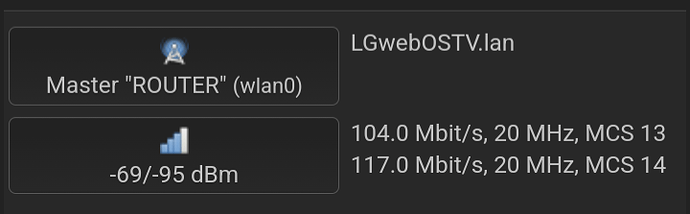
I have installed OpenWRT 21.02.3 on a TP-Link TL-WDR4300 v1 for my mother. She have a phone, a laptop and a tv, which is connected to the router through wlan.
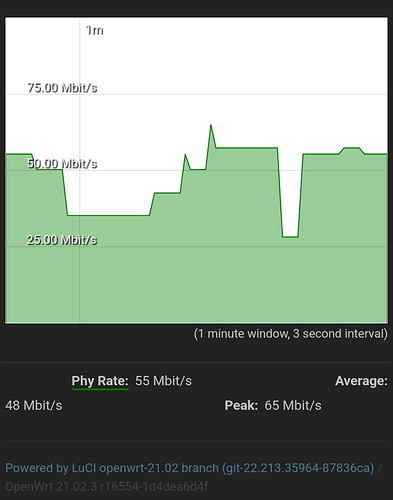
I have called my mother, but she said the TV is switched off (i know, it is probably just in standby). Still, this looks pretty heavy traffic for my eyes.
Does this looks normal? Do you have any idea what's going on here?
trendy
August 8, 2022, 3:27pm
2
Could be some device downloading a firmware upgrade?
Use ssh to connect to the device.
Please run the following commands (copy-paste the whole block) and paste the output here, using the "Preformatted text </> " button:
ubus call system board; \
uci export network; uci export wireless; \
uci export dhcp; uci export firewall; \
head -n -0 /etc/firewall.user; arp
Here you go:
BusyBox v1.33.2 (2022-04-16 12:59:34 UTC) built-in shell (ash)
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
-----------------------------------------------------
OpenWrt 21.02.3, r16554-1d4dea6d4f
-----------------------------------------------------
root@Gb:~# ubus call system board; \
> uci export network; uci export wireless; \
> uci export dhcp; uci export firewall; \
> head -n -0 /etc/firewall.user; arp
{
"kernel": "5.4.188",
"hostname": "AP_NAME",
"system": "Atheros AR9344 rev 2",
"model": "TP-Link TL-WDR4300 v1",
"board_name": "tplink,tl-wdr4300-v1",
"release": {
"distribution": "OpenWrt",
"version": "21.02.3",
"revision": "r16554-1d4dea6d4f",
"target": "ath79/generic",
"description": "OpenWrt 21.02.3 r16554-1d4dea6d4f"
}
}
package network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdec:e059:9f48::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.10.1'
config device
option name 'eth0.2'
option macaddr '60:e3:27:'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '2 3 4 5 0t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 0t'
package wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'platform/ahb/18100000.wmac'
option channel '1'
option band '2g'
option htmode 'HT20'
option disabled '0'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option disabled '0'
option ssid 'ROUTER'
option key 'password'
option encryption 'psk2'
config wifi-device 'radio1'
option type 'mac80211'
option path 'pci0000:00/0000:00:00.0'
option channel '36'
option band '5g'
option htmode 'HT20'
option cell_density '0'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'ROUTER'
option encryption 'psk2'
option key 'password'
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option confdir '/tmp/dnsmasq.d'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
IP address HW type Flags HW address Mask Device
10.171.64. 0x1 0x2 c8:4c:75: * eth0.2
169.254.111. 0x1 0x2 cc:b0:da: * br-lan
10.171.64. 0x1 0x2 00:d0:cb: * eth0.2
192.168.10.175 0x1 0x0 6a:62:cf: * br-lan
192.168.10.241 0x1 0x2 d8:b0:53: * br-lan
192.168.10.203 0x1 0x2 28:b2:bd: * br-lan
192.168.10.184 0x1 0x2 ac:f1:08: * br-lan
192.168.10.122 0x1 0x2 cc:b0:da: * br-lan
192.168.10.204 0x1 0x0 62:63:c7: * br-lan
root@Gb:~#
I don't think so. I update her devices regularily.
The traffic is constantly too high.
Nope, just her phone, laptop and tv. I know all of them, i maintain them.
WPA2-PSK is used on the router. This is in a small village,where accessing others AP is just physically unlikely, as the distances simply way too big.
Run this:
while true; do clear; for wlan in $(iwinfo | grep wlan | awk '{print $1}'); do echo "Interface: $wlan"; iwinfo $wlan assoclist; done; sleep 1; done
It will refresh a list of all connected devices every second.
1 Like
trendy
August 9, 2022, 11:09am
6
Then all these devices belong to your mother?
You can also check the real time packet count with iptraf.iptraf-ng -l br-lan
1 Like
A tip.
3 Likes
I have no idea, what the last MAC is (multicast ipv6?), but the others owned by my mom.
r1ch
August 9, 2022, 6:24pm
9
This is not traffic, it is the link speed of the connection. For Wi-Fi it will constantly fluctuate depending on whether the chipset is trying to power save, environment / interference, etc. The equivalent in Ethernet would be a 100mbps / 1gbps link, it doesn't mean that's actually the amount of traffic going over the link.
2 Likes
Trendy's screenshot has 6 IP addresses though? Yours has 4?
trendy
August 10, 2022, 9:54am
11
42kbps is not some great throughput.@r1ch mentioned.
2 Likes
Thanks, i probably misunderstood it. Thanks. Case closed.
tmomas
August 20, 2022, 3:39pm
13
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.