guest_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_guest_dest_ACCEPT - [0:0]
:zone_lan_guest_dest_REJECT - [0:0]
:zone_lan_guest_forward - [0:0]
:zone_lan_guest_input - [0:0]
:zone_lan_guest_output - [0:0]
:zone_lan_guest_src_REJECT - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[166:14055] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[1184:184623] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[896:155250] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[100:5084] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[0:0] -A INPUT -i eth0.30 -m comment --comment "!fw3" -j zone_lan_guest_input
[185:17971] -A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
[103:11402] -A INPUT -i br-wan -m comment --comment "!fw3" -j zone_wan_input
[25542:19478112] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[24968:19371402] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[222:65983] -A FORWARD -i eth0.30 -m comment --comment "!fw3" -j zone_lan_guest_forward
[352:40727] -A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i br-wan -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -m comment --comment "!fw3" -j reject
[166:14055] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[1326:2010165] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[1209:2003034] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A OUTPUT -o eth0.30 -m comment --comment "!fw3" -j zone_lan_guest_output
[6:388] -A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
[111:6743] -A OUTPUT -o br-wan -m comment --comment "!fw3" -j zone_wan_output
[95:10789] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[8:613] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[100:5084] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[6:388] -A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
[352:40727] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[352:40727] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[0:0] -A zone_lan_guest_dest_ACCEPT -o eth0.30 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_lan_guest_dest_REJECT -o eth0.30 -m comment --comment "!fw3" -j reject
[222:65983] -A zone_lan_guest_forward -m comment --comment "!fw3: Custom lan_guest forwarding rule chain" -j forwarding_lan_guest_rule
[222:65983] -A zone_lan_guest_forward -m comment --comment "!fw3: Zone lan_guest to wan forwarding policy" -j zone_wan_dest_ACCEPT
[102:6855] -A zone_lan_guest_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_guest_forward -m comment --comment "!fw3" -j zone_lan_guest_dest_REJECT
[0:0] -A zone_lan_guest_input -m comment --comment "!fw3: Custom lan_guest input rule chain" -j input_lan_guest_rule
[0:0] -A zone_lan_guest_input -p udp -m udp --sport 68 -m comment --comment "!fw3: Guest allowed to DHCP" -j ACCEPT
[0:0] -A zone_lan_guest_input -d 192.168.0.10/32 -p udp -m udp --dport 53 -m comment --comment "!fw3: Guest allowed PiHole" -j ACCEPT
[0:0] -A zone_lan_guest_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[0:0] -A zone_lan_guest_input -m comment --comment "!fw3" -j zone_lan_guest_src_REJECT
[0:0] -A zone_lan_guest_output -m comment --comment "!fw3: Custom lan_guest output rule chain" -j output_lan_guest_rule
[0:0] -A zone_lan_guest_output -m comment --comment "!fw3" -j zone_lan_guest_dest_ACCEPT
[0:0] -A zone_lan_guest_src_REJECT -i eth0.30 -m comment --comment "!fw3" -j reject
[185:17971] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[185:17971] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[6:388] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[6:388] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[185:17971] -A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[105:4660] -A zone_wan_dest_ACCEPT -o br-wan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[478:101938] -A zone_wan_dest_ACCEPT -o br-wan -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o br-wan -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[103:11402] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[0:0] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[0:0] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[103:11402] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[111:6743] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[111:6743] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[103:11402] -A zone_wan_src_REJECT -i br-wan -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Sat Jan 16 17:13:57 2021
this line is not correct. A couple of lines below is the correct one.
Should be destination port 67.
The destination zone is missing
is not needed.
made all. doesnt work. 
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan_guest'
option output 'ACCEPT'
option forward 'REJECT'
option input 'REJECT'
list device 'eth0.30'
option network 'lan_guest'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option proto 'esp'
option target 'ACCEPT'
option dest 'lan'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
option dest 'lan'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
config rule
option target 'ACCEPT'
option name 'Sonos upnp discover returns'
option proto 'udp'
option dest_port '1900-1905'
option family 'ipv4'
option src 'lan'
option enabled '0'
config rule
option src_port '5353'
option src 'lan'
option name 'Spotify Connect - from LAN'
option family 'ipv4'
option target 'ACCEPT'
option dest_port '5353'
list proto 'udp'
option enabled '0'
config rule
option src 'lan_guest'
option target 'ACCEPT'
option name 'Guest allowed to DHCP'
list proto 'udp'
option src_port '68'
option dest_port '67'
config rule
option name 'Guest allowed PiHole'
option src 'lan_guest'
option dest_port '53'
option dest 'lan'
option target 'ACCEPT'
list proto 'udp'
list dest_ip '192.168.0.10'
config rule 'ovpn'
option name 'Allow-OpenVPN'
option src 'wan'
option dest_port '1194'
option proto 'udp'
option target 'ACCEPT'
option enabled '0'
config forwarding
option src 'lan_guest'
option dest 'wan'
config forwarding
option src 'lan'
option dest 'wan'
# Generated by iptables-save v1.8.4 on Sat Jan 16 19:53:26 2021
*raw
:PREROUTING ACCEPT [53156:55953808]
:OUTPUT ACCEPT [896:708138]
:zone_lan_guest_helper - [0:0]
:zone_lan_helper - [0:0]
[1449:277329] -A PREROUTING -i eth0.30 -m comment --comment "!fw3: lan_guest CT helper assignment" -j zone_lan_guest_helper
[8751:716578] -A PREROUTING -i br-lan -m comment --comment "!fw3: lan CT helper assignment" -j zone_lan_helper
COMMIT
# Completed on Sat Jan 16 19:53:26 2021
# Generated by iptables-save v1.8.4 on Sat Jan 16 19:53:26 2021
*nat
:PREROUTING ACCEPT [670:121215]
:INPUT ACCEPT [74:5822]
:OUTPUT ACCEPT [5:355]
:POSTROUTING ACCEPT [5:355]
:postrouting_lan_guest_rule - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_guest_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_guest_postrouting - [0:0]
:zone_lan_guest_prerouting - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[670:121215] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[126:33051] -A PREROUTING -i eth0.30 -m comment --comment "!fw3" -j zone_lan_guest_prerouting
[539:87948] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[5:216] -A PREROUTING -i br-wan -m comment --comment "!fw3" -j zone_wan_prerouting
[260:49542] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[0:0] -A POSTROUTING -o eth0.30 -m comment --comment "!fw3" -j zone_lan_guest_postrouting
[0:0] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[255:49187] -A POSTROUTING -o br-wan -m comment --comment "!fw3" -j zone_wan_postrouting
[0:0] -A zone_lan_guest_postrouting -m comment --comment "!fw3: Custom lan_guest postrouting rule chain" -j postrouting_lan_guest_rule
[126:33051] -A zone_lan_guest_prerouting -m comment --comment "!fw3: Custom lan_guest prerouting rule chain" -j prerouting_lan_guest_rule
[0:0] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[539:87948] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[255:49187] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[255:49187] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[5:216] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Sat Jan 16 19:53:26 2021
# Generated by iptables-save v1.8.4 on Sat Jan 16 19:53:26 2021
*mangle
:PREROUTING ACCEPT [53156:55953808]
:INPUT ACCEPT [829:87405]
:FORWARD ACCEPT [51986:55800213]
:OUTPUT ACCEPT [907:711794]
:POSTROUTING ACCEPT [52885:56511615]
[116:6888] -A FORWARD -o br-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[118:6860] -A FORWARD -i br-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Sat Jan 16 19:53:26 2021
# Generated by iptables-save v1.8.4 on Sat Jan 16 19:53:26 2021
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_guest_rule - [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_guest_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_guest_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_guest_dest_ACCEPT - [0:0]
:zone_lan_guest_dest_REJECT - [0:0]
:zone_lan_guest_forward - [0:0]
:zone_lan_guest_input - [0:0]
:zone_lan_guest_output - [0:0]
:zone_lan_guest_src_REJECT - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[390:29690] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[440:57755] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[314:46420] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[50:2556] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[0:0] -A INPUT -i eth0.30 -m comment --comment "!fw3" -j zone_lan_guest_input
[118:10987] -A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
[8:348] -A INPUT -i br-wan -m comment --comment "!fw3" -j zone_wan_input
[51986:55800213] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[51700:55741605] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[124:39318] -A FORWARD -i eth0.30 -m comment --comment "!fw3" -j zone_lan_guest_forward
[162:19290] -A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i br-wan -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -m comment --comment "!fw3" -j reject
[390:29690] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[522:683344] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[521:683304] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A OUTPUT -o eth0.30 -m comment --comment "!fw3" -j zone_lan_guest_output
[0:0] -A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
[1:40] -A OUTPUT -o br-wan -m comment --comment "!fw3" -j zone_wan_output
[8:348] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[0:0] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[50:2556] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[0:0] -A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
[162:19290] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[162:19290] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[0:0] -A zone_lan_guest_dest_ACCEPT -o eth0.30 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_lan_guest_dest_REJECT -o eth0.30 -m comment --comment "!fw3" -j reject
[124:39318] -A zone_lan_guest_forward -m comment --comment "!fw3: Custom lan_guest forwarding rule chain" -j forwarding_lan_guest_rule
[0:0] -A zone_lan_guest_forward -d 192.168.0.10/32 -p udp -m udp --dport 53 -m comment --comment "!fw3: Guest allowed PiHole" -j zone_lan_dest_ACCEPT
[124:39318] -A zone_lan_guest_forward -m comment --comment "!fw3: Zone lan_guest to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_guest_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_guest_forward -m comment --comment "!fw3" -j zone_lan_guest_dest_REJECT
[0:0] -A zone_lan_guest_input -m comment --comment "!fw3: Custom lan_guest input rule chain" -j input_lan_guest_rule
[0:0] -A zone_lan_guest_input -p udp -m udp --sport 68 --dport 67 -m comment --comment "!fw3: Guest allowed to DHCP" -j ACCEPT
[0:0] -A zone_lan_guest_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[0:0] -A zone_lan_guest_input -m comment --comment "!fw3" -j zone_lan_guest_src_REJECT
[0:0] -A zone_lan_guest_output -m comment --comment "!fw3: Custom lan_guest output rule chain" -j output_lan_guest_rule
[0:0] -A zone_lan_guest_output -m comment --comment "!fw3" -j zone_lan_guest_dest_ACCEPT
[0:0] -A zone_lan_guest_src_REJECT -i eth0.30 -m comment --comment "!fw3" -j reject
[118:10987] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[118:10987] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[0:0] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[0:0] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[118:10987] -A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[8:392] -A zone_wan_dest_ACCEPT -o br-wan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[279:58256] -A zone_wan_dest_ACCEPT -o br-wan -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o br-wan -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[8:348] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[0:0] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[0:0] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[8:348] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[1:40] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[1:40] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[8:348] -A zone_wan_src_REJECT -i br-wan -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Sat Jan 16 19:53:26 2021
The first two lines are the device input. No packets have arrived since the last firewall restart from guest zone.
The other two lines are for forwarding. Guest zone is allowed to 192.168.0.10:53, but again no packets have hit the firewall.
Try to manually resolve from a guest host
nslookup openwrt.org 192.168.0.10
ok connected via guest wlan.
answer:
Server: piHole
Address: 192.168.0.10
non-authoritative answer
Name: openwrt.org
Addresses: mac +ip
Should be something like that
Non-authoritative answer:
Name: openwrt.org
Address: 139.59.209.225
Name: openwrt.org
Address: 2a03:b0c0:3:d0::1af1:1
The last one is IPv6, not mac.
looks like it works.
i think we can close this thread, i will reopen another one for sonos.
but alteast i have a nice configured guest lan  thank you.
thank you.
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.