no, it gets access to the internet through the fact that you are doing 1:1 NAT for the entire IP address that it's using:
That went right over my head...
SMH...
You may need to research the term "SNAT" then. With an SNAT, you assign an internal IP to use a Public IP....basically it's the opposite of a PORT FORWARD. ![]()
So you would use normal LAN IPs for the machines, then SNAT each one to the desired public address(es) for outbound traffic.
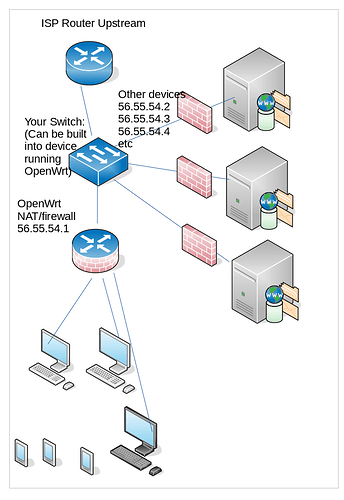
Imagine you have just 5 machines all of which should have a public IP... Then you simply plug in a switch to your ISP's connection, and put each machine with a static public IP... and list the ISP's router as your gateway, and voila, you're on the network...
but then you have to have host firewalls on each machine, or you need to do some firewalling "in the switch". (note, for servers on public IPs I suggest host firewalls EVEN IF you have an upstream firewall as well)
This all becomes problematic if you have some additional machines that don't have static public IPs... so you make one of the "public IPs" be assigned to your OpenWrt router... and put a LAN under NAT behind it.. like a default config for your OpenWrt router.
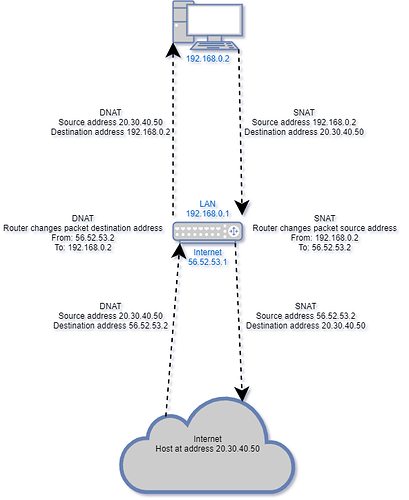
SNAT is Source Network Address Translation. It involves altering the packet header to change its source address. The recipient sees the translated address, not the real address.
DNAT is Destination Network Address Translation. It involves altering the packet header to change its destination address. The sender never knows about the translation.
Here's a quick and dirty diagram I knocked up in draw.io just now. It illustrates the concept.
I totally agree, but the sad truth is that this is a rather uncommon setup - and -worse- in practice always ends up as a hybrid setup (even if you get 8 IPs, you tend to have more devices in your LAN, so you'll practically always end up with NAT as well, and here it gets ugly). Chances are better for IPv6 to take over and push out the need for IPv4, at least one would hope so...
If your ISP is not peering with you on 56.52.53.* network you should be able to use all eight IP addresses.
I think the minimum for one's own AS is a /24. 
At least, it was the last time I checked.
Within your own domain/AS it's up to you. So ISP can give you /29 while advertising /24 or bigger to outside of their domain/AS.
Thank you for all the input you given its very much apprised.
So I tried resetting and starting from scratch.
Setup it BT Home hub 5 A running OpenWrt connected to my ISP via the BTHH built-in DSL.
Connection to the internet via WiFi is possible and is operating with DHCP
I have tried implementing this guide which uses SNAT and DNAT
But still cannot get access to my server from any of the other addresses in my address block
Could someone please clear up two things from the guide for me, please
config interface 'wan3' <<< Is this just a name given to another wan or is it actually pointing to another device
option proto 'static'
option ifname 'eth1' <<<<is this another interface or just a given name ?
option ipaddr '100.64.0.3'
option netmask '255.255.255.248'
option gateway '100.64.0.1' <<< Should this be my router address or the GW of my address block?
Do I need to set up another VLAN to get this to work?
I cannot see or understand how OpenWrt is able to connect to the internet via the above config
This should be the same name as used in your regular WAN. So it might be eth0.2 or eth1 or whatever
As for wan2 that's just a name you're giving to the new openwrt interface... Whatever you like
...you know, the OP could also make a VLAN or use the LAN...I advise a new one...and route /32's to it...hence using them. ![]()
![]() Or better yet, route the whole /29 - as the router is smart enough to know it has one of the IPs assigned to it!
Or better yet, route the whole /29 - as the router is smart enough to know it has one of the IPs assigned to it!
I am curious to know if the ISP uses another IP and gateway in another subnet...if so the OP can use all of the IPs on that subnet (using one [.1] as the VLAN's IP on the router) and simply route it there.
![]() ...and in this scenario, the firewall works (if setup properly, that is).
...and in this scenario, the firewall works (if setup properly, that is).
Yes, that's the config I was thinking of when I said:
The issue comes when you need to do masquerading from say VLAN1 (where you have say 192.168.1.0/24) but want to not masquerade from say VLAN5 (where the whole /29 is)
it's not hard, but it requires some custom firewall rules I think.
An SNAT rule will accept any valid IP. ![]()
I have a /24, I actually have it subnetted...I use the network and broadcast barriers for SNATs on the router. ![]()
If the OP wanted to assign IPs to the devices anyways, this should not be an issue...otherwise, they need to make sure they Port Forward and SNAT the correct ports if used for another service in another network (that just make its convoluted - I'd reserve an IP I don't use in the new VLAN for such a purpose).
Also, each zone can has:
So yea, it can be done...but if the network has those IPs, a masquerade would not occur, the router has been given a (specific) route. ![]()
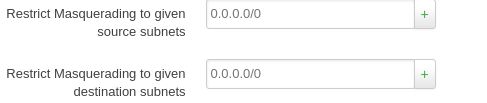
oh nice that GUI for restricting masquerade is exactly what's needed... at that point I think you're right it's just make a VLAN, connect all the "public" devices in that VLAN, give them static IPs, and then for the "private" vlan do masquerade on wan with restricted to just the 192.168.1.0/24 (or whatever) subnet. voila
No masquerade needed in your (our) example - the router knows the route:
well, I'm assuming that there are two groups of machines, one group have public IPs (servers), and a separate group have private only (a home LAN). So the private only machines need masquerade.
This was the only thing keeping me from recommending just putting a VLAN in. But now that I see you can masq based on source address subset without too much manual config... Here's what I'd suggest: @mrbronz61
VLAN1) Your home LAN
VLAN2) Your WAN (typical but could also be say eth1)
VLAN3) Your DMZ/Server Farm
put 192.168.1.1 on eth0.1 and use that like regular OpenWrt out of the box config for the home LAN.
put 56.52.53.1 on the WAN interface (for sake of argument suppose it's eth0.2).
Create a custom routing rule that routes 56.52.53.0/29 to dev eth0.3
Connect your server/public devices to vlan3 ports on your switch
Static IP each of the public devices in their operating system
put eth0.3 in the WAN firewall zone or in its own firewall zone with rules for forwarding from/to WAN
select masquerade on the WAN interface and use only from source 192.168.1.0/24
done
It sounds like the ISP has given a single block of Public IP instead of a WAN block and a LAN block to OP.
In this case, I think the simple way of assign the Public IP to other machines connecting to the Router is to use Layer2 switching.
By default, WAN port is VLAN 2 in OpenWrt. So just assign another port to VLAN2 (untagged), connect the host server to it, and assign IP address in exactly the same way as the Router - just with a different IP address in the block.
In this configuration, the OpenWrt router is just a VLAN switch to the Host Server - so the Host will have full access to the Public Internet and must be running a Host Firewall.
Personally, my ISP give me two set of Dynamic IPs (each set having both IPv4 and IPv6), I am using VLAN trunking to allow one of my Virtual Guest running inside Fedora to use the second set of Public IPs.
But I am interested to to learn how to use the second set of Dynamic IPs in the layer3 way as well.
May be I should create another topic about that.