Yes, I understand that concept! Perhaps I didn't explain myself properly as it can get pretty complicated at times. Let me try and reiterate.
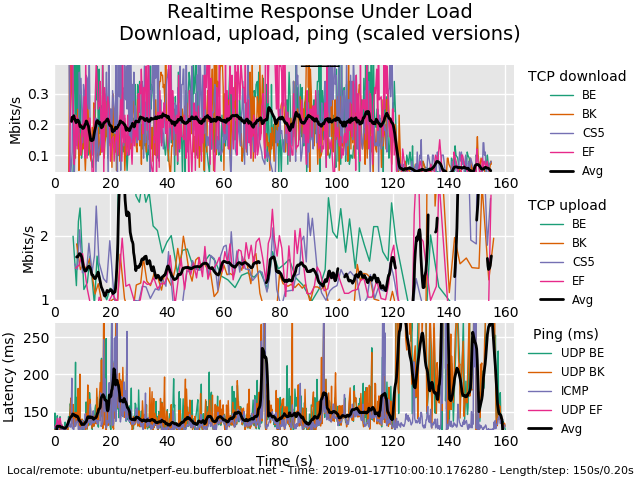
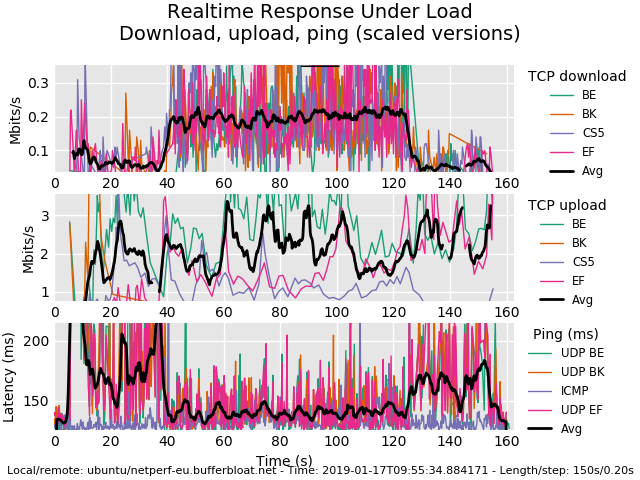
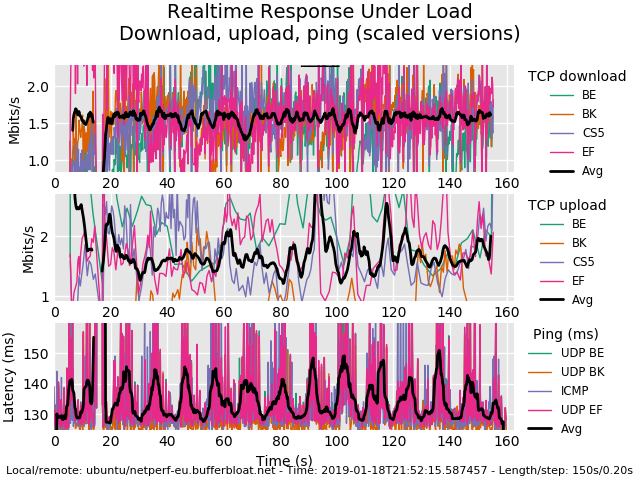
Got egress QoS working, Client OS tags DSCP -> Router -> WAN
Got ingress QoS working with Veth0/1, Router tags DSCP -> Client.
So now I added a OpenVPN (tun0) connection (Hopefully properly) and sending the corresponding ingress over Veth0/1 as well, as I assume if I dont do this, the VPN would circumvent my global QoS ingress setup, no? My game would no longer get prioritized if the VPN runs outside of the QoS setup.
Or is the preferred way to not let VPN run over our existing veth0/1 and instead make a seperate SQM instance for tun0 (vpn interface)
In that case, i could imagine they are not 'aware' of each other and global QoS would not work as expected as the game and all my other traffic is not QoS'ed in the same tins.
Question 2
Ok, theres that, the other thing im trying to figure out in the current 'VPN ingress over veth0/1' method, before i used VPN at all, and had everything setup, i could see on my client with wireshark both incoming and outgoing UDP packets as EF marked, but I dont see incoming packets EF marked with the current VPN setup.
I assumed since the Openwrt has the VPN connection initiated on TCP port 443, i could simply make a rule to mark packets orinating from port 443 to be marked EF, but I dont see it happening when I run the game now,
So either I'm missing something, or not fully grasping it. The iptables code are in my previous post.
I hope I sort of clarified my previous post.