So how can I bridge Wifi "TestOPN" SSID and VLAN 19.

So how can I bridge Wifi "TestOPN" SSID and VLAN 19.
The principle is to connect the wifi SSID to an existing interface.
Taking in consideration the existing lan interface, I'd try this one:
config interface 'Test'
option device 'br-lan.19'
option type 'bridge'
option proto 'none'
I think you need to configure the switch since the ath79 target is still swconfig. (in swconfig you use the Network-Switch page to directly control the hardware switch; bridge-vlans are DSA oriented). Each VLAN needs an entry in the switch to bring it from the eth port to the external port. Also the 10/100 SoCs don't directly support VLAN numbers over 16-- it requires CLI configuration of separate option vlan and option vid.
Avoid running tagged and untagged on the same cable. When running a trunk between two VLAN-aware devices, tag all packets. This means you should convert the lan network to VLAN 1 or some other VLAN number, conventionally 1 is the privileged network used for administration.
I'm not sure how that worked at all since an unmanaged interface has no IP address in the kernel, so there is no way for it to originate layer 3 traffic from the router OS. The 'Test' bridge is going to be a passive layer 2 conversion of wifi to wired. The device at the other end of the Ethernet cable needs to handle DHCP and all layer 3 actions.
Taking in consideration the existing lan interface, I'd try this one:
I've already tried without success, see
I think you need to configure the switch since the ath79 target is still swconfig. (in swconfig you use the Network-Switch page to directly control the hardware switch; bridge-vlans are DSA oriented). Each VLAN needs an entry in the switch to bring it from the eth port to the external port. Also the 10/100 SoCs don't directly support VLAN numbers over 16-- it requires CLI configuration of separate option vlan and option vid.
Can you explain that a bit more? With stock firmware, I just enter VLAN19 at the SSID setting and SSID is in VLAN. I find it strange that this seems to hard to setup in OpenWRT.
Avoid running tagged and untagged on the same cable.
It is historically grown. Network was completely without VLAN. Then TP-Link APs with stock firmware were added and another VLAN was added as guest network. Works very well.
I'm not sure how that worked at all since an unmanaged interface has no IP address in the kernel, so there is no way for it to originate layer 3 traffic from the router OS. The 'Test' bridge is going to be a passive layer 2 conversion of wifi to wired. The device at the other end of the Ethernet cable needs to handle DHCP and all layer 3 actions.
See:
For testing purposes I had also selected DHCP-Client on eht0.19 and I got an IP-Adress in VLAN19. I also could do a curl --interface eth0.19 ifconfig.me and got the outbound IP-Adress of VLAN19.
But now interface is removed again, because from VLAN19 should be no possibility to access any device in the network (except firewall/router, see below).
There is another Linux machine attached to the same ethernet configuration, so without VLAN normal network and an eth0.19 interace where DHCP and routing with seletected firewall rules is running. So OpenWRT should be a stupid AP, just connect eth0.19 with TestOPN Wireless network in this case.
You need to make a bridge containing eth0.19, maybe call it br-vlan19.
config device
option name 'br-vlan19'
option type 'bridge'
list ports 'eth0.19'And a network with proto none to claim this bridge. That really doesn't do anything but if you don't have this section the bridge doesn't get set up at all.
config interface 'vlan19'
option device 'br-vlan19'
option proto 'none'For testing you can set the interface as DHCP client proto dhcp instead and have a local IP.
Then since there is a network called 'vlan19' use option network 'vlan19' in /etc/config/wireless to attach your AP to the bridge. A bridge takes over the interfaces within it, you wouldn't reference 'eth0.19' directly except in the bridge device creation.
brctl show should show the br-vlan19 bridge and the ports within it.
Thanks. Now it works with your configuration.
To get this done via LuCI without editing config files with VLAN19 example:
ip link add link eth0 name eth0.19 type vlan id 19
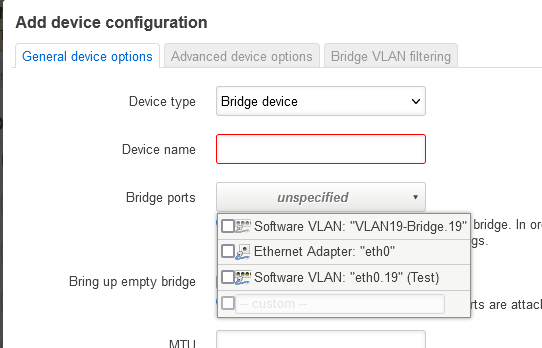
Now go to tab device and click "Add device configuration"
Select "Bridge Device" as device type, give a name like "br-vlan19" and bridge port eth0.19, click Save and then "Save and Apply"
Now go to interfaces again, you see now a VLAN19 interface.
Click Edit button and change device to "br-vlan19".
Now you have a br-vlan19 interface (that was the missing step)
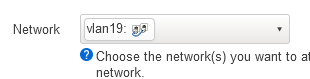
Now you can choose vlan19 at your SSID as Network and it will work. If not enabling and disabling SSID helps.
@Mods: Seems to work as soon as I flagged this as solution. No need to change anything of new user status.
These pictures may be used for an official Wiki article.
@mk24
What a coincidence, I am trying exactly the same thing.
I want to use my old Archer C7v2 as a wireless AP connected to pfSense.
Only LAN1 port is used
One «Wifi» subnet on VLAN110
One «Guests» subnet on VLAN115
Whether I connect to Wifi SSID or Guests SSID, I get a DHCP lease from the VLAN110
On pfSense, VLAN110 is 10.0.110.1
On pfSense VLAN115 is 172.16.115.1
Any help will be greatly appreciated.
{
"kernel": "5.4.143",
"hostname": "OpenWrt",
"system": "Qualcomm Atheros QCA9558 ver 1 rev 0",
"model": "TP-Link Archer C7 v2",
"board_name": "tplink,archer-c7-v2",
"release": {
"distribution": "OpenWrt",
"version": "21.02.0",
"revision": "r16279-5cc0535800",
"target": "ath79/generic",
"description": "OpenWrt 21.02.0 r16279-5cc0535800"
}
}
package network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd55:6aa3:81e2::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1.1'
option ipv6 '0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '10.0.110.2'
option gateway '10.0.110.1'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0t 2 3 4 5'
option vid '1'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 6t'
option vid '2'
config bridge-vlan
option device 'br-guests'
list ports 'eth1.4:t'
config bridge-vlan
option device 'br-wifi'
list ports 'eth1.3:t'
config bridge-vlan
option device 'br-guests'
config bridge-vlan
option device 'br-wifi'
config interface 'Wifi'
option proto 'none'
option device 'br-wifi'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '0t 2t 6t'
option vid '3'
option description 'VLAN110 (Wifi)'
option pvid '110'
config device
option type 'bridge'
option name 'br-wifi'
list ports 'eth1.3'
option ipv6 '0'
config interface 'Guests'
option proto 'none'
option device 'br-guests'
config device
option type 'bridge'
option name 'br-guests'
list ports 'eth1.4'
option ipv6 '0'
config switch_vlan
option device 'switch0'
option vlan '4'
option ports '0t 2t 6t'
option vid '4'
option description 'VLAN115 (Guests)'
option pvid '115'
package wireless
config wifi-device 'radio0'
option type 'mac80211'
option hwmode '11a'
option path 'pci0000:00/0000:00:00.0'
option htmode 'VHT80'
option cell_density '0'
option channel '157'
option country 'CA'
config wifi-iface 'default_radio0'
option device 'radio0'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'sae-mixed'
option ieee80211w '1'
option key 'xxx'
option network 'Wifi lan'
config wifi-device 'radio1'
option type 'mac80211'
option hwmode '11g'
option path 'platform/ahb/18100000.wmac'
option htmode 'HT20'
option cell_density '0'
option channel '6'
config wifi-iface 'default_radio1'
option device 'radio1'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'sae-mixed'
option key 'xxx'
option ieee80211w '1'
option network 'Wifi lan'
config wifi-iface 'wifinet2'
option device 'radio0'
option mode 'ap'
option ssid 'OpenWrt_Invites'
option encryption 'sae-mixed'
option key 'xxx'
option ieee80211w '1'
option network 'Guests lan'
config wifi-iface 'wifinet3'
option device 'radio1'
option mode 'ap'
option ssid 'OpenWrt_Invites'
option encryption 'none'
option network 'Guests lan'
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option ignore '1'
list ra_flags 'none'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
config zone
option name 'off'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'Guests'
list network 'Wifi'
Hold on before any of you reply....
I created the Guest VLAN but forgot to put any rules..... But then, why does my cell phone gets on the Wifi subnet ?
[EDIT 22h00]
Ok, so I configured the firewall rules on pfSense.
My phone is still getting on the Wifi subnet when connecting to Guests SSID.
What's missing ?
Did you already check if this is a pfsense issue or a OpenWRT issue? So did you connect a PC to pfSense to the port where Archer C7v2 is and set in Ethernet Controller VLAN115?
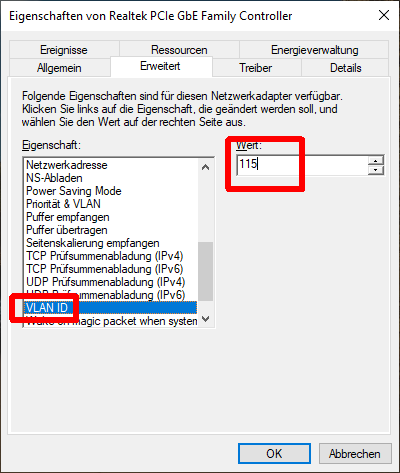
If there is no IP from Guests network, then error is on pfSense.
I can see multiple entries both from swconfig and DSA.
Also clean up the stale entries.
I am not sure I understand what you call stale entries.
While @VLANMaster had only VLAN19, I want to have two VLANS, one for private users and another one for guests. Those 2 entries highlighted in blue are different bridges.
Is it more visible now?
config bridge-vlan
option device 'br-guests'
list ports 'eth1.4:t'
config bridge-vlan
option device 'br-wifi'
list ports 'eth1.3:t'
config bridge-vlan
option device 'br-guests'
config bridge-vlan
option device 'br-wifi'
Oh yes! My bad.
I made quite a cleanup.
Just a reminder of what I am trying to achieve.
Now, my /etc/config/network looks like:
#
##::[[--- Archer C7v2 Config ---]]::##
################################################
# Globals #
#----------------------------------------------
config globals 'globals'
option ula_prefix 'fd0f:50c2:91df::/48'
# Loopback #
#----------------------------------------------
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
# LAN: Regular #
#---------------------------------------------
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1.1'
option ipv6 '0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '10.0.0.11'
option gateway '10.0.0.1'
# LAN: Wifi private addresses #
#--------------------------------------------
config device
option type 'bridge'
option name 'br-wifi'
list ports 'eth1.1 eth1.3'
option ipv6 '0'
config interface 'WIFI'
option device 'br-wifi'
option proto 'dhcp'
option netmask '255.255.255.0'
option gateway '10.0.110.1'
option dns '10.0.110.1'
# LAN: Guests #
#-------------------------------------------
config device
option type 'bridge'
option name 'br-guests'
list ports 'eth1.1 eth1.4'
option ipv6 '0'
config interface 'GUESTS'
option device 'br-guests'
option proto 'dhcp'
option netmask '255.255.255.0'
option gateway '172.16.115.1'
option dns '172.16.115.1'
###########################################
##----- Virtual Switches -----##
###########################################
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0t 2 3 4 5'
option vid '1'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1t 6'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '0t 1t 2t'
option vid '3'
option description 'Wifi(110)'
option pvid '110'
config switch_vlan
option device 'switch0'
option vlan '4'
option ports '0t 1t 2t'
option vid '4'
option description 'Guest(115)'
option pvid '115'
[EDIT 17:00]
Once I added the radios in LuCI, all my comments ##### are gone in /etc/config/network but the file is basically the same.
My bridge between LAN and WIFI must not be working because I get this:
root@OpenWrt:~# brctl show
bridge name bridge id STP enabled interfaces
br-guests 7fff.9aded0f9d1ea no wlan0-1
wlan1-1
br-wifi 7fff.98ded0f9d1ea no wlan0
wlan1
br-lan 7fff.98ded0f9d1eb no eth1.1
And
I can't get a lease on my phone on vlan Guests
I can get a lease on Wifi but it's still in 10.0.0.0 subnet
What I am missing here ?
[EDIT 19h]
So before anyone lose any time on this, I just realised there is a mismatch on the port shown in LuCI vs CLI so I am turning in circles with /etc/config/network
I have started another thread just to get some help in identifying my ports and once I get this resolved, I'll come back here: Mismatch between LuCi en CLI to ask further help if required.
So I solved my logical ports problem.
Here is my latest output
{
"kernel": "5.4.143",
"hostname": "OpenWrt",
"system": "Qualcomm Atheros QCA9558 ver 1 rev 0",
"model": "TP-Link Archer C7 v2",
"board_name": "tplink,archer-c7-v2",
"release": {
"distribution": "OpenWrt",
"version": "21.02.0",
"revision": "r16279-5cc0535800",
"target": "ath79/generic",
"description": "OpenWrt 21.02.0 r16279-5cc0535800"
}
}
package network
config globals 'globals'
option ula_prefix 'fd0f:50c2:91df::/48'
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1.1'
option ipv6 '0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '10.0.0.11'
option gateway '10.0.0.1'
config device
option type 'bridge'
option name 'br-wifi'
list ports 'eth1.1 eth1.3'
option ipv6 '0'
config interface 'wifi'
option device 'br-wifi'
option proto 'dhcp'
option netmask '255.255.255.0'
option gateway '10.0.110.1'
option dns '10.0.110.1'
option type 'bridge'
config device
option type 'bridge'
option name 'br-guests'
list ports 'eth1.1 eth1.4'
option ipv6 '0'
config interface 'guests'
option device 'br-guests'
option proto 'dhcp'
option netmask '255.255.255.0'
option gateway '172.16.115.1'
option dns '172.16.115.1'
option type 'bridge'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0t 6t 2t 3 4 5'
option vid '1'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '0t 6t 2t'
option vid '3'
option description 'Wifi(110)'
option pvid '110'
config switch_vlan
option device 'switch0'
option vlan '4'
option ports '0t 6t 2t'
option vid '4'
option description 'Guest(115)'
option pvid '115'
package wireless
config wifi-device 'radio0'
option type 'mac80211'
option hwmode '11a'
option path 'pci0000:00/0000:00:00.0'
option htmode 'VHT80'
option cell_density '0'
option channel '157'
option country 'CA'
config wifi-iface 'default_radio0'
option device 'radio0'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'sae-mixed'
option key 'nnn'
option ieee80211w '1'
option network 'lan WIFI wifi'
config wifi-device 'radio1'
option type 'mac80211'
option hwmode '11g'
option path 'platform/ahb/18100000.wmac'
option htmode 'HT20'
option cell_density '0'
option channel '6'
config wifi-iface 'default_radio1'
option device 'radio1'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'sae-mixed'
option key 'nnn'
option ieee80211w '1'
option network 'lan WIFI wifi'
config wifi-iface 'wifinet2'
option device 'radio0'
option mode 'ap'
option ssid 'OpenWrt_Invites'
option encryption 'sae-mixed'
option key 'nnn'
option ieee80211w '1'
option network 'GUESTS guests lan'
config wifi-iface 'wifinet3'
option device 'radio1'
option mode 'ap'
option ssid 'OpenWrt_Invites'
option encryption 'sae-mixed'
option key 'nnn'
option ieee80211w '1'
option network 'GUESTS guests lan'
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option ignore '1'
list ra_flags 'none'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
SSID Guest does connect but get a lease from 10.0.0.0
SSID Wifi does not connect
I am stuck
Since this is a dumbAP, you don't need to assign multiple IPs.
Use static IP or DHCP on one interface for management, and the rest can be unmanaged.
In the network configuration I still see a mix of swconfig and DSA.
For example:
config device
option type 'bridge'
option name 'br-guests'
list ports 'eth1.1 eth1.4'
option ipv6 '0'
and
config switch_vlan
option device 'switch0'
option vlan '4'
option ports '0t 6t 2t'
option vid '4'
option description 'Guest(115)'
option pvid '115'
Furthermore you are bridging the eth1.1 on all bridges.
I suggest you reset the device and follow the dumbAP guide. After that works successfully you can add the other 2 wifi and vlans.
swconfig vs DSA is not clear.
In the docs I read, one is not supposed to use list ports but rather "ifname". I tried that believing it could be a problem in my situation. I got locked out both SSH and GUI because the /etc/network could not load properly.
Once I did the mininal setup in LuCI, I reused the same "options" that I saw to be working in order to complete my config.
My two APs are working. Thanks.
Here it is:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd54:7407:331c::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1.1'
option ipv6 '0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '10.0.0.11'
option gateway '10.0.0.1'
list dns '10.0.0.1'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 1 2 3 4 5 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '110'
option pvid '110'
option ports '0t 1t 6t'
config switch_vlan
option device 'switch0'
option vlan '4'
option vid '115'
option pvid '115'
option ports '0t 1t 6t'
config device
option type 'bridge'
option name 'br-wifi'
option ipv6 '0'
list ports 'eth1'
list ports 'eth1.110'
config interface 'wifi'
option proto 'static'
option ipaddr '10.0.110.2'
option netmask '255.255.255.0'
option gateway '10.0.110.1'
option device 'br-wifi'
list dns '10.0.110.1'
config device
option type 'bridge'
option name 'br-guests'
list ports 'eth1'
list ports 'eth1.115'
option ipv6 '0'
config interface 'guests'
option proto 'static'
option device 'br-guests'
option netmask '255.255.255.0'
option ipaddr '172.15.116.2'
option gateway '172.15.116.1'
list dns '172.15.116.1'
config device
option name 'eth1.110'
option type '8021q'
option ifname 'eth1'
option vid '110'
option ipv6 '0'
config device
option name 'eth1.115'
option type '8021q'
option ifname 'eth1'
option vid '115'
option ipv6 '0'
I'll make a thread for a step by step : Archer C7v2 dual WAP (VLAN) downstream pfSense for those it might help.
I suggest that you use the Luci to configure the network configuration. I don't see why the option ipv6 '0' is part of the device configuration, it should be under the interface.
Furthermore you insist on having multiple IPs and default gateways on a dumbAP. Although this might seem to work fine, it can have unexpected issues in the future. There is no need to have a managed interface on guest vlan or wifi if you manage the device from the lan.
I believe when I started over, all was done entirely in the LuCi.
The only reason why I am doing that is to see what's going on from only on interface, namely pfSense. It's how I managed to do it from what I gathered but it may not be kosher...
What would be your suggestion ?
This is the thread I posted once I got it working. Wifi Access Point on 21.02 | 2 SSIDs using vlan 802.1q (Archer C7v2)
Only one interface with static IP, the one you are using for management. The other 2 interfaces will be unmanaged, no IP, just a vlan to trunk to the pfsense.
Did you start clean or did you migrate from an older version of OpenWrt? Under device configuration should be layer 2 and bridge configuration, while ipv6 is layer 3.
Thanks! It works. I though that it did not make any sense to have 3 static IPs for a single device. Plus I had the experience of setting a Unify AP for someone who is not in recycling old devices like I do and it needed only one adress for the managing interface.
Brand new. I migrated from DD-WRT that had been running for at least 5 years. And each time I locked myself out until I figured I got the port mapping wrong, I started from scratch.